Please note, the following steps walk through an example use case and the information that will need to be saved will be specific to your application.
You will only need to follow the below steps if you don’t have Azure Active Directory set up.
If Azure Active Directory is already set up in your Azure Portal and/or configured as a connector in SecurEnds, you can use the Application (Client) ID, Tenant (Directory) ID, and Client Secret (Secret Value) from Azure Active Directory to setup your Office 365 connector.
Step 1: Application Registration
Get started with Office 365 Management APIs | Microsoft Docs
- Sign into the Azure portal using your Azure account
- Office 365 is not at the Azure Portal. It is one level below, registered as an App under Azure AD
- Select Azure Active Directory > App registration > New registration
- Provide a Name for the application
- Select the appropriate “Supported account types”
- Under Redirect URL, select “Web” as the application type, and (optionally) specify a redirect URL if your application requires it
- After setting the values, select Register. The application registration is created, and the Overview page is presented
- Copy the Application ID for use in your application code. This value is also referred to as the Client ID and will be used in the configuration settings within
- Copy the Tenant ID for use in your application code.
- To generate a client secret/Key, select the Certificates & secrets page then select New client secret
- Provide a description for the secret, and an expires duration.
- The Client Secret/key will be displayed when these settings are saved and compulsory, copy the key to the clipboard, once you leave the page the key will not be visible.
- When done, select Add
Step 2: Azure Permissions
After registering SecurEnds as an application within the Azure portal, the next step is to make sure the application has the correct API permissions to access data within Microsoft Graph. To do this the user or administrator must grant the correct permissions via a consent process.
- From the Home screen select App registration > Created App (under owned Applications) > API Permissions > Add Permissions
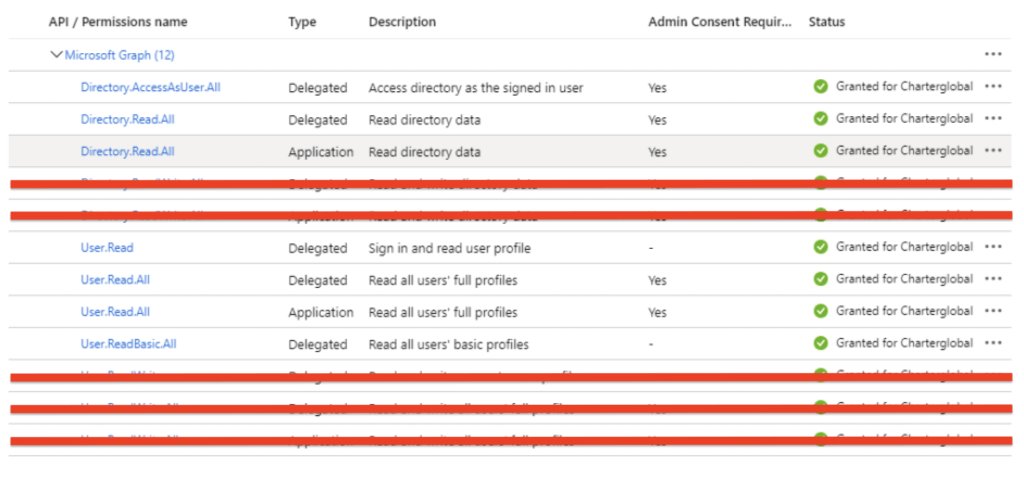
- Under Microsoft Graph give the following Delegated and Application permissions. Totaling 7 permissions in all.
- Delegated permissions:
- User.Read
- User.Read.All
- User.ReadBasic.All
- Directory.AccessAsUser.All
- Directory.Read.All
- Application permissions:
- User.Read.All
- Directory.Read.All
- Delegated permissions:
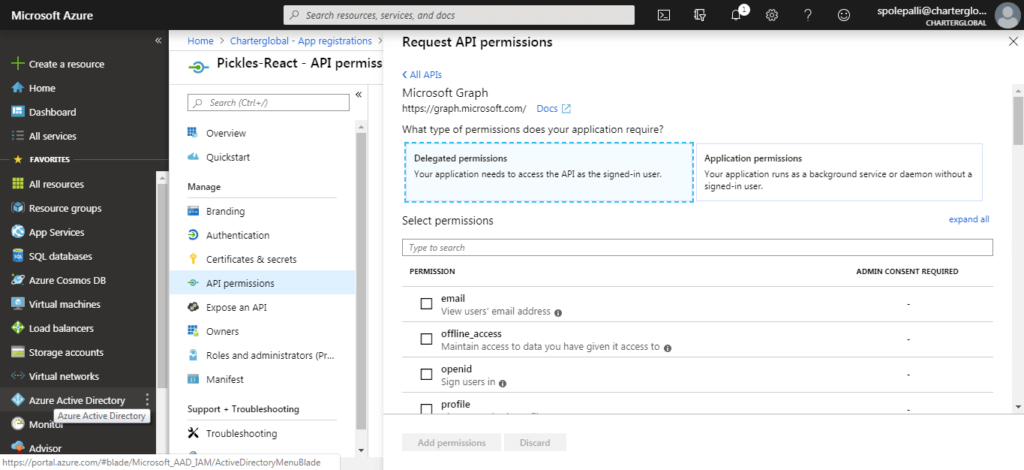
- Once added, click to grant admin consent for the permissions. Once complete, each permission will have a green checkmark as shown below