User Access Reviews
Automate User Access and Entitlement Reviews For Security & Compliance
Still doing User Access/Entitlement Reviews Manually?
User Access Reviews are an important control activity required for internal and external IT security audits. Done monthly or annually manual User Access and Entitlement Reviews can be tedious and cumbersome.
SecurEnds automates User Access reviews, putting CISOs and Security department in control of users’ entitlements across a today’s hybrid IT system. Continuous access certification also enables continuous control.
Automate User Access And Entitlement Reviews
Key Features
Credential Entitlement Management (CEM) for User Access Reviews
SecurEnds Credential Entitlement Management (CEM) product addresses user access reviews that grants enforce, revokes and administers fine-grained access entitlements (also referred to as “authorizations,” “privileges,” “access rights,” “permissions” and/or “rules”). Its purpose is to review IT access policies to structured/unstructured data, devices and services from various endpoints including:
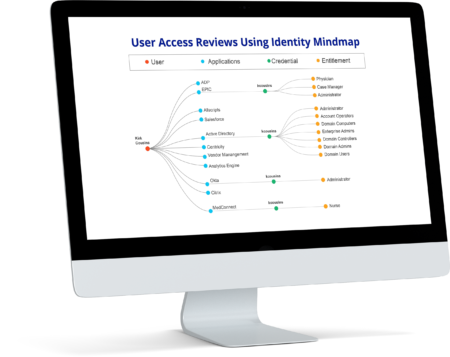
Know Who Has Access to What – With Absolute Clarity
Manual User Access Reviews are error prone and known to lead to audit findings on compliance standards such as SOX, HIPAA, FISMA, GLBA and PCI-DSS.
Key Problems
SecurEnds Solution
Using manual methods such as Excel for conducting user access reviews can lead to inefficiencies and errors.
Struggling to achieve a complete and accurate user access review
Lack of visibility into pending tasks and responsible individuals can hinder effective access management and timely compliance.
Identify the right reviewer for each access review to ensure accurate and compliant access management.
Overcome challenges in accessing and retrieving user data from endpoints such as Active Directory, Office 365, SharePoint, Windows, AWS, Azure, Google G Suite, Salesforce, SAP, and more.
SecurEnds CEM Fixes the Gap in Your Security Stack.
We offer on-premise and cloud offering of our products.
Our products will be configured to provide a solution for your organization
Automate user access rights with a simple workflow
Consolidate enterprise-wide user privileges in a central location
Make your access data more secure to meet compliance regulations
Monitor, track, analyze, and report unauthorized access attempts in real-time.
Generate cross-application rules for separation of duties that trigger real-time alerts
Issue proactive alerts to monitor for sensitive privileges, users, or applications

Accurate Review
Provides an easy solution with complete and accurate review of user access.
Controlled Securely
Ensure your organization is in compliance and user access is controlled securely.
Security Stack
Coordinate and execute user access reviews to fix the gap in your Security stack.

Schedule a Product Demo
Submit your details, and our technical representative will contact you to arrange a personalized demo of our product. Experience its features firsthand and see how it can benefit your business!














