Get Started
Easily Answer “Who has access to what, How can you automate provisioning/deprovisioning? What is your Enterprise Security Posture? How secure is your Cloud?”
With the increase of remote users and modern technology, critical data is crossing organizational boundaries and security teams are grappling to understand “Who has access to what?” and “What are our security risks?”
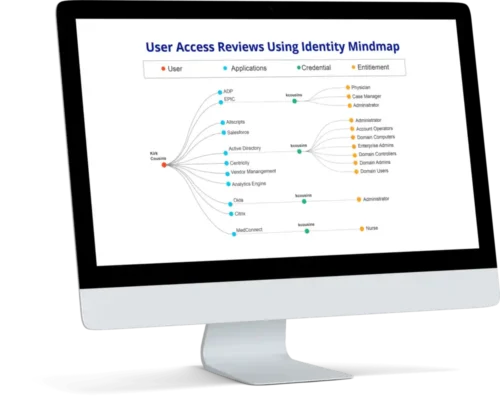
Gain visibility with a single unified view across all applications and platforms – both in the cloud and on-premises – to reduce risk to fortify your security, easily provide proof of compliance, and ultimately reduce audit fatigue
Establish a clean set of user entitlement data to support risk and compliance efforts.
Increase compliance efficiency by streamlining certification processes.
Interactive, identity-centric view across applications and entitlements.
Out-of-the-box application connectors for access reviews.
SaaS-based platform for rapid delivery for quick time-to-value.
Automate access reviews to accelerate accurate access certifications using SecurEnds Credential Entitlement Management (CEM)