Step 1:
Follow the below URL to setup the AWS user for SecurEnds data import.
https://www.securends.com/documentation/configure-aws/
Step 2:
Above step (step 1) is intended to pull the AWS IAM information for single/specific account. However, to work with multi-account (cross-account) scenario, a different approach is required through assume role (STS).
Step 3:
Select one of the multi account and create a custom policy named “SecureEndsCEM-Policy” The “SecureEndsCEM-Policy” must contain the below permissions.
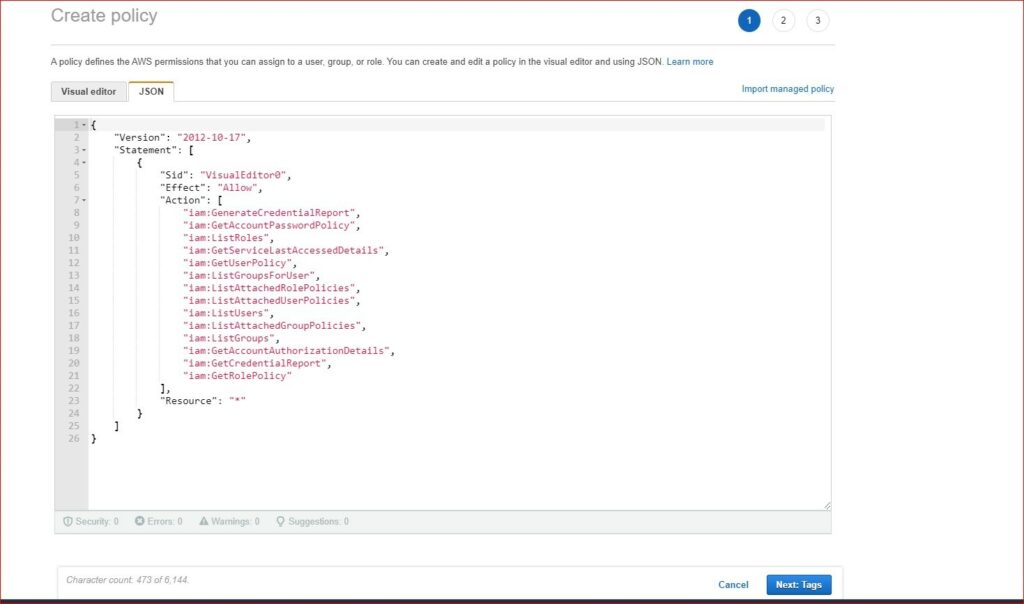
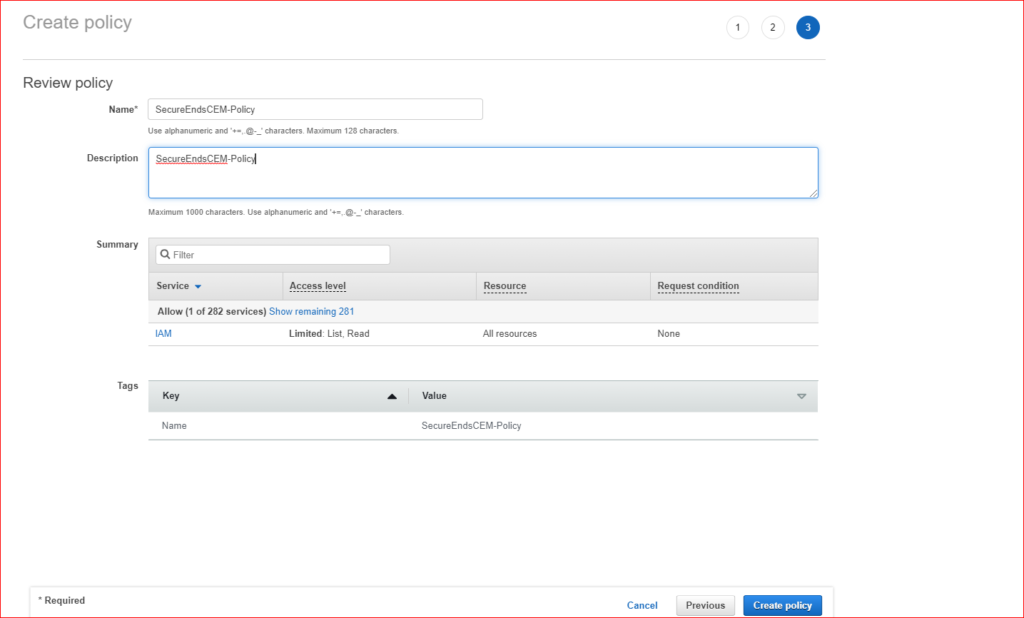
Step 4:
Now, create a new role (assume role) and specify a name E.g., SecureEndsCEM
Attach the custom policy “SecureEndsCEM-Policy” that was created in the step 3 to the “SecureEndsCEM “ role.
Note: Repeat the policy and “assume role” creation process for all the different accounts that were intended to be used by Securends
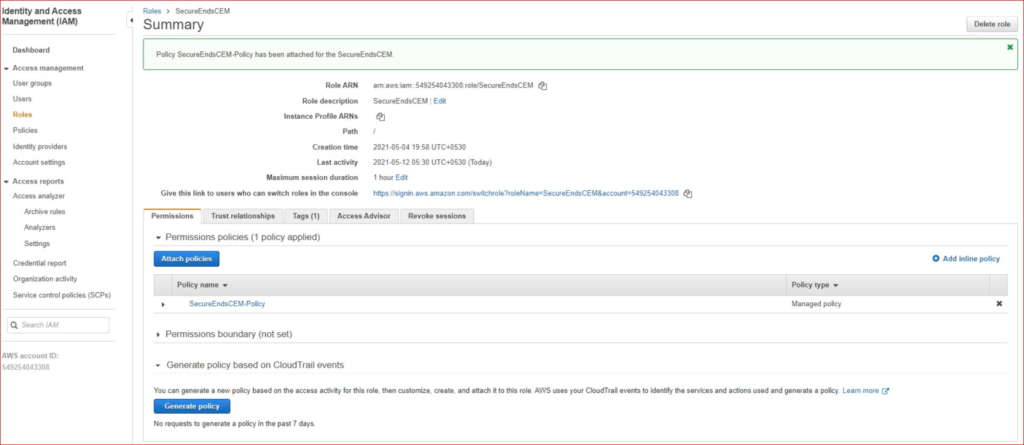
Step 5:
Add the Trust relationship to the STS role. The trust account is the one from which the role is assumed/assigned.
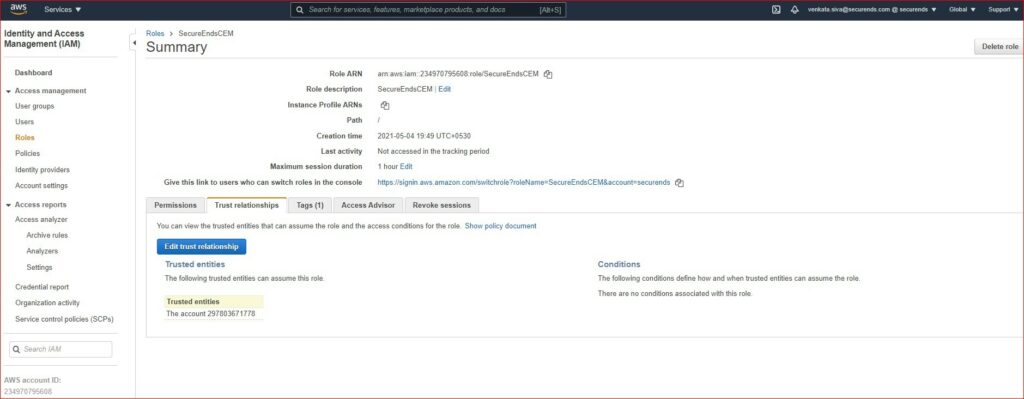
Step 6:
Go to the source account (Securends will use the user from this account to pull the IAM data) and create a custom policy same as specified in the step 3.
Step 7:
Now, go to the user who is created as part of step 1. Go to “Permissions” tab, click on “Add permissions” and attach the custom policy that was created as part of Step 6.
Note: Permissions can be assigned through groups as well. But for now, we are using direct permissions using the policy.
Step 8:
Attach the STS policy (this is new policy) to the new user and mention the assume role ARN of target accounts in the policy (multiple ARN accounts can also be added through resource in the STS policy).
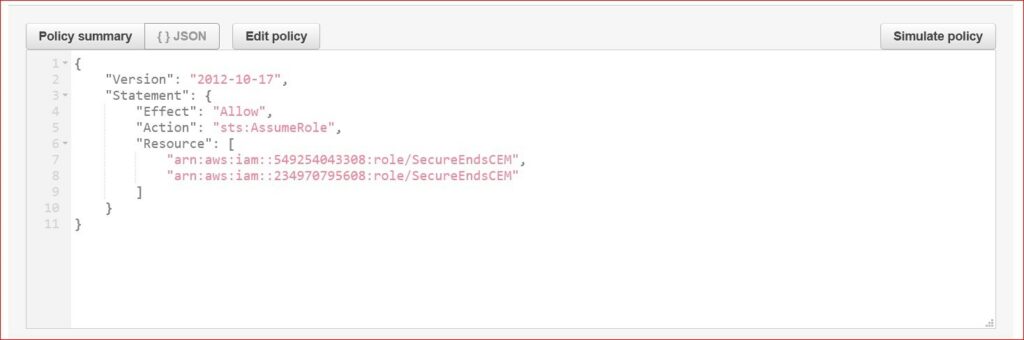
Click on Create policy by providing the name as “SecureEndsCEM-STS-Policy”. After the STS policy is created attach the STS policy to the user
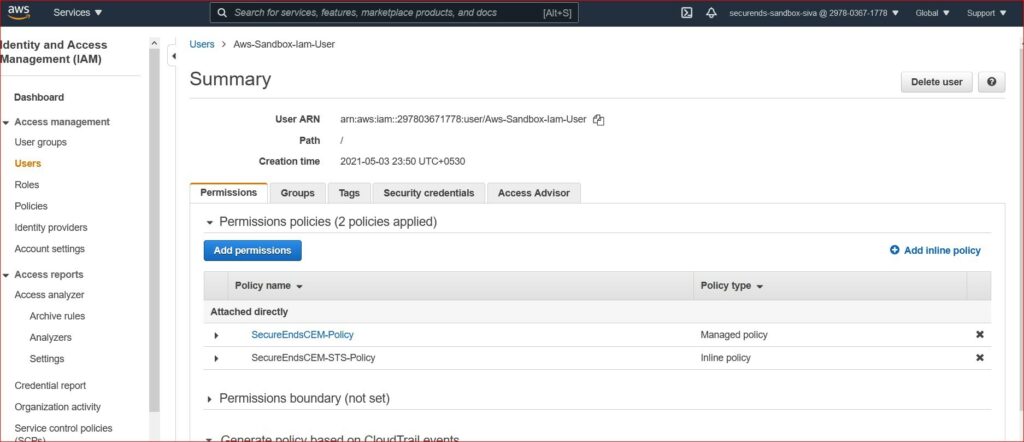
Step 8: Now the user account is setup with the assume role feature to access multiple accounts. Securends can use this assume role and can pull the multi account data using Securends AWS setup credentials https://www.securends.com/documentation/set-up-aws/
Recommended Policies from SecurEnds:
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Sid”: “securends-cem-id”,
“Effect”: “Allow”, “Action”: [ “iam:GetPolicyVersion”, “iam:CreateUser”, “iam:AddUserToGroup”,
“iam:RemoveUserFromGroup”, “iam:ListAttachedRolePolicies”, “iam:ListAttachedUserPolicies”, “iam:ListAttachedGroupPolicies”, “iam:ListRolePolicies”, “iam:DetachUserPolicy”, “iam:ListPolicies”, “iam:GetPolicy”, “iam:ListGroupPolicies”, “iam:UpdateUser”, “iam:ListEntitiesForPolicy”, “iam:DeleteUserPolicy”, “iam:AttachUserPolicy”, “iam:ListRoles”, “iam:DeleteUser”, “iam:ListUserPolicies”, “iam:ListPolicyVersions”, “iam:GetUserPolicy”, “iam:ListGroupsForUser”, “iam:PutUserPolicy”, “iam:ListUsers”, “iam:ListGroups”,
“iam:GetUser”
],
“Resource”: “*”
}
]
}