Identity Analytics
Identity Analytics : A Key Differentiator Of SecurEnds IGA Product
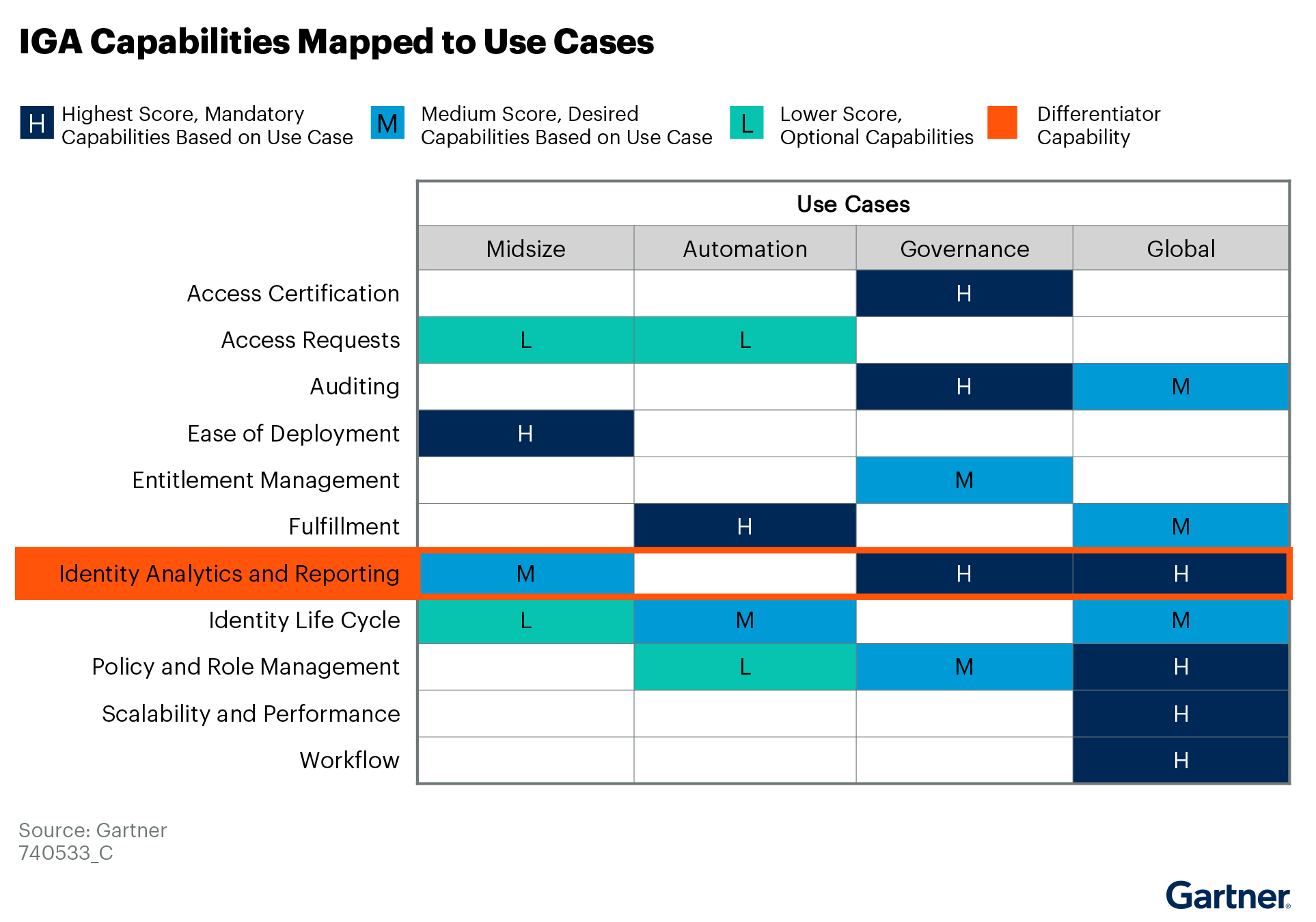
Identity Governance and Administration (IGA): Securing Digital Identities
Identity Governance and Administration (IGA) plays a vital role in IT operations by managing and securing digital identities across users, applications, and data. As businesses expand their technology assets, IGA solutions automate access management, ensuring proper access while minimizing security and compliance risks. With increasing regulatory demands, IGA tools are essential for controlling access to sensitive data, ensuring only authorized personnel can access critical systems and applications.
User Access Review and Certification: Key to Identity Governance
User Access Review and Access Certification campaigns are vital for effective identity governance. As the number of identities—employees, contractors, and vendors—grows across on-premise, hybrid, and cloud systems, managing access becomes increasingly complex. Organizations often struggle to answer, “Are we in continuous compliance?” While traditional methods conduct Access Certifications quarterly or annually, SecurEnds simplifies this process by automating reviews.
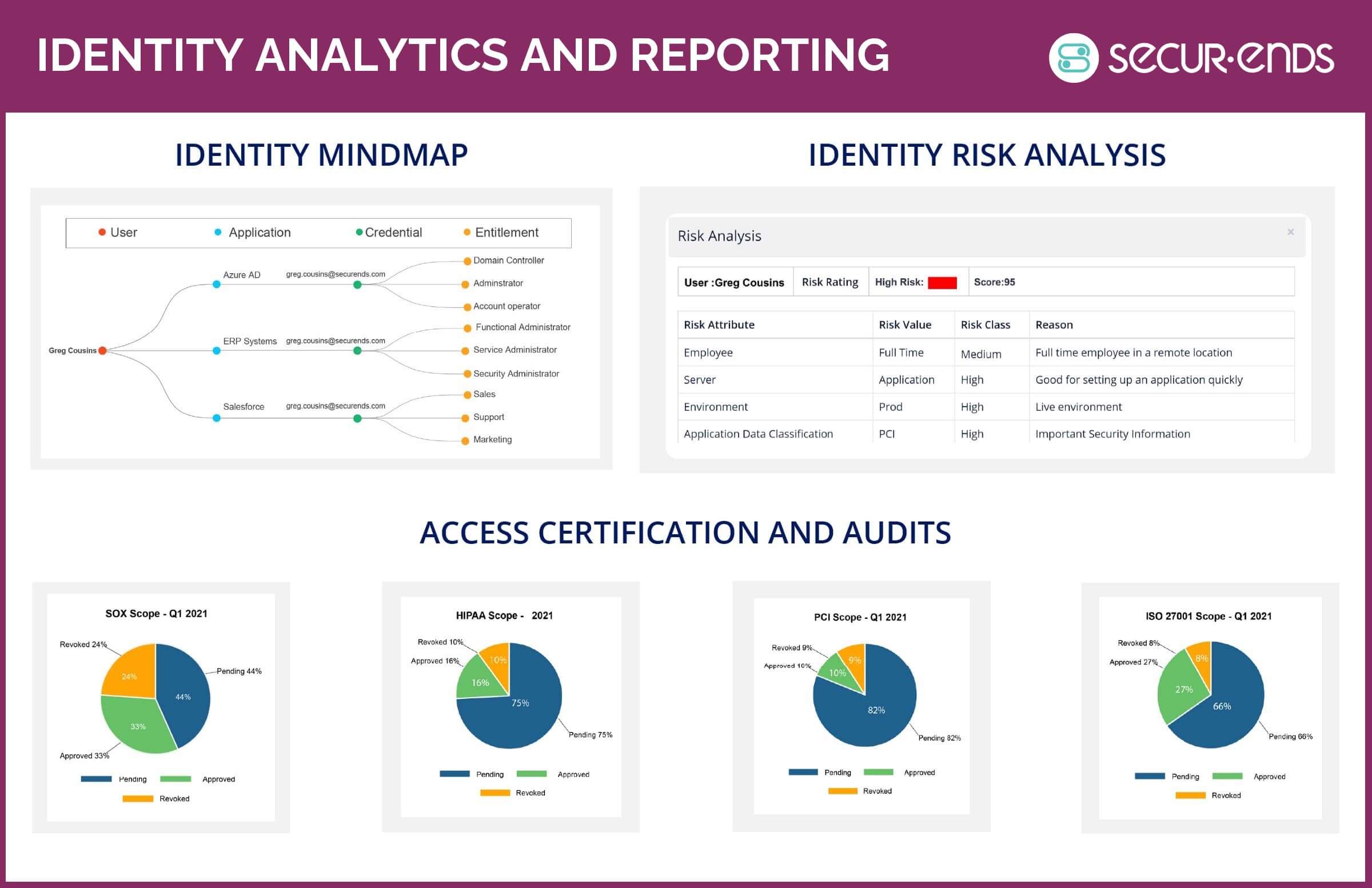
Enhancing Security with Identity Analytics in SecurEnds IGA
Legacy IGA products conduct periodic entitlement reviews, leaving gaps in security. SecurEnds integrates Identity Analytics for continuous, proactive monitoring. This feature allows CISOs, risk analysts, and administrators to detect anomalies by comparing user activity to behavioral baselines. It identifies access and privilege outliers, enhancing security and compliance. Organizations can leverage micro-certifications or continuous monitoring, ensuring real-time risk mitigation and control.