Contractor Self Request Made Easy: Fast, Secure Access with IGA
Contractor Self Request Made Easy: Fast, Secure Access with IGA

Imagine this: A global enterprise is gearing up for a critical product launch. To meet deadlines, they onboard a specialized contractor for database optimization. But before any real work begins, the contractor hits a wall—waiting days for IT to manually provision access to essential systems. The project stalls. Deadlines slip. Frustration mounts.
Sound familiar?
This isn’t an isolated incident—it’s an everyday reality in modern enterprises. As organizations increasingly engage third-party users—contractors, consultants, vendors, and partners—the demand for seamless, secure access to internal systems has never been higher. Yet, provisioning that access remains one of the most overlooked governance challenges.
Manual workflows. Email threads. Disconnected systems. These outdated processes not only slow down productivity but also open the door to serious security and compliance risks. Overprovisioned accounts, orphaned identities, and audit blind spots can quietly accumulate in the background, creating vulnerabilities no organization can afford.
That’s where Contractor Self Request comes in—a modern approach powered by Identity Governance and Administration (IGA) platforms. By enabling contractors to request access via a self-service portal—governed by automated workflows, predefined policies, and real-time approvals—organizations can strike the perfect balance between agility and control.
In this blog, we’ll explore:
- What Contractor Self Request is and where it fits within IGA
- Why third-party access is such a critical governance concern
- How automated access workflows reshape onboarding for external users
- The compliance, security, and operational benefits this model delivers
- And how SecurEnds is making this transformation not only possible—but scalable
If your enterprise works with external collaborators, this blog will help you reimagine access governance in a way that’s faster, smarter, and audit-ready from day one.
2. What Is Contractor Self Request?
Once organizations recognize the need for streamlined third-party access, the next step is understanding how to operationalize it—and that’s where Contractor Self Request comes in.
This feature, built into modern Identity Governance and Administration (IGA) platforms, gives external users like contractors and vendors the ability to request access to enterprise resources through a self-service interface. Rather than waiting on IT or relying on outdated ticketing systems, contractors initiate self request/access requests themselves—securely and in line with organizational policy.
From there, the request is mapped to predefined roles or access levels, routed through an automated approval chain, and—if approved—provisioned with time-bound access. It’s a faster, more secure way to onboard external users, and it leaves behind a complete audit trail for governance teams to review.
Within the broader IGA and Identity Access Management (IAM) ecosystem, Contractor Self Request supports critical components such as:
- Identity Lifecycle Management: It ensures contractor accounts are governed from the moment they’re onboarded to the moment they’re offboarded.
- Policy-Based Provisioning: Every request is evaluated against access policies—what can be requested, by whom, under which conditions.
- Just-in-Time Access Request: Contractors receive access only when they need it, and only for as long as necessary.
- Access Request Workflows: It complements internal mechanisms like Employee Self Request, providing consistency across user types.
Let’s say a cybersecurity consultant is brought in to perform a short-term audit. Instead of granting broad, static access to sensitive systems, your IGA platform enables the consultant to request temporary access via a Contractor Self Request workflow—predefined roles, automated approvals, and a built-in expiration. The result? Quicker onboarding, reduced risk, and full compliance visibility.
3. Why Is Contractor Access a Governance Challenge?
While Contractor Self Request simplifies access on the surface, it’s ultimately a response to a deeper challenge: the governance complexities surrounding external users.
Unlike full-time employees—whose roles, responsibilities, and access needs are typically well-defined—contractors, consultants, and vendors often enter the organization with fluid scopes and short timelines. And yet, they may require access to the same critical systems, databases, or applications.
Traditionally, this has been handled manually: a department sends an email, IT creates an account, someone guesses the right access level, and maybe—if time permits—that access gets reviewed. But manual provisioning is not only inefficient—it’s inherently risky.
Here’s why:
- Overprovisioned Accounts: Contractors often receive more access than necessary “just to get things done,” creating unnecessary exposure.
- Orphaned Accounts: When projects end and contractors leave, their access is rarely revoked promptly—leaving behind active credentials tied to inactive users.
- Shadow IT: In the absence of formal access workflows, contractors may find workarounds—creating risk outside the governance framework.
- Compliance Gaps: Regulatory frameworks like SOX, GDPR, and HIPAA demand strict access control and auditability. Without proper tracking, it’s nearly impossible to demonstrate compliance.
Take, for instance, a marketing consultant brought in to support a product launch. Without a governed access path, they may end up with administrative access to customer data, internal file repositories, or even finance systems—none of which they truly need. Multiply that across dozens of contractors and the governance risk compounds.
That’s why robust third-party access workflows—including features like Contractor Self Request, Just in Time Access Request, and continuous User Access Reviews—are no longer optional. They’re essential to reducing risk, ensuring accountability, and staying compliant.
4. How Contractor Self Request Works Within an IGA Platform
To truly appreciate the impact of Contractor Self Request, it helps to see how it works in practice within an Identity Governance and Administration (IGA) platform. At its core, this feature is designed to make third-party access faster, more secure, and policy-driven—without sacrificing control.
Here’s a streamlined view of the typical flow:
- Contractor Initiates a Request
The contractor logs into a secure access portal—often integrated with platforms like Okta, Azure AD, or a custom IGA interface—and submits a request for specific systems or applications. This could range from internal documentation tools to sensitive project databases.
- System Maps the Request to Roles or Resources
Behind the scenes, the IGA system identifies what access is being requested and matches it to available roles or resource bundles defined by RBAC (Role-Based Access Control) or ABAC (Attribute-Based Access Control) models.
- Automated Approval Workflow Is Triggered
Based on organizational policies, the request is routed through a pre-defined approval chain. For example, a request for accessing code repositories may require approval from both the project lead and the security team.
- Time-Bound Access Is Provisioned
Once approved, access is granted automatically—typically for a predefined duration. This could be 7 days, 30 days, or even a single session, depending on the sensitivity of the resource.
- All Activity Is Logged for Auditing
Every action—request submission, approval, access granted, and revocation—is logged, providing a complete audit trail. This becomes invaluable during User Access Reviews, compliance audits, or incident investigations.
To illustrate, consider an external developer onboarding to support a short-term DevOps project. Through Just in Time Access Request, they can request only the GitHub repositories and cloud environments they need. The system auto-approves it based on their contract type and end date, and disables access once the project ends—no manual ticketing, no gaps in compliance.
In essence, Contractor Self Request transforms third-party access from a reactive IT burden to a proactive, governed process, embedded directly into your broader Identity Access Management (IAM) strategy.
5. Core Components of Contractor Self Request (Under IGA)
For Contractor Self Request to function effectively and securely, it must be built on a strong foundation of governance and automation. Within an IGA (Identity Governance and Administration) framework, several key components work together to enable this seamless experience for both contractors and administrators.
1. Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC)
These are the engines that power access decisions.
- RBAC assigns permissions based on job functions—e.g., “external QA engineer” maps to a pre-approved access profile.
- ABAC takes it further, considering attributes like department, location, contract duration, or project assignment for even more granular control.
This ensures that contractors receive only the access they need, no more, no less—a critical step toward enforcing least privilege.
2. Policy-Based Access Workflows
Not all access requests are equal—and policies help define who can request what, when, and how. For instance:
- A data analyst contractor might be allowed to self-request access to BI dashboards but not to financial reporting tools.
- Emergency access (such as through an Emergency Access Request) may have stricter controls, requiring higher-level approvals or shorter timeframes.
These workflows ensure requests align with internal governance policies and compliance mandates.
3. Integration with HRMS or Contractor Identity Stores
To make accurate decisions, the IGA platform needs to know who the requester is. Integration with identity sources—like Workday, an HRMS, or a contractor registry—ensures that access decisions are context-aware.
This also supports Employee Onboarding and Employee Off-Boarding processes for contractors, syncing identity changes with access entitlements in real-time.
4. Time-Bound or Session-Based Access (JIT)
One of the most powerful features of Contractor Self Request is Just in Time (JIT) Access, which ensures that access is granted only when needed—and for the shortest possible duration.
Think of it as a revolving door that only opens when someone knocks and closes automatically after they leave.
5. Approval Chains and Audit Logging
Approvals aren’t optional—they’re a central piece of the puzzle. Every request is routed through the right stakeholders, and every action—from submission to revocation—is logged.
This level of traceability supports compliance efforts and simplifies User Access Reviews, internal audits, and security investigations.
In short, Contractor Self Request is not just about opening doors—it’s about opening the right doors, for the right people, at the right time, with complete visibility and control.
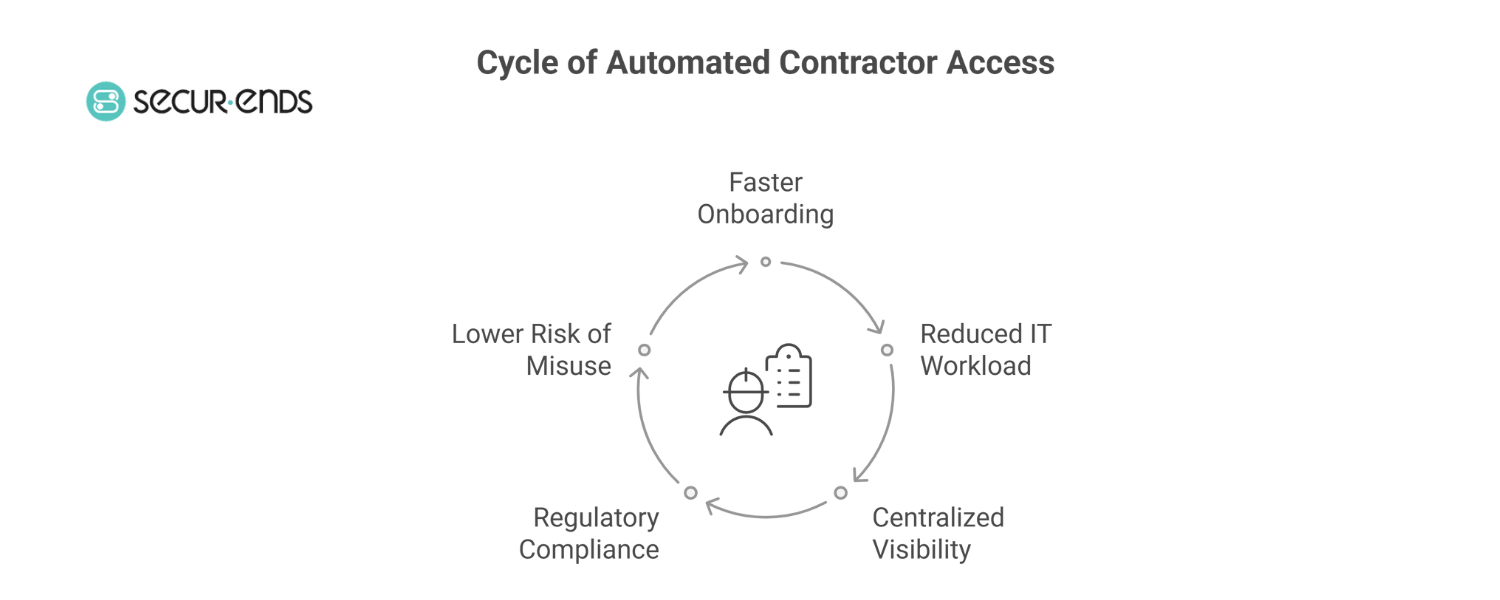
6. Benefits of Automating Contractor Access via Self Request
By now, it’s clear that Contractor Self Request is more than a convenience—it’s a governance accelerator. When integrated into an Identity Governance and Administration (IGA) system, automating third-party access doesn’t just remove friction—it enhances control, compliance, and security at scale.
Here’s how your organization benefits:
1. Faster Onboarding for External Users
In fast-paced environments—especially those working with agile teams, freelancers, or global vendors—time is everything. With Self Request workflows, contractors can gain the access they need within minutes, not days.
No back-and-forth emails, no manual provisioning tickets—just a streamlined, automated path to productivity.
2. Reduced IT Workload
IT and security teams are often bogged down by repetitive access requests. Automating this process with rule-based workflows and predefined roles reduces dependency on IT, allowing teams to focus on more strategic priorities like User Access Reviews, threat detection, and architecture improvement.
3. Centralized Visibility for Access Governance
Each self request/access request—whether for a file share, cloud platform, or collaboration tool—is logged and monitored. With centralized dashboards, security and compliance teams can easily:
- Track who requested what, when, and why
- Detect anomalies (e.g., multiple high-privilege requests from a single identity)
- Simplify reporting for audits and governance reviews
4. Regulatory Compliance Made Simpler
From SOX to HIPAA, GDPR, and ISO 27001, regulatory frameworks require strict oversight of third-party access.
With automated access controls, Just in Time Access Requests, and detailed audit trails, compliance isn’t just a checkbox—it’s a natural outcome of your IGA architecture.
5. Lower Risk of Privilege Misuse
Overprovisioned and orphaned accounts are a goldmine for attackers. By enforcing time-bound and policy-driven access, organizations significantly lower the surface area for insider threats or accidental data exposure.
This also complements Employee Off-Boarding policies by ensuring temporary access doesn’t linger once the contract ends.
In a nutshell, Contractor Self Request brings speed without sacrificing control—making it an essential pillar in any modern Identity Access Management (IAM) strategy.
7. Best Practices for Contractor Self Request Governance
While automating third-party access through Contractor Self Request unlocks tremendous efficiency, it also introduces new responsibilities. Governance isn’t a “set-it-and-forget-it” endeavor—especially when dealing with dynamic, non-employee identities. That’s why having best practices in place is non-negotiable.
Here’s how to make sure your Access Request workflows remain secure, compliant, and scalable:
1. Enforce the Principle of Least Privilege Access
Consider a luxury hotel: guests are granted access to their suite and the relevant amenities—but not to the service corridors or executive offices. Access management for contractors should follow the same philosophy.
Through Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC), permissions are granted strictly based on necessity. This reduces the risk of privilege misuse and aligns seamlessly with Identity Governance and Administration (IGA) frameworks.
2. Set Defined Expiration and Review Intervals
Contract-based work has an inherent timeline—and so should the associated system access. A common pitfall is allowing temporary access to become permanent due to oversight.
Automating Just-in-Time Access Requests with predefined expiration ensures that access concludes when the engagement does. Supplement this with periodic User Access Reviews to reassess ongoing relevance, thereby eliminating dormant or orphaned accounts.
3. Align with Access Recertification Campaigns
Over time, access needs evolve. A contractor who once required elevated privileges may later require minimal system touchpoints.
By integrating Contractor Self Request mechanisms with routine access recertification, organizations can ensure ongoing appropriateness and reinforce their Identity Access Management (IAM) protocols.
4. Fortify with Multi-Factor and Conditional Access
Granting system access without adequate verification is akin to unlocking a secure vault with a single code. For contractors accessing critical infrastructure, particularly in Emergency Access Request scenarios, it’s vital to employ Multi-Factor Authentication (MFA) and contextual access controls.
Conditional policies—such as time-of-day restrictions or location-based filtering—add further security layers without compromising usability.
5. Establish Clearly Defined Approval Chains
Effective governance thrives on clarity. Every Self Request should follow a well-orchestrated approval workflow, specifying who can authorize access and under what conditions.
Whether the approver is a project owner, a system administrator, or a security lead, the process should be transparent and traceable—supporting audit-readiness and accountability.
A successful Contractor Self Request model balances agility with oversight. When underpinned by these best practices, organizations not only streamline third-party access but also elevate their overall access governance maturity.
8. Preventing Access Risks and Ensuring Regulatory Compliance
Even the most sophisticated access request workflows can expose the enterprise to risk if not governed thoughtfully. For contractors, whose roles and durations often differ from full-time employees, access can become a compliance liability if not precisely managed.
This is where strategic automation, continuous oversight, and IGA alignment converge.
Avoiding Orphaned and Overprivileged Accounts
Imagine a contractor hired to renovate a department—once their job is done, the site access badge should be deactivated. But what if it isn’t? In digital terms, this is an orphaned account—a dormant credential still capable of entry.
Or worse, imagine that same contractor was given building-wide access instead of being limited to their specific floor. That’s overprovisioning—and it’s just as dangerous in an IT environment.
Without proper checks, both scenarios can become a gateway to internal threats or external breaches. This is why Just-in-Time Access Requests paired with expiration policies and User Access Reviews are critical components of risk mitigation.
Maintaining Access Appropriateness Over Time
Roles change, contracts extend, and systems evolve. What was appropriate access yesterday may be excessive today. By embedding contractor access into a broader Identity Governance and Administration (IGA) strategy—complete with recertification campaigns and policy enforcement—you ensure access remains aligned with current responsibilities.
Scheduled access certifications should be conducted not just for employees, but for all third-party identities across the board.
Meeting Regulatory Standards with Confidence
Whether you’re navigating SOX, HIPAA, GDPR, or ISO 27001, one constant remains: auditors want traceability, clarity, and control. Every Self Request, whether made by a contractor or through Employee Self Request channels, must be logged, reviewed, and governed with precision.
Identity Access Management (IAM) platforms that support comprehensive audit trails, granular role assignments, and dynamic access policies make it significantly easier to demonstrate compliance. In addition, Emergency Access Requests—which often carry elevated risk—should be time-bound and fully documented to satisfy regulatory scrutiny.
Ultimately, regulatory compliance isn’t just about checking boxes. It’s about building a culture of accountability, supported by systems that prioritize visibility, review, and appropriate access at every step.
9. Contractor Self Request vs. Traditional Provisioning: A Paradigm Shift in Access Management
For decades, provisioning access for contractors was a manual, ticket-based chore—email threads, approval delays, IT bottlenecks. But in today’s fast-paced digital enterprise, that model no longer scales. Organizations now need a nimble, secure, and auditable alternative.
Enter Contractor Self Request—a modern, policy-driven approach that transforms how third-party users gain access, while aligning with broader Identity Access Management (IAM) and Identity Governance and Administration (IGA) objectives.
Let’s break down the contrast:
| Feature | Traditional Provisioning | Contractor Self Request |
| Speed | Manual, delayed by approvals | Instant, automated through workflows |
| Risk | High – prone to human error | Lower – governed by pre-set policies |
| Audit Trail | Often fragmented or missing | Comprehensive, system-generated logs |
| Compliance Readiness | Difficult to enforce consistently | Built-in through governance integration |
| Scalability | Limited | Designed for dynamic contractor access |
Real-World Analogy: The Old vs. the New
Think of traditional provisioning like checking into a hotel by walking to the front desk, waiting in line, filling out paperwork, and waiting for a manual room assignment.
Now, imagine instead that you’ve already checked in via app, selected your room, and received a digital key—all before arriving. That’s the Contractor Self Request approach: fast, secure, governed, and traceable.
Incorporating Access Request workflows into your IGA platform not only reduces administrative strain but also ensures that Just in Time Access Requests and Employee Off-Boarding processes are enforced with surgical precision. The result? Contractors get what they need—no more, no less—while your enterprise remains audit-ready and in control.
10. How Contractor Self Request Integrates with IGA Modules
To fully unlock the value of Contractor Self Request, it must be woven into the core fabric of your Identity Governance and Administration (IGA) strategy—not implemented as a siloed feature, but as an orchestrated component across identity lifecycle stages.
Much like how a well-run airport ensures every passenger goes through check-in, security, and boarding in a coordinated flow, Contractor Self Request must travel through key IGA checkpoints to ensure consistency, compliance, and control.
1. Identity Lifecycle Management
From Employee Onboarding to Contractor Off-Boarding, lifecycle management defines who gets access, when, and for how long. Contractor Self Request can be triggered as part of onboarding events—integrating with HRMS or third-party identity stores—to ensure access is role-aligned and time-bound from day one.
2. Access Requests & Approvals
This is where the self-service experience comes alive. Contractors initiate access through an intuitive portal. Rules baked into the IGA system determine what’s requestable, whether it’s a Just in Time Access Request, an Emergency Access Request, or a limited-scope role. Approvals are automated, multi-tiered, and policy-driven—ensuring governance without slowing down operations.
3. Access Reviews & Certifications
No access should be perpetual. Periodic User Access Reviews allow stakeholders to validate whether contractors still need the access they were granted. These reviews, automated and audit-ready, ensure that any deviations from the principle of least privilege are swiftly corrected.
4. Policy Enforcement & Segregation of Duties (SoD)
Whether preventing conflicts of interest or enforcing compliance, IGA’s policy engine ensures that Self Requests don’t compromise organizational boundaries. For example, a contractor should never have simultaneous access to development and production environments. With SoD controls, such violations can be flagged—or blocked outright—during the request process.
By aligning Contractor Self Request with these IGA modules, enterprises achieve a unified, secure, and scalable access ecosystem—where governance is embedded, not bolted on.
11. How SecurEnds Supports Contractor Self Request
Implementing an effective Contractor Self Request capability demands more than just theory—it requires a platform equipped to automate, govern, and audit third-party access with precision. This is where SecurEnds excels as a comprehensive Identity Governance and Administration (IGA) solution tailored for today’s complex access landscapes.
Self-Service Access Request Interface
SecurEnds provides contractors with an intuitive, user-friendly portal to submit access requests autonomously. This not only streamlines workflows but empowers contractors to request exactly what they need—no more, no less—supporting the principle of least privilege from the outset.
Workflow Automation for Third-Party Access
Behind the scenes, SecurEnds orchestrates automated, policy-driven approval workflows that align with corporate governance. Whether handling routine Just in Time Access Requests or time-sensitive Emergency Access Requests, the platform ensures all approvals are auditable and compliant.
Time-Bound and Policy-Controlled Access
Access granted via SecurEnds is inherently temporary and governed by predefined policies. This ensures contractor access automatically expires as per contractual timelines or project completion, mitigating risks associated with orphaned or overprivileged accounts.
Access Certification & Audit Reports
SecurEnds simplifies User Access Reviews and recertification campaigns, offering detailed audit trails and compliance reports. This not only facilitates internal governance but satisfies regulatory demands under standards such as SOX, HIPAA, GDPR, and ISO 27001.
Integration with Enterprise Systems
To ensure seamless identity lifecycle management, SecurEnds integrates effortlessly with widely used platforms such as Active Directory, Okta, Azure AD, and Workday. This connectivity allows synchronization of contractor identities, streamlining onboarding, off-boarding, and access provisioning workflows.
By leveraging SecurEnds, enterprises can confidently automate contractor access requests within a secure, governed framework—accelerating onboarding while maintaining robust compliance and visibility.
12. Conclusion
Today’s enterprises operate in a world where agility and security must go hand in hand—especially when it comes to third-party access. Contractors, vendors, and consultants are vital to business success, but their access introduces significant governance challenges that cannot be ignored.
Contractor Self Request within an advanced Identity Governance and Administration (IGA) framework offers a smart, scalable way to meet these challenges. By automating access requests, enabling Just in Time Access, and enforcing policy-driven approvals, organizations can grant contractors the access they need—precisely when they need it—without sacrificing control or compliance.
This approach transforms the traditional slow, manual provisioning process into an efficient, risk-mitigated workflow. With continuous User Access Reviews and detailed audit trails, enterprises maintain visibility and meet regulatory requirements with confidence.
Integrating contractor access into the broader Identity Access Management (IAM) lifecycle—from Employee Onboarding to Employee Off-Boarding—ensures seamless governance and reduces the risk of orphaned or excessive privileges.
In a landscape where both speed and security are non-negotiable, embracing Contractor Self Request automation is more than a best practice—it’s a strategic necessity. Platforms like SecurEnds empower organizations to strike the right balance, unlocking business agility while safeguarding critical assets.


