User Access Reviews: A Step-by-Step Guide, Best Practices, Checklist, Process and Compliance
User Access Reviews: A Step-by-Step Guide, Best Practices, Checklist, Process and Compliance
Author – Kumar Jandayala
Head of Product at SecurEnds, driving modular IGA capabilities such as access reviews and provisioning.

TL;DR: What Are User Access Reviews?
What it is:
A user access review (UAR) is a structured, recurring security and compliance process used to verify that every user has the minimum necessary access to systems, data, and applications based on their current role. It helps enforce the principle of least privilege and prevents privilege creep.
Why it matters:
User access reviews reduce insider risk, detect unauthorized or outdated permissions, and support compliance with regulatory standards like Sarbanes–Oxley Act (SOX), Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), and ISO/IEC 27001. Regular reviews strengthen both IAM and IGA programs.
How it works:
The process includes:
-
Identifying critical systems and sensitive data repositories.
-
Extracting entitlement and identity data.
-
Assigning access reviews to managers or system owners.
-
Validating each user’s access against their job responsibilities.
-
Revoking unnecessary access and logging all actions for audits.
Best practices:
-
Automate data collection and review workflows to reduce errors and manual effort.
-
Define clear ownership and accountability for each access decision.
-
Use risk-based prioritization to focus on high-impact systems first.
-
Schedule reviews on a recurring cadence and maintain a complete audit trail.
Imagine this: It’s 6:45 p.m. on a Friday, and the office is quiet. Your team has logged off. But somewhere in your system, an account belonging to a former employee, still has access to sensitive financial data. No one notices. No alarms go off. Until Monday morning, when that dormant access turns into a data breach.
This isn’t a rare story. It’s happening more often than we’d like to admit. In October 2026, businesses rely on hundreds of applications and platforms. Each of these holds pieces of sensitive customer, financial, or operational data. And when you don’t know who has access to what, you’re leaving the door wide open for a cyber disaster.
That’s where user access reviews step in. They’re not just a security checkbox—they’re your frontline defense. Done right, a solid user access review policy can protect your company from privilege creep, insider threats, compliance fines, and human error.
In this guide, we’ll walk you through everything from what a user access review is to how to automate the entire access review process with modern user access review software. With clear steps, real-world insights, and a user access review checklist, we’ll help you build smarter reviews that improve security and make audits less painful.
What Is a User Access Review?
A user access review is a structured process where organizations examine who has access to what—and decide whether that access is still necessary. It’s not just about identifying who has admin rights. It’s about aligning permissions with roles, responsibilities, and real-world usage.
User Access Review Process
Imagine a third-party contractor who wrapped up a project months ago — but their credentials are still live. That’s not just an oversight; it’s a ticking time bomb.
A structured, well-governed User Access Review (UAR) process ensures these issues are identified and resolved before they escalate into incidents. It aligns your workforce access with current roles, strengthens your IAM/IGA posture, and ensures ongoing compliance with frameworks like Sarbanes–Oxley Act (SOX), Health Insurance Portability and Accountability Act (HIPAA), and General Data Protection Regulation (GDPR).
Step 1: Build a Clear Review Framework
Every effective access review starts with structure.
This means defining:
-
Scope: List all systems and applications (on-prem and cloud), including third-party integrations.
-
Objectives: Clarify your security, compliance, and operational goals.
-
Stakeholders: Identify reviewers — typically IT, Security, Department Heads, HR, and sometimes external auditors.
-
Timeline: Schedule realistic milestones based on regulatory deadlines or internal policy.
A solid framework ensures nothing slips through the cracks — and every stakeholder knows their role in the process.
Step 2: Collect and Correlate Access Data
Access data lives in many places — HR systems, directories, applications, and SaaS tools. To get an accurate picture:
-
Inventory all users, their roles, and permissions.
-
Correlate identities to accounts (e.g., one person might have multiple login IDs across systems).
-
Ingest data automatically wherever possible to reduce manual work and error rates.
SecurEnds automates this step with flex connectors, bringing data from both connected and disconnected systems into a centralized dashboard — ready for review.
Step 3: Verify and Validate Access
This is the heart of the UAR.
Here, you assess whether the current access each user has is appropriate based on their job function, department, and regulatory scope.
Common checks include:
-
Privilege creep: Has a user accumulated more access than they need?
-
Shadow admin accounts: Are there users with hidden elevated privileges?
-
Orphaned accounts: Are there active accounts tied to inactive or terminated identities?
-
Temporary vs permanent access: Are temporary permissions still lingering?
Best practice: Apply the principle of least privilege and align access with role-based access control (RBAC) or access control matrices to simplify enforcement.
Step 4: Take Action — Revoke, Remediate, Realign
Once violations or misalignments are detected, access must be adjusted:
-
Revoke orphaned and excessive access immediately.
-
Reclassify roles where permissions exceed current responsibilities.
-
Convert unnecessary permanent access into temporary, time-bound access (e.g., JIT access).
-
Document the reviewer, action, and timestamp for audit evidence.
SecurEnds streamlines remediation through automated workflows — enabling manager or app-owner signoffs, real-time notifications, and change tracking in a single place.
Step 5: Document and Report for Compliance
Every review should leave behind a clear audit trail.
This includes:
-
Systems reviewed
-
Reviewer identity and decision
-
Actions taken (approval/revocation/modification)
-
Justification and supporting notes
A centralized log supports external audits, internal reporting, and continuous improvement. It also ensures regulatory compliance without the last-minute scramble during audit season.
SecurEnds automatically captures these details, generating ready-to-share compliance reports for SOX, HIPAA, GDPR, and other frameworks.
Step 6: Formalize Review Cycles
Access reviews aren’t one-time exercises. They should be:
-
Quarterly or monthly for privileged accounts and critical systems.
-
Annual or semi-annual for standard user accounts.
-
Triggered ad hoc during major organizational changes (M&A, layoffs, compliance shifts).
By establishing a repeatable review cadence, organizations maintain continuous alignment between user access and business reality — not just compliance checkboxes.
Step 7: Automate Wherever Possible
Manual reviews are slow, error-prone, and hard to scale. Automation:
-
Reduces time spent collecting and correlating data.
-
Ensures accurate, near real-time visibility.
-
Eliminates spreadsheet chaos.
-
Creates immutable proof of compliance with e-signature approvals.
SecurEnds’ UAR platform was built for this. With dynamic connectors, flexible scheduling, heartbeat identity tracking, and centralized dashboards, security teams can cut review effort drastically while increasing coverage and audit-readiness.
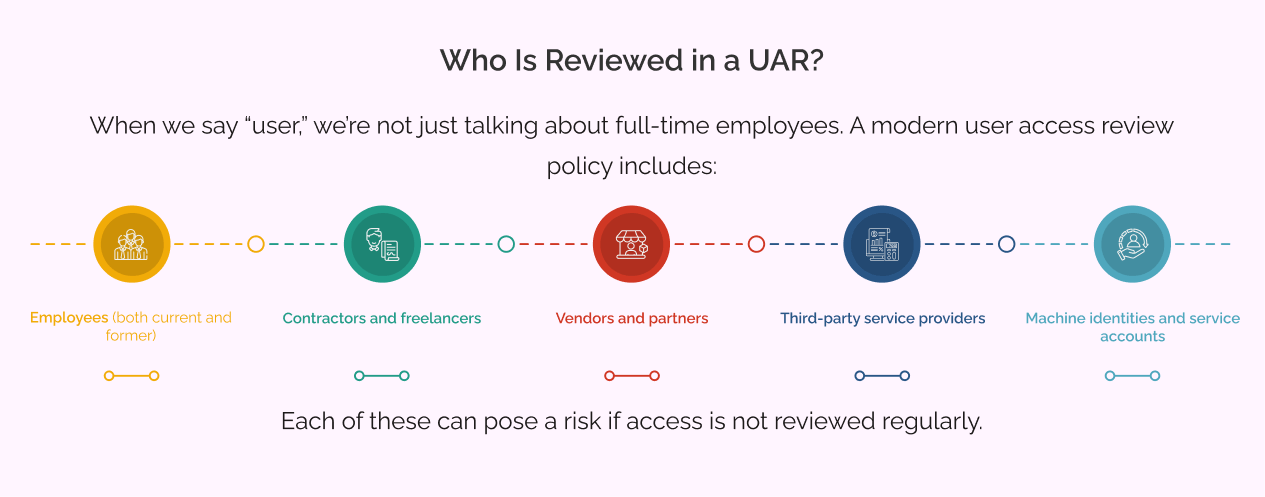
Who Is Reviewed in a User Access Review?
A access review is not only about checking employee accounts. In modern organizations, many different people and even systems can connect to company resources. That is why the review must include every identity that can log in or access any part of your environment.
1. Employees (Current and Former)
Current employees often gain extra access as they move between roles or teams. Over time this can create unnoticed security gaps.
Former employees should have their access removed quickly after leaving. Old accounts are a common way attackers find their way into a system.
2. Contractors and Freelancers
Temporary workers often receive special access for a short period. If their accounts are not cleaned up after their work is finished, they can become weak spots that attackers can exploit.
3. Vendors and Partners
Business partners often use shared tools or connect through APIs. Since they are outside your company, their permissions can be missed during regular checks. Including them in reviews helps close these security gaps.
4. Third Party Service Providers
External service providers and support teams often have access to sensitive systems. Their access should be carefully checked and removed once their job is complete.
5. Machine Identities and Service Accounts
Not all accounts belong to people. Many belong to applications, bots or automated services. These accounts often have powerful and long term access. If they are not reviewed regularly, they can become serious security risks.
A Quick Example: When Access Isn’t Revoked in Time
Let’s say a nurse at a private hospital resigns. Weeks later, an IT audit discovers she still has access to patient records through the electronic health system. That’s not just a privacy risk—it’s a compliance violation under HIPAA.
A simple UAR template—run monthly or quarterly—could have caught and resolved this long before an auditor did.
Why Are User Access Reviews Important?
Think of your organization’s systems like a massive hotel. Every employee, contractor, and vendor holds a key. Some have access to the lobby. Others—like finance or IT—can enter vaults, private offices, or even server rooms. But what happens when someone quits and their key still works?
That’s how privilege creep begins. Over time, users collect access they no longer need. Maybe they’ve changed roles. Maybe they’ve left. Maybe someone forgot to remove their admin rights. It seems harmless—until it isn’t.
In 2024 alone, over 90% of organizations experienced at least one identity-related incident, according to the Identity Defined Security Alliance. Many of these incidents could have been prevented with regular user access audits and identity access assessments. Conducting thorough access entitlement reviews helps organizations ensure that every account and system access is properly monitored and secured.
Let’s break down why these reviews matter so much:
1. They Stop Unauthorized Access Before It Starts
Without a routine user access review audit, it’s hard to spot users who have too much access—or access they shouldn’t have at all. These gaps become goldmines for bad actors, especially when credentials get compromised.
Access management reviews give you a way to catch the risk before it turns into a headline.
2. They Support Regulatory Compliance
If your business handles financial records, personal health info, or customer data, compliance isn’t optional. Regulations like SOX, HIPAA, GDPR, and ISO 27001 all mandate regular user access reviews.
Failing to follow a clear user access audit policy could lead to massive fines, lawsuits, or a loss of customer trust. Regular access entitlement checks and identity access assessments help organizations stay compliant and reduce the risk of unauthorized access.
3. They Prevent Privilege Creep
Over time, employees change jobs or take on new projects. If you don’t regularly review their access, they could end up with rights that no longer match their responsibilities.
User access audits ensure that every account only has the access it needs—no more, no less. By performing regular access entitlement reviews and identity access assessments, organizations can minimize the risk of privilege misuse and maintain strong security controls.
4. They Reduce Insider Threats
Sometimes the threat isn’t from the outside. It’s from someone who already has access. Insider breaches—whether malicious or accidental—are some of the costliest. A UAR checklist helps identify risky accounts before they become incidents.
5. They Make Audits (Much) Easier
Ever scrambled to pull access logs for an external audit? Manual audits drain your team’s time. Automated user access review software not only reduces your workload but also keeps a record of every review, decision, and change for full traceability.
How User Access Reviews Support Major Compliance Frameworks
Most compliance failures don’t happen because policies are missing. They happen because access is not properly reviewed or removed when people change roles, leave the company, or when vendor engagements end. This is exactly why almost every major security and privacy framework requires regular user access audits and identity access assessments..
Auditors want proof that the organization knows who has access, why they have it, and how that access is controlled over time. UARs provide that proof.
How UARs Support Key Regulations and Standards
-
Sarbanes–Oxley Act (SOX)
SOX focuses on protecting the integrity of financial systems. Regular access reviews help ensure only authorized personnel can access accounting platforms and financial data, which reduces fraud risk and supports clean financial reporting. -
Health Insurance Portability and Accountability Act (HIPAA)
Healthcare organizations must tightly control access to patient information. UARs help catch old or excessive permissions, ensuring compliance with the Security Rule and reducing the risk of data breaches. -
General Data Protection Regulation (GDPR)
GDPR Article 32 requires organizations to enforce strict access controls. Regular reviews ensure employees and third parties have only the minimum access needed, protecting personal data and preventing unauthorized use. -
ISO/IEC 27001
Clause A.9.2.5 mandates periodic reviews of user access rights. UARs help keep permissions aligned with job roles and make audit reporting straightforward. -
National Institute of Standards and Technology Special Publication 800-53
AC-2 and AC-5 controls require regular account management and reviews. Without UARs, proving compliance with these controls is difficult and risky. -
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS clearly states that only people who need cardholder data can access it. UARs provide the evidence trail that shows how access is granted, reviewed, and revoked. -
System and Organization Controls 2 (SOC 2)
SOC 2 focuses on security, availability, and confidentiality. Access reviews help demonstrate strong internal controls, which auditors require during assessments.
In addition, frameworks like CIS, CJIS, CMMC, Cyber Essentials, FTC Safeguards Rule, CCPA, FedRAMP, and NYDFS also highlight the importance of periodic access reviews to maintain compliance and security hygiene.
How User Access Reviews Improve Security & Compliance
Let’s rewind to 2023.
A major tech company suffered a breach—not because of an outsider breaking in, but because a former employee still had access to critical systems. It cost millions. Not in just fines or recovery costs—but in lost trust.
User access audits are designed to prevent exactly that. By conducting access entitlement reviews and identity access assessments, organizations can ensure that only the right people have access to the right resources at the right time.
Think of UARs as Digital Housekeeping
Over time, people move, roles evolve, projects end, and systems expand. But if access doesn’t change with those shifts, your environment becomes cluttered with outdated permissions.
This clutter isn’t harmless.
It becomes the perfect hiding place for insider threats, dormant accounts, and accidental data leaks.
A clean, consistent user access policy helps eliminate those blind spots. It’s like closing windows in a storm—you don’t wait until the rain pours in.
Benefits of Regular Access Reviews
Here’s how regular user access reviews make a direct impact:
1. Prevents Unauthorized Access
Roles change. People leave. But if their access doesn’t reflect that, your systems stay exposed.
A structured access review process ensures users have just enough access—not more, not less. This reduces privilege creep, minimizes your attack surface, and ensures only the right eyes see sensitive information.
2. Helps Meet Compliance Requirements
Regulations like SOX, HIPAA, and GDPR demand that organizations demonstrate control over user access. That means periodic reviews, documented decisions, and audit trails.
A user access audit provides the proof auditors need. Regular access entitlement reviews and identity access assessments create a clear record showing that every account and permission has been properly evaluated and managed. Miss a review, and you’re not just non-compliant—you’re risking six-figure fines or worse.
3. Supports Least Privilege Access
The principle of least privilege (PoLP) means giving users only the permissions they need. No more, no less.
Without regular access management reviews, it’s nearly impossible to enforce PoLP in growing teams.
UAR act as checkpoints to realign permissions with actual business needs.
4. Catches Insider Threats Early
Sometimes, the biggest risk isn’t from the outside.
A 2023 IBM report noted that insider threats cost companies over $11 million per incident on average.
Regular user access audits identify excessive or unnecessary access—before it’s misused, whether intentionally or accidentally.
5. Reduces “Access Debt”
Just like technical debt, access debt piles up when old permissions aren’t cleaned up. Dormant accounts, unused entitlements, forgotten admin privileges—all add risk.
A consistent access review process clears out the clutter and strengthens your security foundation.
How Often Should You Conduct User Access Reviews?
The frequency of user access audits isn’t one-size-fits-all—it depends on your business size, industry, and the sensitivity of the data your users handle. But here’s a truth you can’t ignore: the longer you wait, the bigger the risk.
Let’s break it down.
Why Frequency Matters
Think of your access review like locking the doors at night. You don’t check the locks once a year—you do it regularly to avoid surprises. The same logic applies to reviewing access to your systems.
Employees change roles, contractors come and go, and systems evolve. If you don’t keep up, your environment becomes a maze of outdated permissions. That’s how unauthorized access and security gaps start.
Recommended Frequency by Compliance & Risk
| Review Frequency | Best For | Why It’s Needed |
| Quarterly | Finance, Healthcare, Government | Ensures timely revocation of access and supports SOX user access review audits. |
| Semi-Annually | Medium-risk industries like SaaS, Retail | Balances security needs with operational overhead. |
| Annually | Small businesses or low-sensitivity data | Basic compliance hygiene, but not ideal for dynamic environments. |
| Trigger-Based | Any industry | Conducted after role changes, offboarding, or a security incident. |
Regulatory Expectations
- SOX: Requires quarterly or bi-annual access reviews for financial reporting systems.
- HIPAA: Recommends routine reviews to restrict access to protected health information (PHI).
- GDPR: Expects ongoing reviews to ensure that only authorized users handle personal data.
- ISO 27001: Requires periodic reviews as part of an overall access management review policy.
According to a Statista report, companies that perform UAR Audits quarterly report 40% fewer access-related incidents than those doing it annually.
Pro Tip:
If your organization handles sensitive data, opts for zero-trust security, or has high staff turnover, lean toward more frequent access reviews—not less.
Step-by-Step: How to Conduct a User Access Review
If you’ve never done a access review before—or if you’re trying to make yours more effective—this step-by-step guide is a good place to start.
Each step helps you spot unnecessary access, protect sensitive data, and stay compliant with regulations like SOX, HIPAA, or GDPR.
Step 1: Identify the Systems That Need Reviewing
Start by listing out every tool, system, or platform where users have access—like cloud apps, databases, financial systems, HR tools, or internal portals. Don’t forget third-party apps and shared drives.
Step 2: Gather User Access Data
Pull a report of who has access to what. This includes user names, roles, departments, and permission levels (e.g., read, write, admin). If you use tools like Active Directory or Okta, this step can be automated.
Step 3: Review Permissions Against Job Roles
Check if each user actually needs the access they’ve been given. If someone changed roles or no longer uses the app, their access should be reduced or removed. This helps prevent privilege creep.
Establish a clear User Access Review Policy that defines ownership, scope, and review frequency.Build a consistent governance framework that meets audit and regulatory demands.
Step 4: Revoke or Adjust Access Where Needed
If you find users with unnecessary access, update their permissions right away. This is where automation tools can help. Many user access review software platforms allow you to modify or revoke access with just a few clicks.
Step 5: Document Everything
Keep records of who was reviewed, what access they had, what changes were made, and who approved them. This is important for compliance audits and internal governance.
Step 6: Repeat Regularly
Set a schedule for reviews (quarterly, semi-annually, or annually depending on your business). Don’t let this be a one-time task. Regular access review processes keep your systems secure and compliant.
Common Challenges in Manual User Access Reviews
Doing access reviews manually might seem manageable at first—especially if your company is small. But as your business grows, so does the number of users, tools, and systems. That’s where things start to get messy.
Here are some of the most common problems companies face when reviews are done the old-fashioned way:
1. It Takes Too Much Time
Manually pulling access data from spreadsheets, emails, or different admin dashboards can take hours—or even days. Multiply that by the number of systems you have, and it’s easy to see how time-consuming it becomes.
According to industry reports, teams spend up to 48 hours per review cycle when they don’t use access review software.
2. Human Errors Are Inevitable
Let’s be honest: it’s easy to miss something when you’re juggling dozens of users across multiple systems. You might forget to revoke access for a former employee or accidentally keep admin privileges for someone who no longer needs them.
These errors may seem small, but they open the door to security risks, non-compliance, and even data breaches.
3. Too Many Systems, Not Enough Visibility
Your marketing team uses HubSpot, your finance team uses NetSuite, and your IT team uses AWS. Each tool has its own way of managing access—and not all of them talk to each other.
Without a centralized access management review system, you’re left piecing together fragmented data to figure out who has what. It’s inefficient and error-prone.
4. Delayed Responses = Delayed Security
When someone changes roles or leaves the company, their access needs to be updated immediately. But with manual reviews, there’s often a lag. And that lag can mean unauthorized access lingers longer than it should.
In regulated industries, that kind of delay can lead to failed audits and serious fines.
5. Poor Documentation Hurts Compliance
Regulations like SOX, HIPAA, and GDPR require organizations to keep detailed records of their user access audits. But with manual reviews, maintaining a clean audit trail can be a nightmare.
You need to track who reviewed the access, what they found, what changes were made, and when everything happened.
Without automated tracking or a clear UAR checklist, you’re flying blind.
Bottom Line: Manual reviews are not just slow—they’re risky. If you want to reduce errors, save time, and stay audit-ready, it’s time to look into automated access review tools.
Bonus: Built-In Intelligence
SecureEnds isn’t just rule-based — it learns. Using AI, it understands usage patterns and flags unusual behavior.
Example?
If someone in Sales suddenly gets access to financial reporting tools, it triggers an alert.
Now you’re not just compliant — you’re proactive.
Your User Access Review Checklist & Template
What to check. What to fix. What to log.
Even with automation, every access review still needs human accountability. That’s where a simple, structured UAR checklist makes a big difference.
Think of it as your map. Whether you’re running a quarterly access management review or prepping for a SOX audit — this ensures nothing falls through the cracks.Use our User Access Review checklist to ensure every step of your audit is covered.
This resource helps you validate permissions, document actions, and stay audit-ready.
✅ The Ultimate User Access Review Checklist
- Define Your Scope
- Which systems are in scope? (Think: HRIS, CRM, databases, finance tools)
- Are third-party vendors and contractors included?
- Which systems are in scope? (Think: HRIS, CRM, databases, finance tools)
- Determine Review Frequency
- High-risk systems: Monthly or Quarterly
- Lower-risk systems: Semi-annually or Annually
(Read: How Often Should You Conduct User Access Reviews?)
- High-risk systems: Monthly or Quarterly
- Gather User Access Data
- Pull active user lists from IAM tools (e.g., Active Directory, Okta, Azure AD)
- Export access logs, permission levels, and role assignments
- Pull active user lists from IAM tools (e.g., Active Directory, Okta, Azure AD)
- Validate Active vs. Inactive Users
- Spot orphaned accounts
- Reconcile with HR data (exits, leaves, transfers)
- Spot orphaned accounts
- Check for Excessive or Outdated Privileges
- Review role alignment with current job duties
- Look for users with admin access they don’t need
- Review role alignment with current job duties
- Flag Segregation of Duties (SoD) Risks
- Ensure no one has conflicting roles (e.g., request + approve transactions)
- Review Shared, Service, and Machine Accounts
- Ensure these follow your user access review policy
- Are their access levels justified and secured?
- Ensure these follow your user access review policy
- Revoke or Modify Access as Needed
- Remove old, risky, or excessive permissions
- Downgrade users with privilege creep
- Remove old, risky, or excessive permissions
- Log Reviewer Actions
- Who approved/revoked what
- Reviewer comments and timestamps
- Who approved/revoked what
- Generate Audit Reports
- SOX user access review logs
- GDPR/HIPAA access review history
- Proof of adherence to user access review audit standards
- Download the user access review template
💡 Pro Tip: You can automate this entire process using SecureEnds access review software, including checklist workflows, task assignments, and compliance logs — without touching a spreadsheet.
Download a practical Access Review template to streamline reviews and reporting.
Simplify recurring access audits with pre-built formats designed for compliance teams.
Best Practices for Conducting User Access Reviews Efficiently
Let’s be real—UAR can feel overwhelming. But with the right practices in place, they can become a streamlined, reliable process that boosts security and keeps you compliant.
Here are some proven best practices to make your UAR process efficient, accurate, and audit-ready:
1. Set a Clear User Access Review Policy
Start with a written UAR policy that outlines:
- How often access reviews should happen (e.g. quarterly or bi-annually).
- Who’s responsible for reviewing each system (IT, HR, department heads).
- What needs to be reviewed (systems, apps, cloud tools, files, etc.).
- What to do next (approve, revoke, or adjust access).
This sets expectations, eliminates confusion, and makes the whole access management review process smoother for everyone involved.
2. Prioritize High-Risk Accounts
Not all access is created equal. Focus your attention where the stakes are higher:
- Admin-level accounts
- Finance and payroll systems
- Cloud infrastructure (AWS, Azure, GCP)
- Any account that touches customer data or intellectual property
Risk-based reviews help you act fast where it matters most.
3. Involve the Right People
The IT team can’t do this alone.
- Managers know what their team members need (and don’t need).
- HR can flag role changes or exits that require access changes.
- Compliance teams ensure that the process meets regulatory standards like SOX user access review and GDPR.
Bringing in multiple perspectives helps make better decisions.
4. Keep a Structured User Access Review Checklist
Having a consistent UAR checklist saves time and reduces mistakes. Your checklist should include:
✅ What systems are in scope
✅ Which users and roles need to be reviewed
✅ What actions should be taken (approve, revoke, modify)
✅ Notes or justifications for changes
✅ Timestamps and reviewer names
You can even use a UAR template to standardize the format.
5. Use Automation Wherever You Can
Manual reviews are slow and prone to error. With the right user access review software, you can:
- Automatically pull access data from all systems
- Send reminders to reviewers
- Flag risky or unusual access patterns
- Track every decision and action for audit readiness
Companies that automate access reviews save 70% of the time compared to those using spreadsheets.
See how automating User Access Reviews reduces manual work and errors.
Learn how automation ensures timely reviews, accurate records, and audit-ready documentation.
6. Document Everything for Audits
Whether you’re facing a user access review audit for SOX, HIPAA, or ISO 27001, detailed documentation is a must.
Keep logs of:
- Who had access
- Who reviewed it
- What was changed and why
- When it was done
Good records mean stress-free audits and faster compliance reporting.
By following these best practices, your access review process becomes a proactive part of your security strategy—not just a compliance checkbox.
What Is User Access Review Software (and Why SecureEnds Is Built for It)
Still tracking user access in spreadsheets? Still emailing department heads one by one during audits?
That’s exactly what UAR software is built to fix—and it’s why companies are switching to SecureEnds.
So, What Is User Access Review Software?
It’s a platform that helps you manage, monitor, and automate user access reviews across all your business systems—think cloud apps, HR software, Active Directory, databases, and more.
With SecureEnds, you can:
- Automatically gather access data across all systems
- Trigger reviews on a schedule or during job role changes
- Flag risky access instantly
- Route access certifications to the right reviewers
- Maintain a full audit trail for every decision
- Export reports for SOX access review or GDPR audits in one click
In short, SecureEnds helps you do more with less manual work.
Why SecureEnds Stands Out
SecureEnds isn’t just another access review tool. It’s built for modern, growing businesses that need scalable, smart, and simple access governance.
Real-Time Access Visibility
See who has access to what—across on-prem, cloud, SaaS, and even homegrown apps.
Automated Workflows
No more chasing people. SecureEnds sends reminders, tracks progress, and completes reviews automatically.
AI-Driven Risk Scoring
Flag inactive accounts, excessive privileges, and SoD violations before they cause damage.
Compliance Made Easy
Whether it’s a SOX user access review, HIPAA, or ISO 27001, SecureEnds gives you audit-ready reports and full traceability.
One Platform, 50+ Integrations
Connect to Okta, Azure AD, AWS, Workday, ServiceNow, and more without any custom coding.
Scales Effortlessly
From startups to global enterprises, SecureEnds adapts to your access management review needs.
The Old Way vs. SecureEnds
| Manual Access Reviews | SecureEnds UAR Software |
| Weeks of spreadsheets and chasing | Minutes with automation |
| Missed revocations and privilege creep | Real-time risk alerts and cleanup |
| Last-minute audit stress | One-click access review audit reports |
| High security risk | Continuous monitoring + role-based control |
SecureEnds also includes:
- A access review checklist to stay audit-ready
- Pre-built access review templates for repeatable success
- Custom review policies and triggers (e.g. when someone switches departments)
If your access review process feels messy, manual, or risky—it’s time to automate UAR user access reviews the SecureEnds way.
Plug and Play: SecureEnds’ Pre-Built User Access Review Connectors
Managing user access across disconnected systems can be a nightmare. That’s why SecureEnds comes equipped with a wide range of pre-built connectors—making it easy to bring all your access data into one place without custom code or long IT cycles.
These integrations are a cornerstone of identity governance and administration, allowing organizations to automate access reviews, track permissions, and enforce least privilege—across every business-critical system.
Identity & Access Management (IAM)
Effortlessly integrate with top IAM platforms to support centralized identity governance and administration:
✔ Active Directory (AD), Azure AD, AWS IAM, Okta, OneLogin, JumpCloud
Cloud & Storage
Keep access secure across all major cloud environments and storage platforms:
✔ AWS, Google Cloud, Google Drive, AWS Cloud DB & Storage
ITSM & Ticketing Systems
Trigger and manage access workflows from your helpdesk tools:
✔ ServiceNow, Zendesk, TeamDynamix, DesktopPro, Freshdesk
Collaboration & Code Repositories
Ensure access controls extend to your day-to-day and dev environments:
✔ Slack, Confluence, Jira, SharePoint, GitHub, GitLab, Bitbucket, BOX
HR, Finance & ERP Systems
Align access with real-time role and status changes from your core business systems:
✔ Workday, ADP, Paylocity, SAP SuccessFactors, NetSuite, Microsoft Dynamics, UKG, Fiserv, Jack Henry Silverlake, Ceridian Dayforce, GFX
Databases & File Transfers
Gain deep visibility and control over who accesses your data—down to the table or file:
✔ MS SQL Server, MySQL, Oracle via Flex, Postgres via Flex, DB Flex, Flex SFTP, Flex Folder
Other Key Business Applications
Extend identity governance and administration across every corner of your tech stack:
✔ Salesforce, Office 365, Docusign, Dropbox, Lawson, WebAPI, Thycotic, RPA, Symitar, Concur
No blind spots. No manual spreadsheets. No more missed audits.
With SecureEnds’ pre-built connectors and enterprise-grade integrations, you get full-spectrum identity governance and administration—delivered at scale.
How Automation Makes User Access Reviews Smarter, Faster, and Safer
Manual access reviews are like trying to find a needle in a haystack — slow, tiring, and error-prone. Automation changes everything.
With SecureEnds, you don’t just automate access reviews — you build a system that runs in the background, flags what matters, and gives you time back.
Why Manual Doesn’t Cut It Anymore
- People change roles.
- Contractors come and go.
- Access keeps getting added… but rarely cleaned up.
By the time your audit rolls around, you’re buried in spreadsheets, chasing teams for approvals, and hoping nothing critical slips through.
Now imagine a tool that does it for you.
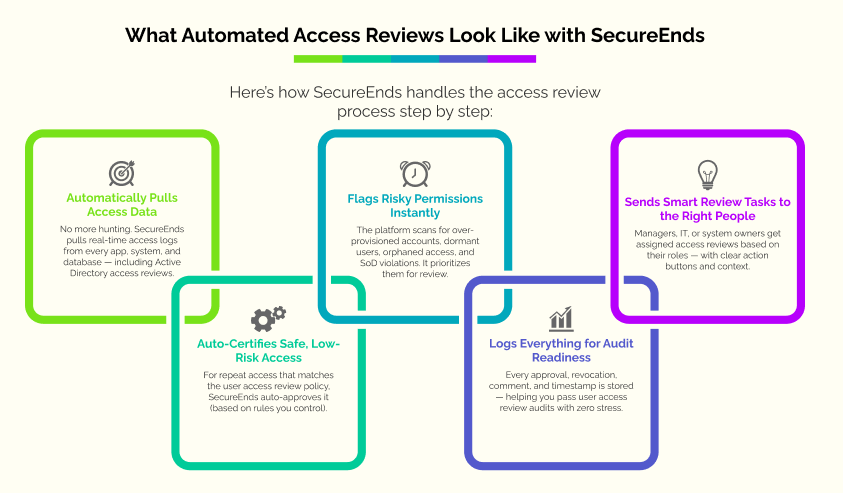
What Automated Access Reviews Look Like with SecureEnds
Here’s how SecureEnds handles the access review process step by step:
1. Automatically Pulls Access Data
No more hunting. SecureEnds pulls real-time access logs from every app, system, and database — including Active Directory access reviews.
2. Flags Risky Permissions Instantly
The platform scans for over-provisioned accounts, dormant users, orphaned access, and SoD violations. It prioritizes them for review.
3. Sends Smart Review Tasks to the Right People
Managers, IT, or system owners get assigned access reviews based on their roles — with clear action buttons and context.
4. Auto-Certifies Safe, Low-Risk Access
For repeat access that matches the access review policy, SecureEnds auto-approves it (based on rules you control).
5. Logs Everything for Audit Readiness
Every approval, revocation, comment, and timestamp is stored — helping you pass access review audits with zero stress
Explore key User Access Review best practices that keep your organization compliant.
Improve accuracy, efficiency, and governance with proven IAM and IGA strategies.

Bonus: Built-In Intelligence
SecureEnds isn’t just rule-based — it learns. Using AI, it understands usage patterns and flags unusual behavior.
Example?
If someone in Sales suddenly gets access to financial reporting tools, it triggers an alert.
Now you’re not just compliant — you’re proactive.
Your User Access Review Checklist & Template
What to check. What to fix. What to log.
Even with automation, every access review still needs human accountability. That’s where a simple, structured UAR checklist makes a big difference.
Think of it as your map. Whether you’re running a quarterly access management review or prepping for a SOX audit — this ensures nothing falls through the cracks.Use our User Access Review checklist to ensure every step of your audit is covered.
This resource helps you validate permissions, document actions, and stay audit-ready.
✅ The Ultimate User Access Review Checklist
- Define Your Scope
- Which systems are in scope? (Think: HRIS, CRM, databases, finance tools)
- Are third-party vendors and contractors included?
- Which systems are in scope? (Think: HRIS, CRM, databases, finance tools)
- Determine Review Frequency
- High-risk systems: Monthly or Quarterly
- Lower-risk systems: Semi-annually or Annually
(Read: How Often Should You Conduct User Access Reviews?)
- High-risk systems: Monthly or Quarterly
- Gather User Access Data
- Pull active user lists from IAM tools (e.g., Active Directory, Okta, Azure AD)
- Export access logs, permission levels, and role assignments
- Pull active user lists from IAM tools (e.g., Active Directory, Okta, Azure AD)
- Validate Active vs. Inactive Users
- Spot orphaned accounts
- Reconcile with HR data (exits, leaves, transfers)
- Spot orphaned accounts
- Check for Excessive or Outdated Privileges
- Review role alignment with current job duties
- Look for users with admin access they don’t need
- Review role alignment with current job duties
- Flag Segregation of Duties (SoD) Risks
- Ensure no one has conflicting roles (e.g., request + approve transactions)
- Review Shared, Service, and Machine Accounts
- Ensure these follow your user access review policy
- Are their access levels justified and secured?
- Ensure these follow your user access review policy
- Revoke or Modify Access as Needed
- Remove old, risky, or excessive permissions
- Downgrade users with privilege creep
- Remove old, risky, or excessive permissions
- Log Reviewer Actions
- Who approved/revoked what
- Reviewer comments and timestamps
- Who approved/revoked what
- Generate Audit Reports
- SOX user access review logs
- GDPR/HIPAA access review history
- Proof of adherence to user access review audit standards
- Download user access review template
💡 Pro Tip: You can automate this entire process using SecureEnds user access review software, including checklist workflows, task assignments, and compliance logs — without touching a spreadsheet.
Download a practical User Access Review template to streamline reviews and reporting.
Simplify recurring access audits with pre-built formats designed for compliance teams.
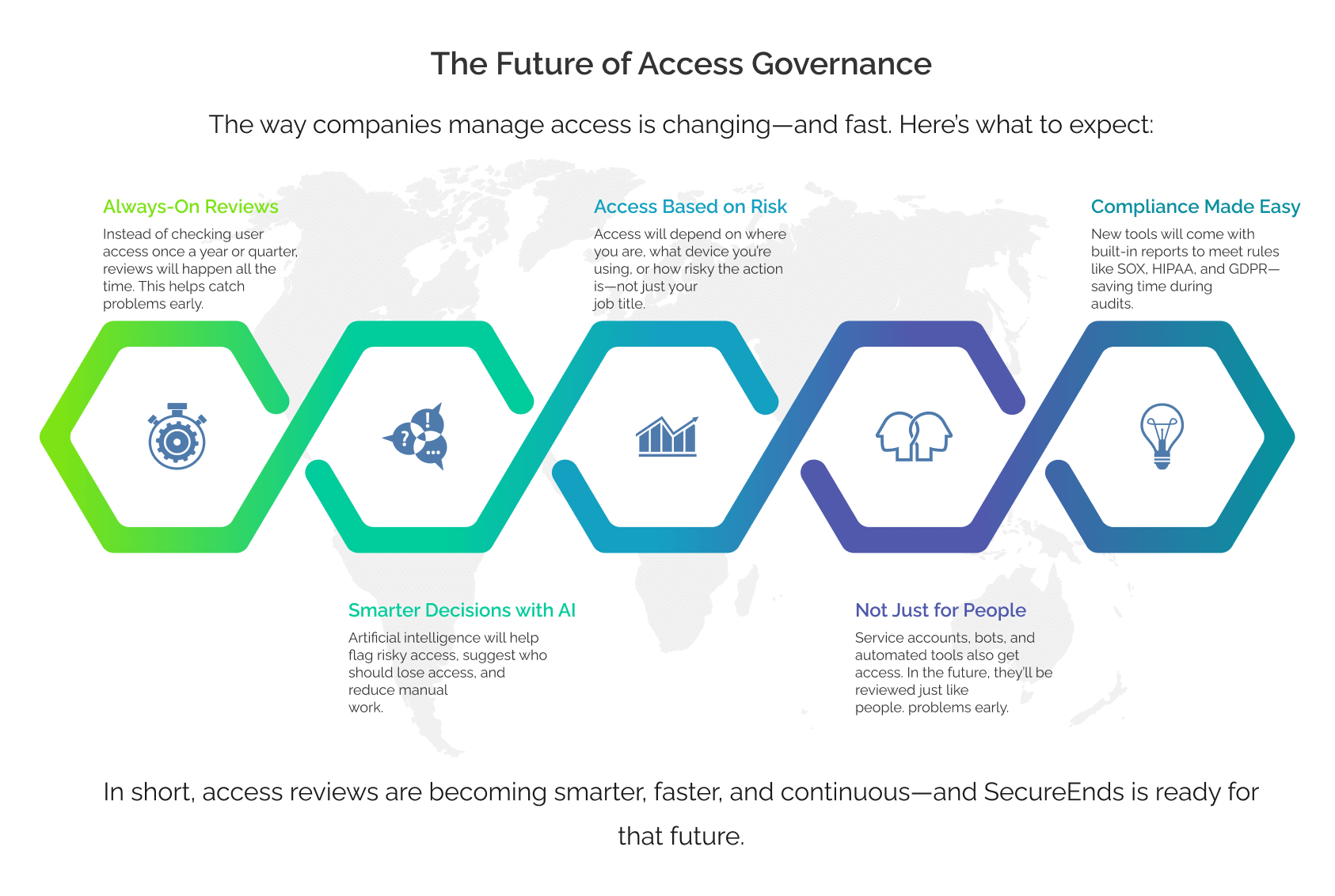
The Future of Access Governance
The way companies manage access is changing—and fast. Here’s what to expect:
Always-On Reviews
Instead of checking user access once a year or quarter, reviews will happen all the time. This helps catch problems early.
Smarter Decisions with AI
Artificial intelligence will help flag risky access, suggest who should lose access, and reduce manual work.
Access Based on Risk
Access will depend on where you are, what device you’re using, or how risky the action is—not just your job title.
Not Just for People
Service accounts, bots, and automated tools also get access. In the future, they’ll be reviewed just like people.
Compliance Made Easy
New tools will come with built-in reports to meet rules like SOX, HIPAA, and GDPR—saving time during audits.
Wrapping Up: Access Reviews That Actually Work
Let’s be real— access reviews aren’t the most exciting part of your job. But skipping them? That’s a risk no growing business can afford.
In today’s world of cloud apps, remote teams, and constant change, it’s easy for access to spiral out of control. That’s how you end up with former employees still holding onto permissions… or interns accidentally having admin rights.
A regular access review policy keeps all of that in check. It’s how you:
- Protect sensitive data from falling into the wrong hands
- Stay ahead of SOX, HIPAA, and GDPR audits
- Cut down on manual work and avoid those last-minute compliance scrambles
- Build stronger identity governance and administration practices from the ground up
And the best part? Tools like SecureEnds make it all simple. With automation, real-time alerts, and ready-to-use templates, you can run clean, consistent, and audit-ready reviews—without the spreadsheet headaches.
So if you’ve been putting off your next access review… now’s a good time to hit “Go.”
About the Author
The Head of Product at SecurEnds leads the design and delivery of the platform’s modular identity governance capabilities. With deep expertise in access reviews, segregation of duties, provisioning, and access templates, he focuses on building scalable solutions that align with industry needs. His blend of customer empathy and product vision helps organizations modernize their identity governance programs.


