Year in Review 2023: Insights, Updates, and Customer Success
Year in Review 2023: Insights, Updates, and Customer Success

As we bid farewell to another transformative year in the realm of cybersecurity, it’s time to reflect on the milestones, innovations, and achievements that have defined our journey at SecurEnds.
In this comprehensive article, we’ll delve into captivating insights, unveil the latest advancements in our products, celebrate the successes of our valued customers, and explore the evolving landscape of security in the modern day.
Join us on this exploration as we revisit the key moments that shaped our year, highlight the strides we’ve made in enhancing our solutions, and showcase the tangible impact of our commitment to security excellence. From emerging trends to groundbreaking product updates, this review encapsulates the essence of SecurEnds’ dedication to empowering organizations with robust and adaptive cybersecurity solutions.
Let’s dig in.
It all starts with user access reviews
One of the pivotal themes that resonated throughout 2023 was our commitment to empowering Chief Information Security Officers (CISOs) and security professionals with the knowledge and tools they need to navigate their user access management. A highlight in this journey was our blog post titled “Automating User Access Reviews: A CISO’s Guide,” where we delved into the critical aspects of automating this fundamental security process.
👉 Read full article – Automating User Access Reviews: A CISO’s Guide
Identity is at the heart of every data breach
Understanding the past is as crucial as preparing for the future. Our blog post “The Worst Data Breaches in History & How You Can Prevent the Next Big Security Compromise” dissected some of the most notorious data breaches that have shaped the industry. More importantly, we provided actionable insights on how organizations can fortify their defenses to prevent the next significant security compromise.

Teams need to become more efficient
Cybersecurity is not only defined by external threats but also by the internal challenges that organizations face, such as budget constraints and workforce reductions. In our blog post, “How Cybersecurity Teams Can Do More with Less Amid Budget Cuts and Layoffs,” we addressed the pressing need for efficiency and resilience in the face of economic uncertainties.

👉 Read full article – How Cybersecurity Teams Can Do More with Less Amid Budget Cuts and Layoffs
Automation is the future
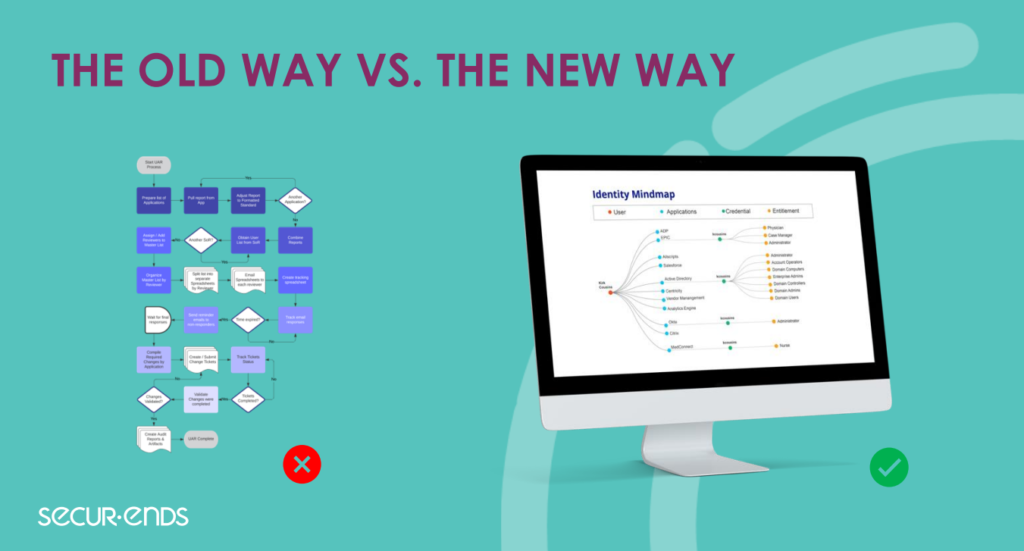
The need for precise and efficient user access management has never been more critical. Our first webinar of the year, “The Dangers of Manual User Access Reviews & How to Overcome Them,” shed light on the pitfalls associated with manual processes. Afterwards, we put together a comprehensive guide on ensuring a secure and streamlined approach to user access reviews.
New Module: Segregation of Duties
Understanding the nuances of SoD is one thing; implementing it effectively is another. Our blog post “Reducing Risk with Segregation of Duties: Best Practices, Use Cases, and Implementation” outlined best practices for organizations to follow when establishing and maintaining SoD policies. From defining clear roles and responsibilities to conducting regular audits, these best practices serve as a roadmap for organizations looking to enhance their security posture through strategic access controls.

👉 Learn more about SecurEnds Segregation of Duties Module and schedule a demo today
Offboarding can be a huge vulnerability
Offboarding, when not executed with precision, can expose organizations to heightened security risks. This blog post outlined the time-sensitive nature of the offboarding process, emphasizing the need for swift and comprehensive actions to revoke access, safeguard sensitive data, and minimize the potential for unauthorized activities.

👉 Read full article – Ensuring Fast & Secure Offboarding with Automated User Access Reviews
Identity governance is being overhauled
Identity governance is intrinsically tied to compliance, with regulations and standards continually evolving. This blog post addressed the challenges organizations face in staying compliant and provided strategies to navigate this ever-changing landscape. From continuous monitoring to real-time reporting, the best practices highlighted ways organizations can proactively address compliance requirements within their identity governance framework.

👉 Read full article – Identity Governance: Best Ways to Make Your Processes Easier & More Efficient
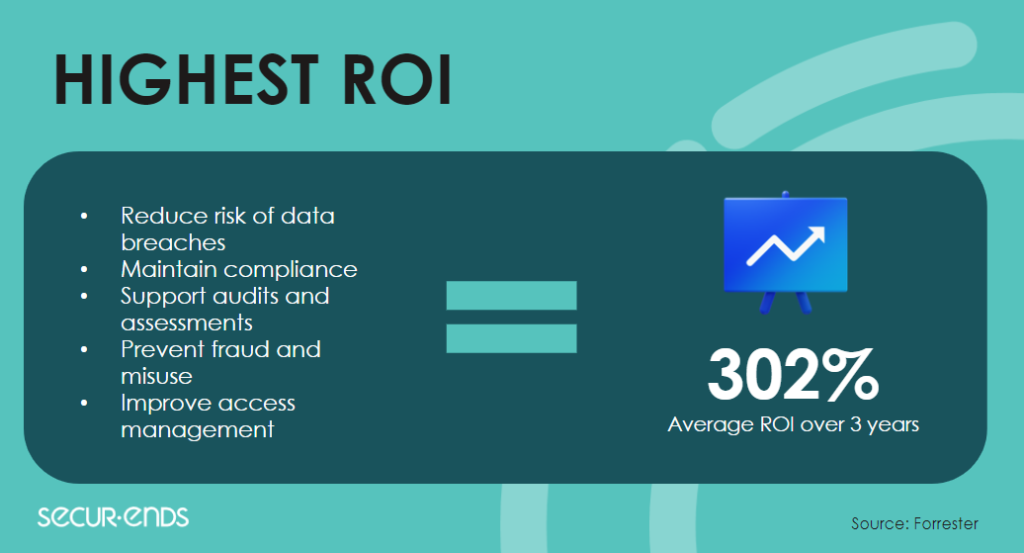
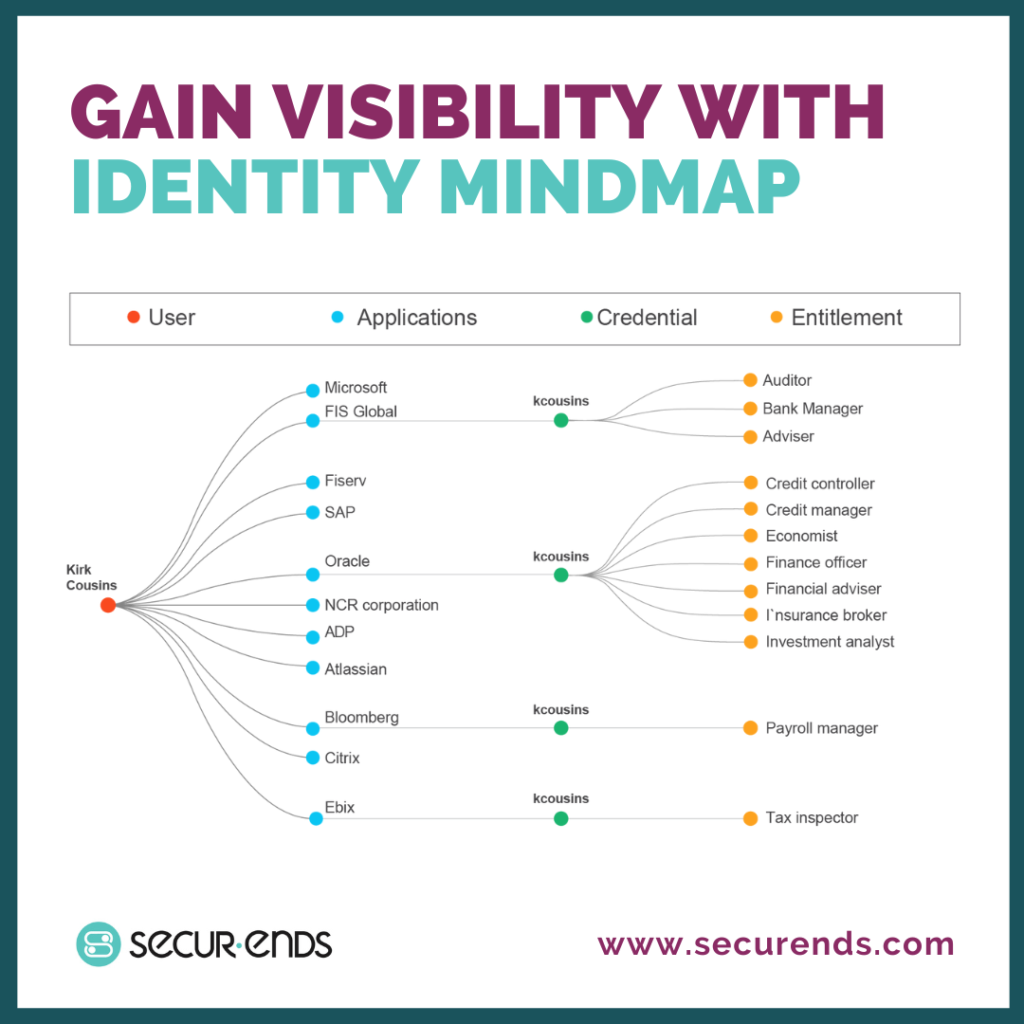
Visibility is key
Recognizing the interplay between compliance and cybersecurity, the post emphasized how adherence to regulatory standards contributes to enhanced visibility. By aligning cybersecurity practices with compliance requirements, organizations can ensure a holistic approach to security that not only prevents data breaches but also establishes a resilient defense against evolving threats.
Finance sector needs better IAM
With the sheer volume of identities and access permissions within financial organizations, manual IAM processes become impractical. This blog post delved into the significance of automation in addressing IAM challenges. By automating onboarding, offboarding, access reviews, and other critical processes, financial institutions can ensure efficiency, accuracy, and compliance.

👉 Read full article – IAM: Top Challenges Facing Banks, Credit Unions, and Financial Institutions
New Module: Access Requests & Approvals
Manual access request and approval processes often lead to bottlenecks, delays, and the potential for errors. This blog post delved into the pitfalls of relying solely on manual workflows, emphasizing the need for organizations to transition to more automated and streamlined approaches to enhance efficiency and reduce the risk of human error.

👉 Read full article – A Guide to Simplifying Access Requests & Approvals
👉 Learn more about SecurEnds Access Request Module and schedule a demo today
Customer Success Stories
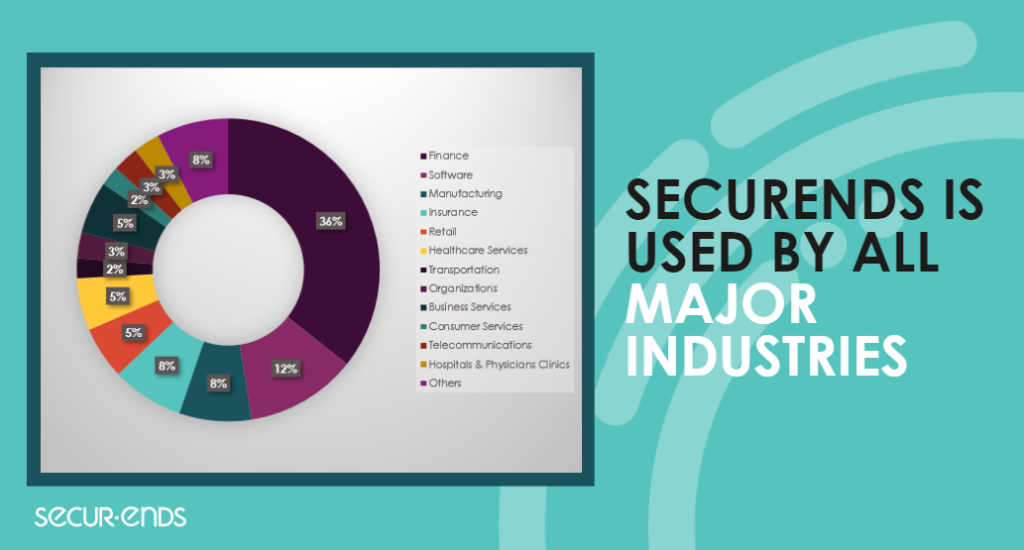
Real-world success stories speak volumes about the effectiveness of solutions. Throughout the year, SecurEnds has had the privilege of collaborating with diverse organizations across the fintech, banking, telecom, and healthcare sectors, delivering tailored solutions to meet their unique challenges. Let’s delve into the impactful case studies that showcase how SecurEnds made a difference in enhancing security, streamlining processes, and fortifying access management across these critical industries.

👉 Read full case study – Bank Rapidly Scales User Access Reviews 4X with SecurEnds
👉 Read full case study – Fintech Accelerates User Access Review Completion Time by 75%
👉 Read full case study – Leading Healthcare Provider Saves 50% in User Access Review Hours
👉 Read full case study – Telecom Leader Reduces User Access Review Cycle by 10 Weeks
Introducing the SecurEnds Webinar Series
After a year of progress, we take a moment to reflect on the invaluable insights and knowledge shared during the SecurEnds 2023 Webinar Series. Covering a spectrum of crucial cybersecurity topics, our webinars brought together industry experts, thought leaders, and professionals to explore, discuss, and provide actionable strategies.

👉 Watch Full Webinar: The Dangers of Manual Access Reviews & How to Overcome Them
👉 Watch Full Webinar: CISOs, Cybersecurity, and Compliance Teams: Automating User Access Reviews
👉 Watch Full Webinar: Solving the Visibility Problem in Identity Governance
👉 Watch Full Webinar: Reducing IT Security & Compliance Risk with Segregation of Duties
👉 Watch Full Webinar: Simplifying Access Requests & Approvals with Automation
Start 2024 with SecurEnds
As you envision the future of your organization in 2024 and beyond, make SecurEnds your partner in cybersecurity success.
Whether you’re navigating compliance challenges, fortifying your IAM strategy, or seeking innovative solutions for a secure digital perimeter, we’re here to support you every step of the way.
The journey to a secure future begins with the right partners, tools, and knowledge. Start 2024 with SecurEnds, and let’s build a resilient digital landscape together.
Here’s to a year of cybersecurity empowerment, innovation, and success!