Identity Governance: Best Ways to Make Your Processes Easier & More Efficient
Identity Governance: Best Ways to Make Your Processes Easier & More Efficient

Your organization faces numerous challenges in managing identities and access rights across your networks, applications, and systems. The growing complexity of IT environments, the rise of remote workforces, and the increasing number of regulatory compliance requirements have made identity governance a critical aspect of modern cybersecurity.
To effectively navigate these challenges, you must adopt robust identity governance practices that streamline processes, enhance security, and improve overall efficiency. This article covers six key strategies that will help you and your team simplify your identity governance processes while ensuring compliance and reducing security risks.
We’ll look at practical insights, industry best practices, and real-world examples that highlight the value of effective identity governance in the modern era. Whether you’re an IT professional, a security practitioner, or a business leader, this article will provide you with actionable steps to optimize your identity governance processes and protect your organization’s critical assets.
Automation is no longer optional
Automation has emerged as an indispensable tool for organizations seeking to streamline their processes and improve efficiency. Traditional manual methods of identity management are not only time-consuming but also prone to errors, leading to security vulnerabilities and compliance gaps. With the increasing complexity of IT environments and the growing number of user accounts, automating identity governance has become a necessity rather than a luxury.
By leveraging automation, your organization can significantly reduce the administrative burden associated with managing identities and access rights. Automated provisioning and deprovisioning enables swift and accurate user onboarding and offboarding, ensuring that employees have timely access to the resources they need, and that access is promptly revoked when no longer required. This not only improves operational efficiency but also minimizes the risk of unauthorized access.

Automation also enables organizations to implement role-based access control (RBAC) effectively. RBAC assigns access permissions based on job roles, ensuring that users have the appropriate level of access required to perform their tasks without unnecessary privileges. By automating the assignment and revocation of access based on predefined roles, you streamline the access request and approval process, reducing the time and effort required for manual access management.
Another crucial aspect of automation in identity governance is the enforcement of segregation of duties (SoD). SoD policies prevent conflicts of interest by ensuring that no single user has excessive access rights that could be exploited for malicious purposes. Automating SoD policy enforcement not only strengthens security but also facilitates compliance with industry regulations and standards.
Additionally, automation plays a vital role in monitoring and auditing user activities. By implementing automated user activity monitoring and log analysis, you can proactively detect and respond to suspicious or anomalous behavior, mitigating the risks associated with insider threats and unauthorized access.
Automation can generate real-time alerts and notifications, empowering your security teams to take immediate action and investigate potential incidents promptly.
Security Fundamentals: User and Service Accounts
A solid understanding of user and service accounts is fundamental to establishing a robust security foundation. User accounts represent individuals within an organization, while service accounts are dedicated accounts used by applications, systems, or services to access resources. Both types of accounts require careful management to ensure the integrity and confidentiality of critical assets.
User Accounts
User accounts are the primary means by which individuals access organizational resources. Managing user accounts effectively is essential to prevent unauthorized access and maintain data confidentiality. Here are key considerations for secure user account management:
- User Provisioning and Deactivation: Implement automated processes for user onboarding and offboarding to ensure that access rights are promptly granted or revoked based on personnel changes. This reduces the risk of orphaned accounts and unauthorized access.
- Strong Authentication: Enforce the use of strong passwords and multi-factor authentication (MFA) to enhance the security of user accounts. MFA adds an extra layer of protection by requiring users to provide additional verification factors, such as biometrics or a unique code, along with their passwords.
- User Access Reviews: Conduct regular reviews of user access privileges to ensure that they align with the principle of least privilege. Remove unnecessary or excessive access rights to minimize the potential impact of compromised accounts.

Service Accounts
Service accounts play a critical role in enabling applications and systems to access resources and perform tasks automatically. However, inadequate management of service accounts can introduce security vulnerabilities. Consider the following best practices for service account management:
- Account Inventory: Maintain an inventory of all service accounts within the organization, including their purpose, associated applications or systems, and authorized users. This helps prevent the proliferation of undocumented or forgotten service accounts.
- Secure Credential Storage: Store service account credentials securely, using industry-standard encryption and access controls. Avoid hardcoding credentials in scripts or configuration files, as this can expose sensitive information to potential attackers.
- Regular Rotation of Credentials: Regularly rotate service account credentials to mitigate the risk of credential compromise. Implement automated processes to generate and distribute new credentials, ensuring a seamless transition without service disruption.
- Least Privilege Principle: Apply the principle of least privilege to service accounts, granting them only the minimum privileges required to perform their designated tasks. Avoid granting excessive or unnecessary permissions that could be exploited by malicious actors.
By implementing robust practices for user and service account management, you can enhance the security posture of your identity governance processes. Regularly assess and update these practices to adapt to evolving security threats and compliance requirements.
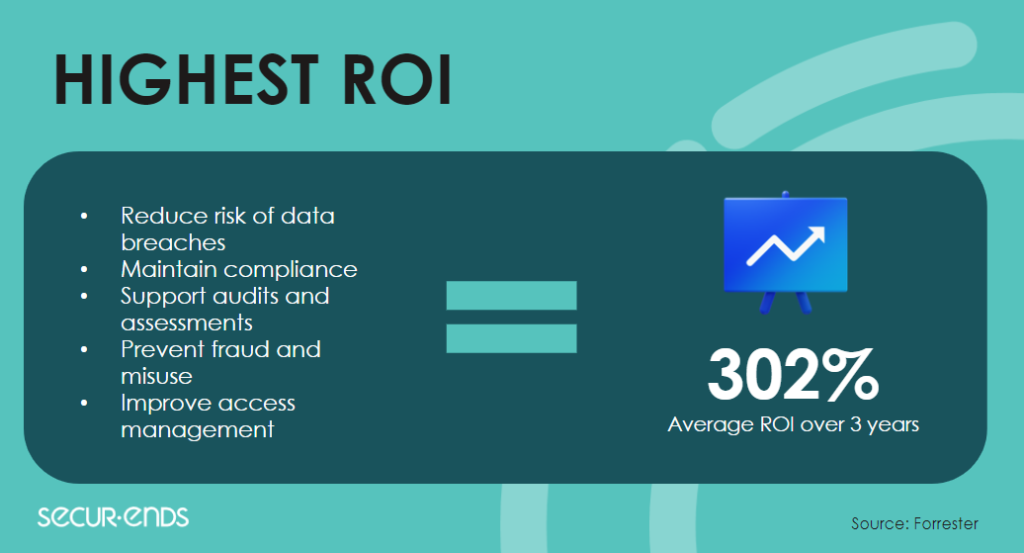
Automating user access reviews has the highest ROI
User access reviews are a critical aspect of identity governance, ensuring that user accounts have appropriate access privileges and align with the principle of least privilege. Traditionally, conducting access reviews manually has been a labor-intensive and time-consuming process for organizations. However, the implementation of automated user access reviews has proven to deliver substantial returns on investment (ROI), as supported by compelling data.
- Time and Resource Savings: Studies have shown that organizations that automate user access reviews experience significant time and resource savings. According to a recent survey, companies that adopted automated access reviews reduced the time spent on manual review processes by an average of 50-70%. This efficiency gain allows IT and security teams to focus on strategic initiatives and higher-value tasks, ultimately boosting overall productivity.
- Increased Accuracy and Consistency: Automation eliminates the potential for human error and ensures consistent evaluation of user access privileges. A study conducted by a leading research firm revealed that automated access reviews resulted in a 30% reduction in access-related errors compared to manual reviews. This heightened accuracy translates into strengthened security controls, reduced compliance risks, and enhanced data protection.
- Enhanced Compliance and Audit Readiness: Regulatory compliance is a critical concern for organizations across various industries. Automated user access reviews provide a systematic and auditable process, reducing compliance risks and facilitating the audit process. Real-world data showcases a significant improvement in compliance outcomes, with organizations achieving up to 80% reduction in compliance violations after implementing automated access reviews.
- Proactive Identification of Risks: Automation enables organizations to proactively identify and address risks associated with inappropriate access privileges or potential insider threats. A study conducted by a global cybersecurity company revealed that organizations using automated access reviews experienced a 75% decrease in security incidents related to unauthorized access. By leveraging continuous monitoring and intelligent analysis, automation empowers organizations to stay ahead of potential security risks.
- Scalability and Adaptability: The scalability and adaptability offered by automated access reviews are key drivers of ROI. Research indicates that organizations scaling their operations observed up to a 60% reduction in the time and effort required for access review processes when utilizing automation. Additionally, automation seamlessly accommodates changes in roles, responsibilities, and access requirements, ensuring that identity governance remains efficient and effective as organizations evolve.
The data-backed results demonstrate that automating user access reviews delivers substantial ROI. The time and resource savings, increased accuracy, enhanced compliance, proactive risk identification, and scalability provided by automation directly contribute to cost savings, improved security, and streamlined operations.
Why SecurEnds?
When it comes to implementing effective and efficient identity governance practices, partnering with the right solution provider is crucial. SecurEnds stands out as a leading provider in the field, offering comprehensive solutions that address the complexities of modern identity governance. Here are some compelling reasons why organizations choose SecurEnds:
- Advanced Automation Capabilities: SecurEnds brings advanced automation capabilities to the table, allowing organizations to streamline their identity governance processes and achieve significant time and resource savings. With SecurEnds, manual and error-prone tasks such as user provisioning, access reviews, and role management can be automated, resulting in increased efficiency, accuracy, and compliance readiness.
- Intelligent and Data-Driven Insights: SecurEnds leverages the power of AI and machine learning to provide intelligent insights into user access and entitlements. By analyzing patterns, access histories, and entitlement data, SecurEnds enables organizations to detect anomalies, identify potential security risks, and make informed decisions regarding access privileges. These data-driven insights empower organizations to strengthen their security posture and proactively address access-related risks.
- Customizable Policy Enforcement: Every organization has unique identity governance requirements, and SecurEnds understands the importance of flexibility. With its customizable policy engine, SecurEnds allows organizations to define and enforce access policies based on their specific needs and industry regulations. This ensures that access rights are aligned with business objectives and compliance mandates, enabling organizations to maintain control and reduce the risk of unauthorized access.
- Seamless Integration and Scalability: SecurEnds is designed to seamlessly integrate with existing IT systems, applications, and directories. Whether it’s cloud-based applications, on-premises systems, or hybrid environments, SecurEnds provides easy integration and interoperability. Additionally, as organizations grow and evolve, SecurEnds scales effortlessly, accommodating changes in user populations, organizational structures, and access requirements. This scalability ensures that identity governance remains effective and efficient as business needs evolve.
- Comprehensive Reporting and Audit Trail: SecurEnds offers robust reporting and auditing capabilities, providing organizations with comprehensive visibility into user access and entitlements. Customizable reports, real-time dashboards, and audit trails allow organizations to monitor compliance, track access changes, and generate evidence for audits and regulatory requirements. This not only simplifies the audit process but also supports accountability and transparency within the organization.
- Trusted Expertise and Support: With years of experience in identity governance and a team of dedicated experts, SecurEnds provides trusted expertise and support to its customers. From implementation to ongoing maintenance, SecurEnds offers comprehensive support services, ensuring that organizations maximize the value of their identity governance solutions. The knowledgeable and responsive support team is committed to helping customers navigate challenges, resolve issues, and achieve their identity governance goals.
SecurEnds offers advanced automation capabilities, intelligent insights, customizable policy enforcement, seamless integration, comprehensive reporting, and trusted expertise. By choosing SecurEnds as their identity governance partner, organizations can confidently tackle the complexities of identity governance, strengthen security, ensure compliance, and drive operational efficiency.
Use Cases
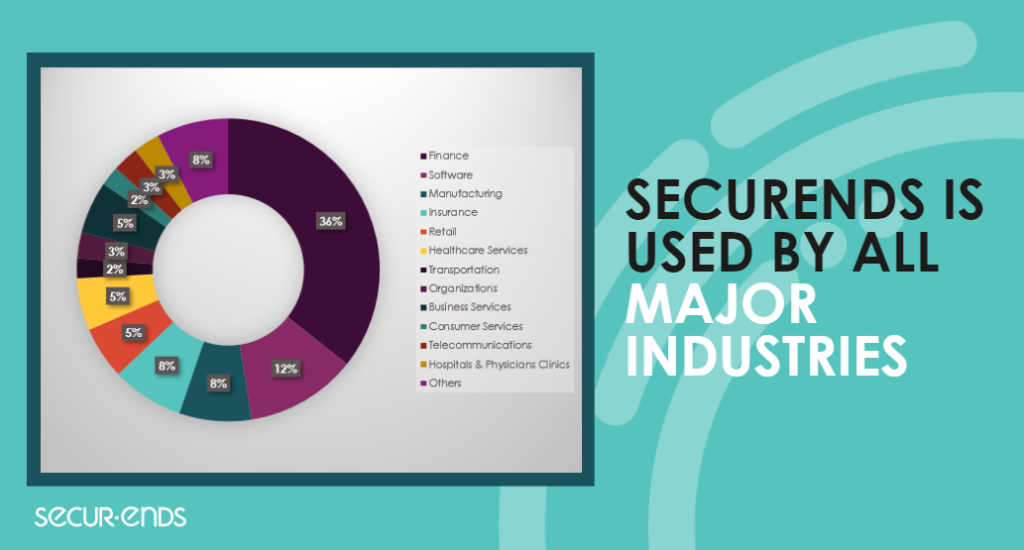
SecurEnds offers a versatile and adaptable identity governance solution that caters to a wide range of use cases across various industries. Let’s explore some of the key use cases where SecurEnds excels:
- Compliance and Regulatory Requirements: Achieving and maintaining compliance with industry regulations and standards is a top priority for organizations. SecurEnds assists in streamlining compliance efforts by providing automated access reviews, customizable policy enforcement, and comprehensive reporting capabilities. Whether it’s GDPR, HIPAA, SOX, or any other regulatory framework, SecurEnds helps organizations ensure that access rights align with compliance mandates, facilitating audit preparations and reducing compliance risks.
- Insider Threat Mitigation: Insider threats, whether intentional or accidental, can pose significant risks to an organization’s security. SecurEnds helps organizations proactively detect and mitigate insider threats by providing continuous monitoring, intelligent access analysis, and anomaly detection. By leveraging AI and machine learning algorithms, SecurEnds identifies unusual access patterns, detects unauthorized activities, and triggers alerts for potential insider threats, enabling organizations to take immediate action and protect their critical assets.

- Privileged Access Management: Managing and securing privileged accounts is critical to prevent unauthorized access and potential security breaches. SecurEnds offers comprehensive privileged access management capabilities, including automated provisioning, privileged access reviews, and segregation of duties enforcement. By implementing granular controls, real-time monitoring, and automated workflows, SecurEnds ensures that privileged accounts are managed effectively, minimizing the risk of misuse and unauthorized access.
- Role-Based Access Control (RBAC): Implementing RBAC policies can be complex, especially in large organizations with diverse user populations. SecurEnds simplifies RBAC implementation by providing automated role assignment, access certification, and role lifecycle management. With SecurEnds, organizations can define roles based on job responsibilities, grant access privileges accordingly, and automatically review and update roles as personnel changes occur. This ensures that access rights are aligned with job functions, simplifies access management, and reduces the risk of excessive privileges.
- Cloud-Based Application Governance: As organizations increasingly adopt cloud-based applications, managing access rights across multiple platforms becomes challenging. SecurEnds offers seamless integration with popular cloud applications, providing centralized access governance and user lifecycle management. Organizations can leverage SecurEnds to automate user provisioning, access reviews, and entitlement management, ensuring consistent and secure access to cloud resources while maintaining visibility and control.
These use cases represent just a snapshot of the broad range of scenarios where SecurEnds excels in identity governance. From compliance and insider threat mitigation to privileged access management and cloud application governance, SecurEnds empowers organizations to strengthen their security posture, optimize access controls, and streamline identity governance processes.
Customer Success Stories
SecurEnds has successfully partnered with numerous organizations in the banking and telecom sectors to enhance their identity governance practices. Let’s explore a couple of customer success stories that highlight the value and impact of SecurEnds’ solutions in these industries.
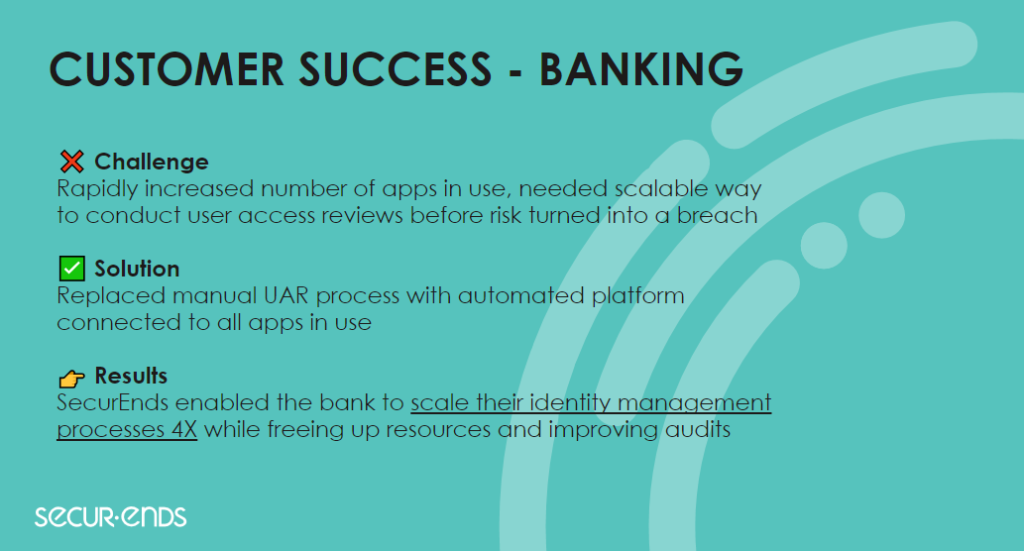
Banking Sector
A leading financial institution faced challenges in managing access reviews and meeting regulatory compliance requirements. Manual access review processes were time-consuming and prone to errors, putting the bank at risk of non-compliance.
By implementing SecurEnds’ automated access review solution, the bank achieved remarkable results. The solution automated the access review process, reducing the time spent on reviews by 60% while increasing accuracy and consistency.
The comprehensive reporting capabilities provided by SecurEnds helped the bank demonstrate compliance with industry regulations, enhancing audit readiness and minimizing compliance risks.

Telecom Sector
A major player in the telecommunications industry recognized the need to strengthen their privileged access management and mitigate insider threats. With a vast network infrastructure and numerous privileged accounts, the telecom company faced challenges in managing and securing access across their systems.
SecurEnds provided a robust privileged access management solution tailored to the telecom industry’s specific needs. By implementing SecurEnds’ solution, our client gained granular control over privileged accounts, automated privileged access reviews, and enforced segregation of duties. Real-time monitoring and anomaly detection capabilities helped the company proactively identify and address insider threats, ensuring the security of their critical systems and customer data.
These customer success stories demonstrate how SecurEnds has delivered tangible value to organizations in the banking and telecom sectors. By addressing specific industry challenges, such as regulatory compliance and privileged access management, SecurEnds’ solutions have empowered these organizations to streamline their identity governance processes, enhance security, and achieve their business objectives.
Start enhancing your Identity Governance today

Identity governance plays a vital role in today’s interconnected digital landscape, where organizations face complex challenges in managing user access and ensuring security.
SecurEnds offers a comprehensive suite of solutions designed to streamline identity governance processes, strengthen security controls, ensure compliance, and drive operational efficiency.
Through automation, intelligent insights, customizable policies, and seamless integration, SecurEnds empowers organizations to optimize their identity governance frameworks.
Ready to enhance their access reviews, secure privileged accounts, mitigate insider threats, and achieve regulatory compliance with confidence? Book a demo of SecurEnds now.
✍ Article by Dino Juklo