Secure & Seamless Employee Offboarding: A Complete Access-Centric Guide
Secure & Seamless Employee Offboarding: A Complete Access-Centric Guide

Introduction
Employee exits are inevitable, but security lapses during offboarding shouldn’t be. Whether it’s a voluntary resignation, retirement, or a difficult termination, every departure marks a moment of elevated risk for the organization. And while offboarding is often seen as an HR-led process, in reality, it’s a security-critical, access-driven operation that demands precision and collaboration between HR, IT, and compliance teams.
Behind every departure lies a digital footprint: system logins, cloud app credentials, VPN tokens, and access to sensitive data. When not properly revoked, these can become orphaned accounts—an open door for insider threats, data leakage, or audit failures. In a hybrid and SaaS-heavy landscape, this risk only grows.
That’s why modern organizations are rethinking Employee Off-Boarding through the lens of Identity Access Management (IAM) and Identity Governance and Administration (IGA). This blog serves as your end-to-end guide to access-centric offboarding. We’ll explore the risks, outline best practices, and provide actionable strategies—including how tools like User access reviews and automated deprovisioning can close security gaps and keep your enterprise compliant.
Let’s break down what secure offboarding looks like—and why it’s time to move beyond spreadsheets and checklists.
What is Employee Offboarding?
At its core, Employee Off-Boarding is the formal disengagement of a departing team member from an organization’s digital and operational landscape. But it’s not just about deactivating accounts or returning hardware—it’s about orchestrating a clean, complete, and compliant separation across every touchpoint of access.
This process spans multiple stakeholders. HR initiates and tracks the exit. IT ensures technical revocation. Compliance validates policy alignment. And direct managers handle knowledge transfer and operational continuity. The coordination between these roles is what transforms offboarding from a loose checklist into a secure, structured protocol.
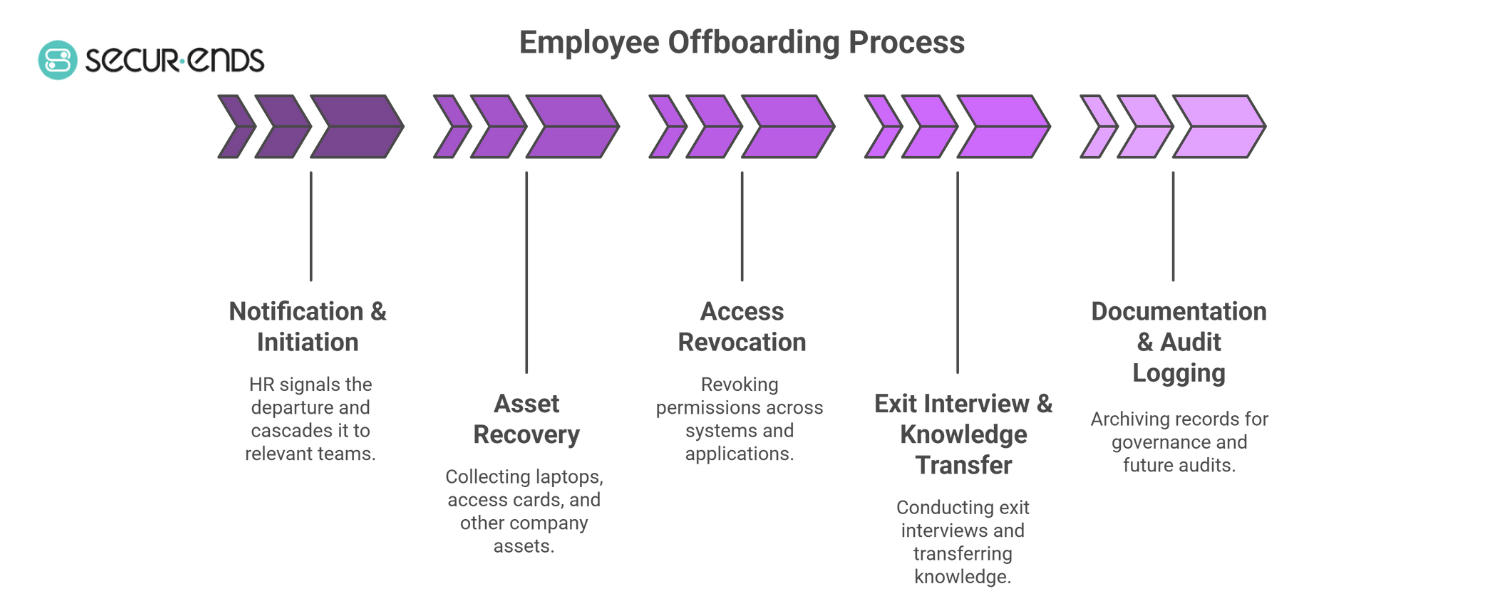
While the triggers may differ—voluntary resignations, involuntary terminations, layoffs, retirements, or even contract expirations—the fundamental stages of offboarding remain consistent:
- Notification & Initiation – HR signals the departure and cascades it to relevant teams.
- Asset Recovery – From laptops and access cards to mobile devices and authentication tokens.
- Access Revocation – Revoking permissions across on-prem systems, cloud applications, and third-party tools.
- Exit Interview & Knowledge Transfer – Ensuring smooth transition of responsibilities and project data.
- Documentation & Audit Logging – Archiving records for governance and future audits.
In organizations that support Acccess Request, Contractor Self Request, or Employee Self Request capabilities, the complexity of offboarding scales. Without visibility into these identity touchpoints, even the most mature teams risk leaving behind unused credentials and access loopholes.
And it’s exactly these invisible cracks that make offboarding one of the most underestimated security vulnerabilities in enterprise environments.
Why Employee Offboarding is a Security Risk
In practice, delays in deactivating access are surprisingly common. In fact, industry reports reveal that over 30% of organizations take more than three days to revoke all system access after an employee leaves—and some never fully complete the process at all. The result? A growing inventory of orphaned accounts—still active, still credentialed, and still capable of being exploited.
These inactive credentials are more than just a housekeeping issue. They’re a direct invitation for:
- Unauthorized access: Orphaned accounts create entry points for threat actors, especially if login credentials haven’t been reset.
- SaaS exposure: Unrevoked access to platforms like Salesforce, Slack, or GitHub opens the door to data exfiltration, often without raising immediate alarms.
- Compliance violations: Regulatory frameworks like HIPAA, SOX, and ISO 27001 require timely deprovisioning and detailed audit trails. Any deviation can result in audit findings—or worse, penalties.
The stakes become even higher when former employees retain privileged access or administrative roles. There have been documented cases of ex-employees deliberately accessing systems post-departure, leaking data, or sabotaging environments. These aren’t isolated incidents—they’re a direct consequence of inconsistent offboarding practices and insufficient User access reviews.
This is where a robust Identity Governance and Administration (IGA) framework becomes essential. By aligning offboarding with Identity Access Management (IAM) principles and embedding periodic reviews, organizations can prevent access drift and mitigate risks well before they manifest.
But awareness alone isn’t enough. The real shift happens when offboarding becomes structured, policy-driven, and fully embedded within your identity lifecycle.
Core Components of a Secure Offboarding Process
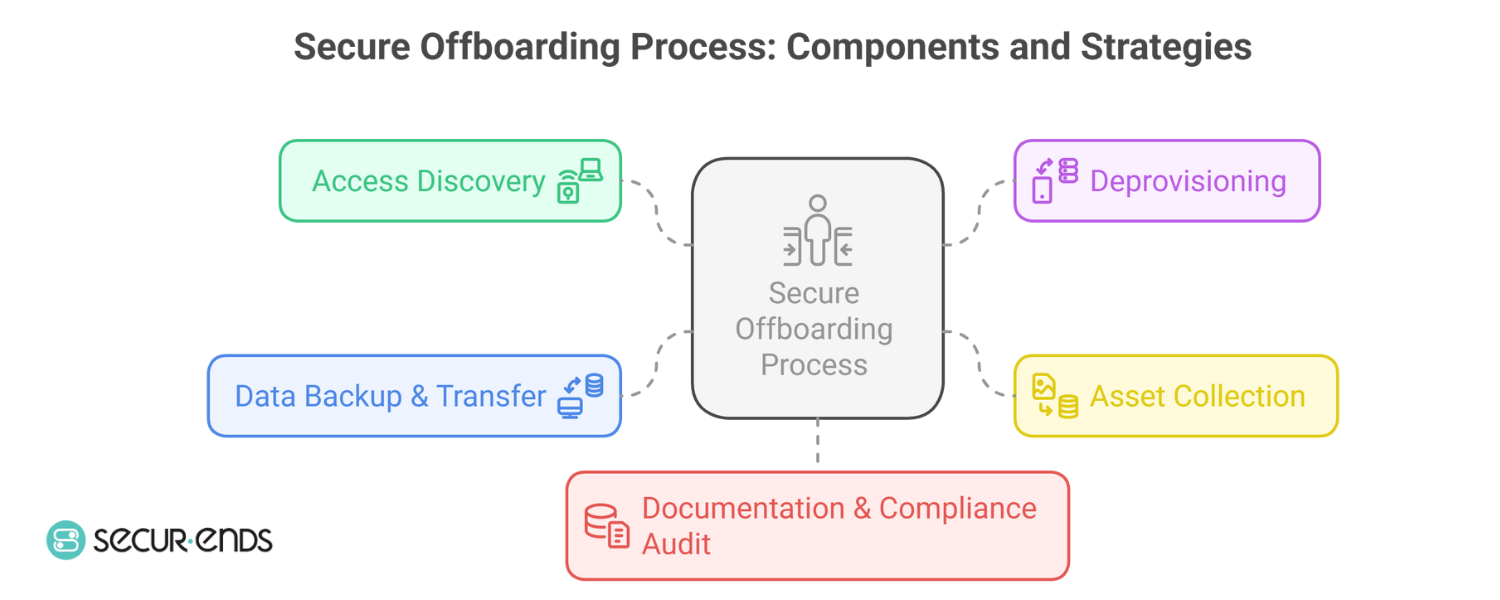
Effective offboarding begins with visibility—knowing where access exists—and ends with assurance—knowing it has been revoked, recorded, and verified. A secure, access-centric offboarding process typically involves the following core components:
1. Access Discovery
Before you can revoke access, you need to know exactly where it exists. This means mapping all user accounts across directories, SSO systems, SaaS platforms, and cloud infrastructure. For organizations operating in decentralized environments or dealing with Shadow IT, this step is crucial.
Without visibility into every identity touchpoint—including accounts created via Employee Self Request, Contractor Self Request, or ad hoc integrations—accesses are easily missed. This is where User access reviews and identity analytics come into play, helping to surface unknown or unused entitlements.
2. Deprovisioning
Access should never linger beyond the employee’s final working moment. Depending on the sensitivity of the role, this could mean immediate revocation upon notification, or a staged deprovisioning tied to knowledge transfer and project handover.
This step becomes exponentially more efficient when managed through Identity Governance and Administration (IGA) tools that enable policy-based deprovisioning. For example, platforms like SecurEnds allow organizations to configure deprovisioning workflows based on user roles, departments, or even exit triggers.
3. Asset Collection
Physical and digital asset recovery is often overlooked, especially in hybrid or remote setups. Beyond laptops and phones, think access badges, hard tokens, external drives—even SaaS licenses tied to individual user credentials. Each item carries potential exposure if left unaccounted for.
4. Data Backup & Transfer
Departing employees often leave behind critical files, process knowledge, or project IP stored across cloud tools and collaboration platforms. Secure offboarding should include structured data export, file ownership reassignment, and clearly documented project transitions.
This step not only supports continuity but also prevents future reliance on inactive accounts just to retrieve old data—a common but dangerous workaround.
5. Documentation & Compliance Audit
Every action taken during offboarding—from access revocation to device collection—must be logged, timestamped, and retained. These records form the backbone of your audit readiness, especially under regulations like SOX, HIPAA, and ISO 27001.
Audit-grade visibility isn’t just about ticking boxes—it’s about proving that your organization handles Employee Off-Boarding with the same rigor as employee onboarding or access provisioning.
Pro Tip: Automating these steps not only ensures consistency but significantly reduces the margin for human error.
In fact, automation is often the difference between a reactive offboarding process and a secure, scalable one—a topic we’ll explore in the next section.
Manual vs Automated Offboarding: Why It Matters
Manual offboarding methods—email chains, spreadsheets, disparate system alerts—create unavoidable friction. Teams operate in silos. Tasks fall through the cracks. Access revocation is delayed or incomplete. And without centralized oversight, no one is entirely sure what’s been done, or what’s been missed.
These inefficiencies don’t just slow the process—they amplify risk.
The Pitfalls of Manual Offboarding:
- Delayed revocation: Critical access can remain active for days—or indefinitely
- Visibility gaps: No consolidated view of what systems a user was connected to
- Policy inconsistencies: No standardized workflows for different roles or exit types
- Audit exposure: Fragmented records, if any, make compliance nearly impossible to prove
In contrast, automation enables a proactive and consistent offboarding experience—driven by policy, not people.
The Advantage of Automation:
- Faster deprovisioning: Access is revoked across systems the moment HR triggers the exit
- Integrated workflows: Seamless coordination between HR platforms (like Workday) and identity systems
- Role-based deactivation: Users offboarded based on predefined rules tied to job function, department, or location
- Audit-ready: Every step logged, time-stamped, and accessible for compliance review
Solutions like SecurEnds are purpose-built for this challenge. They offer:
- Automated user deprovisioning across hybrid and cloud environments
- Continuous User access reviews to validate entitlements pre- and post-exit
- Configurable, role-based offboarding workflows that reduce manual oversight
- Support for time-based triggers such as Just in Time Access Request expiration or emergency access windows
By aligning offboarding with your Identity Access Management (IAM) architecture and embedding automation at every layer, you gain both control and speed—two things manual processes rarely offer in tandem.
But the stakes grow even higher when your workforce is no longer bound to a central office.
Want to understand how onboarding and offboarding fit into the bigger identity and access strategy? Explore our Employee Lifecycle Access Management to see how SecurEnds secures every stage — from Day One to departure.
Offboarding in Hybrid and Remote Work Environments
Today’s offboarding process doesn’t happen in a single building or at a single desk. As employees shift to remote and hybrid roles, the traditional methods of collecting hardware, disabling local accounts, and handing over responsibilities are no longer enough.
The same factors that make automated deprovisioning essential—scalability, speed, and visibility—are even more critical in this distributed landscape. Employees now operate across personal devices, public networks, and an expanding ecosystem of SaaS platforms. Access isn’t just assigned by IT—it’s often initiated through Access Request, or triggered dynamically through policies like Just in Time Access Requests for project-specific tools.
And without the right identity governance in place, the offboarding process can leave dangerous gaps:
- Devices may not be returned on time—or at all.
- Access tied to Employee Self-Request or temporary credentials may go unnoticed.
- Accounts created in third-party platforms remain active long after the final working day.
These aren’t edge cases—they’re everyday realities in organizations managing hybrid teams, contract workers, or international operations. Left unchecked, they lead to orphaned accounts, unauthorized access, and compliance violations.
This is where Identity Governance and Administration (IGA) platforms like SecurEnds offer real value. With centralized access visibility, automated triggers, and support for distributed environments, they help security and IT teams offboard confidently—no matter where the employee logs in from.
In essence, automation isn’t just about operational efficiency anymore. It’s about sustaining security posture in a borderless, cloud-driven workplace.
Best Practices Checklist for Secure Offboarding
Trigger offboarding as soon as HR initiates the exit
Waiting until the final day increases the window of risk. Offboarding should begin the moment the separation process is confirmed—especially for sensitive roles or privileged users.
Maintain a centralized inventory of user access
Visibility is everything. Regular User access reviews help identify where accounts exist, what permissions they hold, and whether Employee Self Request or Contractor Self Request workflows have introduced additional access points.
Use role-based models to simplify revocation
Access tied to roles is easier to deactivate systematically. Integrating Identity Access Management (IAM) with your offboarding workflows helps ensure nothing is missed.
Integrate IT and HR systems for seamless coordination
Connecting tools like Workday with platforms like SecurEnds ensures offboarding actions (e.g., access revocation, deprovisioning) are automatically triggered—without relying on manual handoffs.
Enforce time- or event-based deprovisioning policies
Use identity governance rules to revoke access based on termination date, project end, or role change. This supports compliance and improves operational hygiene.
Audit and document every offboarding step
Log asset recovery, access revocation, and data handover activities. This is crucial for regulatory audits and internal reviews, especially when governed under SOX, HIPAA, or ISO frameworks.
Run post-offboarding access certifications
A final User access review—conducted days or weeks after separation—helps validate that all entitlements were removed and no reactivations occurred.
Monitor high-risk access scenarios even after exit
Temporary credentials, Emergency Access Requests, or SaaS tokens can remain active beyond the exit window. Automate expiration policies where possible.
Automate wherever feasible to reduce dependency on manual effort
Manual checklists are prone to error. By embedding Identity Governance and Administration (IGA) tools, organizations can execute repeatable, scalable offboarding with confidence.
Even with a well-documented process, execution often breaks down in the details—especially when teams rely on disconnected tools or manual steps. That’s where the right platform makes a measurable difference.
How SecurEnds Simplifies Employee Offboarding
SecurEnds is built to eliminate the friction and blind spots that often plague traditional offboarding processes. By centralizing visibility and automating access actions, it ensures that every exit—whether planned or sudden—is handled with precision.
Here’s how it helps organizations stay secure, compliant, and in control:
- Automated Deprovisioning
Trigger access revocation across directories, apps, and cloud platforms the moment an employee’s exit is initiated. Whether it’s a standard Employee Off-Boarding or triggered via a Contractor Self Request, workflows are designed to adapt dynamically. - Access Review Workflows
Conduct periodic User access reviews or targeted offboarding reviews post-exit. Ensure that no entitlements—especially those tied to Emergency Access Requests or external apps—slip through the cracks. - SaaS Discovery and Shadow IT Monitoring
Uncover unmanaged accounts and cloud tools used outside IT visibility. This is especially critical in hybrid teams where Employee Self Request or Just in Time Access Requests may have expanded access footprints without centralized control. - Role- and Time-Based Policy Enforcement
Align access with business rules—not just user roles. Whether you’re offboarding a retiree, contractor, or remote team member, SecurEnds applies time-bound and condition-based revocation across all environments. - Comprehensive Audit Trails
Every offboarding action—approval, revocation, reassignment—is logged. This ensures readiness for audits and reinforces compliance with frameworks like HIPAA, SOX, and ISO standards, as part of broader Identity Governance and Administration (IGA) initiatives.
When offboarding is handled through SecurEnds, it doesn’t just become faster—it becomes smarter, more secure, and tailored to your business needs.
Conclusion
A secure employee offboarding process is no longer a back-office function—it’s a critical layer in your organization’s identity and access strategy. From managing cloud entitlements to eliminating orphaned accounts, the stakes are too high for manual, fragmented approaches.
By combining automation, governance, and audit-ready workflows, solutions like SecurEnds help enterprises offboard with confidence—every time, across every environment.
Now is the time to assess your offboarding maturity. Strengthen your controls. Reduce your risk. And if you’re ready to take the next step, our experts are here to help.


