What is Identity Governance and Administration (IGA)?
What is Identity Governance and Administration (IGA)?
Author – Kumar Jandayala
Head of Product at SecurEnds, driving modular IGA capabilities such as access reviews and provisioning.
The cost of cyber breaches and compliance failures in 2025 has never been higher. IBM’s latest Cost of a Data Breach Report shows that the global average now exceeds $4.5 million per incident. In healthcare and finance, penalties can climb even faster once fines and regulatory investigations are added. For many organizations, the real impact isn’t only financial—it’s the reputational damage and the loss of customer trust.
As we move into 2026, businesses face increasing pressure from escalating cyber threats and rising compliance requirements. Identity Governance and Administration (IGA) has become a foundational control in addressing these risks. As threats grow more frequent and sophisticated, organizations must protect sensitive data while maintaining compliance with regulations such as GDPR, HIPAA, and SOC 2. Without structured identity governance, controlling access to critical systems becomes increasingly complex, leaving organizations exposed to security and regulatory risk.
The financial impact of these breaches is significant — not only in direct costs, but also in penalties, remediation efforts, and reputational harm. Identity governance and administration provides a structured approach to managing user access and permissions. It helps reduce the risk of unauthorized access while supporting compliance with industry standards. By automating processes such as access reviews and certifications, IGA enables organizations to stay ahead of evolving threats while minimizing audit fatigue and operational risk.
In this blog, we explore how identity governance and administration provide a clear framework for improving security, strengthening compliance, and reducing operational exposure. In today’s security landscape, IGA plays a critical role for organizations seeking to remain secure and audit-ready in 2026 and beyond.
What is Identity Governance and Administration (IGA)?
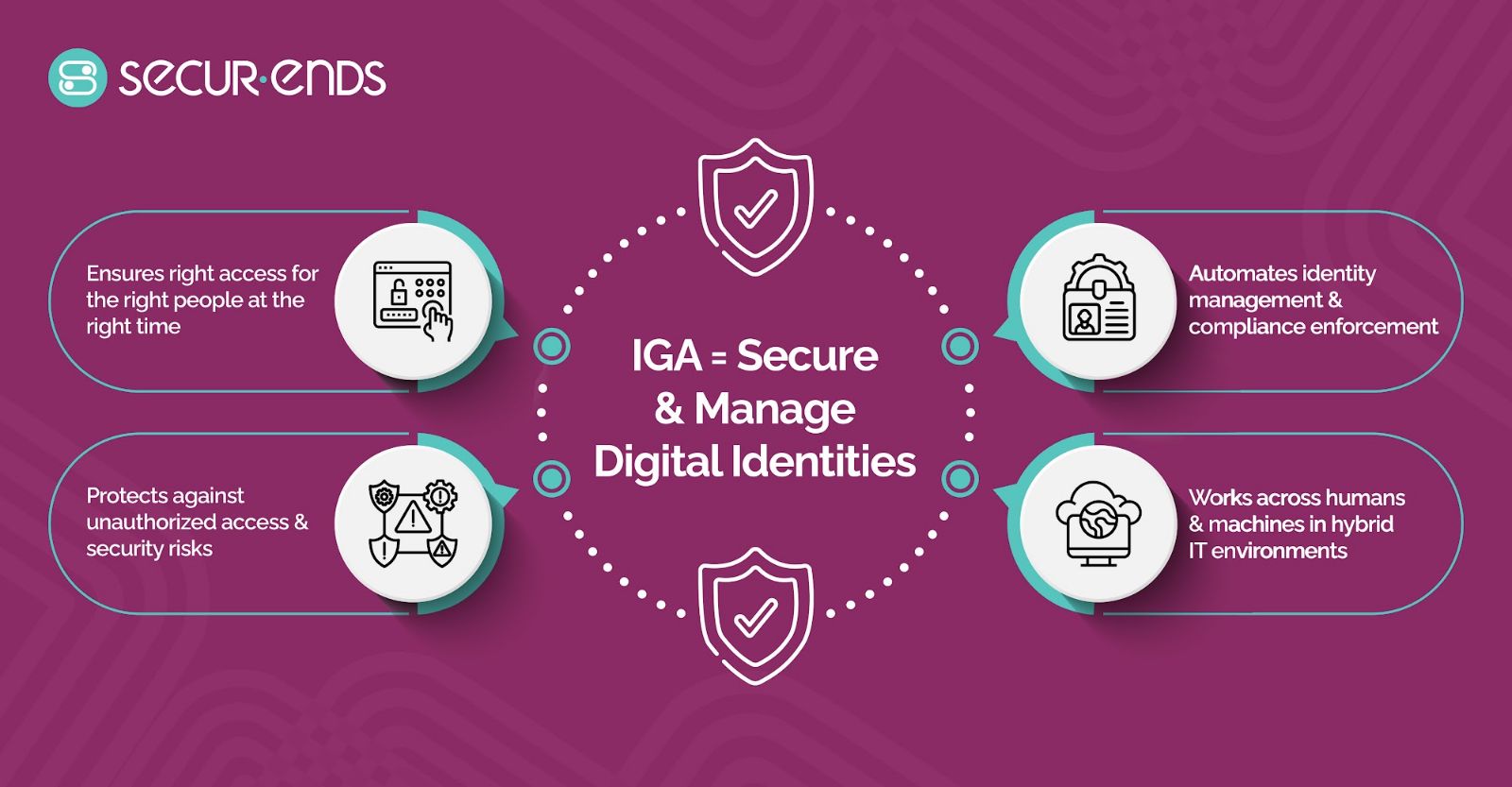
Identity and Governance Administration (IGA) points to the policies, processes and technologies that help and assist an organization to manage and control user access to critical data and systems. This procedure involves a continuous process of managing identities and also ensuring users have the required access to perform and their roles to maintain compliance with industry standards.
IGA is just about managing who has access to what, when and why they have it. This includes managing user identities, assigning roles and controlling access to them based on the role. It also involves conducting a regular review to make sure access remains appropriate. It also guarantees compliance with regulatory frameworks which is GDPR, HIPAA and SOC 2. For which require businesses to have strict access controls and audits in place.
One key area of identity governance and administration is that it allows businesses to manage user access more effectively and efficiently. By automating processes such as access reviews, provisioning along with de provisioning, IGA helps organizations to reduce the complexity of access management at the same time helping in reducing the risk of human error.
IGA also plays a very important role in industries such as finance and healthcare. The reason is it is there that the cost of non compliance can be very severe and harsh. With the right tools, businesses can simplify the audit process and also improve security with enhanced operational efficiency.
In brief, Identity and Governance Administration promises that only the required people have access to the resources they need at the necessary time without compromising any security or compliance.
Why Your Organization Needs Identity Governance and Administration in 2026

As cyber threats evolve and regulatory expectations tighten, Identity Governance and Administration (IGA) has become a critical control for organizations operating in complex IT environments. Hybrid infrastructures, cloud applications, third-party vendors, and remote workforces have significantly expanded the identity attack surface. Without structured governance, access risks increase quickly and often go unnoticed.
Organizations without an effective IGA framework face several operational and compliance challenges:
Unauthorized Access
Without automated lifecycle controls, users may retain access beyond what is required for their roles. Over time, excessive permissions accumulate, increasing exposure to data misuse and credential-based attacks.
Compliance Risk
Regulatory requirements such as GDPR, HIPAA, and HITRUST demand demonstrable access controls and periodic reviews. Failure to maintain structured governance can result in audit findings, penalties, and reputational damage.
Audit Fatigue
Manual access reviews, spreadsheet tracking, and email-based approvals are resource-intensive and prone to error. This approach increases the likelihood of missed violations and incomplete documentation.
Operational Inefficiency
Managing access manually across multiple systems slows onboarding, delays role transitions, and increases the burden on IT teams.
How IGA Strengthens Compliance
IGA introduces structured oversight and automation into identity management processes. It helps organizations stay aligned with regulatory frameworks such as GDPR, HIPAA, and HITRUST by enabling:
-
Access Reviews: Ensuring permissions remain aligned with business roles
-
Role-Based Access Control (RBAC): Standardizing access assignment based on job function
-
Audit Trails: Maintaining documented evidence of access approvals and changes
By automating certifications and enforcing policy controls, IGA reduces compliance gaps while improving accuracy and accountability.
Business Impact of Implementing IGA
Beyond security and compliance, IGA delivers measurable operational benefits:
-
Reduced manual workload through automation
-
Faster onboarding and role-based provisioning
-
Improved visibility into identity risk
-
Lower exposure to privilege creep and orphaned accounts
In 2026, IGA is not simply a security enhancement — it is an operational requirement for maintaining governance at scale.
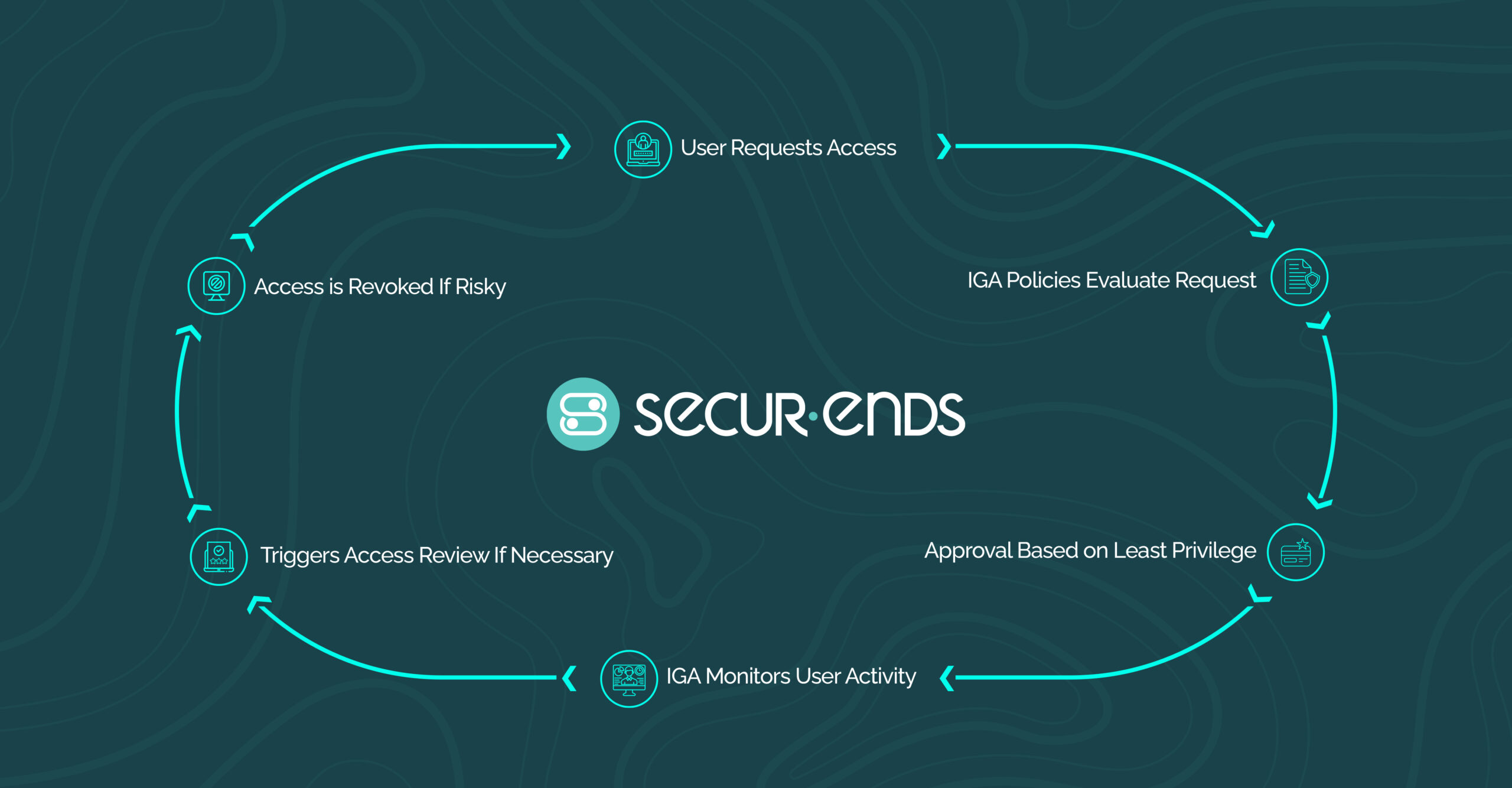
How Identity Governance and Administration Works
Identity Governance and Administration operates through structured lifecycle controls, policy enforcement, and continuous access validation. Rather than managing identities in isolation, IGA establishes repeatable processes that govern how access is granted, reviewed, modified, and removed.
1. Joiner–Mover–Leaver Lifecycle
IGA begins with identity lifecycle management:
-
Joiner: When a new employee joins, access is provisioned automatically based on predefined roles and business policies.
-
Mover: When a user changes roles or departments, permissions are adjusted to align with new responsibilities.
-
Leaver: When employment ends, access is revoked promptly to prevent orphaned accounts.
This lifecycle approach reduces privilege creep and ensures that access remains aligned with actual job function.
2. Access Requests and Approval Workflows
IGA platforms standardize access requests through structured workflows. Users request access to systems or applications, and approvals are routed to managers or application owners based on defined policies.
Every approval, modification, or rejection is documented. This creates traceable evidence required for regulatory compliance under frameworks such as GDPR, HIPAA, and HITRUST.
3. Role and Entitlement Management
Instead of assigning permissions individually, IGA organizes access through role-based access control (RBAC). Roles reflect job functions, and entitlements are mapped to those roles.
This model:
-
Reduces manual access assignment
-
Improves consistency across systems
-
Enforces least-privilege principles
Role governance also enables organizations to detect excessive access across departments.
4. Access Certifications and Reviews
Periodic access certifications are a core function of IGA. Managers and system owners review user access at defined intervals to confirm that permissions remain appropriate.
These reviews:
-
Identify dormant or excessive access
-
Reduce audit findings
-
Provide documented compliance evidence
Automated certification workflows significantly reduce audit fatigue while increasing review accuracy.
5. Policy Enforcement and Audit Reporting
IGA continuously evaluates access against policy rules, including segregation of duties (SoD) controls and risk-based access thresholds.
When violations occur, alerts are generated and remediation workflows are triggered. Detailed audit logs and reporting dashboards allow organizations to demonstrate compliance and governance maturity.
Why This Process Matters
Without structured lifecycle governance, access management becomes reactive. IGA transforms identity control into a documented, enforceable process that supports security, operational efficiency, and regulatory accountability.
In modern hybrid environments, governed identity processes are essential to maintaining control at scale.
Challenges in Identity Governance and Ways to Overcome Them
Implementing Identity and Governance Administration (IGA) comes with its own challenges. But to truly understand these obstacles and to take proactive measures can help mitigate their impact. Below mentioned are some of the most common challenges almost all the organizations face in IGA implementation. Strategies are also provided to overcome them:
1. Orphaned Accounts
Orphaned accounts are user accounts that remain active after an employee leaves or no longer requires access. These accounts pose a huge security risk as they often have the ability to provide unauthorized access to sensitive data and systems.
Solution: Conduct an user access review regularly to identify and to deactivate orphaned accounts. Also make sure to implement automated workflows that trigger account deactivation when a user leaves the company or changes roles. This process helps to remove the unused accounts quickly. This in turn reduces the risk of unauthorized access.
2. Privilege Creep
Privilege creep occurs when users gather excessive access rights over time. This happens often due to job changes or departmental shifts within the organization. The excessive access can lead to users having more access than required for them. This increases the risk of accidental and also intentional misuse of sensitive information.
Solution: For resolving this, use Role-Based Access Control (RBAC) to assign and also to enforce access based only on roles rather than individual users. Please make sure to implement regular access reviews and the user privileges remain aligned with their current given responsibilities. Automated entitlement management can help manage and track changes in user access.
3. Audit Fatigue
Audit fatigue is a common issue when an organization relies only on manual processes to track and verify user access and their activities. The complexity and volume of data involved in audits can overwhelm teams which most of the time leads to errors or missed violations.
Solution: Implement automated access certification and audit trails. THis will reduce manual effort and improve accuracy. The benefit of an automated system is that audits can be performed with minimal intervention. This helps in allowing your team to focus on exceptions rather than manually checking each user’s access every single time.
4. Integration with Legacy Systems
Many organizations still rely on legacy IT systems. These are very difficult to integrate with modern and current IGA solutions. These outdated systems will only complicate the implementation of consistent access controls across the complete organization.
Solution: Choose IGA solutions that offer a robust integration capability with legacy systems. Many modern identity governance tools can integrate seamlessly with older platforms. This helps in allowing you to maintain a unified access control strategy across all systems.
Core Capabilities of an Identity Governance and Administration (IGA) Solution
A mature Identity Governance and Administration solution delivers structured identity lifecycle management, entitlement oversight, and compliance visibility. Rather than focusing on isolated features, organizations should evaluate how effectively the platform governs user provisioning, deprovisioning, access certifications, and policy enforcement across hybrid IT environments.
1. Entitlement Management
Entitlement management defines, monitors, and controls user permissions across enterprise systems. It ensures that access rights are aligned with business roles and continuously validated against least-privilege principles. Strong entitlement governance reduces identity risk, prevents orphaned accounts, and limits excessive access accumulation.
How It Helps: Entitlement management ensures users only to have access to what they need for their role. It helps in reducing the risk of unauthorized access to any sensitive data. It also helps when users change roles or leave the company, as access rights can be swiftly revoked, contributing to stronger identity governance and administration practices.
2. Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC)structures access through defined job functions rather than individual assignments. Permissions are mapped to roles, simplifying governance and enforcing least-privilege principles across the organization.
How It Helps:
RBAC improves consistency in provisioning and deprovisioning, reduces administrative complexity, and supports scalable identity lifecycle management as users join, move, or leave the organization.
3. Access Reviews and Compliance
Access certifications validate that permissions remain appropriate over time. Automated review workflows enable structured access governance.
How It Helps:
Regular certifications generate audit-ready evidence, reduce compliance gaps, and support regulatory alignment under frameworks such as GDPR, HIPAA, and HITRUST.
4. Risk-Based Access Policies
Risk-based access policies assess the level of risk associated or involved with a user access and adjusts the permissions accordingly. This ensures that sensitive data and high risk users are protected well by stricter access controls. The lower risk users can be granted more flexibility with this.
How It Helps: By implementing a risk-based access policies, your organization can focus security efforts where it matters most which is protecting critical assets. This approach ensures that the identity governance and administration is not only functional but also a proactive measure in safeguarding valuable data.
5. Self-Service Access Requests
Structured self-service workflows allow users to request permissions through controlled approval mechanisms.
How It Helps:
This balances operational agility with documented governance, ensuring access decisions remain traceable and policy-compliant.
IGA vs IAM vs PAM
In the world of identity management, Identity Governance and Administration (IGA), Identity Access Management (IAM) and Privileged Access Management (PAM) are just terms that almost always come up. While all of it deals with controlling and also within securing access to users and its resources, each serves a different purpose. Understanding the differences between these concepts is very important and will assists in building a strong access management strategy.
What is IAM?
Identity Access Management (IAM) is a framework to manage and secure user identities along with their access to resources across an organization. It focuses on ensuring that the right individuals have the right access at the necessary time. IAM solutions usually handle authentication (verifying users) and authorization (granting access to resources).
IAM solutions assists in making sure that all employees, contractors and all the partners involved can access the systems they need. This also ensures that unauthorized access is stopped then and there. But IAM focuses primarily on managing user authentication and authorization rather than the broader identity governance requirements necessarily needed to comply with regulations or to oversee the entire lifecycle of user access.
What is PAM?
Privileged Access Management (PAM) specifically deals with managing and also with monitoring access to high privilege accounts. High privileged accounts are accounts with elevated permissions. The users in this department are administrators or IT staff. PAM solutions are designed to minimize the risks of exposing and information associated with these highly privileged accounts. This is done by restricting and controlling access by monitoring activity and preventing misuse.
PAM tools almost all the time are involved in session recording, password vaulting and strict access controls to protect the most sensitive accounts from any attacks. While PAM plays a crucial role in protecting privileged users, it is not as comprehensive and complete in handling and providing security and access of everyday users throughout the organization.
What is IGA?
Identity Governance and Administration (IGA) on the other hand encompasses a broad and complete approach to access management. IGA solutions focusses not only on providing and managing access. It also ensures compliance with industry regulations along with auditing access control policies with continuously reviewing user access.
Where IAM focuses only on managing user authentication and authorization and PAM focuses on privileged access. On the other hand, IGA covers the complete lifecycle of identity management. This ensures users have the appropriate and required level of access based on their roles and conducts regular reviews which helps to prevent risks including =privilege creep, orphaned accounts or unauthorized access to private or sensitive data.
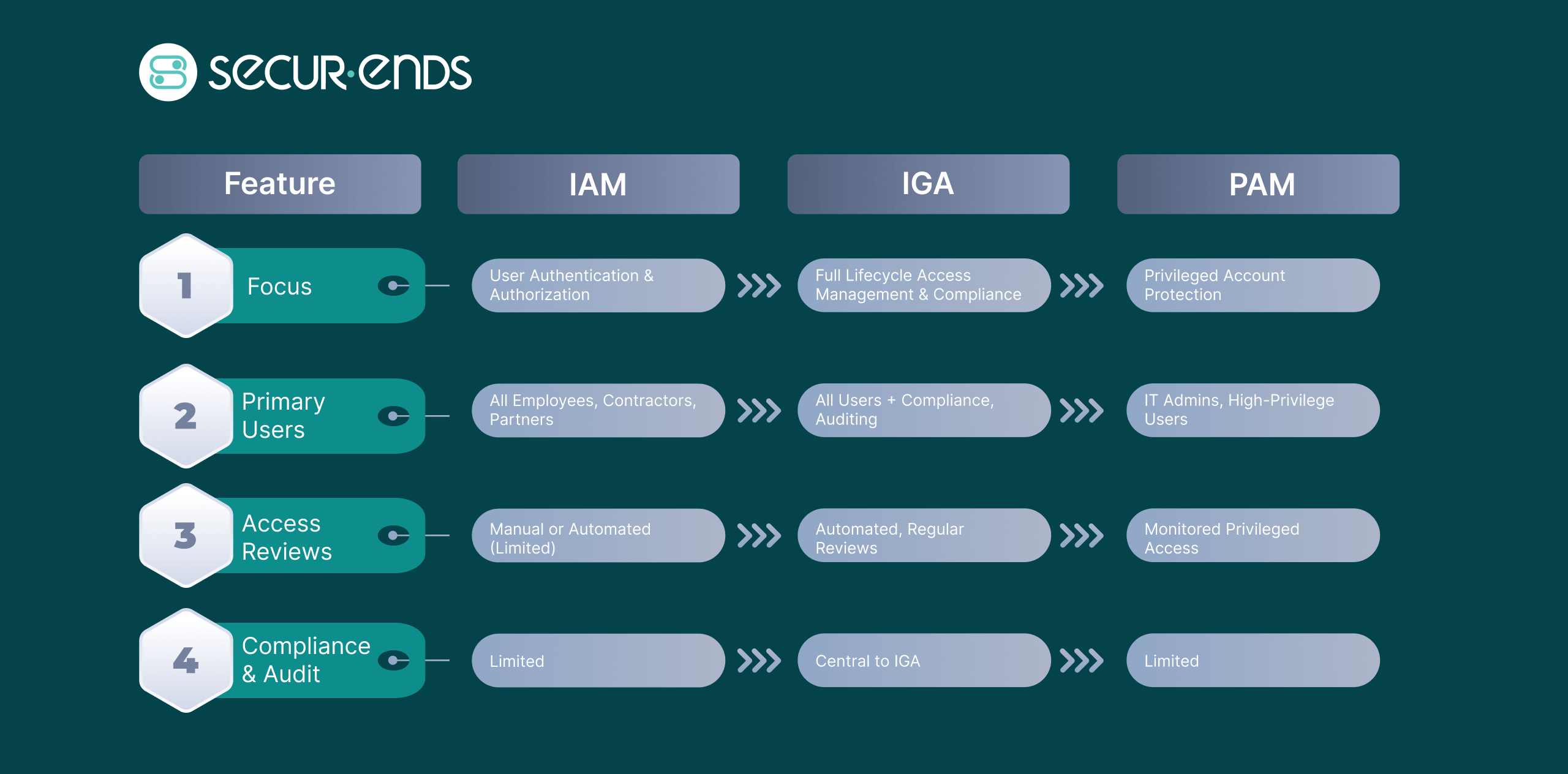
Key Differences in Scope
| Feature | IAM | IGA | PAM |
| Focus | User Authentication & Authorization | Full Lifecycle Access Management & Compliance | Privileged Account Protection |
| Primary Users | All Employees, Contractors, Partners | All Users + Compliance, Auditing | IT Admins, High-Privilege Users |
| Access Reviews | Manual or Automated (Limited) | Automated, Regular Reviews | Monitored Privileged Access |
| Compliance & Audit | Limited | Central to IGA | Limited |
IGA solutions go beyond the scope of IAM and PAM, offering a comprehensive governance approach that includes User access reviews, entitlement management, and integration with compliance frameworks such as GDPR, SOC 2, and HIPAA.
How SecurEnds Delivers Excellence in IGA
When it comes to Identity Governance and Administration (IGA), finding a solution that is both scalable and efficient is crucial. SecurEnds stands out in this space by providing an automated, seamless approach to managing user access and ensuring compliance. With integrations across leading platforms such as Okta, Workday, and ServiceNow, SecurEnds offers a comprehensive IGA solution designed to meet the demands of today’s security and compliance challenges.
SecurEnds Solutions: Okta, Workday, and ServiceNow Integration
SecurEnds’ IGA solutions are built to integrate smoothly with existing IT infrastructures, including popular platforms like Okta, Workday, and ServiceNow. These integrations ensure that organizations can leverage their existing tools while benefiting from the advanced capabilities of identity governance and administration.
- Okta: SecurEnds’ integration with Okta enhances identity management by automating user provisioning, de-provisioning, and access reviews. This integration provides real-time synchronization of user data, reducing manual intervention and improving the overall IGA process.
- Workday: For organizations using Workday for HR and finance management, SecurEnds offers seamless integration to automate the assignment of roles and responsibilities based on job functions. This ensures that employees are granted the right level of access based on their current role and department, aligning perfectly with identity governance best practices.
- ServiceNow: With ServiceNow integration, SecurEnds streamlines service management, ensuring that access requests and approvals are tracked and handled efficiently. This integration supports a unified view of user access across platforms, simplifying governance and compliance processes.
Features of SecurEnds’ IGA Solutions
SecurEnds offers several key features that set its IGA solutions apart from the competition:
- Automation: Automating access reviews and certifications helps reduce human error, save time, and ensure continuous compliance.
- Scalability: SecurEnds’ solutions scale with your organization, adapting to changing business needs and IT environments.
- Easy Integrations: Whether you’re using Okta, Workday, or ServiceNow, SecurEnds integrates seamlessly, enhancing your existing infrastructure without disruption.
Customer Success Stories
SecurEnds’ IGA solutions have been instrumental for businesses across various industries. For instance, a global financial services firm was able to automate its access certification process, reducing audit preparation time by 40% and improving compliance reporting. Another client, a large healthcare organization, streamlined its user access management, resulting in a 25% reduction in manual administrative work while improving security controls and compliance with HIPAA.
Key Features of SecurEnds’ IGA Solutions
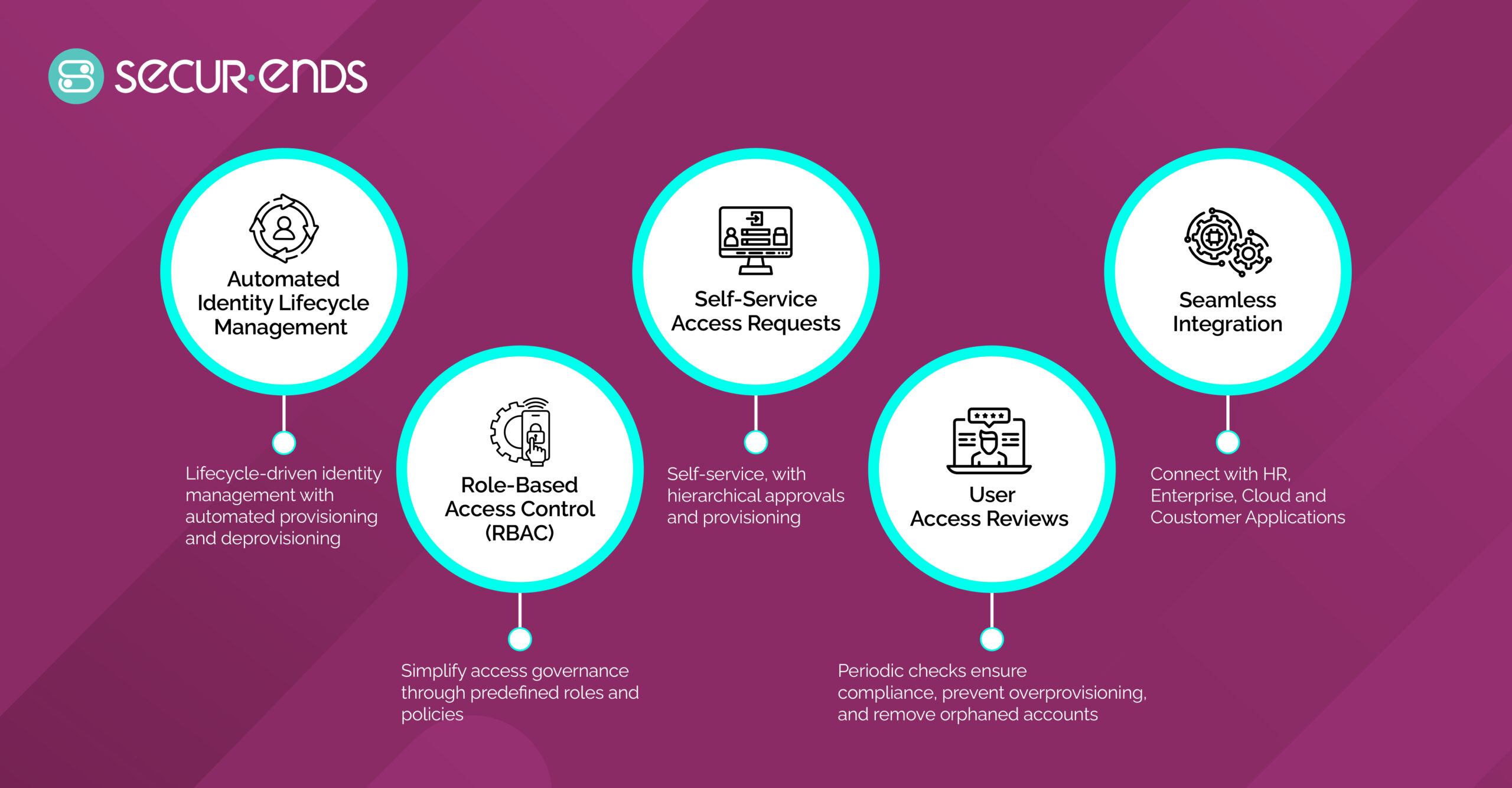
SecurEnds offers several standout features in its IGA solutions:
- Automation: Automating tasks like access reviews and certifications reduces manual workload and minimizes human errors, helping to maintain continuous compliance across your organization.
- Scalability: Whether you are a small business or a large enterprise, SecurEnds’ IGA solutions scale with your needs, adapting to changing requirements and supporting growth.
- Easy Integrations: SecurEnds seamlessly integrates with leading tools like Okta, Workday, and ServiceNow, enhancing your existing IT infrastructure while providing enhanced identity governance capabilities.
Customer Success Stories
Several organizations have benefitted from SecurEnds IGA solutions. For instance, a major financial institution was able to automate its access certification process, saving 40% of the time spent on audits and enhancing compliance reporting. A large healthcare provider also leveraged SecurEnds to streamline user access management, reducing administrative workload by 25% while strengthening HIPAA compliance.
Best Practices for Implementing Identity Governance
Implementing Identity Governance and Administration (IGA) is a strategic initiative that can significantly enhance your organization’s security, compliance, and operational efficiency. To ensure a successful IGA deployment, it’s essential to follow best practices that align with your business goals and regulatory requirements. Below are some key steps and strategies for establishing a strong IGA framework.
1. Define Clear Access Policies
The first step in implementing a robust IGA solution is to define clear access policies. This includes determining who should have access to what resources, under what conditions, and for how long. Establish role-based access control (RBAC) to categorize users based on their job functions and grant them access to the data they need to perform their tasks.
How It Helps: By clearly defining access policies, your organization ensures that only the right users have access to the right resources. This reduces the risk of privilege creep and ensures compliance with regulations such as GDPR and HIPAA.
2. Conduct Regular User Access Reviews
Regular user access reviews are a cornerstone of identity governance and administration. These reviews help ensure that user access is aligned with their current roles and responsibilities. Set up automated workflows to prompt periodic reviews, which can be scheduled at regular intervals or triggered by specific events, such as role changes or employee departures.
How It Helps: Automated access reviews not only improve security by ensuring that only authorized users have access, but they also save time and reduce manual effort. This contributes to more efficient compliance with industry regulations and audit requirements.
3. Prevent Entitlement Creep
Entitlement creep occurs when users accumulate excessive permissions over time, often due to job changes or departmental shifts. Over time, this can lead to unnecessary access to sensitive data, posing significant security risks. To combat entitlement creep, implement automated workflows for regularly reviewing and adjusting user access based on their role.
How It Helps: By regularly reviewing and adjusting user entitlements, you reduce the risk of over-provisioned access and maintain a principle of least privilege. This ensures compliance with identity governance best practices and minimizes exposure to data breaches.
4. Automate Access Requests and Approvals
Manual access requests and approvals can be slow and prone to error, leading to unnecessary delays and operational inefficiencies. By automating the access request process, you not only speed up workflows but also ensure that requests are consistently evaluated against established policies.
How It Helps: Automation streamlines the access request process, improving operational efficiency while ensuring compliance with identity governance policies. It also reduces the workload on IT staff and provides a more seamless experience for users requesting access.
5. Integrate with Existing IT Systems
A successful IGA implementation requires seamless integration with your existing IT systems, including HR systems, directories, and enterprise applications. This integration allows you to manage user identities and access across all platforms, ensuring consistency and reducing manual errors.
How It Helps: Integrating IGA solutions with your existing IT infrastructure helps centralize access control and ensures that identity data is consistently updated across all systems. It also improves scalability and enhances identity governance and administration capabilities as your organization grows.
6. Ensure Continuous Monitoring and Auditing
Continuous monitoring and auditing are crucial components of any IGA strategy. Implement automated tools to track user activity, monitor access patterns, and detect anomalies. These tools should also provide the ability to generate detailed reports for audits and compliance reviews.
How It Helps: Continuous monitoring enhances security by allowing your organization to identify potential threats in real-time. Automated audits ensure that access control policies are being followed and provide the necessary documentation for regulatory compliance.
Best Practices for IGA Implementation
1. Secure Leadership Buy-In
A top-down approach ensures IGA receives the necessary resources and attention. Involve executive leadership to drive commitment and adherence to governance policies.
2. Conduct Employee Training and Awareness Programs
Educate employees on IAM risk management, access management best practices, security risks, and compliance obligations. Regular training enhances awareness and reduces security vulnerabilities.
3. Establish a Feedback Loop for Continuous Improvement
Encourage ongoing feedback from employees and stakeholders. Regularly refine IGA policies based on evolving organizational needs and emerging security threats.
A strong IGA framework enhances security, compliance, and operational efficiency. By regularly reviewing user access, preventing entitlement creep, and integrating IGA with existing IT systems, organizations can successfully implement IGA best practices while ensuring long-term sustainability.
Industry-Specific Use Cases for IGA
Identity Governance and Administration (IGA) is critical for organizations across various industries, each with its own unique regulatory and operational challenges. Implementing IGA solutions ensures that businesses meet compliance standards while managing user access effectively. Below are some industry-specific use cases for IGA that demonstrate its versatility and effectiveness.
1. Financial Institutions (SOX, PCI)
Financial institutions are subject to stringent regulations like SOX (Sarbanes-Oxley) and PCI DSS (Payment Card Industry Data Security Standard). These regulations require robust controls over user access to sensitive financial data. IGA plays a pivotal role in ensuring that only authorized users can access financial records, preventing fraud, and simplifying audit processes.
How IGA Helps: By implementing IGA solutions, financial institutions can automate access reviews, enforce role-based access controls, and ensure compliance with SOX and PCI DSS. This not only strengthens security but also streamlines compliance reporting.
2. Healthcare (HIPAA, HITRUST)
In the healthcare sector, protecting patient data is a top priority. Healthcare organizations must comply with strict regulations such as HIPAA (Health Insurance Portability and Accountability Act) and HITRUST. IGA solutions help ensure that patient information is only accessible to authorized medical professionals and that access is revoked promptly when it’s no longer needed.
How IGA Helps: IGA solutions help healthcare providers automate user access reviews, manage entitlement creep, and maintain an audit trail of who accessed patient data. This ensures compliance with HIPAA and HITRUST, protecting patient privacy while also reducing administrative burden.
3. Small and Medium-Sized Businesses (SMBs)
For SMBs, managing user access can be challenging due to limited resources. However, IGA solutions can help SMBs implement efficient access control measures without overwhelming their IT teams. These solutions help SMBs scale securely, ensuring that users have the right level of access as the business grows.
How IGA Helps: IGA solutions help SMBs implement scalable access controls, automate compliance processes, and reduce the administrative overhead associated with managing user access. By adopting IGA, SMBs can improve security and ensure they stay compliant with regulations, even as they grow.
4. Government & Public Sector (FedRAMP, CJIS)
Government organizations and public sector agencies handle highly sensitive data, which makes security and compliance even more critical. With regulations like FedRAMP (Federal Risk and Authorization Management Program) and CJIS (Criminal Justice Information Services), these agencies need strict access controls and continuous monitoring.
How IGA Helps: IGA solutions enable public sector organizations to enforce access policies, automate access reviews, and ensure that only authorized personnel can access sensitive government data. By streamlining compliance with FedRAMP and CJIS, these solutions help mitigate risks and enhance security across government systems.
5. Hybrid IT Enterprises
As organizations adopt hybrid IT environments that combine on-premises and cloud-based systems, managing user access becomes more complex. IGA helps unify access control across both environments, ensuring that policies are consistent, regardless of where the data is stored.
How IGA Helps: IGA solutions provide enterprises with the tools to manage access across both cloud and on-premises systems, ensuring consistent policies and compliance. This centralized approach to identity governance and administration simplifies the management of hybrid IT environments, reducing security risks.
Solving Cross-Application Challenges with IGA
In today’s increasingly complex IT environments, managing user access across multiple applications can be a daunting task. Organizations often struggle with ensuring consistent access control, especially when applications are spread across on-premises, cloud, and hybrid environments. Identity Governance and Administration (IGA) helps solve these cross-application challenges by providing a centralized approach to managing access and ensuring compliance across all systems.
1. Eliminating Cross-Application Segregation of Duties (SoD) Violations
Segregation of Duties (SoD) is a critical control that helps prevent fraud and errors by ensuring that no individual has control over two or more conflicting tasks. For example, a user who can initiate payments should not have the ability to approve those payments. Cross-application SoD violations occur when users have conflicting access rights across multiple systems.
How IGA Helps: IGA solutions provide SoD controls across all integrated applications, automatically flagging and preventing conflicting access assignments. By enforcing SoD policies in a centralized manner, organizations can reduce the risk of fraud, ensure compliance with internal controls, and maintain a clear audit trail for all access activities.
2. Streamlining Hybrid IT Access
With organizations increasingly adopting hybrid IT infrastructures, managing access across both on-premises and cloud-based systems becomes increasingly complex. IGA solutions provide a unified approach to access management, allowing businesses to apply consistent policies across all platforms.
How IGA Helps: By integrating IGA tools with both on-premises and cloud applications, organizations can streamline identity governance across disparate systems. This ensures that access rights are consistently applied, helping to manage risk and simplify compliance with GDPR, HIPAA, and other regulatory requirements. Hybrid IT access is more manageable, and security is enhanced through unified controls.
3. Automating Legacy System Integration
Many organizations still rely on legacy IT systems that were not built to integrate with modern IGA solutions. This creates challenges in managing user access across new and old platforms. Without proper integration, businesses are left with security gaps and administrative inefficiencies.
How IGA Helps: Modern IGA solutions offer seamless integration with legacy systems, ensuring that access management policies are enforced across all platforms. Through integration, IGA tools help automate processes such as user provisioning, de-provisioning, and role assignments, reducing the burden on IT teams and ensuring consistent identity governance and administration.
4. Automating Legacy Identity Management Solutions
Legacy Identity and Access Management (IAM) systems often struggle to keep up with the demands of modern business environments, especially as organizations scale. IGA solutions help automate and modernize legacy IAM systems, providing better controls and ensuring compliance.
How IGA Helps: With IGA tools, organizations can automate critical identity and access management functions that were previously handled manually. This includes user provisioning, access reviews, and role-based access assignments, all of which can be streamlined to enhance the security of legacy systems while maintaining full compliance.
2026 Trends in Identity Governance & Administration
The world of Identity Governance and Administration (IGA) is constantly evolving to keep up with technological advancements and regulatory changes. In 2026, several key trends are shaping the future of IGA solutions. These trends are driven by the growing complexity of IT environments, increasing compliance requirements, and the need for enhanced security measures. Understanding these trends is crucial for organizations looking to stay ahead of the curve and strengthen their identity governance and administration frameworks.
1. AI-Driven Identity Analytics
Artificial intelligence (AI) is transforming identity governance and administration by enabling smarter, data-driven decisions. AI-driven identity analytics use machine learning algorithms to analyze vast amounts of user data, detect anomalous behaviors, and predict potential security risks.
How It Helps: AI-powered identity governance tools can identify patterns in user behavior that may indicate a security breach or policy violation. By leveraging AI-driven identity analytics, organizations can proactively address risks, improve the accuracy of access reviews, and automate remediation processes, leading to more efficient and secure IGA.
2. Cloud & SaaS IGA Expansion
As more organizations move their operations to the cloud, the demand for cloud-based IGA solutions has grown significantly. Cloud IGA platforms offer flexibility, scalability, and better integration with modern applications, making them essential for businesses with hybrid or fully cloud-based IT environments.
How It Helps: Cloud-based IGA solutions simplify the management of user access across cloud and on-premises systems. These solutions provide centralized identity governance for cloud applications, allowing businesses to manage user access and ensure compliance with ease. As cloud services continue to dominate, cloud IGA will play a crucial role in securing sensitive data and simplifying access management.
3. IGA & Zero Trust Convergence
Zero Trust has become a core security model for organizations looking to protect against evolving threats. This model assumes that no user or device, whether inside or outside the network, should be trusted by default. The convergence of IGA and Zero Trust ensures that user access is continually verified, reducing the risk of data breaches.
How It Helps: Integrating IGA solutions with Zero Trust principles allows organizations to ensure that user access is continuously monitored, validated, and adjusted based on risk. By combining Zero Trust with identity governance, organizations can implement stricter access controls and mitigate the impact of compromised credentials.
4. Regulatory Shifts (DORA, SEC Rules)
Regulatory frameworks continue to evolve to keep pace with the digital transformation of businesses. In 2026, regulations like DORA (Digital Operational Resilience Act) and new SEC rules for cybersecurity disclosures are expected to have a significant impact on identity governance and administration.
How It Helps: As compliance requirements tighten, IGA solutions will help organizations stay aligned with new regulatory rules. For example, DORA focuses on ensuring that financial institutions have strong operational resilience, which includes ensuring robust access controls and identity management. IGA tools enable organizations to track and report on compliance, reducing the burden of regulatory reporting and mitigating risks related to non-compliance.
5. Automation and Self-Service Features
Automation continues to be a driving force in the evolution of identity governance. In 2026, more IGA solutions will feature self-service capabilities, allowing users to request access, reset passwords, and manage their roles without involving IT teams. This self-service approach reduces the workload on IT administrators and improves operational efficiency.
How It Helps: Automated self-service features empower users while maintaining control over identity governance policies. By automating routine access tasks, IGA solutions enable faster response times, reduce errors, and ensure that users have the right access when they need it, without compromising security.
Managing Identity Governance in Hybrid IT Environments
As organizations continue to adopt hybrid IT environments that combine on-premises infrastructure with cloud-based systems, managing identity governance and administration across these disparate environments becomes increasingly complex. The traditional methods of identity management are no longer sufficient to handle the unique challenges of hybrid IT, and organizations need more advanced IGA solutions to ensure seamless, secure access control.
1. Challenges in Hybrid IT
Hybrid IT environments introduce a variety of challenges for identity governance:
- Complex Access Management: Managing user access across both on-premises and cloud-based systems can result in inconsistent access policies and difficulty in tracking permissions.
- Data Silos: With data distributed across multiple systems, ensuring consistent access and compliance is difficult, leading to potential gaps in security.
- Integration Complexity: Legacy systems and modern cloud applications often don’t integrate seamlessly, making it challenging to enforce consistent identity governance policies.
2. Tools for Hybrid Governance
To address these challenges, organizations can turn to identity governance and administration (IGA) solutions specifically designed to work across hybrid IT environments. These solutions provide the tools needed to manage access, enforce security policies, and ensure compliance, no matter where the data resides. Key features include:
- Unified Access Control: IGA tools provide a centralized platform to manage user access across both cloud and on-premises systems. This ensures consistent enforcement of policies and reduces the risk of security gaps.
- Integration with Legacy Systems: Many IGA solutions are designed to integrate with both modern cloud applications and legacy on-premises systems. This enables organizations to maintain strong identity governance controls without replacing existing infrastructure.
- Real-Time Monitoring: Advanced IGA solutions offer real-time monitoring and auditing capabilities, which is essential for detecting anomalies in hybrid environments and ensuring compliance with industry regulations.
3. Automation Benefits in Hybrid IT
One of the key advantages of using IGA solutions in a hybrid IT environment is automation. By automating processes such as user access reviews, role-based access control (RBAC), and compliance checks, businesses can:
- Improve Efficiency: Automation reduces the time spent on manual tasks, such as manually reviewing user access or assigning roles, freeing up IT resources for more strategic activities.
- Minimize Human Error: Automating critical access management tasks reduces the risk of human error, ensuring that access rights are consistently enforced.
- Enhance Compliance: Automated compliance checks and access reviews ensure that organizations meet regulatory requirements without relying on error-prone manual processes.
4. The Role of IGA in Securing Hybrid IT Environments
In a hybrid IT setup, IGA solutions help ensure that security is not compromised as organizations extend their infrastructure to the cloud. By providing real-time insights into user access and activity across both on-premises and cloud applications, these solutions enable organizations to:
- Detect Potential Security Risks: IGA solutions continuously monitor access activity, identifying unusual patterns that may signal security threats or compliance violations.
- Ensure Continuous Compliance: Automated reporting and real-time auditing ensure that identity governance policies are adhered to, helping organizations remain compliant with regulations like GDPR, HIPAA, and SOC 2, even in hybrid environments.
Why Identity Governance and Administration (IGA) Is Critical for Modern Enterprises
With enterprises managing users across cloud, on-prem, and hybrid environments, IGA has become a foundational layer of secure and governed access control. It shifts identity management from basic authentication toward structured oversight, policy enforcement, and continuous validation of user entitlements.
Enhances Security
By enforcing least-privilege access and continuously validating entitlements, IGA reduces the risk of excessive permissions and access creep. It strengthens defense against credential misuse and insider threats by ensuring access remains aligned with business need.
Strengthens Regulatory Readiness
Regulatory frameworks such as GDPR, HIPAA, and HITRUST require demonstrable access governance and periodic reviews. IGA enables organizations to produce structured audit evidence, maintain traceable approval records, and validate access controls with confidence.
Improves Governance Visibility
A centralized view of identities and entitlements provides leadership and security teams with measurable insight into identity risk. Real-time visibility into who has access — and why — reduces orphaned accounts and high-risk exposure.
Supports Scalable Growth
As organizations expand, adopt new applications, and restructure teams, access governance must scale accordingly. IGA supports dynamic role models and lifecycle-based policies that adapt to workforce and infrastructure changes.
Enables Controlled Agility
Through structured workflows, delegated approvals, and automated provisioning, IGA balances governance with operational efficiency. Teams gain timely access without compromising oversight or compliance integrity.
IGA is no longer only about access control — it is about maintaining governed, defensible identity practices at enterprise scale.
Integrating Identity Governance with Existing Tools
For organizations seeking to enhance their Identity Governance and Administration (IGA) processes, integrating IGA solutions with existing tools and systems is essential. Many businesses already use platforms like Okta, Workday, and ServiceNow to manage their workforce, security, and IT service management. By seamlessly integrating identity governance with these tools, organizations can simplify their access management processes, reduce operational complexity, and improve security.
1. Okta Integration for Seamless Identity Management
Okta is a popular identity management platform used by organizations to manage user identities and access to applications. Integrating Okta with an IGA solution allows businesses to automate processes such as user provisioning, de-provisioning, and access reviews, ensuring that access rights are consistently applied across all systems.
How It Helps: By integrating Okta with IGA solutions, businesses can centralize identity management and automate the enforcement of access policies. This reduces manual intervention, enhances security, and ensures compliance with regulations like GDPR and HIPAA.
2. Workday Integration for HR and Compliance
Workday is an enterprise software platform used for human resources and financial management. IGA solutions can be integrated with Workday to automate the process of assigning and managing user roles based on employee job functions. This ensures that access rights are aligned with an employee’s role within the organization, simplifying compliance management and reducing the risk of entitlement creep.
How It Helps: Integration with Workday ensures that when employees change roles, departments, or leave the organization, their access rights are automatically updated, reducing the risk of unauthorized access to sensitive data. It also helps maintain identity governance best practices by aligning access with up-to-date employee records.
3. ServiceNow Integration for IT Service Management
ServiceNow is widely used for IT service management, helping businesses automate workflows and manage incidents, changes, and service requests. Integrating ServiceNow with IGA solutions allows organizations to automate access request workflows and track user access across different systems and applications.
How It Helps: Integration with ServiceNow ensures that access requests are tracked, approved, and provisioned based on established policies. This reduces the time spent on manual access management, improves efficiency, and ensures that access rights are granted consistently according to identity governance policies.
4. Benefits of Integration for Scalability and Security
Integrating IGA solutions with existing tools like Okta, Workday, and ServiceNow offers several benefits:
- Scalability: As your organization grows, integrating IGA solutions with existing systems ensures that access management scales with your needs. Whether you’re adding new users or expanding to new platforms, integration helps maintain consistent access control policies.
- Improved Security: Integration ensures that access rights are enforced uniformly across all platforms, reducing the risk of human error and unauthorized access to sensitive data. Automated workflows and access reviews improve the security posture of your organization.
Streamlined Compliance: By integrating IGA solutions with compliance-focused platforms like Workday and ServiceNow, businesses can streamline the process of tracking and reporting compliance with industry regulations. Automated reports help
Top Identity Governance and Administration Tools
Selecting the right Identity Governance and Administration (IGA) tools is essential for organizations aiming to streamline access management, improve security, and ensure compliance with industry regulations. With the wide range of IGA solutions available today, it’s important to understand the features and benefits of the leading tools in the market. Below, we explore some of the top identity governance and administration tools that can help organizations manage user access and safeguard critical data.
1. SecurEnds IGA Solutions
SecurEnds provides a comprehensive suite of IGA solutions designed to help businesses automate and streamline user access management. With features like automated access reviews, role-based access control (RBAC), and seamless integration with tools like Okta, Workday, and ServiceNow, SecurEnds offers a powerful platform for managing identity governance across complex IT environments.
Strengths:
- Seamless integration with existing IT tools like Okta and Workday.
- Automated access reviews and entitlement management.
- Scalable solutions that adapt to growing organizational needs.
Best Fit: Ideal for businesses looking for an integrated IGA solution that works with existing infrastructure, providing comprehensive access control and compliance management.
2. SailPoint
SailPoint is one of the leading identity governance solutions that offers a wide range of features for automating user access and ensuring compliance. SailPoint’s identity governance and administration software provides robust tools for managing roles, entitlements, and access requests, all while delivering insights into access patterns and security risks.
Strengths:
- Advanced analytics and AI-driven identity governance.
- Flexible deployment options (cloud, on-premises).
- Strong support for regulatory compliance (GDPR, HIPAA).
Best Fit: Ideal for organizations with complex access requirements, looking for a solution that combines automation, compliance, and security.
3. Saviynt
Saviynt is another top IGA solution provider that focuses on automating identity governance and improving access control across hybrid IT environments. Its cloud-native platform offers integrated identity governance, identity management, and access governance features, making it easy for organizations to secure their applications and data.
Strengths:
- Cloud-native platform with advanced security features.
- User-friendly interface for administrators.
- Detailed audit trails for compliance and reporting.
Best Fit: Suitable for enterprises looking to secure both on-premises and cloud-based applications with an integrated identity governance solution.
4. Oracle Identity Governance
Oracle offers a comprehensive identity governance solution that provides centralized control over user access across enterprise applications. With a focus on compliance and security, Oracle’s IGA tools enable organizations to enforce access policies, automate reviews, and ensure regulatory compliance.
Strengths:
- Strong integration with enterprise systems, including Oracle Cloud.
- Powerful reporting and analytics tools for compliance tracking.
- Robust risk management capabilities.
Best Fit: Ideal for organizations using Oracle products and looking for a unified IGA solution to manage access across their enterprise applications.
5. CyberArk
CyberArk is well-known for its focus on Privileged Access Management (PAM), but it also offers robust identity governance capabilities. CyberArk’s IGA solution ensures that high-privilege accounts are managed securely and that access to sensitive systems and data is tightly controlled.
Strengths:
- Focus on Privileged Access Management for high-risk accounts.
- Comprehensive monitoring and auditing tools.
- Advanced security features to protect critical data.
Best Fit: Ideal for organizations needing enhanced security for privileged accounts while also managing broader identity governance requirements.
Comparison Table:
| Tool | Strengths | Best Fit |
| SecurEnds | Seamless integration, automated reviews | Integrated solution for growing organizations |
| SailPoint | AI-driven insights, flexible deployment | Complex organizations with compliance needs |
| Saviynt | Cloud-native, security-focused | Hybrid IT environments |
| Oracle | Enterprise integration, robust reporting | Organizations using Oracle systems |
| CyberArk | Privileged access management, auditing | High-security needs, privileged access |
Benefits of IGA for Organizations
Implementing Identity Governance and Administration (IGA) brings a host of benefits to organizations, enhancing security, improving compliance, and optimizing operational efficiency. As businesses face increasing security threats and regulatory pressures, the advantages of adopting a comprehensive IGA solution have become undeniable. Below are the key benefits of IGA and how it helps organizations achieve their strategic goals.
1. Improved Compliance (GDPR, HIPAA, HITRUST)
One of the primary benefits of IGA is its ability to help organizations stay compliant with a wide range of regulatory standards, including GDPR, HIPAA, SOX, and HITRUST. IGA solutions streamline the process of managing access rights and ensure that sensitive data is only accessible by authorized individuals. Regular access reviews, automated audits, and detailed reporting features enable businesses to meet stringent regulatory requirements more efficiently.
How It Helps: By automating access reviews and enforcing compliance policies, IGA solutions reduce the risk of human error and ensure that all access permissions are in line with regulatory standards. This leads to fewer compliance gaps, mitigating the risk of penalties and reputational damage.
2. Operational Efficiency
IGA solutions enhance operational efficiency by automating many of the manual tasks traditionally associated with user access management. From provisioning and de-provisioning users to performing regular access reviews, automation reduces administrative overhead and allows IT teams to focus on more strategic initiatives.
How It Helps: By automating tasks like role assignments, user access provisioning, and periodic access certifications, IGA solutions save time and reduce errors. This leads to more efficient workflows, quicker onboarding for new users, and faster response times when access adjustments are needed.
3. Reduced Risk of Breaches
The principle of least privilege, enforced by IGA solutions, ensures that users only have access to the data they need to perform their jobs. By preventing users from accumulating unnecessary access rights (a phenomenon known as entitlement creep), IGA tools significantly reduce the potential for security breaches.
How It Helps: IGA solutions help maintain tight access controls, limiting the exposure of sensitive data to only those users who require it. This minimizes the risk of data leaks, breaches, and insider threats, making it easier to protect the organization’s most critical assets.
4. Better User Experience
While identity governance focuses on security and compliance, it also improves the user experience by providing self-service access features. Employees can request access to applications and systems without waiting for manual approval from IT teams. Self-service password resets, access requests, and role modifications enhance user satisfaction and reduce bottlenecks.
How It Helps: By allowing users to request and manage their own access through self-service features, organizations can ensure that employees have quicker, easier access to the tools and resources they need, improving overall productivity and reducing frustration.
5. Streamlined Auditing and Reporting
IGA solutions provide organizations with automated tools to track and report on user access. With detailed auditing capabilities, businesses can generate reports that show who has access to what resources, when they accessed them, and whether that access is still appropriate. This is invaluable for security teams and auditors, especially when preparing for regulatory audits or investigating potential security incidents.
How It Helps: With IGA solutions, auditing becomes a more streamlined process. Automated reports and real-time access logs ensure that businesses can easily demonstrate compliance and quickly respond to potential security threats or audit requests. This enhances transparency and simplifies reporting to regulatory bodies.
Conclusion
Implementing Identity Governance and Administration (IGA) brings a host of benefits to organizations, enhancing security, improving compliance, and optimizing operational efficiency. As businesses face increasing security threats and regulatory pressures, the advantages of adopting a comprehensive IGA solution have become undeniable. Below are the key benefits of IGA and how it helps organizations achieve their strategic goals.
1. Improved Compliance (GDPR, HIPAA, HITRUST)
One of the primary benefits of IGA is its ability to help organizations stay compliant with a wide range of regulatory standards, including GDPR, HIPAA, SOX, and HITRUST. IGA solutions streamline the process of managing access rights and ensure that sensitive data is only accessible by authorized individuals. Regular access reviews, automated audits, and detailed reporting features enable businesses to meet stringent regulatory requirements more efficiently.
How It Helps: By automating access reviews and enforcing compliance policies, IGA solutions reduce the risk of human error and ensure that all access permissions are in line with regulatory standards. This leads to fewer compliance gaps, mitigating the risk of penalties and reputational damage.
2. Operational Efficiency
IGA solutions enhance operational efficiency by automating many of the manual tasks traditionally associated with user access management. From provisioning and de-provisioning users to performing regular access reviews, automation reduces administrative overhead and allows IT teams to focus on more strategic initiatives.
How It Helps: By automating tasks like role assignments, user access provisioning, and periodic access certifications, IGA solutions save time and reduce errors. This leads to more efficient workflows, quicker onboarding for new users, and faster response times when access adjustments are needed.
3. Reduced Risk of Breaches
The principle of least privilege, enforced by IGA solutions, ensures that users only have access to the data they need to perform their jobs. By preventing users from accumulating unnecessary access rights (a phenomenon known as entitlement creep), IGA tools significantly reduce the potential for security breaches.
How It Helps: IGA solutions help maintain tight access controls, limiting the exposure of sensitive data to only those users who require it. This minimizes the risk of data leaks, breaches, and insider threats, making it easier to protect the organization’s most critical assets.
4. Better User Experience
While identity governance focuses on security and compliance, it also improves the user experience by providing self-service access features. Employees can request access to applications and systems without waiting for manual approval from IT teams. Self-service password resets, access requests, and role modifications enhance user satisfaction and reduce bottlenecks.
How It Helps: By allowing users to request and manage their own access through self-service features, organizations can ensure that employees have quicker, easier access to the tools and resources they need, improving overall productivity and reducing frustration.
5. Streamlined Auditing and Reporting
IGA solutions provide organizations with automated tools to track and report on user access. With detailed auditing capabilities, businesses can generate reports that show who has access to what resources, when they accessed them, and whether that access is still appropriate. This is invaluable for security teams and auditors, especially when preparing for regulatory audits or investigating potential security incidents.
How It Helps: With IGA solutions, auditing becomes a more streamlined process. Automated reports and real-time access logs ensure that businesses can easily demonstrate compliance and quickly respond to potential security threats or audit requests. This enhances transparency and simplifies reporting to regulatory bodies.
FAQs about Identity Governance and Administration
As organizations continue to implement Identity Governance and Administration (IGA) solutions, many questions arise regarding the functionality, implementation, and benefits of these systems. Below, we address some of the most frequently asked questions about IGA to help clarify its role and importance in modern access management.
1. What is IGA in cybersecurity?
Identity Governance and Administration (IGA) is a framework that enables organizations to manage and control user access to sensitive data and systems in a secure, compliant, and automated manner. IGA solutions ensure that users have the appropriate level of access based on their role within the organization and that access is continually reviewed to prevent unauthorized access and potential breaches.
2. How does IGA differ from IAM and PAM?
While Identity Access Management (IAM) focuses on the authentication and authorization of users, and Privileged Access Management (PAM) focuses specifically on high-privilege accounts, IGA provides a more comprehensive approach. IGA combines the capabilities of IAM and PAM, ensuring that all user access—whether privileged or regular—is managed, reviewed, and compliant with regulations. IGA also includes features like access reviews, entitlement management, and compliance reporting.
3. What are examples of IGA tools?
Some of the leading IGA tools include:
- SecurEnds: An integrated solution for automating access reviews, role-based access control (RBAC), and ensuring compliance with regulatory standards.
- SailPoint: A comprehensive platform for identity governance and compliance, featuring AI-driven insights and automation.
- Saviynt: A cloud-native IGA solution for managing identity governance in hybrid IT environments.
- Okta: While primarily an IAM tool, Okta integrates well with IGA solutions, offering user provisioning, access reviews, and compliance features.
4. Why is IGA important in 2026?
As organizations increasingly adopt hybrid IT environments and face more stringent regulatory requirements, IGA becomes essential for securing sensitive data and ensuring compliance. With the rise of Zero Trust models, automation, and AI-driven insights, IGA solutions help organizations manage complex access controls, improve operational efficiency, and reduce the risk of breaches in 2026 and beyond.
5. How does IGA support Zero Trust?
IGA supports Zero Trust by ensuring that access is continuously verified, even for users already inside the network. With Zero Trust principles, no one is trusted by default, and IGA solutions enforce this by implementing strict access controls, continuous monitoring, and automated reviews. This ensures that users only have access to the resources they need, reducing the risk of unauthorized access and insider threats.
6. Can IGA be implemented in a cloud environment?
Yes, IGA solutions are essential for managing user access in cloud environments. As organizations move to the cloud, IGA ensures that access is appropriately controlled, even as users and applications are distributed across on-premises and cloud-based systems. Many modern IGA tools are designed to work seamlessly with cloud platforms like AWS, Microsoft Azure, and Google Cloud, providing consistent and automated access management across all environments.
7. How often should access reviews be conducted in IGA?
The frequency of access reviews depends on the organization’s regulatory requirements and internal policies. However, it’s recommended to conduct access reviews at least quarterly or annually. Automating these reviews with IGA solutions ensures that they occur regularly and consistently, reducing the risk of unauthorized access and improving compliance with industry regulations.
8. What is the role of automation in IGA?
Automation plays a critical role in IGA by streamlining manual tasks such as user provisioning, access reviews, and entitlement management. Automated workflows help reduce the risk of human error, save time, and ensure that access is continuously aligned with users’ roles and responsibilities. IGA solutions leverage automation to improve security, efficiency, and compliance, making it easier to manage large numbers of users and access rights.


