Increase M&A Agility
Mitigate Cybersecurity Risk For Successful M&A
CISOs are achieving cybersecurity, privacy and compliance postures for target organizations using SecurEnds
M&A Agility
Challenge
Access reviews during the due diligence phase or post-integration are extremely critical for the eventual success of any M&A deal. Why? Any orphan or unused account presents a cyber risk vulnerability waiting to be exploited by hackers. Marriott’s acquisition of Starwood Group was marked with one such
incident hackers stole data of approximately 500million customers. The attackers remained in the system after Marriott acquired Starwood in 2016 and were not discovered until September 2018.
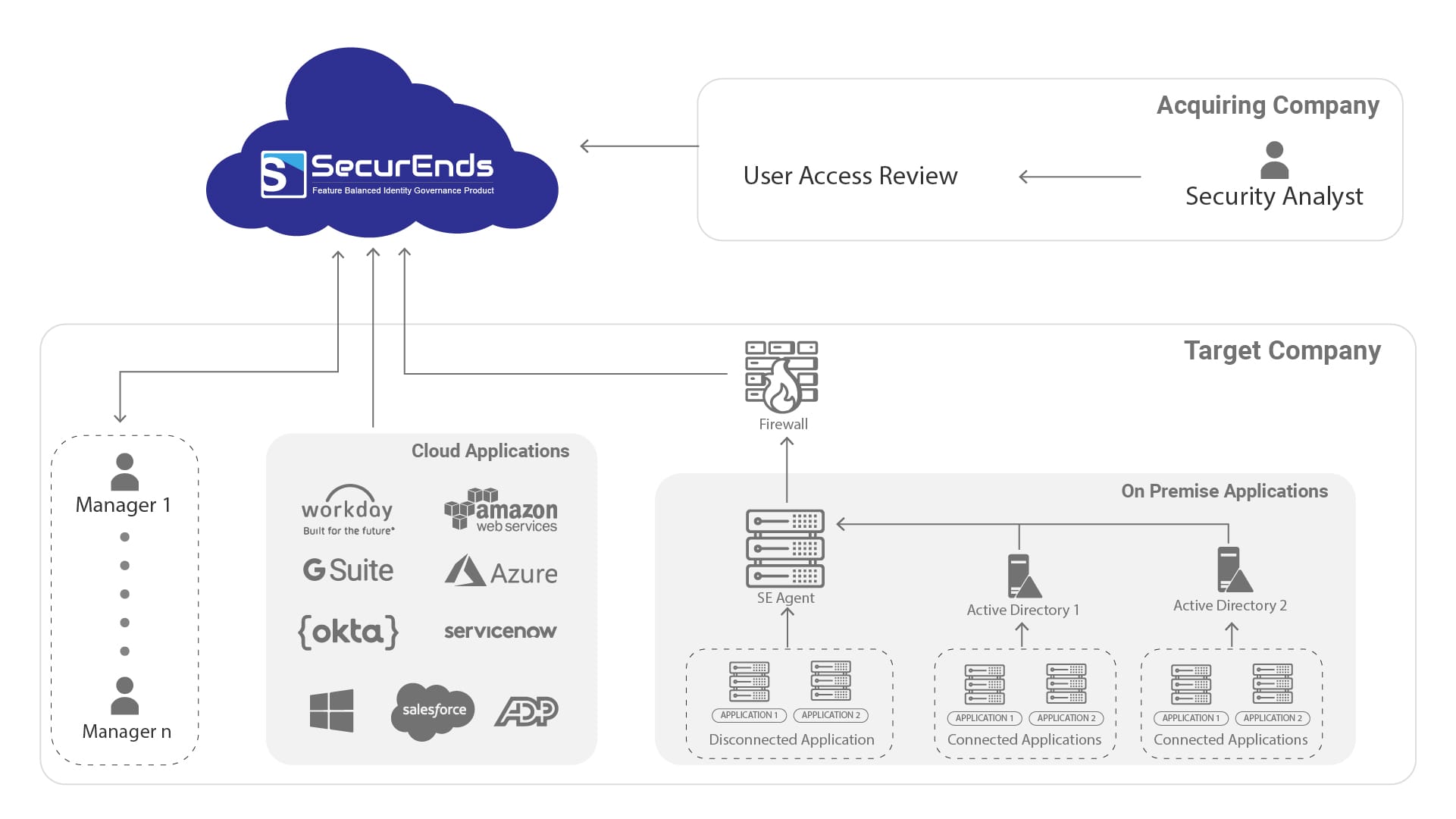
Our Approach
We recently put together a comprehensive access and entitlement review program for a financial services institution to help its M&A department stay on point. Using SecurEnds CEM and ILM, a multi-tenant, SaaS module, we created powerful governance and provisioning/ de-provisioning solution that will be used by the M&A team to evaluate and remediate potential attack vectors. The CEM module will allow recurring automated access review campaigns that validate users within systems and ensure their access rights are appropriate while the ILM module will drive the management of dormant and orphan accounts.
Product Features
- Create single source of truth by connecting to single or multiple HR systems such as ADP etc
- Easily connect enterprise applications (Epic, Citrix, Oracle etc), files (unstructured data) etc
- Connect custom applications using database,web-api, script based flex-connectors
- Match identities with user credentials across healthcare systems using pattern matching fuzzy logic.
- Set up attribute based access review campaigns for heartbeat accounts and service accounts.
- Schedule onetime or delta reviews across applications, group of application or attributes.
- Send reminder emails to reviewers , review and managers.
- Integrate with service management systems (ServiceNow, Jira etc) to trigger employee termination workflow
- Generate proof of compliance reports for auditors.
- Easy to drill down Identity MindMaps to see “who has access to what data”.
Our Results
Legal Services
A leading Law Services firm consolidated multiple active directories across its acquisitions
Commercial Bank
A big five Financial Services client conducted accelerated user access reviews on target companies
Healthcare
A Fortune 1000 client discovered 200 over-provisioned and orphan accounts.
Flexible Options
Buy Side License
Organizations that make recurring strategic purchases can use SecurEnds software during the due diligence and post acquisition Identity Access Management integration. Our software with its flexible deployment models tailored to fit a variety of environments and industries helps organizations internal M&A group build a repeatable program.
Managed Service Program
We provide a pre-configured instance in a fully managed private cloud environment. A team of highly-skilled cybersecurity professionals using our industry software offer 24 hours a day, 365 days a year identity governance and remediation program.