What is MFA? A Complete Guide to Multi-Factor Authentication for Secure Enterprises
What is MFA? A Complete Guide to Multi-Factor Authentication for Secure Enterprises

1. Introduction
Cybercriminals no longer rely on brute force—they rely on human error. In recent years, phishing attacks, credential theft, and data breaches have surged, exploiting weak or reused passwords to infiltrate even the most secure-looking environments. As digital identities become the new perimeter, password-based logins are proving to be one of the most vulnerable links in the cybersecurity chain.
This is where Multi-Factor Authentication (MFA) becomes essential. MFA requires users to verify their identity using two or more independent factors—making it significantly harder for unauthorized users to gain access.
But MFA isn’t just a security enhancement—it’s a strategic component of Identity Governance and Administration (IGA) and Identity Access Management (IAM) frameworks. When embedded into enterprise IAM architecture, MFA supports IAM risk management, improves access visibility, and helps enforce governance policies across users, devices, and systems. In a world where digital identities are prime targets, MFA is no longer optional—it’s foundational to secure and compliant operations.
2. What is MFA? A Simple Explanation
Multi-Factor Authentication (MFA) is a security mechanism that requires users to present two or more independent credentials—also known as “factors”—to verify their identity before gaining access to a system. These factors typically fall into one of three categories: something you know (like a password), something you have (such as a smartphone or hardware token), and something you are (biometric data like a fingerprint or facial scan).
In contrast to single-factor authentication, which relies solely on a password, MFA adds an extra layer of defense—making it significantly harder for unauthorized users to breach enterprise systems, even if one credential is compromised.
Consider common use cases: logging into a corporate laptop with a password and an authenticator app, accessing a banking app with Face ID, or entering a secure VPN with a smart card and PIN. Each of these combines multiple authentication factors to enhance identity assurance.
MFA forms a foundational component of customer identity and access management and plays a pivotal role in modern IGA security. It strengthens the authentication process while supporting broader goals within Identity Governance and Administration (IGA) and Identity Access Management (IAM) strategies.
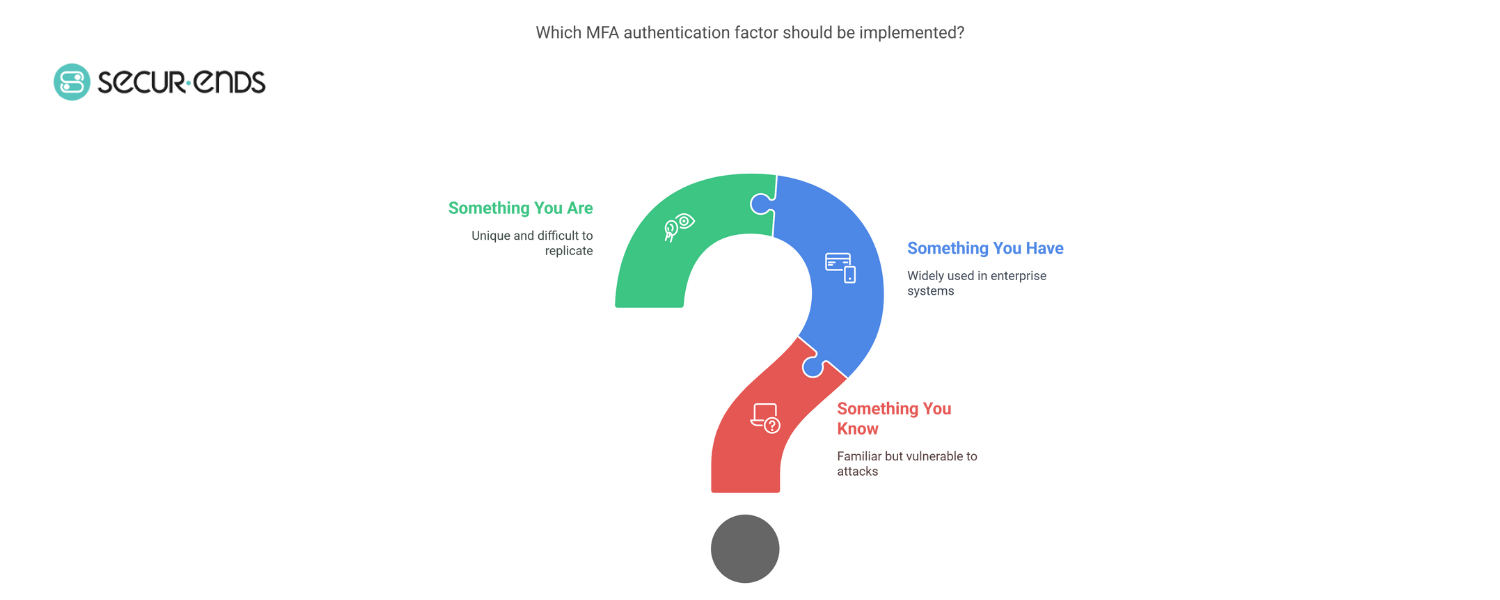
3. The Three Core MFA Authentication Factors
At the heart of Multi-Factor Authentication (MFA) are three distinct categories of authentication factors, each contributing to a more secure and layered access experience.
- Something You Know
This is the most familiar form—passwords, PINs, or answers to security questions. While essential, these alone are highly vulnerable to phishing, social engineering, and brute-force attacks. - Something You Have
This includes physical or digital items such as OTP (One-Time Password) tokens, smart cards, mobile phones, or authenticator apps. These are widely used across enterprise login systems, especially in Federated Identity & Access Management environments, where secure access across integrated platforms is essential. - Something You Are
Biometric data like fingerprints, retina scans, and facial recognition fall into this category. These are unique to the user and difficult to replicate, making them a strong second or third factor in identity governance and administration solutions.
Advanced implementations may also leverage behavioral or AI-driven authentication—like recognizing keystroke patterns or location anomalies—which adds context-aware intelligence to the verification process.
Understanding these factors is crucial for building secure IAM frameworks and conducting effective User Access Reviews, especially in systems that rely on Role-Based Access Control (RBAC) to govern access levels across the enterprise.
4. MFA vs 2FA: What’s the Difference?
While often used interchangeably, Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) are not the same. 2FA is a subset of MFA that uses exactly two authentication factors—typically a password and one additional method, like an OTP or biometric scan.
MFA, on the other hand, encompasses two or more factors and is more flexible. Enterprises may adopt adaptive MFA or step-up authentication, where the number and type of factors adjust based on risk level, user behavior, or location—supporting smarter IAM risk management strategies.
For instance, accessing a Google account may only require 2FA, but logging into high-security enterprise systems often demands full MFA with layered verification. These advanced methods are often essential for maintaining strong controls in Identity Access Management (IAM) frameworks and ensuring compliance during User Access Reviews.
5. Types of MFA Methods
Enterprises today have a wide array of Multi-Factor Authentication (MFA) methods at their disposal—each with unique strengths and ideal use cases. Choosing the right mix depends on organizational needs, user experience goals, and integration capabilities within broader Identity Governance and Administration (IGA) and IAM systems.
- One-Time Passwords (OTP):
Delivered via SMS, email, or authenticator apps like Google Authenticator or Microsoft Authenticator. These are widely used for securing logins, especially in customer identity access management scenarios. - Push Notifications:
Apps like Duo or Okta Verify send real-time approval requests to a user’s mobile device. Easy to use and more phishing-resistant than SMS. - Hardware Tokens:
Devices like YubiKeys or smart cards generate cryptographic keys. Common in high-security environments and useful for IGA security and federated identity & access management. - Biometric Scans:
Fingerprints, facial recognition, or retina scans offer seamless yet secure access. Biometrics also help reduce reliance on passwords. - Adaptive MFA:
Uses contextual signals like device, IP address, or time of access to assess risk and adjust the authentication level—supporting smarter IAM risk management. - QR Code Logins / Magic Links:
User-friendly alternatives that reduce friction while maintaining security standards. - Context-Aware MFA:
Powered by behavioral analytics and Scim API integrations, this method tailors access based on user behavior and enterprise policies.
Together, these MFA types play a critical role in enforcing policies, securing identities, and enabling precise Role-Based Access Control (RBAC) in modern enterprises.
6. Why MFA Matters: Top Benefits for Enterprises
1. Prevents Unauthorized Access:
By adding extra layers of verification, MFA significantly reduces the risk of account takeover, phishing, and brute-force attacks—even if credentials are compromised.
2. Strengthens Enterprise Security Posture:
MFA supports IAM risk management by limiting exposure across cloud apps, VPNs, and endpoints, especially in hybrid and remote work environments.
3. Aids in Compliance:
Meeting regulatory mandates like SOX, HIPAA, PCI-DSS, and ISO often requires strong access controls. MFA is a foundational control in many identity governance and administration solutions.
4. Secures Third-Party Access:
Vendors and contractors often operate outside core security infrastructure. MFA ensures these external users are verified before accessing sensitive systems.
5. Supports Zero Trust and RBAC Models:
When paired with Role-Based Access Control (RBAC), MFA enforces least-privilege access, a cornerstone of modern customer identity and access management and Zero Trust architecture.
7. How MFA Supports Identity Governance
Multi-Factor Authentication (MFA) is more than just a login checkpoint—it’s an integral component of robust Identity Governance and Administration (IGA) strategies. By verifying users beyond passwords, MFA strengthens identity assurance and supports the enforcement of enterprise-wide access policies.
In the context of User Access Reviews, MFA provides an additional layer of validation. When reviewing user privileges across cloud and on-prem systems, organizations can ensure that only authenticated and verified users retain access to sensitive resources—closing the loop on risky, outdated permissions.
MFA also complements Role-Based Access Control (RBAC) by adding dynamic authentication on top of static role assignments. This synergy enables Zero Trust enforcement, ensuring that users are not just assigned the right role, but also continuously verified.
During joiner-mover-leaver lifecycle events, MFA helps automate access provisioning and de-provisioning. For example, with SCIM API integrations, organizations can synchronize MFA policies with identity platforms like Okta, Azure AD, or custom directories—streamlining governance across federated and hybrid ecosystems.
By integrating MFA into your identity governance and administration solutions, enterprises gain not only security but also visibility, audit readiness, and operational efficiency—core to modern IAM risk management.
Explore how SecurEnds bridges MFA with access governance to drive smarter, safer identity ecosystems.
8. Challenges in Implementing MFA
Despite its clear benefits, implementing Multi-Factor Authentication (MFA) across the enterprise comes with hurdles—especially in diverse IT environments.
User friction is a common concern. If not properly configured, MFA can lead to login fatigue, resistance, or increased support tickets. Striking a balance between usability and security is critical for successful adoption.
Legacy systems and older applications often lack native support for MFA or modern SCIM API integrations, making deployment inconsistent. Additionally, remote workforce onboarding and BYOD (bring your own device) scenarios pose risks if MFA enforcement isn’t uniform.
Enterprises may also face challenges with federated identity & access management compatibility, especially when managing multiple identity providers.
SecurEnds addresses these challenges through intelligent orchestration, seamless plug-ins for legacy and modern systems, and risk-aware MFA workflows that align with broader IAM risk management and Identity Governance and Administration (IGA) goals.
9. Best Practices for Enterprise MFA Implementation
To maximize the impact of Multi-Factor Authentication (MFA) and ensure long-term scalability, enterprises should align implementation with their broader Identity Access Management (IAM) and Identity Governance and Administration (IGA) strategies. Here are some key practices:
- Conduct a Security Audit First
Identify high-risk access points, privileged users, and regulatory gaps before deploying MFA.
- Select the Right MFA Methods
Choose a mix of factors (OTP, biometrics, contextual) based on user roles, risk levels, and system sensitivity.
- Ensure Seamless User Experience
Reduce friction by offering intuitive options like push notifications or authenticator apps. Train users on phishing-resistant behavior.
- Enable Adaptive and Context-Aware MFA
Leverage device recognition, geolocation, and behavior analytics to trigger step-up authentication only when needed—supporting IAM risk management.
- Integrate with Existing IAM & IGA Systems
Use SCIM API or federated protocols for smooth integration across identity providers and governance platforms.
- Document and Monitor Continuously
Maintain clear MFA policies, track usage patterns, and align them with User Access Reviews and identity governance and administration solutions.
10. Conclusion
Multi-Factor Authentication (MFA) isn’t just a defensive mechanism—it’s a proactive step toward building a resilient, governance-driven enterprise. As identity becomes the new security perimeter, modern businesses must go beyond basic authentication to adopt layered, intelligent controls.
MFA, when strategically implemented, integrates seamlessly with Identity Governance and Administration (IGA) and Identity Access Management (IAM) frameworks—enhancing security, streamlining compliance, and enabling agile access control. It supports a broader vision that includes IAM risk management, SCIM API integrations, and User Access Review cycles to ensure that the right users have the right access, always.
Whether your enterprise is navigating regulatory mandates, scaling digital ecosystems, or enabling remote workforces, MFA serves as the cornerstone of a secure and compliant identity architecture.
Explore how SecurEnds helps enterprises unify MFA with access governance—bringing security, visibility, and control under one intelligent platform.
11. FAQs
1. What is the difference between MFA and 2FA?
Two-Factor Authentication (2FA) uses exactly two types of authentication factors—typically something you know and something you have. Multi-Factor Authentication (MFA) includes two or more factors and may also incorporate biometrics or contextual signals. MFA offers greater flexibility and is more aligned with enterprise-grade Identity Access Management (IAM) strategies.
2. Is MFA mandatory for compliance?
Yes, many compliance frameworks—such as HIPAA, PCI-DSS, SOX, and ISO—require MFA as part of broader Identity Governance and Administration (IGA) and access control policies. MFA is often cited as a key control in audit requirements and User Access Reviews.
3. Can MFA be bypassed?
While MFA significantly reduces risk, no security measure is infallible. Social engineering, SIM swapping, and phishing-resistant weaknesses can lead to bypasses. That’s why it’s crucial to pair MFA with IGA security, RBAC, and continuous monitoring for anomalous behavior.
4. How does SecurEnds integrate with Okta, Azure AD, or Active Directory?
SecurEnds uses SCIM API, federated protocols, and pre-built connectors to integrate seamlessly with popular identity providers like Okta, Azure AD, and Active Directory. These integrations allow enterprises to enforce MFA policies consistently across the identity lifecycle.


