Identity Lifecycle Management: A Complete Guide
Identity Lifecycle Management: A Complete Guide

1. Introduction
Every digital interaction in your organization—whether it’s an employee logging into a dashboard, a customer signing up for your service, or a contractor accessing a shared folder—starts with an identity. But what happens to that identity after day one? What about when roles change, or someone leaves? Who’s tracking that? And more importantly—who’s shutting off the access when it’s no longer needed?
Identity Lifecycle Management (ILM) is how smart organizations stay on top of this. It’s the process of managing every digital identity from the moment it’s created to the moment it’s deactivated—securely, efficiently, and without manual chaos.
Why is it such a big deal today? Because the stakes are higher. With hybrid work, cloud-first ecosystems, and stricter compliance rules like GDPR and HIPAA, there’s a lot more to lose if access gets into the wrong hands—or if it just lingers longer than it should.
And with security models like Zero Trust becoming the norm, ILM isn’t just an IT best practice anymore—it’s the foundation for Identity Access Management (IAM), IGA security, and everything from user access reviews to automated deprovisioning.
In short: if you care about security, compliance, or just keeping things running without bottlenecks, ILM needs to be on your radar.
2. What Is Identity Lifecycle Management?
So now that we’ve established why Identity Lifecycle Management matters, let’s break down what it actually is.
Think of ILM as the operating system for digital identity. Behind every login, every file share, and every tool someone opens at work, there’s a set of permissions quietly making it all happen—or not happen. ILM is how organizations track, manage, and adjust those permissions as people (and systems) come and go.
It covers every kind of identity you work with, not just employees:
- New hires and interns
- Contractors, freelancers, and vendors
- Long-term partners
- Customers with login portals
- Even non-human identities like apps, APIs, bots, and devices
The lifecycle starts the moment an identity is created—like when HR adds a new employee—and continues through every change in their role, team, or tool access. Eventually, it ends with deactivation, ideally as soon as access is no longer needed. (No more ghost accounts lingering in your systems.)
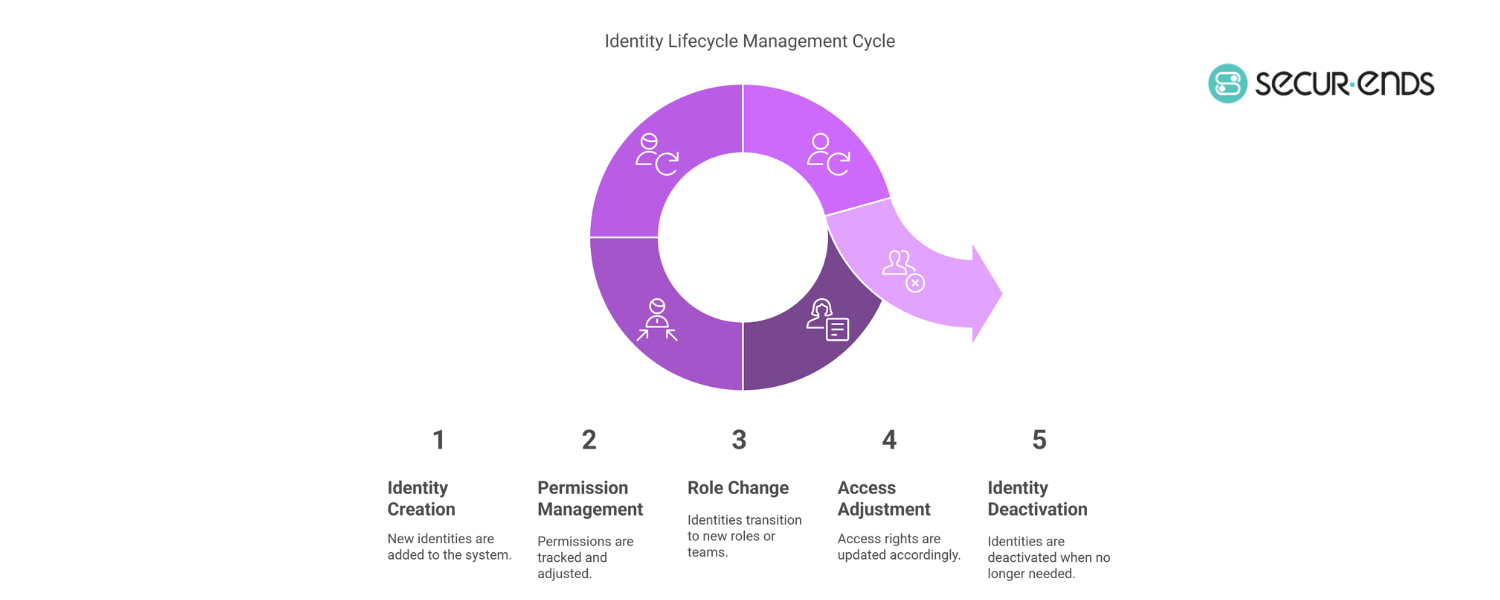
Here’s the big picture of how ILM works:
- Provisioning: Someone or something joins. Access is granted.
- Managing: Roles evolve. Access changes.
- Deprovisioning: The relationship ends. Access is removed.
When done right, it’s seamless, secure, and smart—powered by tools that automate updates, apply Role-Based Access Control (RBAC), and help you meet compliance needs without slowing things down.
In other words, ILM is how your organization stays in control of identity access—every step of the way.
3. Why Identity Lifecycle Management Matters
By now, ILM might sound like a clean and structured process — and ideally, it is. But the real question is: why should your business care?
Why invest time, tools, and strategy into managing identities this closely?
Because when identity access gets out of sync, things fall apart fast — from accidental data exposure to compliance headaches and operational slowdowns. Identity Lifecycle Management isn’t just about access; it’s about risk management, accountability, and agility.
Here are a few reasons why ILM isn’t optional anymore — especially in environments governed by Identity Governance and Administration (IGA) and IAM Risk Management:
- Stronger Security & Access Control
ILM ensures that only the right people (or systems) can access the right resources at the right time — nothing more, nothing less. It supports least privilege, reduces attack surfaces, and prevents lingering access that could be exploited.
- Regulatory Compliance (GDPR, HIPAA, SOX & more)
Regulators expect clear answers: Who had access? Why? For how long? ILM provides that audit trail through centralized controls, reporting, and continuous User Access Reviews, all of which are core to modern IGA security strategies.
- Operational Efficiency
Without ILM, identity management becomes manual chaos. With it, onboarding, role changes, and offboarding can be automated and integrated with your HR and IT systems — saving time and cutting down on errors.
- Insider Threat Mitigation
It’s not always outsiders you have to worry about. ILM ensures access changes the moment someone leaves a role, team, or the company—closing the door on accidental (or intentional) misuse.
- Cost Reduction Through Automation
Manual processes eat up IT resources. ILM tools equipped with Scim API and smart workflows can handle the high-volume identity tasks without constant intervention.
Whether you’re a growing business or an enterprise juggling thousands of users, ILM acts as your silent guardian — making Identity Access Management (IAM) cleaner, faster, and safer.
4. Identity Lifecycle Management Stages
Knowing why ILM matters is one thing — but how does it actually work in real life?
The identity lifecycle isn’t a single event. It’s a continuous journey made up of key stages, each with its own impact on security, compliance, and user experience. Let’s break it down:
a. Provisioning (Onboarding)
This is where it all begins.
Provisioning is the process of creating a digital identity when someone joins the organization — whether they’re a full-time employee, a consultant, or even a system like an API or SaaS tool.
Done right, provisioning goes beyond just handing over login credentials. It includes:
- Assigning access based on roles or attributes using Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC)
- Syncing with HR systems to automate access from day one
- Applying Federated Identity & Access Management to simplify cross-platform logins
Modern ILM tools can automatically assign the right resources based on job title, department, location, and more — ensuring people only get access to what they need, nothing more.
b. Managing Identities
Once someone is in, their identity evolves.
Maybe they switch teams, take on a new project, or move up in the company. That means their access needs to shift — and this is where many organizations stumble.
Effective ILM ensures that:
- Access privileges stay in sync with changing roles
- RBAC and least privilege principles are continuously enforced
- IT, HR, and security teams stay aligned with real-time updates
This is also the stage where User Access Reviews and IGA solutions play a huge role. Regularly auditing access helps prevent privilege creep — when users accumulate more permissions than they actually need.
c. Deprovisioning (Offboarding)
This might be the most critical — and most overlooked — stage of ILM.
When someone leaves (whether it’s an employee, contractor, or vendor), their access needs to disappear immediately and completely. Otherwise, you’re left with orphaned accounts — a goldmine for attackers.
Automated deprovisioning ensures:
- Accounts are disabled across apps, cloud services, and internal systems
- Access is revoked uniformly and instantly
- There are no backdoors or forgotten credentials left behind
This stage alone is where IAM Risk Management proves its worth. A robust offboarding process protects your organization from unnecessary exposure and helps demonstrate IGA compliance.
These three stages—provisioning, managing, and deprovisioning—are the foundation of Identity Lifecycle Management. When automated and consistently monitored, they create a secure, compliant, and scalable identity environment.
5. Core Components of Identity Lifecycle Management
If the lifecycle stages are the what, then these are the how.
Behind every smooth onboarding, secure access update, or clean offboarding, there’s a set of ILM components quietly working in sync.
Let’s walk through the core elements that make Identity Lifecycle Management actually work — not just in theory, but in the everyday rhythm of your business.
a. Authentication
First up — are you really who you say you are?
Authentication is the gatekeeper. It verifies identities before granting access, and it’s no longer just about passwords.
Modern ILM strategies lean on:
- Multi-Factor Authentication (MFA) for layered security
- Biometric verification like fingerprints or facial recognition
- Passwordless logins in federated environments using Federated Identity & Access Management tools
Authentication is where Identity Access Management (IAM) truly begins. And the more seamless (yet secure) it is, the better your user experience and security posture.
b. Authorization
Authentication answers who you are. Authorization decides what you’re allowed to do.
This component enforces access policies through:
- Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC)
- Conditional access rules based on location, device type, or risk level
- Automated approval workflows tied to user roles and department needs
With good authorization practices, you’re not just granting access — you’re making smart, risk-aware decisions about who gets what, when, and why.
c. Administration
Behind every successful ILM program is a well-oiled engine of administration.
This includes:
- Centralized policy configuration (who gets access, under what conditions)
- Automating identity workflows — like provisioning new accounts or triggering access changes
- Syncing across systems using protocols like Scim API
Smart administration reduces the manual load on IT teams and helps maintain consistent access governance, even as your organization scales or undergoes rapid change.
d. Auditing & Reporting
If you can’t track it, you can’t control it.
Auditing and reporting are where IGA security and compliance frameworks come into play. This component handles:
- Detailed logging of identity events: who accessed what, when, and how
- User Access Reviews for internal oversight and regulatory audits
- Real-time alerts for suspicious activity or policy violations
These tools are your safety net — helping you respond to incidents quickly, demonstrate compliance with frameworks like GDPR or SOX, and refine policies over time.
Together, these four components form the backbone of any modern ILM solution. They enable organizations to strike the right balance between usability, compliance, and security — all while keeping identities at the center of access strategy.
6. Common Challenges in Identity Lifecycle Management
If Identity Lifecycle Management were easy, every organization would have it figured out. But the truth is — even with the best tools and intentions, ILM can get messy. Especially when growth is fast, users are many, and systems don’t talk to each other.
Here are some of the most common roadblocks teams run into:
Manual Processes & Human Error
When access requests and deprovisioning are handled manually, mistakes happen. People forget. Tickets get buried. Access gets granted just to move things along — and often never gets revoked.
This isn’t just inefficient — it’s a security liability.
That’s where Identity Governance and Administration (IGA) tools can help by automating routine identity tasks and minimizing the margin for error.
Delayed Access Revocation
One of the riskiest blind spots? Former employees or third-party users who still have access to internal systems.
Without automated offboarding and User Access Review processes in place, orphaned accounts pile up — becoming low-hanging fruit for threat actors or insiders.
Balancing Security with User Experience
You need tight controls — but you also want users to get work done without jumping through hoops. That tension is real.
Too much friction, and users find workarounds. Too little, and you compromise on security. The key lies in smart implementation: things like Role-Based Access Control (RBAC), MFA, and conditional access that adapt to context.
Diverse Identity Types
It’s not just employees anymore. You’re managing access for:
- Contractors and gig workers
- Customers logging into your apps
- API keys, bots, and service accounts
This calls for more than basic IAM — it requires customer identity and access management solutions and the ability to govern non-human identities with the same precision.
Privilege Creep and Overprovisioning
Over time, users change roles, switch teams, or get promoted — but their old access often stays intact.
This accumulation of permissions is called “privilege creep.”
Left unchecked, it creates a bloated access landscape that’s hard to audit and even harder to secure. That’s where IGA security features like periodic access reviews and automated role reassignment prove essential.
None of these challenges are unsolvable — but they are common. And acknowledging them is the first step toward building a more resilient ILM strategy.
7. Identity Lifecycle Management Tools & Solutions
If you’re trying to manage identities at scale without the right tools, it’s like juggling with your eyes closed — eventually, something’s going to drop.
The good news? There’s an entire ecosystem of solutions purpose-built for Identity Governance and Administration (IGA) and Identity Access Management (IAM) that can streamline everything from onboarding to offboarding — while reducing risk along the way.
Here’s what to look for in an ILM solution that actually makes life easier:
Automated Provisioning and Deprovisioning
This is non-negotiable. The ability to instantly create or revoke access based on real-time changes in HR systems or role mappings isn’t just convenient — it’s foundational to strong IAM Risk Management.
Whether it’s a new hire, a department transfer, or a resignation — automated flows ensure that the right people have the right access at the right time (and not a moment longer).
Role-Based and Attribute-Based Workflows
Modern ILM tools should support both RBAC and ABAC (Attribute-Based Access Control). Why? Because access isn’t always about title — sometimes it’s about geography, project, or even device type.
Granular policies allow for smarter, more context-aware access decisions. And when you add Federated Identity & Access Management into the mix, your users can move seamlessly across environments without managing multiple logins.
Integration with HR, IT, and IAM Systems
Your ILM strategy is only as strong as its integrations. Look for tools that play well with:
- HR systems like Workday or SAP
- Cloud directories like Azure AD or Google Workspace
- IAM platforms and Scim API for standardized identity provisioning
Tightly coupled systems reduce latency in updates and help eliminate the silos that slow you down.
Dashboards, Reporting, and Audits
You can’t govern what you can’t see. Built-in reporting dashboards — especially those tailored for compliance — help teams stay audit-ready with minimal scrambling.
Want to pass a User Access Review without sifting through spreadsheets? These tools should make it a few clicks, not a few days.
Popular Tools to Consider
While your choice will depend on organizational needs and tech stack, some well-regarded ILM solutions in the market include:
- Okta – Great for cloud-first environments and federated access
- SailPoint – Deep IGA capabilities with strong analytics
- SecurEnds – Especially useful for audit and certification workflows
- OneLogin – Known for speed, simplicity, and scalability
- Microsoft Entra ID (formerly Azure AD) – Ideal if you’re embedded in the Microsoft ecosystem
Each has its strengths — the key is to align features with your business goals and compliance requirements.
With the right ILM solution in place, your identity strategy moves from reactive to proactive — saving time, reducing risk, and giving your team breathing room to focus on what matters.
8. Benefits of Automated Identity Lifecycle Management
You’ve probably heard the pitch before: “automation saves time.” But when it comes to identity lifecycle management, it does much more than just save a few work hours — it becomes the invisible backbone of enterprise security, compliance, and productivity.
Here’s how automated ILM quietly transforms your organization behind the scenes:
1. Faster Onboarding and Offboarding
Manual provisioning is a productivity killer. With automation, new employees don’t have to wait days to get access to essential tools — they’re up and running on Day One. Just as importantly, when someone leaves, their access is revoked instantly. No loose ends, no orphaned accounts, no doors left unlocked.
This isn’t just about speed — it’s about security.
2. Enhanced Visibility and Audit Trails
Need to prove compliance with GDPR, SOX, or HIPAA? Automated ILM gives you centralized visibility into who has access to what, when, and why. Every change is logged. Every permission granted has a reason. No more guesswork during audits.
Tools with built-in dashboards and User Access Review workflows let you stay ahead of the curve — and the regulators.
3. Stronger Security Posture
By combining automation with Role-Based Access Control (RBAC) and Identity Governance and Administration solutions, you eliminate human error and drastically reduce the risk of privilege creep — where users end up collecting permissions over time like digital clutter.
Plus, when coupled with IGA security principles, automation ensures access is always aligned with actual job roles, not assumptions.
4. Reduced IT Workload
Let’s face it: IT teams are swamped. Automated workflows take repetitive identity tasks off their plate — no more ticket queues for password resets, no more manual access assignments, no more chasing down approvals.
This frees your IT team to focus on strategic initiatives instead of being stuck in reactive mode.
5. Better Compliance, Less Stress
With automation doing the heavy lifting — syncing with HR systems, triggering deprovisioning, maintaining access logs — your organization becomes audit-ready by default. You’re no longer scrambling to prepare compliance reports at the eleventh hour.
It also helps meet the rising standards around IAM Risk Management, especially when paired with customer identity and access management solutions that ensure external users are governed just as tightly.
In short, automation doesn’t just simplify ILM — it amplifies its impact across the business.
9. Best Practices for Implementing ILM
Automating identity lifecycle management sounds great — and it is — but success doesn’t come from just plugging in a tool and hoping for the best. ILM works best when there’s a clear strategy behind it. Think of it as building a well-oiled access machine, not just buying one.
Here’s how to set it up for long-term value:
1. Start with the Principle of Least Privilege
No one should have more access than they absolutely need — it’s a golden rule in IAM Risk Management. Whether it’s an intern or a senior executive, the idea is simple: grant just enough access to do the job, nothing more.
This also helps reduce the fallout in case of a breach or compromised credentials. Fewer privileges = smaller blast radius.
2. Use RBAC and ABAC for Scalable Access Control
Role-Based Access Control (RBAC) gives structure. Attribute-Based Access Control (ABAC) adds context. Together, they create scalable frameworks that work across departments, roles, and even regions.
Think: “A sales manager in India” gets different access than “a sales manager in the US.” These models make that distinction clear, repeatable, and enforceable.
3. Automate High-Volume, Low-Value Tasks
Manual provisioning, password resets, and access revocations eat into valuable IT time. Automate wherever you can — especially for tasks that are routine and prone to human error. Let workflows, triggers, and integrations do the heavy lifting.
Modern IGA tools and platforms that support SCIM API standards make this smoother than ever.
4. Promote Cross-Department Collaboration
ILM isn’t just IT’s job. It sits at the intersection of HR, Security, Compliance, and Business Ops. A new hire’s onboarding? That’s HR. Access policies? That’s security. Audit readiness? That’s compliance.
A successful ILM strategy brings everyone to the table. The more alignment upfront, the fewer surprises later.
5. Don’t Skip Security Awareness Training
Automation won’t save you from human behavior. Employees should understand how identity systems work — even at a basic level — and be aware of how their actions affect security.
Empower them to report anomalies, follow safe access practices, and treat credentials like the keys they are.
6. Review Access Regularly — Not Just During Audits
Access reviews shouldn’t be annual box-checking exercises. They should be continuous, dynamic, and supported by your ILM solution.
With User Access Review features and automated recertification workflows, you can keep access rights accurate and up to date — not just compliant on paper.
When done right, ILM becomes more than a control mechanism — it becomes a framework for trust, transparency, and resilience.
10. Use Cases of Identity Lifecycle Management
Identity Lifecycle Management isn’t just a “set it and forget it” system — it’s something that quietly shapes day-to-day operations. Every new hire, promotion, or vendor login tells a story of access. Here’s what ILM looks like in action:
1. Onboarding a New Employee
It’s day one, and a new employee logs in. Everything just works — from email to project management tools — without endless IT tickets. Behind the scenes? ILM systems pull from HR data, create the digital identity, apply RBAC policies, and assign access based on role.
The best part? The process is secure, trackable, and compliant — a seamless fusion of IAM and IGA security in action.
2. Role Change or Promotion
When someone changes teams or gets promoted, their access must evolve too. Hanging on to old permissions leads to privilege creep, which is one of the biggest threats in IAM Risk Management.
A robust ILM setup detects role changes, updates entitlements automatically, and ensures access stays relevant — without exposing sensitive systems.
3. Offboarding a Departing Employee
A disgruntled ex-employee still having admin access is a nightmare waiting to happen. With ILM, the moment HR updates their status, accounts are deactivated, permissions revoked, and federated identity and access management connections terminated across systems.
No stragglers. No orphaned accounts. Just clean exits with full audit logs to back it up.
4. Mergers & Acquisitions (M&A) Transitions
M&A events often create identity chaos — duplicate accounts, conflicting access rights, and compliance headaches. ILM helps unify identity systems, apply consistent policies, and manage access across entities without compromising security.
Identity governance and administration solutions with centralized controls and SCIM API integrations shine in these high-stakes environments.
5. Third-Party Access Control
Vendors, contractors, and partners often need temporary or limited access. ILM allows organizations to define time-bound or task-specific access, enforce strict policies, and ensure those identities are deactivated once the engagement ends.
This is especially vital in industries where customer identity and access management solutions and external collaboration tools are heavily used.
These aren’t hypothetical scenarios — they’re daily realities for security and IT teams. ILM ensures these transitions are secure, efficient, and scalable.
11. Moving Forward: How to Get Started
Understanding Identity Lifecycle Management is one thing — putting it into practice is where the real transformation begins. If your current identity processes are a patchwork of spreadsheets, manual approvals, and too many “just in case” access permissions, it’s time for a reset.
Here’s how to get started without feeling overwhelmed:
1. Conduct an Identity Audit
Start by asking the tough questions:
- Who has access to what?
- Is every identity still valid?
- Are there ghost accounts floating around?
This audit isn’t just a clean-up — it’s your baseline for better Identity Governance and Administration (IGA) and smarter User Access Review processes.
2. Define Policies and Role Mappings
Work with HR, IT, and compliance to establish clear, role-based access rules. Define what each role should and shouldn’t be able to access. This is the foundation for enforcing Role-Based Access Control (RBAC) or even Attribute-Based Access Control (ABAC) as you scale.
Think of this as building the blueprint for your IAM strategy — precise, scalable, and defensible in audits.
3. Choose the Right ILM Tool
Not all tools are created equal. Look for solutions that support:
- Automated provisioning and deprovisioning
- Deep HR and IT integration
- Centralized dashboards and audit trails
- Support for SCIM API, Federated Identity & Access Management, and multi-cloud environments
Whether you’re considering platforms like SailPoint, Microsoft Entra ID, or SecurEnds, align the tool with your organization’s size, tech stack, and regulatory needs.
4. Start Small, Then Automate
You don’t need to automate everything on day one. Begin with high-impact workflows like onboarding and offboarding. Test, refine, and then expand to role changes and third-party access.
This phased approach keeps your team confident and your IGA security posture strong.
5. Monitor, Measure, Improve
Once your ILM system is up and running, don’t switch to autopilot. Regularly review performance, spot gaps, and keep refining your policies. Schedule periodic User Access Reviews to ensure compliance — especially if you’re aiming for identity access management certifications or must answer to regulators.
ILM isn’t just a tool — it’s a mindset. A way to ensure that the right people have the right access at the right time — and that nobody keeps access when they shouldn’t.
12. Conclusion
Every user, device, or application granted access to your systems is more than a line item in a directory — it’s a potential doorway. And how you manage those doors determines how resilient, agile, and secure your organization truly is.
That’s the power of Identity Lifecycle Management.
It’s not just about provisioning and deprovisioning. It’s about building a digital environment where trust is earned, access is intelligent, and compliance is automatic — not an afterthought. When paired with a strong Identity Governance and Administration (IGA) framework, automated workflows, and tools that speak the language of SCIM APIs, Federated IAM, and User Access Reviews, ILM becomes a quiet engine driving both productivity and protection.
The future of IAM Risk Management isn’t manual. It’s not siloed. And it’s definitely not reactive.
It’s continuous. It’s contextual. And it’s already here.
Your next move?
Start small, automate smart, and scale with confidence. And when you’re ready, SecurEnds is here to help you turn identity chaos into clarity.


