How To Automate User Access Reviews
How To Automate User Access Reviews
How To Automate User Access Reviews
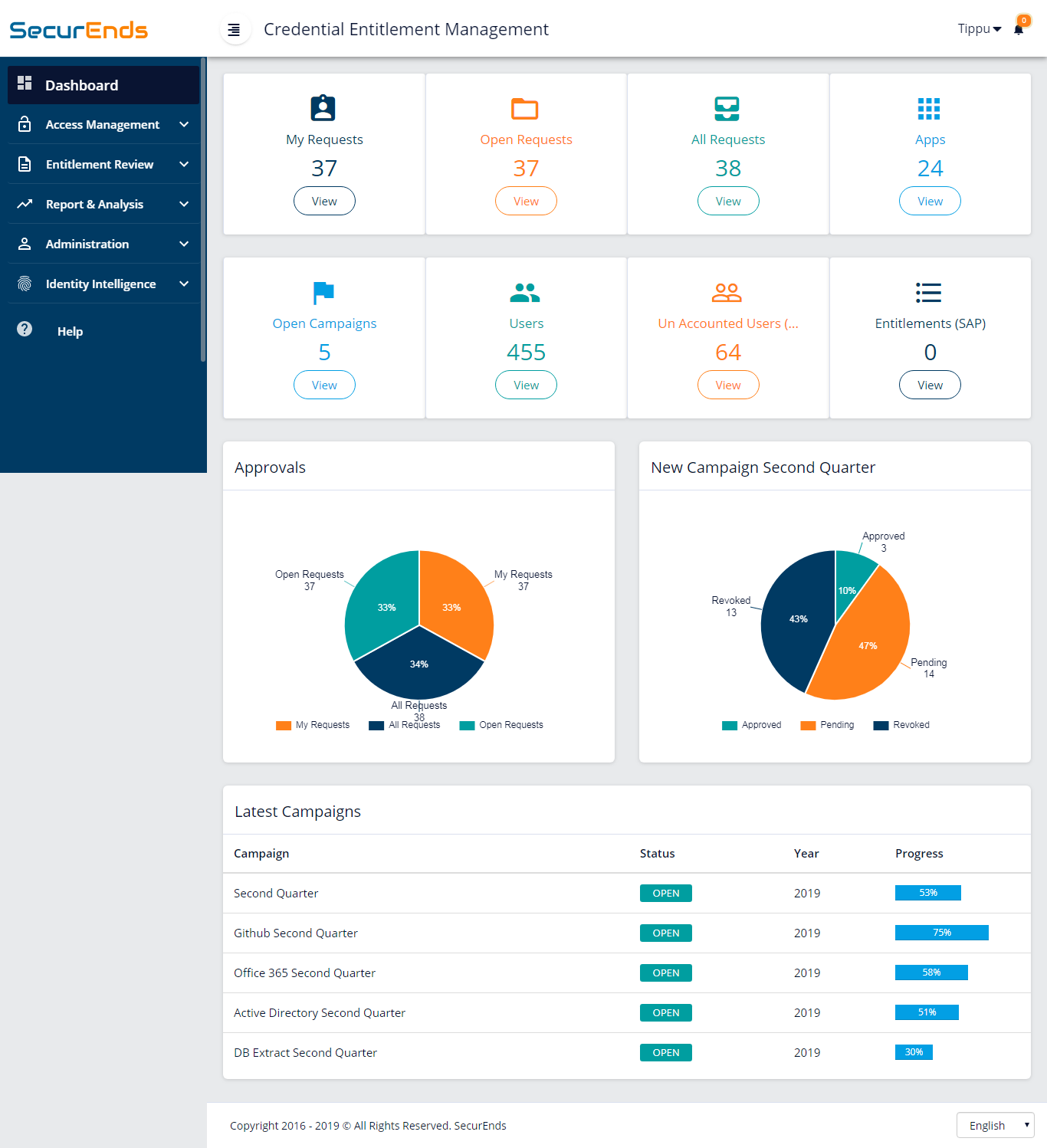
SecurEnds automates the User Access/Entitlement Reviews (IAM) across the enterprise for access certification to meet security compliance.
We know, User Access Reviews are very manual and tedious work from extracting application data, matching with HR or System of Record data, identifying managers/reviewers, sending emails to reviewers to complete access reviews and at the same time meet the audit timelines.
SecurEnds provides cutting-edge solution to automate User Access Reviews with a great UI and quick setup to add value to the information security and compliance teams.
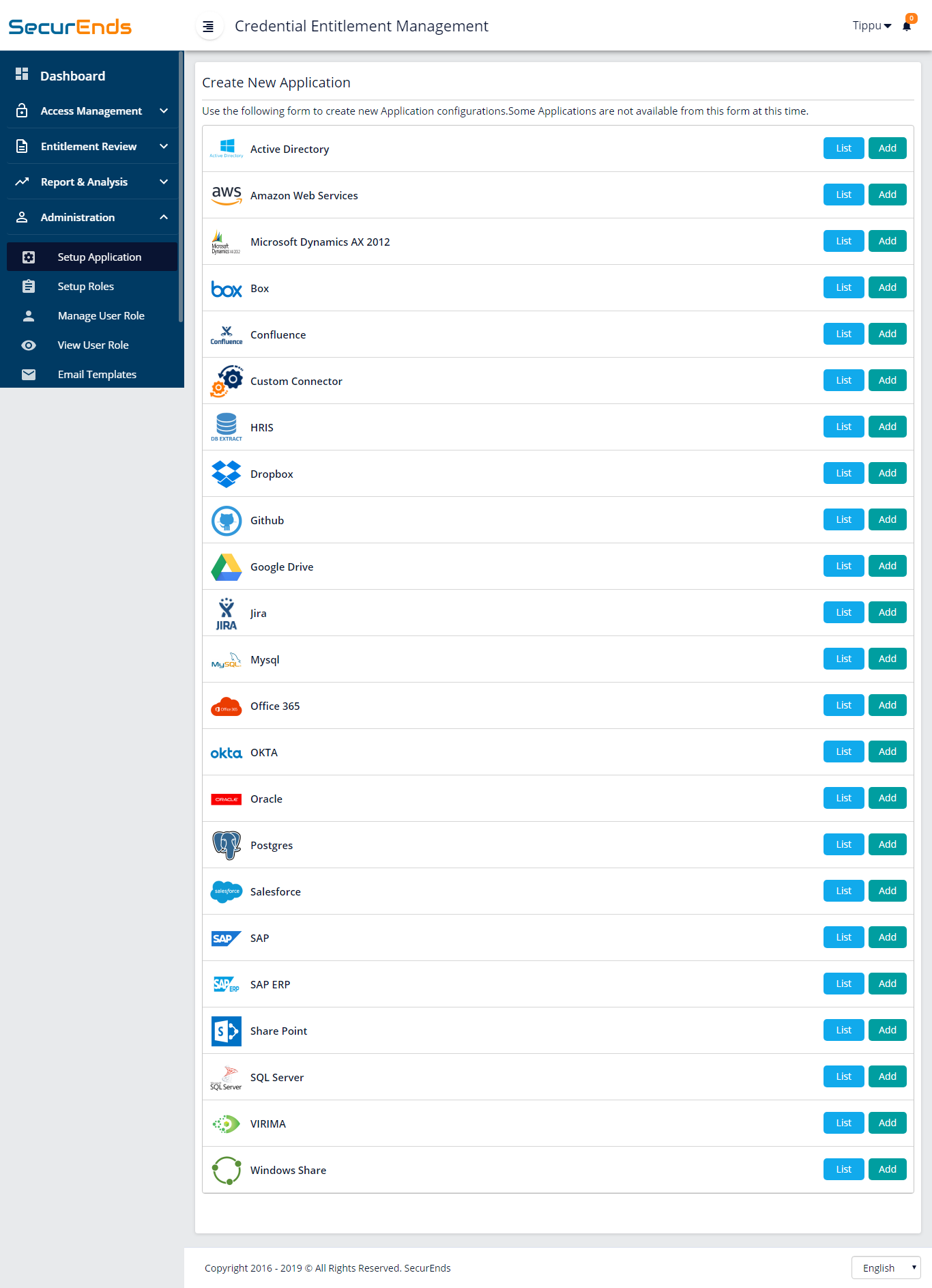
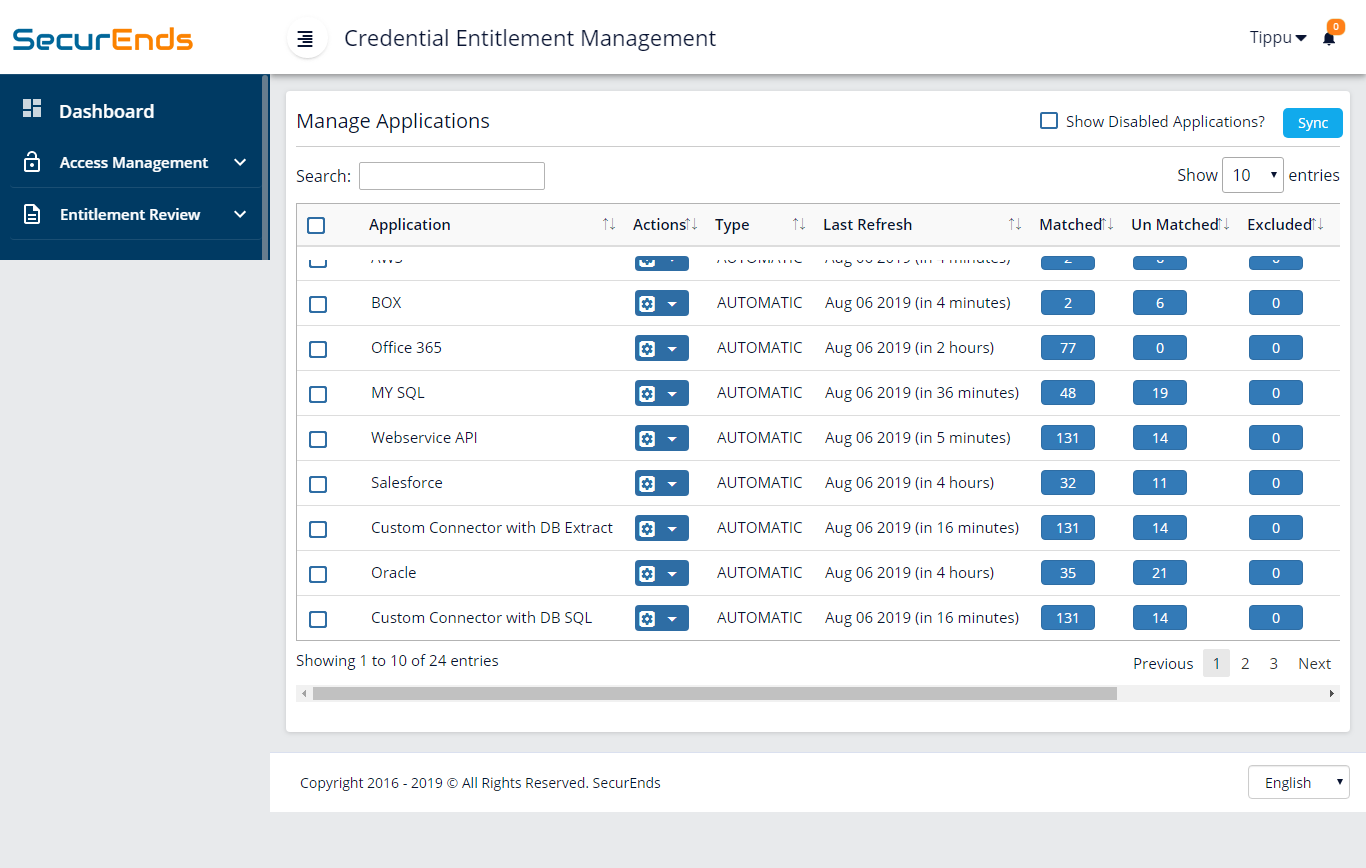
1. Easy to configure connectors to connect to standard applications and custom connectors to custom applications to extract users and entitlement data.
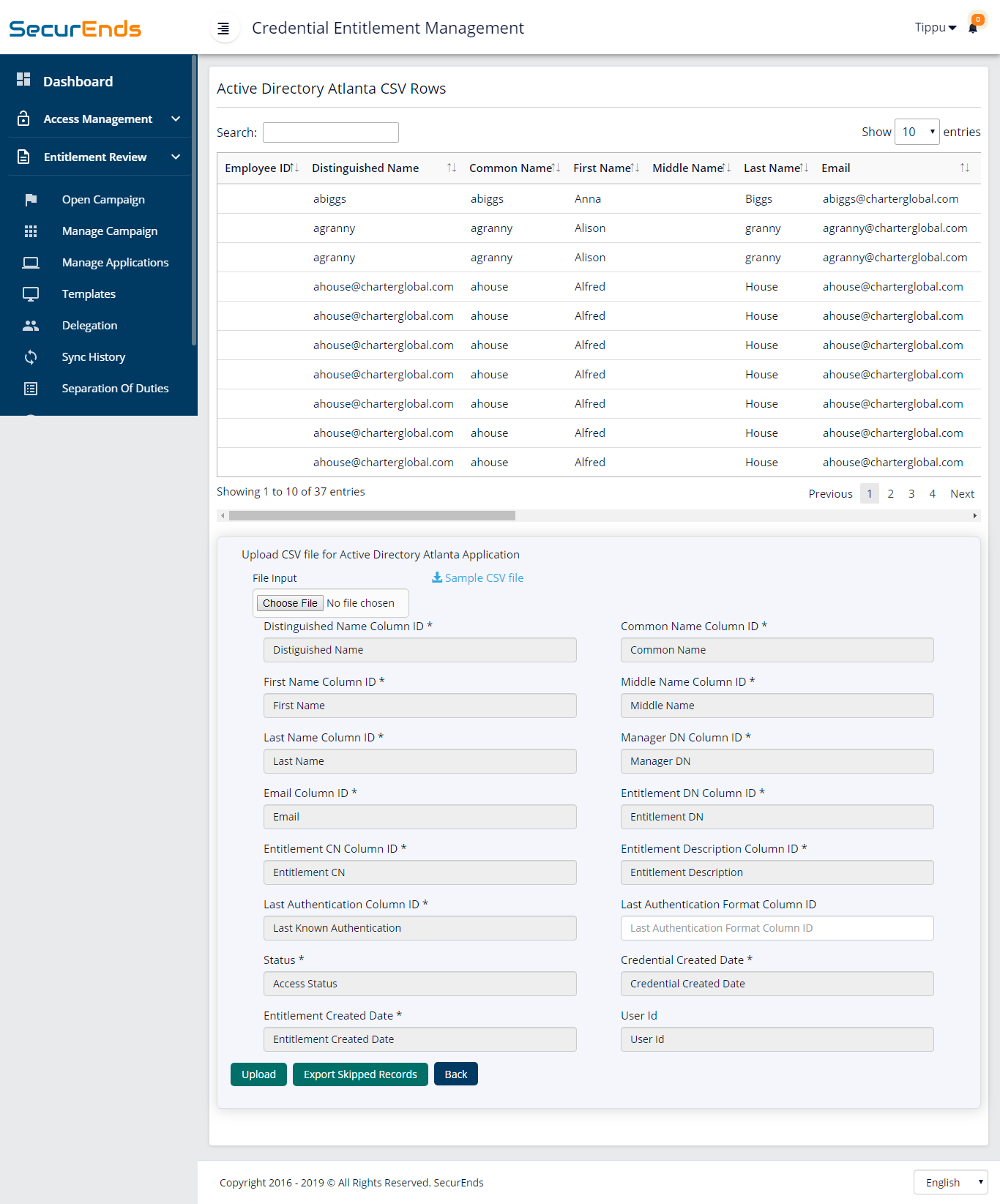
2. If connectors are not needed, upload a CSV file with users and entitlement data to perform reviews.
3. Match all application users to HR/System of Record.
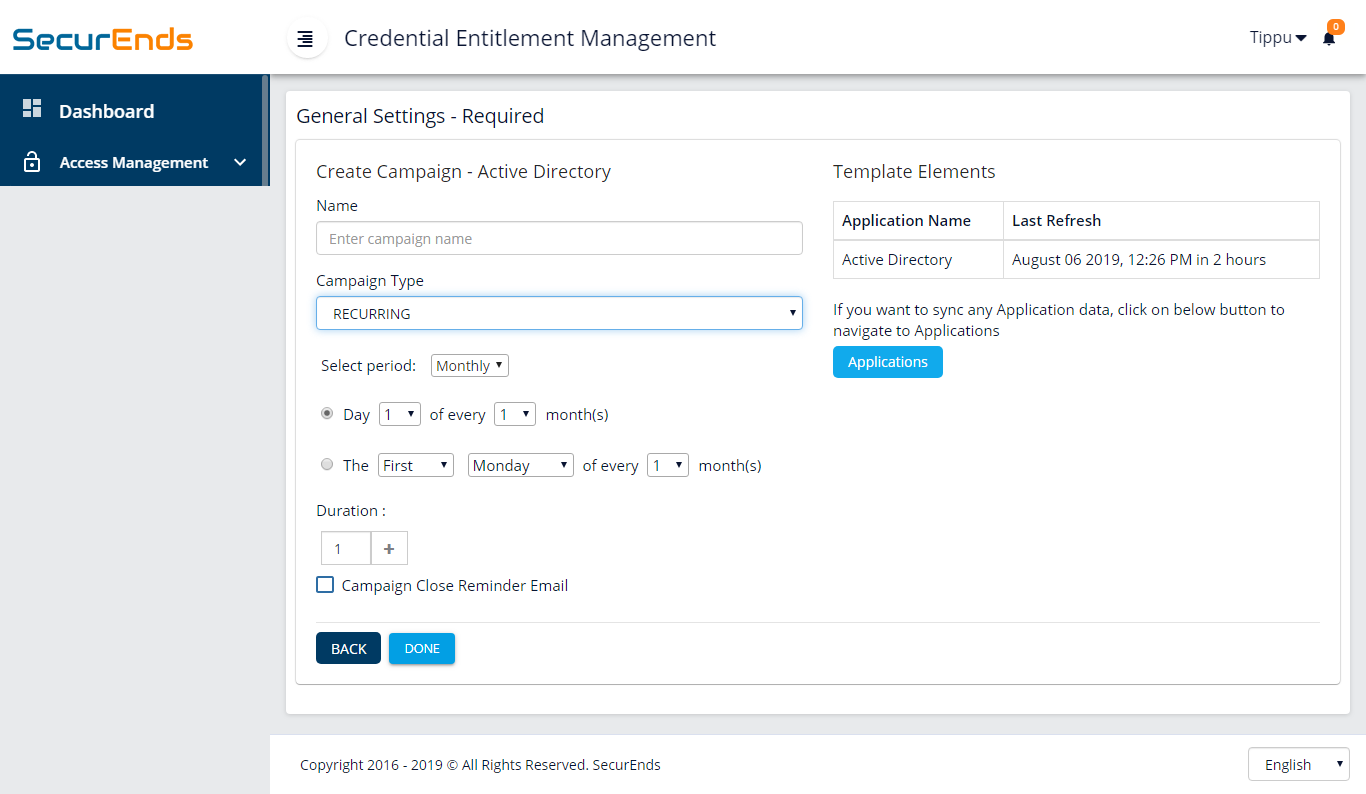
4. Schedule periodic and onetime access review campaigns for applications.
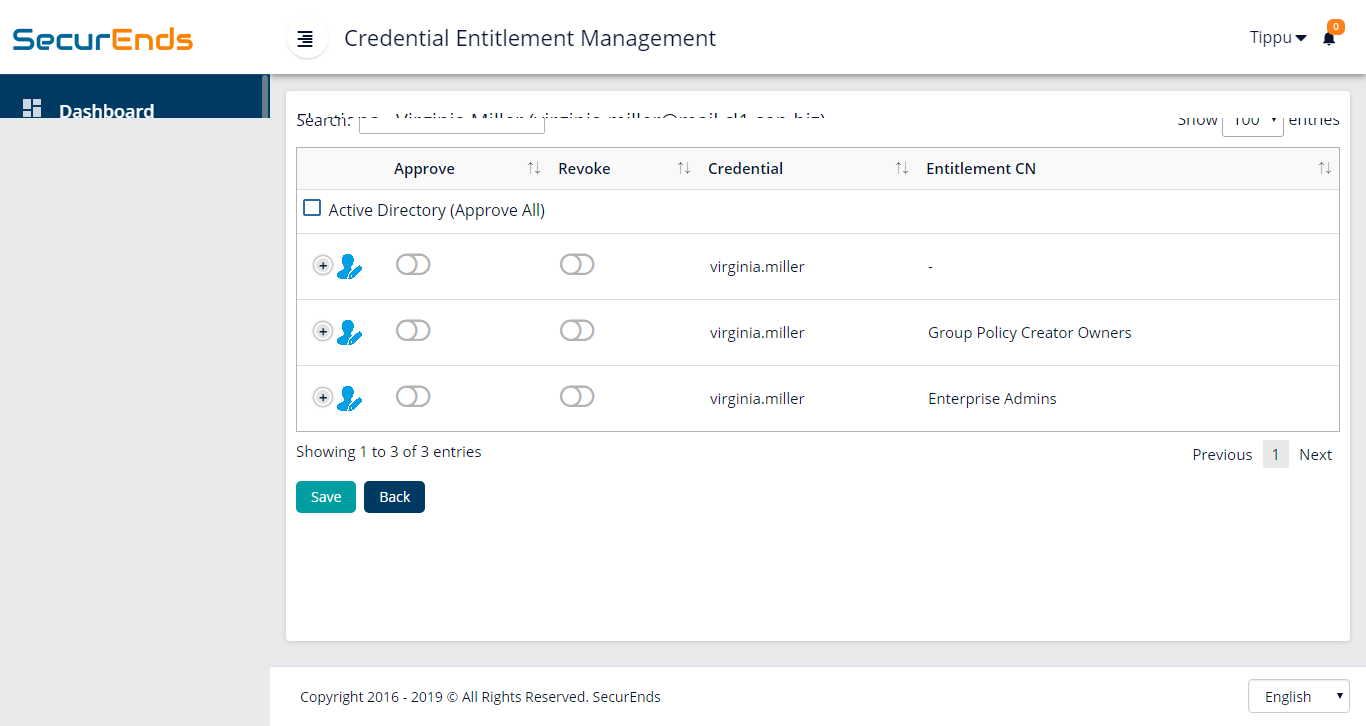
5. Managers/Reviewers to perform access reviews at a secured portal.
6. Complete access certification and generate audit reports for access attestation.
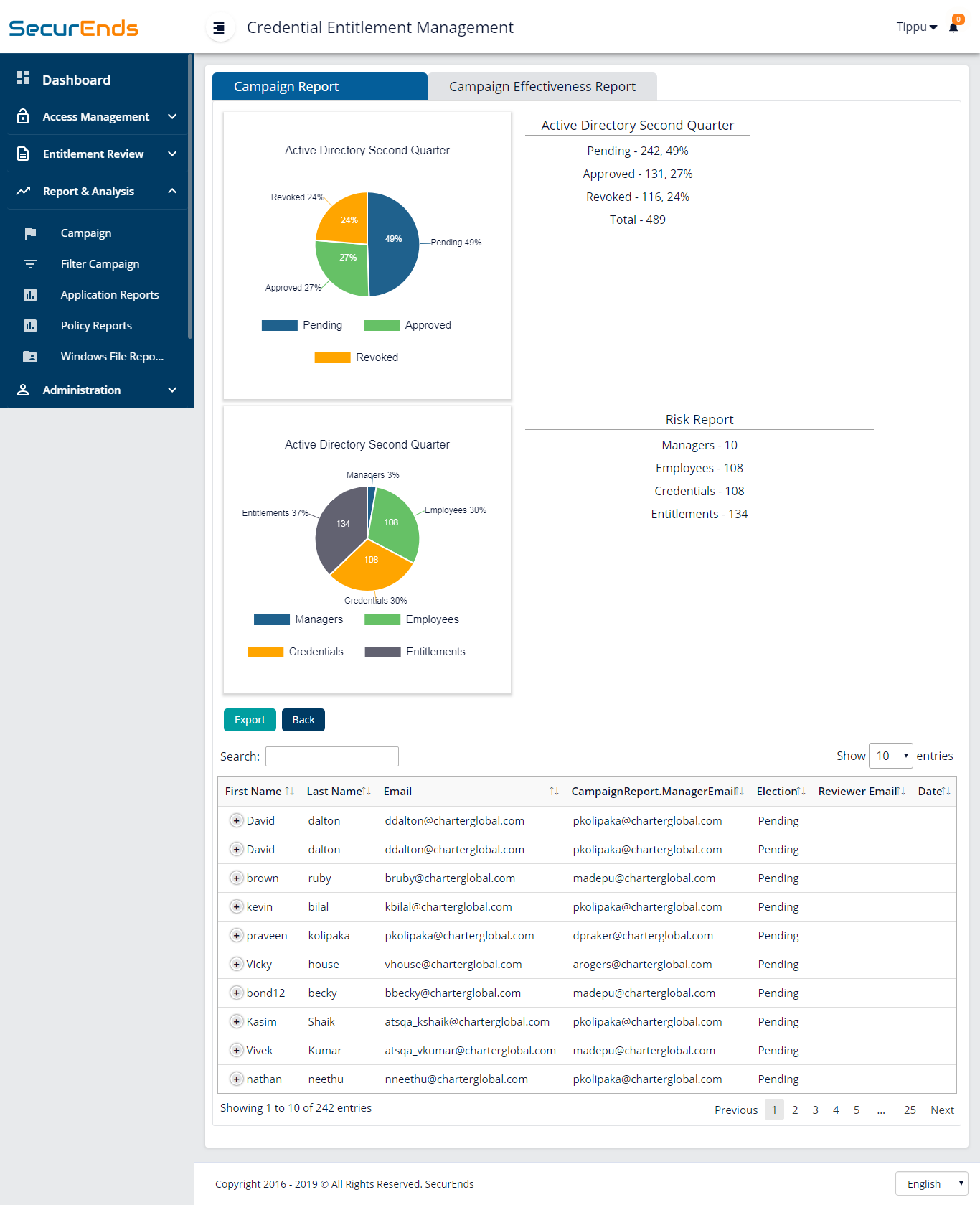
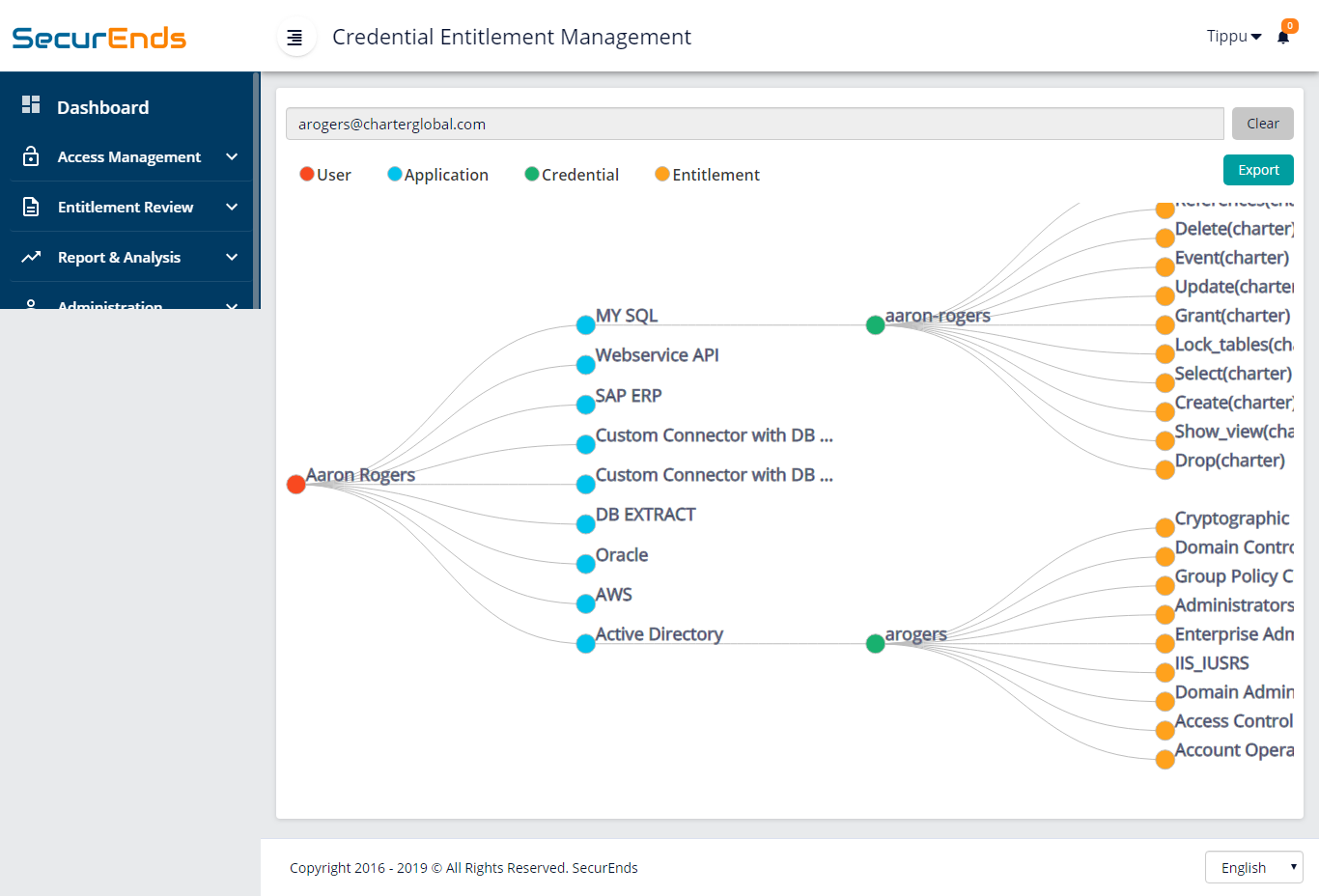
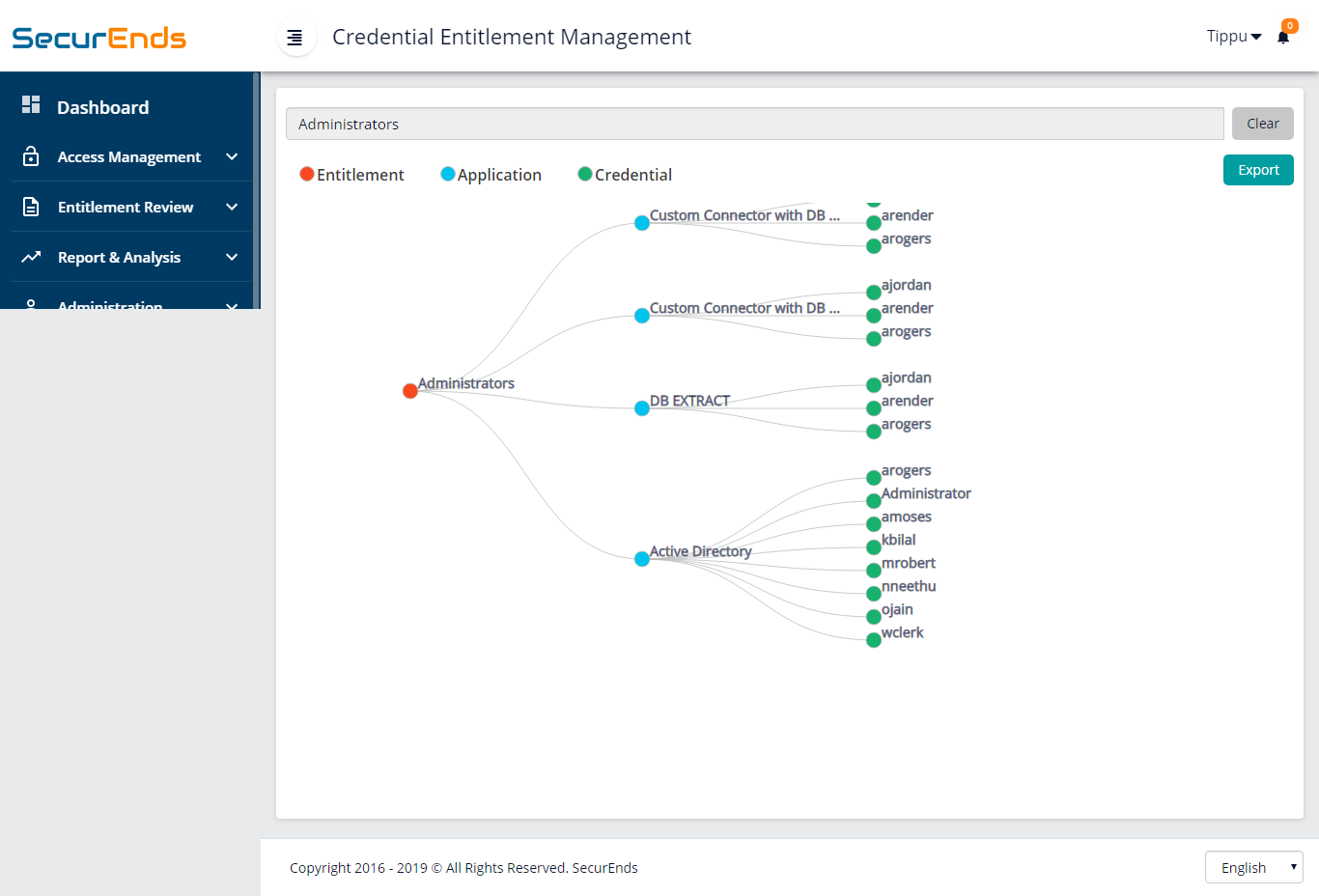
7. Show who has access to what across your enterprise.
8. Rapid implementation using SecurEnds SaaS offering.