Employee Lifecycle Access Management: A Complete Guide to Joiner, Mover, Leaver Workflows
Employee Lifecycle Access Management: A Complete Guide to Joiner, Mover, Leaver Workflows
1. Introduction: Why Lifecycle-Based Access Management Matters
When someone joins your company, it’s not just about handing over a laptop and a login. It’s about giving them access to the right systems — and just as importantly, knowing when to update or remove that access as they change roles or leave.
This is where many organizations struggle. New hires are left waiting for the tools they need. Employees who change departments keep old permissions they no longer need. And those who exit the company sometimes walk away with access still intact — a silent security threat.
These aren’t small issues. Over time, they add up to serious risks: too much access floating around, unclear permission trails, and compliance gaps that make audits stressful. That’s why managing access across the entire employee lifecycle — from onboarding to offboarding — is more than an IT task. It’s a business-critical priority.
Modern organizations need a smarter way to handle this. And that’s where Identity Access Management (IAM) and Identity Governance and Administration (IGA) come in. These systems help ensure that access is granted when it should be, reviewed regularly, and removed the moment it’s no longer needed.
Whether it’s an Employee Self Request, a Contractor Self Request, or even a Just in Time Access Request for urgent needs, every access decision should be guided by clear policies and backed by automation. Features like User Access Reviews and Emergency Access Requests further help organizations stay in control and audit-ready.
At SecurEnds, we help companies make this entire process seamless — connecting HR data with access controls so that every joiner, mover, or leaver gets exactly the access they need, no more and no less.
2. What Is Employee Lifecycle Access?
To manage access effectively, you first need to understand the concept of the employee lifecycle not just from an HR perspective, but from the lens of access and security.
In simple terms, employee lifecycle access refers to how a person’s access to systems, applications, and data changes throughout their time with your organization. These changes typically follow a familiar path, often referred to as the Joiner–Mover–Leaver (JML) process.
- A Joiner is someone being onboarded — a new hire, a contractor, or even a temporary worker. They need the right access to get started without delay.
- A Mover is someone who changes roles — maybe they’ve been promoted, switched departments, or are temporarily taking on new responsibilities. Their access needs to reflect their new position, while removing anything no longer relevant.
- A Leaver is someone who is leaving the organization — whether it’s voluntary, contract-based, or involuntary. Their access must be removed immediately to avoid potential data breaches or compliance violations.
This lifecycle doesn’t just apply to full-time employees. It also includes contractors, vendors, interns, and any third party accessing your systems. Whether through a formal Employee Self Request, a Contractor Self Request, or time-sensitive needs like a Just in Time Access Request, the system must respond with speed and precision.
This is where Identity Governance and Administration (IGA) tools make a difference. They provide the structure needed to manage these transitions — defining access rules, automating approvals, and maintaining oversight throughout the lifecycle.
Visualizing this process as a cycle — Joiner → Mover → Leaver — helps simplify what’s really happening: your access environment is constantly evolving. By aligning access with each stage, organizations reduce risk, avoid overprovisioning, and stay compliant.
3. The Three Stages of JML: Joiner, Mover, Leaver
Every employee’s journey involves transitions — and each transition comes with access requirements that must be carefully managed. Let’s explore the three core stages of the employee lifecycle: Joiner, Mover, and Leaver, and how Identity Access Management (IAM) and IGA solutions support these workflows.
Joiner: Getting Access Right from Day One
The onboarding stage is where security and productivity begin to intersect. New employees, contractors, or vendors — whether through traditional hiring or Employee Self Request — must be granted timely and appropriate access to tools, applications, and data.
When access is delayed, onboarding slows down. When it’s too broad, it opens the door to unnecessary risk. A new sales associate shouldn’t have access to financial reporting systems. Nor should an intern be able to download sensitive customer data.
To prevent this, organizations use Role-Based Access Control (RBAC) and define clear policies based on job functions. When HR systems such as Workday or SAP SuccessFactors flag a new hire, that HR event should automatically trigger a workflow in the IAM platform to assign the right access — no manual handoffs needed.
This is where automated Employee Onboarding becomes critical. It ensures every joiner has the tools to contribute from day one — securely and without delays.
Mover: Managing Access When Roles Change
People rarely stay in the same role forever. Whether through promotions, department transfers, or temporary assignments, employees are constantly shifting — and so are their access needs.
The danger during this stage is privilege creep — when users accumulate permissions over time without anything being taken away. This can result in excess access that violates compliance standards and opens doors to insider threats.
That’s why User Access Reviews are essential, especially during mover events. Regular reviews help validate that users still need the access they have, and tools like dynamic role mapping allow for seamless updates when responsibilities change.
In mature IGA programs, Access Request features let managers or employees initiate changes, while policy engines enforce rules and prevent conflicts, such as violations of Segregation of Duties (SoD).
When done right, mover workflows keep permissions aligned with real-time responsibilities — nothing more, nothing less.
Leaver: Securing the Exit
The final and most sensitive stage is offboarding. Whether an employee is leaving voluntarily or through termination, access should be removed immediately. Delays here can lead to serious consequences — from data theft to misuse of internal systems.
In many breaches, former employees retained access to confidential systems long after their departure. The risk isn’t theoretical — it’s real, and often due to gaps in communication between HR and IT.
This is why automated Employee Off-Boarding is crucial. When an HR system marks someone as a leaver, their access should be revoked instantly across all systems — including cloud apps, VPNs, and collaboration tools.
For urgent cases, systems should also support Emergency Access Requests — ensuring access can be revoked or granted outside regular processes when the situation demands it.
Effective lifecycle access isn’t just about provisioning and deprovisioning — it’s about controlling access dynamically as people join, move within, and leave your organization.
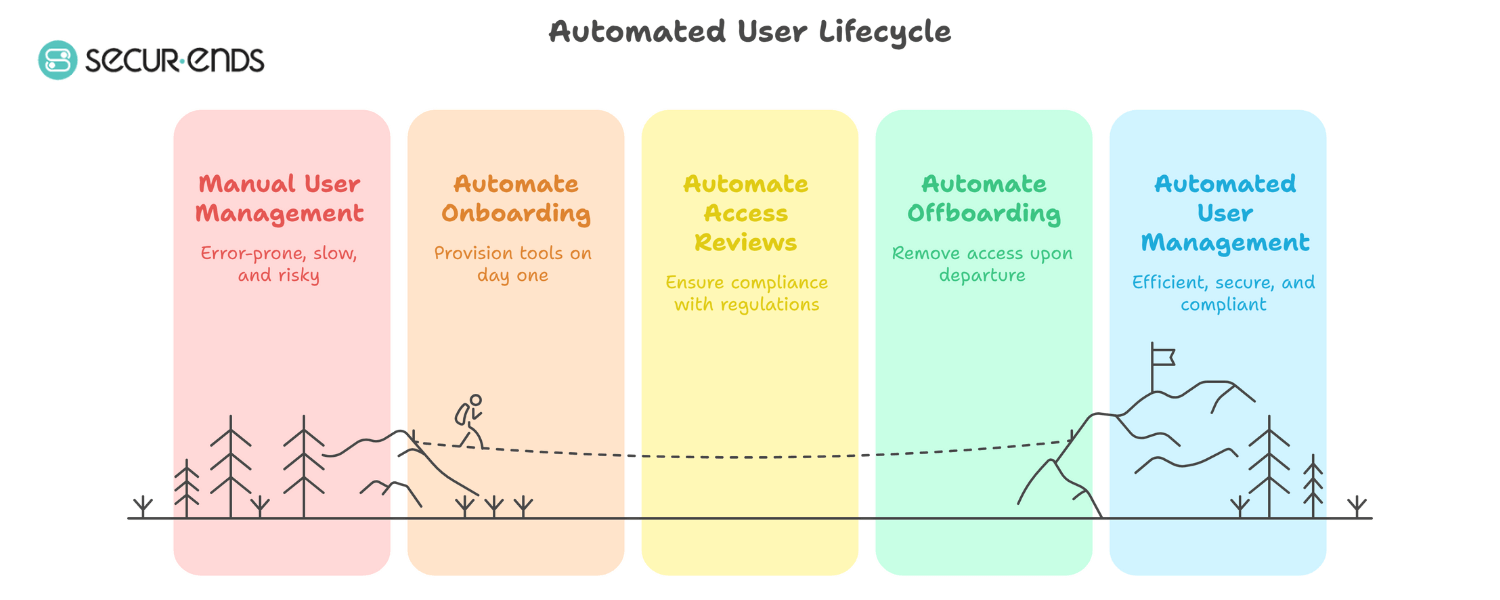
4. Why Manual Lifecycle Access Management Fails
Manual processes might seem manageable when headcount is low or systems are few. But as your organization scales, so does the complexity — and so do the risks. When Joiner–Mover–Leaver workflows are handled manually, delays, inconsistencies, and blind spots are almost guaranteed.
Here’s why relying on spreadsheets, emails, or ticketing systems for access changes just doesn’t work:
Delayed Access Provisioning (or Revocation)
In manual environments, there’s often a lag between an HR event (like a new hire or a resignation) and the corresponding IT action. This delay leaves joiners waiting for access, movers accumulating outdated privileges, and leavers retaining access far longer than they should.
Without automated Employee Onboarding and Off-Boarding processes, IT teams are left chasing requests — and that lag introduces risk.
No Real-Time Updates from HR Systems
In an ideal setup, HR systems act as the single source of truth. But when these systems aren’t integrated with your IAM tools, there’s no real-time sync between workforce changes and access provisioning. HR may record an exit, but unless IT is manually informed, the user could still have access days or even weeks later.
This gap is especially dangerous when managing Contractor Self Requests or temporary hires, where start and end dates are often short and fluid.
Incomplete Deprovisioning
Deprovisioning isn’t just about turning off a user’s email. It involves revoking access across dozens of platforms — cloud services, internal tools, admin consoles, VPNs, and more. Manual offboarding often misses something. And even one overlooked permission can lead to shadow IT risks, data leaks, or compliance violations.
No Audit Trails or Certification
When access changes are made manually, there’s often little to no documentation. Who approved that access? When was it granted? Was it ever reviewed?
Without reliable audit trails or User Access Reviews, proving compliance with standards like SOX, HIPAA, or ISO becomes a challenge — especially during external audits or security assessments.
Real-World Consequences
The risks aren’t theoretical. Many security incidents stem from ex-employees or third-party vendors who still had access to internal systems. In some cases, this has led to financial fraud, ransomware attacks, or breaches of sensitive customer data.
Manual IAM processes can’t keep up with the speed of today’s workforce changes. Whether it’s onboarding a new team member or revoking access during an abrupt departure, timing matters — and manual coordination isn’t fast or consistent enough.
The only sustainable path forward is automation — driven by HR events, governed by policy, and validated through regular review.
5. Automating the Lifecycle: HR-Driven IAM Workflows
If manual processes are the bottleneck, automation is the unlock. With the right integrations and governance policies, every change in the employee lifecycle — whether it’s a hire, promotion, or exit — can automatically trigger the right access actions across your ecosystem.
Let’s break down how HR-driven IAM workflows turn lifecycle events into secure, repeatable, and auditable processes.
HR as the Source of Truth
Modern identity access strategies begin with one principle: access follows the HR record.
Whether it’s a full-time hire logged in Workday, a contractor added in BambooHR, or a promotion updated in SAP SuccessFactors — HR is the first to know. And when integrated properly, that event should immediately trigger workflows in your Identity Access Management (IAM) and Identity Governance and Administration (IGA) systems.
This removes the dependency on IT to interpret and act on changes manually. The process becomes systematic, scalable, and — most importantly — secure.
Automating Access Provisioning, Updates & Revocation
Here’s how automation looks across the lifecycle:
- Joiners: As soon as an HRIS records a new hire, a predefined onboarding workflow assigns access based on role, department, and location. This may include systems like CRM, collaboration tools, and email — all without manual intervention.
- Movers: When employees change roles or take on new responsibilities, IAM systems update their access automatically — removing outdated permissions and assigning new ones according to dynamic role mapping or Just in Time Access Requests.
- Leavers: On the date of separation, systems immediately trigger deprovisioning — closing accounts, revoking tokens, and eliminating orphaned access across all environments.
These workflows ensure consistency across all access changes, whether it’s for a long-term employee or a Contractor Self Request with a short-term engagement.
Benefits of Lifecycle Automation
- Faster Onboarding: Employees hit the ground running with the right tools from day one.
- Reduced Risk: No more forgotten accounts or over-provisioned users.
- Clean Audit Trails: Every access event is recorded, making compliance reporting easy and accurate.
- Less Admin Overhead: IT and security teams gain time back to focus on strategic priorities.
- Compliance Ready: Automated User Access Reviews and policy enforcement keep your organization aligned with regulatory frameworks.
And in urgent scenarios, systems can support Emergency Access Requests, granting time-bound access that automatically expires and is logged for compliance.
When HR data drives your IAM strategy, access management becomes less reactive and more intelligent — adapting in real time to how your workforce evolves.
6. The Role of Identity Governance in Lifecycle Access
Automation handles the how of lifecycle access — but governance defines the why, who, and how much. That’s where Identity Governance and Administration (IGA) comes in.
IGA ensures that every access decision — whether it’s granting permissions to a new joiner, modifying access for a mover, or deprovisioning a leaver — is aligned with organizational policies, risk tolerance, and compliance obligations.
Centralized Visibility & Control
In a typical enterprise, users have access across dozens of systems — from collaboration tools to finance platforms to cloud infrastructure. Without centralized visibility, it’s easy to lose track of who has access to what.
IGA brings that visibility into one dashboard. IT, security, and compliance teams can monitor access across the entire lifecycle — not just during Employee Onboarding or Employee Off-Boarding, but also when employees move across roles.
This centralization also helps identify dormant accounts, unapproved access, or signs of privilege creep — long-term users accumulating excessive permissions over time.
Role-Based Access Control (RBAC)
Rather than assigning access individually, IGA frameworks support Role-Based Access Control (RBAC) — where access is granted based on a user’s job function, department, or seniority.
This model reduces human error, speeds up provisioning, and keeps access consistent across similar roles. For example:
- A new sales executive in New York automatically gets access to the CRM, sales dashboards, and relevant shared drives — without needing a manual Access Request.
- A finance manager promoted to regional lead sees their access update dynamically based on their new role — with unnecessary permissions removed automatically.
RBAC also simplifies lifecycle transitions. Whether it’s a Contractor Self Request or a full-time hire, roles drive access consistently, with less room for error.
While RBAC ensures access aligns with roles, it can be further strengthened with Time-Based Access Controls which limit access to specific time windows. This is especially useful for contractors or temporary roles. Learn how Time-Based Access Controls enhance security and compliance
Enforcing Policies & Preventing Conflicts
With governance in place, organizations can define and enforce access policies — such as:
- No single user can access both payroll and accounts payable systems (to prevent fraud)
- Temporary Emergency Access Requests must auto-expire and be logged
- Certain high-risk systems require multi-level approval before access is granted
These rules enforce segregation of duties (SoD), helping reduce insider threats and meet audit requirements.
User Access Certifications
Governance isn’t just about setting rules — it’s about validating them regularly.
User Access Reviews (UARs) are scheduled certifications where managers or system owners confirm that users still need the access they’ve been granted. These reviews are especially crucial for movers, whose access must evolve with their role.
Automated IGA systems streamline UARs with pre-configured workflows, reminders, and dashboards — ensuring no review slips through the cracks.
Audit Readiness & Compliance
Whether your organization is subject to SOX, HIPAA, ISO 27001, or any other standard, identity governance provides the controls and documentation needed to stay compliant.
You’ll have the reports to show:
- Who had access to what
- When access was granted or revoked
- Whether reviews were conducted on time
- What exceptions, if any, were made — and why
Without this level of accountability, compliance becomes a guessing game. With governance, it becomes a checklist.
In short, automation executes. Governance ensures it’s done right.
7. How SecurEnds Simplifies Lifecycle Access Management
Managing joiners, movers, and leavers efficiently isn’t just about avoiding risk — it’s about enabling your organization to move faster, stay compliant, and scale with confidence. This is where SecurEnds steps in — offering a streamlined, purpose-built solution for lifecycle access management rooted in automation and identity governance.
Let’s explore how SecurEnds simplifies the complexities of Identity Access Management (IAM) through smart integrations, policy-driven workflows, and complete visibility.
Native HRIS Integrations for Real-Time Triggers
SecurEnds connects directly with leading Human Resource Information Systems (HRIS) like Workday, BambooHR, and SAP SuccessFactors — turning HR events into real-time access triggers.
- Employee Onboarding: As soon as HR creates a new user record, SecurEnds provisions access based on predefined roles, department policies, and job responsibilities — without manual intervention.
- Employee Off-Boarding: The moment an employee’s status changes in HRIS, SecurEnds kicks off automated deprovisioning — revoking access across all systems and eliminating lingering entitlements.
This alignment between HR and IAM eliminates lag, reduces human error, and ensures that access reflects real-time employment status.
No-Code Workflow Builder for JML Automation
Every organization’s lifecycle process is unique — which is why SecurEnds offers a flexible, no-code workflow builder tailored for Joiner, Mover, Leaver (JML) scenarios.
You can customize onboarding sequences, route Self Requests, enable Just in Time Access Requests, or define escalation paths for Emergency Access Requests — all with drag-and-drop simplicity.
Whether it’s for full-time employees, contractors, or temporary staff, workflows are easy to adapt, audit, and deploy at scale.
Periodic User Access Reviews Built In
User access doesn’t stay static — and neither should your review process.
SecurEnds enables User Access Reviews that are tied directly to lifecycle events. For example:
- When a user changes departments, their manager is automatically prompted to review and approve (or revoke) existing access.
- Regular certifications ensure Contractor Self Requests don’t linger beyond the contract period.
- Exception cases, like Emergency Access, are flagged for post-facto attestation.
This review mechanism closes the loop between provisioning, usage, and revocation — keeping your organization audit-ready at all times.
Unified Dashboard for JML Visibility
One of SecurEnds’ strongest advantages is its centralized dashboard, which offers real-time insights into your user base:
- View how many joiners were onboarded in the last 30 days
- Track pending access reviews or offboarding tasks
- Identify anomalies, such as users with excessive or conflicting access
By mapping every identity to its lifecycle stage, SecurEnds makes it easy to spot risks early and take informed action.
Customer Success in Action
A leading healthcare provider recently implemented SecurEnds to manage lifecycle access for over 10,000 employees and contractors across multiple locations.
Before SecurEnds, onboarding took days, movers accumulated unnecessary access, and offboarding relied heavily on email trails. After deployment:
- Onboarding time was cut by 70%
- Automated User Access Reviews increased compliance scores
- HR and IT aligned through integrated workflows, reducing errors and gaps
That’s the impact of getting JML automation and governance right — measurable efficiency with zero compromise on security.
8. Best Practices for Implementing Lifecycle-Based Access
Implementing lifecycle access management isn’t just about deploying the right tools — it’s about creating a framework where HR, IT, and security teams work in sync, guided by clear policies and automated workflows. Whether you’re just beginning your journey with Identity Access Management (IAM) or optimizing an existing setup, these best practices will help establish a secure, scalable foundation.
1. Start with Accurate and Up-to-Date HR Data
Your access management system is only as reliable as the data feeding into it. Since employee status, role, and department changes typically originate in your HR platform, it’s crucial to:
- Ensure clean and standardized HRIS data
- Establish consistent naming conventions
- Regularly audit HR feeds for accuracy
This ensures that Employee Onboarding, Mover events, and Employee Off-Boarding workflows are triggered precisely and without delay.
2. Define Roles and Access Policies Clearly
Ambiguity is the enemy of access control. Define roles and entitlements based on job functions, departments, and project needs. Use Role-Based Access Control (RBAC) to:
- Minimize privilege creep
- Standardize provisioning rules
- Support Just in Time Access Requests and Self Request flows securely
These clear policies are the foundation for scalable automation and governance.
3. Automate Wherever Possible
Manual provisioning and deprovisioning are time-consuming and prone to error. Automating Joiner–Mover–Leaver (JML) workflows helps eliminate these risks and ensures:
- Fast, policy-driven Employee Onboarding
- Timely access updates for movers
- Complete, consistent Employee Off-Boarding
Automation also extends to Contractor Self Requests and Emergency Access Requests, enabling real-time responsiveness with full audit trails.
4. Conduct Regular User Access Reviews
Don’t wait for audits to catch access gaps. Instead, schedule periodic User Access Reviews aligned with lifecycle events. This helps:
- Confirm that movers retain only what they need
- Detect dormant or orphaned accounts
- Validate temporary access or contractor permissions
User Access Reviews also reinforce your Identity Governance and Administration (IGA) framework and support compliance mandates.
5. Ensure Continuous Visibility Across Access Lifecycle
To maintain control at scale, organizations need more than automation — they need insight.
Implement centralized dashboards to:
- Monitor active joiners, movers, and leavers
- Flag exceptions or access anomalies
- Track the lifecycle of every access request, from Employee Self Request to revocation
This visibility builds trust between IT and HR while improving response times and security posture.
6. Align IT and HR Teams on Lifecycle Triggers
Finally, success in lifecycle access depends on cross-functional alignment. Both teams should:
- Share a common understanding of key JML events
- Agree on trigger points, approval flows, and escalation paths
- Collaborate on process refinement and feedback loops
This collaboration ensures lifecycle access management is not just a security initiative, but an enterprise-wide operational improvement.
9. Conclusion: Secure Every Step of the Employee Lifecycle
Access is no longer just about credentials — it’s about context.
Who is the user? What do they need right now? And just as important — what don’t they need anymore?
Every organization is in constant motion. People join, change roles, take on new responsibilities, or move on. But when access management doesn’t evolve with them, the result isn’t just inefficiency — it’s risk.
That’s why lifecycle-based access management is no longer a “nice to have.” It’s the quiet engine that powers secure, compliant, and scalable operations.
From Employee Onboarding that sets the right permissions from day one, to dynamic updates during internal moves, to clean and immediate Employee Off-Boarding, every stage matters. Add in Just in Time Access Requests, Contractor Self Requests, and periodic User Access Reviews, and it becomes clear: access must be fluid, responsive, and intelligent.
That’s exactly what SecurEnds delivers.
With automated workflows, seamless HRIS integrations, and full support for Identity Access Management (IAM) and Identity Governance and Administration (IGA) practices, SecurEnds empowers organizations to:
- Cut down access delays
- Prevent privilege creep before it starts
- Stay audit-ready, always
In a world where one overlooked permission can become a breach, lifecycle-aware IAM isn’t just good governance — it’s peace of mind.
Because access should move at the speed of your people.


