How Decentralized User Access Reviews Empower Efficiency in Large Enterprise Companies [Identity Experts Series]
How Decentralized User Access Reviews Empower Efficiency in Large Enterprise Companies [Identity Experts Series]

In this article, we’ll explore the differences between centralized and decentralized user access review management in large enterprises. After learning the pros and cons of each, you’ll also find out why choosing the right SaaS solution is key to making the most of your efforts.
There’s a pivotal shift that’s reshaping how user access reviews are performed for big businesses. When it comes to global enterprises, efficient management of user access is essential for keeping a strong cybersecurity posture and staying compliant with regulations.
However, the traditional centralized user access review process, which aims to streamline access rights approvals, presents challenges for large businesses with diverse entities spanning multiple countries – here’s why.
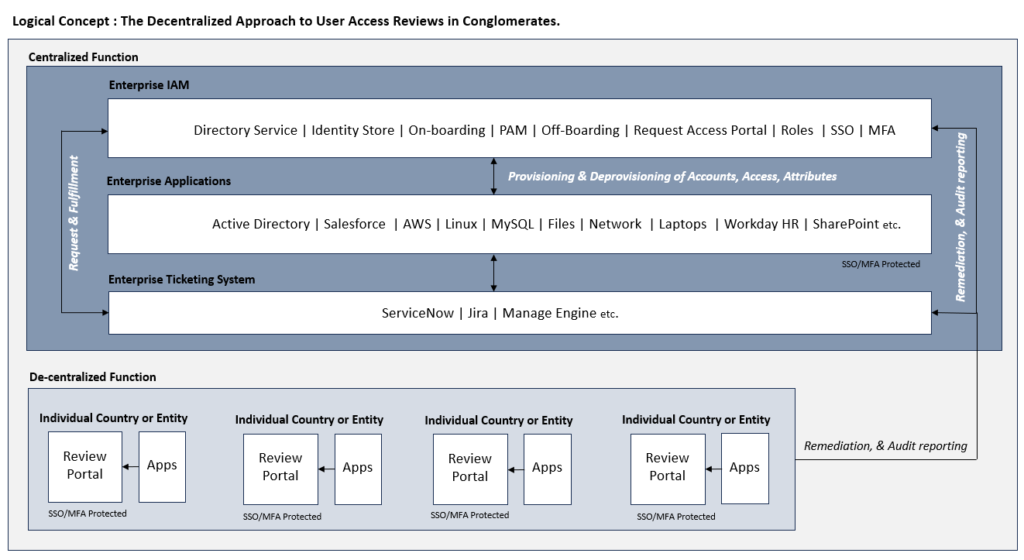
The problem with centralization
Centralized user access reviews typically involve consolidating the responsibility for reviewing and approving access rights within a single entity, often the IT department or a dedicated team. While this approach seeks to standardize the process and uphold security protocols, it’s not without its drawbacks. Let’s look at the pros and cons of centralization:
Pros
- Standardization: Ensures a uniform approach to user access reviews, aligning with predefined standards and best practices, but it may not be the ideal fit for large enterprises. This is due to their complex and diverse organizational structures, which makes it difficult to enforce a one-size-fits-all model across entities spanning multiple countries.
- Control: Provides authority over the entire access review process.
Cons
- Integration Complexity: Integrating enterprise user access review solutions is rarely a simple task, especially with a diverse set of applications.
- Resource Costs: Both in terms of technology infrastructure and human resources, since these tools have high license and implementation costs. Moreover, large enterprise organizations often require third-party service providers to offer integration services, further contributing to the financial burden. Additionally, the intricacies of centralized tools often necessitate technical expertise for effective management, adding another layer of complexity and resource demand to the overall maintenance process.
Decentralized UARs give you more freedom
In response to the obstacles posed by centralized user access reviews, a decentralized approach is gaining momentum. This paradigm shift involves delegating the responsibility for access reviews to individual application owners, entity owners, department heads, or sister companies within the business. Here are some pros and strategic advantages to this methodology:
Pros
- Efficiency: Decentralization facilitates a more agile and responsive user access review process, reducing bottlenecks and expediting approvals.
- Cost-Effective: Distributing responsibility enables large enterprises to optimize resources and allocate review tasks to those closest to its applications and data.
Strategic Advantages
- Local Compliance Adherence: Decentralization becomes a strategic imperative to adhere to local regulations and compliance requirements. Different countries may have unique access review standards, and a decentralized approach allows for tailored compliance at each entity.
- Audit Preparedness: Creating a bottleneck can lead to failed audits, especially when auditors require evidence of timely and thorough access reviews. Decentralization enhances audit preparedness by ensuring a more agile and responsive approach to compliance requirements.
Accelerate mergers and acquisitions
Decentralized user access reviews offer substantial benefits during mergers and acquisitions (M&As), where speed and efficiency are vital to success. Here are a few benefits and recommendations for this scenario:
Benefits
- Integration Agility: Decentralization simplifies the integration of new entities by allowing them to manage their own access reviews. This not only accelerates the integration process but also ensures compliance with local regulations.
- Reduced Bottlenecks: Centralized processes often create bottlenecks during M&As, delaying the integration of systems and data. Decentralization streamlines this process, allowing for a faster and smoother transition.
Recommendations
- Proactive Compliance: Emphasize the role of decentralized user access reviews in proactively addressing compliance requirements, mitigating the risk of failed audits.
- M&A Integration Strategy: Incorporate access reviews as a core strategy in M&A planning, facilitating quicker and more efficient integrations.
Decentralized user access reviews, when powered by a SaaS solution such as SecurEnds, bring a myriad of benefits that not only address the challenges of centralized approaches but also revolutionize the entire review process. Here are some key advantages to this:
- Ease of Use: SecurEnds is designed with a user-friendly interface, making it accessible to individuals across various departments and levels of technical expertise. This ease of use ensures that the user access review process is intuitive and can be efficiently managed by a broader audience within the organization.
- Rapid Deployment and Go-Live: Unlike traditional software implementations that can be time-consuming, SecurEnds includes rapid deployment and quick go-live capabilities. This agility is particularly beneficial for large enterprises that need to adapt swiftly to changing access requirements or new compliance standards.
- No Technical Savvy Required: SecurEnds is known for simplicity and straightforward functionality. By eliminating the need for in-depth technical expertise, individuals from various departments can manage user access reviews without the requirement of specialized IT skills. This democratization of the process enhances efficiency across the board.
| Centralized | Decentralized | |
| Average time to launch UARs for a single application | 15-30 days | 2 hours |
| Average backlog of applications to be onboarded | 3-6 months | None |
| Skillset required to iterate applications and launch campaigns | IT/Development | Business/Analyst |
- Cost-Effectiveness: SecurEnds operates on a subscription-based model, eliminating the need for significant upfront investments in software licenses and infrastructure. This cost-effective approach is particularly advantageous for conglomerates looking to optimize resources and reduce overall expenses associated with user access reviews.
- Scalability: SecurEnds offers scalability to accommodate the dynamic nature of enterprise organizations. Whether you’re expanding operations or undergoing structural changes, SecurEnds can easily scale to meet evolving user access review requirements without the need for extensive modifications or system overhauls.
- Automated Updates and Maintenance: SecurEnds handles routine updates and maintenance, ensuring that the system is always up to date with the latest features and security patches. This alleviates the burden on internal IT teams and guarantees a consistently secure and high-performance user access review environment.
- Accessibility and Collaboration: SecurEnds operates in the cloud, providing accessibility from any location with an internet connection. This promotes collaboration among decentralized entities, allowing them to seamlessly participate in the user access review process regardless of geographical boundaries.
- Reduced Implementation Time: SecurEnds has a shorter implementation cycle compared to traditional software. This accelerated timeline is crucial for conglomerates seeking to quickly deploy user access reviews without lengthy delays.
Adopting a decentralized approach to user access reviews in large enterprise companies isn’t just a strategic choice anymore but a vital necessity.
Through the empowerment of individual entities and the integration of modern SaaS solutions like SecurEnds, enterprises can unlock rapid efficiency, adhere to local regulations, and expedite M&A processes. This establishes simultaneous maintenance of a strong cybersecurity posture without compromising on standards.
It’s time to recognize decentralization as the linchpin, offering a more agile, compliant, and secure future for today’s businesses.
✍ Article by Sushank Vallepalli, Vijay Doraiswamy, and Michael Kruzer