Nexus AI Security
The Authorization Layer for
AI Agents
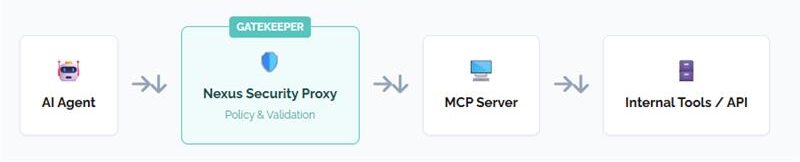
AI agents are now calling your tools, moving your data, and triggering real workflows. Nexus Security Proxy sits in front of your MCP servers to enforce policy-driven authorization, payload validation, and governance before any action is executed.
Built for Model Context Protocol (MCP)
Policy-as-Code for AI & tools
Zero Trust for agent actions
< 25ms p95 authorization latency
The New Gap in AI Security
AI Agents Are the New Identity.
Who’s Authorizing Them?
We’ve learned how to secure users, devices, and applications. But AI agents don’t fit neatly into any of those categories:
They don’t sign in through Okta or Azure AD.
They don’t have HR records, onboarding, or offboarding.
Yet they can move money, query sensitive data, and call internal tools via MCP and APIs.
A Gatekeeper for AI Agents and MCP Tool Calls
Nexus Security Proxy is a lightweight, high-performance gateway that sits in front of your Model Context Protocol (MCP) servers. It evaluates every request from AI agents and clients, then decides whether to:
ALLOW
DENY
TRANSFORM
Key Outcomes
Nexus brings Zero Trust principles to AI by treating every agent-to-tool call as an authorization decision.
Stop unauthorized tool calls
Enforce compliance on payloads
Centralize policy across MCP servers
Full visibility into AI actions
Designed for AI-Forward, Security-Critical Organizations
What Nexus Security Proxy Delivers


Built to Complement, Not Replace, Your MCP Servers
MCP servers manage tool definitions. Nexus manages authorization. It provides a single control layer across multiple servers and tools.
Flexible Deployment for Modern AI Platforms
Performance Targets
Real-World Scenarios Nexus Secures
Starting with Authorization.
Growing into Full AI Governance.
Near-Term Enhancements
- Adaptive and context-based risk scoring
- Optional step-up (MFA/Approval) for high-risk actions
- Shadow mode for policy testing
Long-Term Vision
- AI identity lifecycle management
- Access reviews for AI agents
- Behavior analytics & anomaly detection
- Data boundary and DLP integrations
Why an Authorization Proxy is the Right Primitive
Instead of hardcoding RBAC and business rules into each MCP server, enterprises gain a shared control plane that can evolve as AI usage grows.
Decouples security policy from application logic
Scales with your AI adoption, not just a single project
Centralizes control across many servers and tools
Supports governance and compliance from day one
Frequently Asked Questions
We already have an MCP server with some RBAC. Why do we need this?
MCP RBAC is typically scoped to a single server and doesn’t handle payload policies, multi-environment governance, or centralized audit. Nexus gives you a cross-platform authorization fabric for all AI agents and servers.
Does this slow down our AI workloads?
Nexus is optimized for low-latency authorization. Policies are evaluated in-memory, with sub-25ms p95 targets, and the design is fully stateless for horizontal scaling.
Do we need to modify our AI agents or MCP servers?
In most cases, no. Nexus can run as a reverse proxy with no changes, making adoption quick and low-risk.


