Ultimate Guide to User Access Control (UAC): Models, Implementation, and Best Practices for 2025
Ultimate Guide to User Access Control (UAC): Models, Implementation, and Best Practices for 2025

Introduction
In today’s boundaryless digital world, your organization’s most valuable assets aren’t just stored in vaults—they’re spread across cloud platforms, remote endpoints, mobile devices, and enterprise applications. And with every login, every access request, and every role change, a question is silently posed: Should this user really have access to this information—right now?
This is the question that User Access Control (UAC) answers. It’s not just a cybersecurity feature; it’s the foundation of trust in modern IT environments. From financial institutions and healthcare systems to tech startups and global enterprises, the ability to control who gets access to what—and when, where, and how—has become a defining factor of operational resilience.
Modern access control isn’t static. It’s dynamic, contextual, and adaptive—powered by policy, behavior, and identity. Whether you’re implementing structured access via Role-Based Access Control (RBAC) or exploring the flexibility of Attribute-Based Access Control (ABAC), the goal is the same: to give the right people the right access, for the right reasons, at the right time.
In this comprehensive guide, we’ll break down everything from UAC basics and core models to advanced implementation strategies, hybrid-cloud challenges, and best practices tailored for 2025’s ever-shifting digital terrain.
Ultimate Guide to UAC in 2025
- User Access Control (UAC) ensures secure, policy-driven access across cloud and hybrid environments
- It is central to modern identity and security strategies like Zero Trust and least privilege
- Models like RBAC and ABAC offer scalable ways to manage diverse access needs
- UAC helps reduce risk, support compliance, and improve operational efficiency
- Automation, visibility, and regular reviews are key to long-term UAC success
What is User Access Control (UAC)?
At its core, User Access Control (UAC) is a cybersecurity framework that governs who can access digital resources within an organization—and under what conditions. It defines how identities are authenticated, how permissions are assigned, and how access to systems, applications, and data is enforced and monitored.
In simpler terms, UAC acts like a system of digital keys. Imagine your IT environment as a high-security building with dozens of rooms—servers, databases, apps, and cloud services. Each user is given a key (or a set of keys) that unlocks only the rooms they need to do their job. Nothing more, nothing less.
The Purpose of UAC in Cybersecurity
The primary goal of UAC is to protect sensitive data and systems from unauthorized access, whether the threat comes from external attackers or internal users with excessive privileges. But its purpose goes beyond protection. UAC also ensures operational efficiency, supports regulatory compliance, and enables secure collaboration across distributed teams, vendors, and devices.
Key Elements of UAC
A robust User Access Control system typically includes:
- Identity Verification – Confirming the legitimacy of a user through authentication.
- Access Permissions – Defining what a user can see or do within a system.
- Policy Enforcement – Applying business rules to ensure access is consistent, secure, and compliant.
These components are often part of larger Identity Access Management (IAM) and Identity Governance and Administration (IGA) strategies, providing a structured approach to managing digital identities across cloud, hybrid, and on-premise environments.
Now that we understand what UAC is and what it does, let’s explore why it’s not just helpful—but essential—for protecting modern enterprises from growing security risks.
Why User Access Control Is Essential
As we’ve discussed, UAC plays a central role in maintaining a secure environment for organizations. But its significance extends far beyond just preventing unauthorized access. In today’s complex digital landscape, a robust UAC framework is crucial for mitigating risks, ensuring regulatory compliance, and enabling businesses to thrive in a hybrid, cloud-enabled world.
1. Preventing Unauthorized Access
The most fundamental aspect of UAC is its ability to prevent unauthorized access—whether that be from cybercriminals or internal threats. By tightly controlling who can access what resources, organizations can significantly reduce the risk of data breaches. Without effective UAC, sensitive information becomes vulnerable, and the potential for security incidents increases.
2. Reducing the Risk of Data Breaches and Privilege Abuse
Data breaches and privilege abuse are among the most dangerous threats facing enterprises today. UAC is essential in addressing both of these risks by ensuring that users only have access to what is necessary for their job. This principle is not just about limiting access—it’s about enforcing least privilege and ensuring that access is continually monitored. This also supports an organization’s IAM Risk Management efforts by minimizing the exposure of critical systems and data.
3. Enabling Data Privacy and Regulatory Compliance
In an increasingly regulated environment, UAC is not just a best practice—it’s often a legal requirement. Compliance with standards such as GDPR, HIPAA, and ISO 27001 demands strict oversight of who has access to sensitive data. UAC systems provide detailed audit trails and access logs, ensuring organizations can prove compliance during audits and avoid costly penalties. Moreover, it supports businesses in managing their customer identity and access management responsibilities.
4. Supporting Modern Workforces
With the rise of remote work, BYOD (Bring Your Own Device) policies, and partnerships with third-party vendors, the workforce has become more decentralized than ever. UAC ensures that remote employees, contractors, and vendors only access the resources they need, regardless of their device or location. This adaptability is particularly important when integrating systems with Federated Identity & Access Management (IAM), which helps organizations manage access across disparate environments while maintaining robust security.
5. Integral to IAM Strategies
UAC is not an isolated function—it’s a core part of an organization’s larger Identity and Access Management (IAM) strategy. IAM solutions offer a holistic approach to identity governance, ensuring the right individuals have the right access at the right time. With UAC integrated into IAM systems, businesses can automate access decisions and enforce policies across all user interactions, supporting stronger security and compliance.
Having outlined why UAC is essential for modern enterprises, it’s now time to explore how UAC actually works in practice. Understanding the workflow behind authentication, authorization, and access is critical to realizing its full potential in your organization’s security framework.
How User Access Control Works
While the concept sounds straightforward—managing who has access to what—it involves a coordinated process built on several critical mechanisms that support both security and operational efficiency.
1. The Access Control Flow: Authenticate → Authorize → Access
The UAC process begins with authentication, where a user’s identity is verified using methods like passwords, biometrics, or multi-factor authentication (MFA). Once identity is confirmed, authorization determines what resources the user is allowed to access. Finally, access is granted based on the defined permissions and policies.
This flow is foundational to Identity Access Management (IAM) systems, which are designed to automate and enforce access decisions across the organization.
2. Access Decision Points
Every access decision considers multiple factors:
- Who is requesting access? (User identity, role, attributes)
- What are they accessing? (Applications, files, systems)
- When and where is the request being made? (Time of access, device used, location)
- How is the user accessing the system? (Via VPN, internal network, or cloud apps)
This contextual decision-making is what enables advanced models like Attribute-Based Access Control (ABAC) and supports IGA security measures, which demand precise control over access conditions.
3. Integration with IAM Ecosystem
For UAC to be truly effective, it must integrate seamlessly with other components of the identity infrastructure:
- Single Sign-On (SSO) simplifies access across multiple applications.
- MFA strengthens authentication.
- Directory services like Active Directory (AD) and LDAP manage identities centrally.
- Scim API allows standardized user provisioning and deprovisioning, improving efficiency and reducing human error.
Such integrations are especially critical in environments using Federated Identity & Access Management, where access must be governed across multiple platforms and domains—often involving third-party apps and cloud services.
4. Visualizing the UAC Workflow
Here’s a simplified breakdown of how UAC typically functions within an organization:
User Request → Identity Verification (MFA/SSO) → Access Evaluation (Policies + Roles + Attributes) → Access Granted/Denied → Activity Logged
This process is continuously monitored and adjusted based on evolving policies, user roles, and risk assessments—all core elements in effective Identity Governance and Administration (IGA).
By understanding the mechanics of how UAC works, organizations can make more informed decisions when building their access control architecture. Up next, we’ll dive into the key components that make a UAC system truly robust and future-ready.
Key Components of a Robust User Access Control System
An effective User Access Control (UAC) strategy isn’t just about putting up barriers—it’s about building an intelligent, responsive framework that ensures the right people have access to the right resources at the right time. This requires a combination of foundational components that work together under the broader umbrella of Identity Governance and Administration (IGA).
1. User Identities and Roles
Every UAC framework starts with understanding who your users are. This includes not only employees, but also contractors, third-party vendors, and partners. Within Identity Access Management (IAM), identities are tied to roles—collections of permissions that reflect a user’s responsibilities. This structure supports Role-Based Access Control (RBAC), ensuring consistency and clarity across the organization.
2. Permissions and Entitlements
Once identities and roles are defined, organizations must assign permissions—what each user or role is entitled to access. This could include applications, databases, files, or infrastructure. Defining entitlements clearly is essential to avoid over-provisioning or privilege creep, both of which are common risks in access management.
3. Access Policies
Policies are the rules that govern access decisions. These can be static (role-based) or dynamic, taking context into account. In modern environments, combining RBAC with Attribute-Based Access Control (ABAC) results in more adaptive, risk-aware systems. These policies are especially important for aligning UAC with customer identity and access management strategies in digital-facing applications.
4. Authentication Mechanisms
Strong authentication is the gateway to secure access. Organizations are moving beyond passwords to incorporate:
- Multi-Factor Authentication (MFA)
- Biometric verification
- One-time passwords (OTPs)
Such measures are vital to IAM risk management, reducing the chances of identity-related breaches and unauthorized access.
5. Audit Logs and Monitoring
Visibility is non-negotiable. UAC systems must generate detailed logs of every access request—who accessed what, when, and how. These logs support ongoing User Access Reviews, compliance audits, and anomaly detection. Logging also enables historical analysis, helping organizations respond swiftly to incidents and meet audit requirements under standards like ISO 27001 or SOX.
6. Automation and Integration
To maintain accuracy and efficiency, modern UAC systems leverage automation—especially in provisioning and deprovisioning user access. Tools using the SCIM API help streamline identity syncing across platforms, reducing manual errors and improving compliance with identity governance and administration solutions.
A well-structured UAC system built on these components doesn’t just secure your environment—it also supports operational agility and regulatory alignment. Next, we’ll explore the various access control models available, helping you choose the approach that best fits your organizational needs.
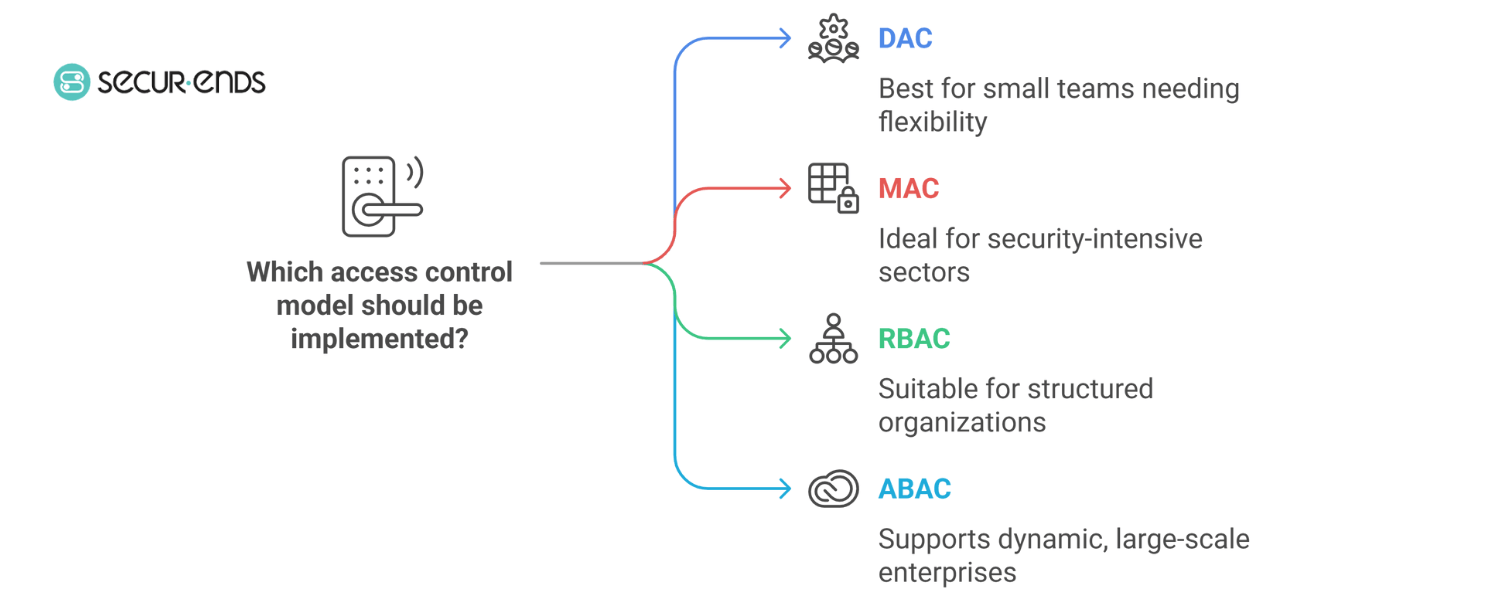
4 Core Types of Access Control Models
A strong UAC strategy isn’t just about defining who gets access—it’s about selecting the right access control model that aligns with your organization’s structure, risk posture, and regulatory responsibilities. Each model differs in how it handles access permissions, and understanding these differences is key to making informed decisions.
- Discretionary Access Control (DAC)
In DAC, the owner of a file or system resource decides who gets access and what level of access is granted. While DAC offers flexibility and is easy to implement in smaller environments, it often lacks the centralized oversight needed for enterprise-grade Identity Governance and Administration (IGA). This model can increase the risk of privilege sprawl, making ongoing User Access Review (UAR) and IAM Risk Management more challenging. - Mandatory Access Control (MAC)
MAC enforces access based on fixed security labels and classifications defined by system administrators. Commonly used in defense, healthcare, and government systems, MAC prioritizes confidentiality and policy enforcement over user convenience. It aligns well with stringent regulatory frameworks such as ISO 27001, but may not provide the agility needed in customer identity and access management or dynamic cloud-first environments. - Role-Based Access Control (RBAC)
RBAC is a widely adopted model in enterprise IAM. It assigns access based on a user’s job role within the organization. This simplifies provisioning and ensures consistent permissioning across departments. RBAC supports scalable identity governance and administration solutions, and is a foundation for many identity access management certifications. When paired with automation, it helps reduce over-provisioning and streamlines compliance efforts. - Attribute-Based Access Control (ABAC)
ABAC considers user attributes (e.g., department, device, location), resource attributes, and environment conditions to make access decisions. This model offers granular control and dynamic policy enforcement, making it ideal for hybrid workforces and cloud-native ecosystems. ABAC integrates seamlessly with IAM platforms that support Scim API and federated identity & access management, helping organizations implement real-time, context-aware access governance.
Rule-Based Access Control and Policy-Based Access Control (PBAC)
Comparison Table: Access Control Models
| Model | Control Level | Flexibility | Ideal For | Risk Level |
| DAC | User | High | Small teams, dev environments | High |
| MAC | Admin | Low | Military, government | Low |
| RBAC | Role-based | Medium | Enterprises, regulated sectors | Medium |
| ABAC | Contextual | High | Cloud-native orgs, SaaS apps | Low |
Which Model Is Right for You?
Each model serves different use cases:
- DAC suits small teams that prioritize flexibility
- MAC is ideal for highly regulated, security-intensive sectors
- RBAC works well in structured organizations with defined roles
- ABAC (or ABAC + RBAC) supports dynamic, large-scale, cloud-first enterprises
Adopting the right model—or combining them—is essential for minimizing risks, ensuring compliance, and improving operational efficiency.
Benefits of Implementing User Access Control
Whether your organization relies on Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), or a hybrid approach, the benefits of a strong access control framework are substantial and measurable.
- Minimizes Risk of Unauthorized Access
By granting access based strictly on roles, attributes, or rules, UAC restricts sensitive systems and data to only those who need it. This reduces the chances of insider threats or accidental data exposure, especially in complex, federated identity & access management environments. - Strengthens IAM Risk Management
UAC allows for granular tracking of user privileges, enabling security teams to detect anomalies and respond proactively. Combined with tools like Scim API and real-time identity governance and administration solutions, organizations can prevent access misuse and maintain a resilient IAM framework. - Simplifies Compliance and Audits
Whether you’re aligning with GDPR, HIPAA, or SOX, UAC helps demonstrate compliance through clear access logs and policy enforcement. Features like automated User Access Review streamline audit preparation and support identity access management certifications, saving time and reducing manual errors. - Enhances Operational Efficiency
Through Role-Based Access Control and automation, onboarding and offboarding become faster and more secure. Predefined access templates eliminate repetitive permissioning tasks, ensuring users have the exact access they need—nothing more, nothing less. - Enables Scalable Identity Governance
As businesses scale, so do the complexity of their access needs. A mature UAC strategy supports centralized governance across departments, cloud platforms, and remote teams. With integrated IGA security tools, enterprises can manage permissions dynamically while retaining full visibility and control.
When executed strategically, UAC becomes more than a safeguard—it’s a growth enabler that supports business agility without compromising security.
In the next section, we’ll explore how to build an effective UAC policy, including key components, best practices, and real-world considerations.
Common Challenges in UAC Implementation
While the advantages of User Access Control are undeniable, organizations often encounter a series of operational and technical hurdles when implementing or scaling UAC systems. Recognizing these challenges early can help mitigate security gaps and inefficiencies.
- Managing a Growing Number of Users, Devices, and Identities
With hybrid-cloud environments and remote workforces becoming the norm, identity sprawl is a real concern. Without robust Identity Governance and Administration (IGA) processes in place, keeping up with the volume of users—employees, contractors, and third parties—becomes increasingly complex. - Over-Provisioning and Privilege Creep
As roles evolve, users often retain outdated access permissions. Over time, this privilege accumulation can create serious IAM risk management concerns. Regular User Access Reviews and automated deprovisioning workflows can help reduce the threat of excessive permissions. - Limited Visibility into Access Activities
Without centralized audit logging and monitoring, it’s difficult to track who accessed what, when, and from where. This lack of transparency can compromise both customer identity and access management and regulatory compliance readiness. - Securing Remote and Third-Party Access
Bring Your Own Device (BYOD) policies and vendor access further complicate UAC enforcement. Integrating access control systems with federated identity & access management platforms can help maintain consistent enforcement across varied user types. - Delays in Role Changes and Offboarding
Manual user provisioning/deprovisioning is prone to delays and errors. A lack of integration between HR systems, identity providers, and access governance tools leads to inefficiencies and increases the attack surface. - Compatibility with Legacy Systems
Older infrastructure may lack the APIs or interoperability required for modern identity access management certifications or Scim API integration. This complicates the rollout of unified access control measures across the enterprise.
To successfully overcome these hurdles, organizations must prioritize automation, policy standardization, and continuous visibility into their UAC ecosystem.
Top 12 User Access Control Best Practices (2025 Edition)
The following UAC strategies—tailored for 2025—can help your organization strengthen its Identity Access Management (IAM) framework while staying compliant and future-ready.
- Adopt Zero Trust Principles
Assume no one is trustworthy by default—inside or outside the network. Every access request must be verified, validated, and continuously monitored. - Enforce Least Privilege Access
Grant users only the access they need to perform their specific tasks. Use Role-Based Access Control (RBAC) to enforce this principle efficiently. - Combine RBAC + ABAC Models
Merging RBAC with Attribute-Based Access Control (ABAC) allows for both structure and flexibility—ideal for dynamic teams and hybrid environments. - Automate User Provisioning and Deprovisioning
Automate onboarding, role changes, and offboarding processes through tools supporting Scim API to minimize human error and reduce privilege creep. - Use Multi-Factor Authentication (MFA)
Strengthen authentication by requiring multiple factors—such as passwords, biometrics, or one-time tokens—for access. - Implement Just-in-Time (JIT) Access
Limit access duration for sensitive operations by enabling temporary permissions that expire automatically after task completion. - Regularly Audit and Review Permissions
Schedule periodic User Access Reviews to identify and revoke outdated or unused permissions. This is essential for IAM risk management and compliance. - Set Role-Based Access Expiration Dates
Prevent indefinite access by assigning expiration timelines to temporary roles or project-specific access privileges. - Use Behavior-Based Anomaly Detection
Leverage AI-powered tools to monitor access patterns and flag deviations that could signal compromised credentials or insider threats. - Educate Employees on UAC Hygiene
Regular training helps users understand the importance of secure access practices—an often overlooked part of customer identity and access management. - Integrate with Business-Critical Applications
Ensure your UAC policies extend to all essential systems, including CRM, ERP, and cloud-based platforms, using identity governance and administration solutions. - Log Everything and Maintain a Change History
Maintain detailed logs of access requests, approvals, and changes. These logs support governance efforts, audits, and incident investigations.
Incorporating these practices ensures your UAC strategy remains adaptable, secure, and aligned with enterprise Identity Governance and Administration (IGA) goals.
Hybrid Access Control: Why RBAC + ABAC Is the Future
Role-Based Access Control (RBAC) has been the go-to model for managing user access in many organizations. However, in today’s rapidly changing work environments—especially with remote and hybrid teams—RBAC alone doesn’t always meet the needs of modern organizations. That’s why combining RBAC with Attribute-Based Access Control (ABAC) is becoming increasingly important.
Why RBAC Alone Doesn’t Always Work
RBAC assigns access based on roles or job titles, which works well in many traditional setups. But today’s workforce is more dynamic, with remote employees, contractors, and multiple access points. RBAC doesn’t consider factors like location, device type, or the time of access, which makes it less flexible in complex scenarios.
How ABAC Adds Flexibility
Attribute-Based Access Control (ABAC) solves this by allowing access decisions based on specific attributes such as the user’s department, their device, or even the time of day. This fine-grained approach ensures that access is granted based on a broader set of conditions.
For example, an employee might have access to a sensitive document, but only if they’re logging in from an approved location or device. ABAC gives organizations the flexibility to manage access in a more context-aware way.
How the Hybrid Model Works
By combining RBAC and ABAC, organizations get the best of both worlds. RBAC provides structure, ensuring users get the right access based on their roles, while ABAC adds the flexibility to refine those decisions based on context like time, location, or device.
For example, in industries like finance or healthcare, employees may need specific access to resources only under certain conditions. This hybrid approach makes it easier to manage complex access needs securely.
Tools for the Hybrid Approach
Many modern IAM tools now support hybrid RBAC + ABAC models. These tools enable organizations to apply both structured role-based access and context-aware controls, ensuring better security and flexibility.
As access control needs continue to evolve, the RBAC + ABAC combination offers a more scalable and adaptable solution.
User Access Control in the Cloud and SaaS Era
With more businesses moving to the cloud and using SaaS, managing user access has become more complicated. Unlike traditional systems, cloud environments allow users to access data from anywhere, making it harder to control who can access what.
Challenges in Cloud and SaaS
In the cloud, users can access data from multiple devices and locations. This makes it tough to track and control who has access. Cloud services are often provided by third parties, so it’s important to have strong controls in place to manage access securely.
IAM for Cloud Businesses
For cloud-based businesses, Identity and Access Management (IAM) is essential. It helps companies control who can access data across different cloud platforms like AWS, Azure, and Google Cloud. IAM tools also include security features like Single Sign-On (SSO) and Multi-Factor Authentication (MFA).
Managing Third-Party Access
In cloud environments, businesses often need to give external vendors or contractors access to certain data. Strong UAC policies help ensure they only see what they need, reducing security risks. Federated Identity Management (FIM) allows external users to use their own credentials to access the system securely.
Federated vs. Centralized Access
Two common ways to manage user access in the cloud are Federated Identity and Centralized Access. Federated Identity allows users to log in once and access multiple services. Centralized Access stores all user credentials in one place. Both have their benefits, and the right choice depends on the business needs.
As cloud technology grows, effective User Access Control remains crucial to keep data safe and meet security standards.
Compliance and Governance Considerations
User Access Control (UAC) isn’t just about keeping data secure—it also helps businesses meet important regulations. Many industries have strict rules about how data should be accessed and protected. These rules ensure that companies protect sensitive information and avoid costly fines.
How UAC Helps with Compliance
A well-managed UAC system is essential for meeting regulatory requirements like GDPR, HIPAA, and SOX. These regulations require companies to monitor and control who can access sensitive data. UAC helps by setting policies that ensure only authorized users have access to certain information, reducing the risk of data breaches.
Auditing and Reporting
To stay compliant, businesses must also be able to track who accessed what data and when. Auditing and reporting features in UAC systems allow organizations to keep a log of user activity, which is often required for compliance. It’s also important to know how long to store these logs to meet legal requirements.
Industry-Specific UAC Requirements
Different industries have different needs. For example, healthcare organizations need to follow HIPAA, while financial institutions must comply with SOX. Each of these regulations has specific requirements for how data should be accessed and protected, and UAC helps ensure these standards are met.
Choosing the Right User Access Control Solution
Choosing the right User Access Control (UAC) solution is critical to ensuring your business’s data remains secure and compliant. With so many options available, it’s important to pick a solution that fits your company’s needs.
Key Features to Look For
When evaluating UAC solutions, consider these key features:
- Scalability: The solution should grow with your business, handling an increasing number of users and devices.
- Integration: It should easily integrate with your existing IT systems, including your Identity and Access Management (IAM) tools.
- Security: Look for features like Multi-Factor Authentication (MFA), encryption, and secure access controls.
- Compliance Support: Ensure the solution helps you meet regulatory requirements like GDPR or HIPAA.
Questions to Ask Vendors
Before making a decision, ask potential vendors these important questions:
- Does the solution support role-based and attribute-based access controls (RBAC & ABAC)?
- How does the solution handle user provisioning and deprovisioning?
- What kind of reporting and auditing features does it offer?
- Can it integrate with cloud services and third-party applications?
Comparing Top UAC Solutions
There are several UAC solutions available, each with its strengths. When comparing, focus on how well they meet your business’s specific needs for access control, security, and compliance.
Checklist for Evaluating a UAC Product
- Does it offer robust authentication methods (MFA, biometrics)?
- Is it easy to manage user roles and permissions?
- Does it provide detailed audit logs?
- How does it handle third-party or remote user access?
By carefully evaluating these factors, you can select a UAC solution that keeps your business secure while supporting your growth and compliance needs.
Final Thoughts
User Access Control (UAC) is a vital aspect of any organization’s cybersecurity strategy. In today’s rapidly evolving digital landscape, where remote work and third-party access are commonplace, UAC ensures that only authorized users can access sensitive data and systems. This helps prevent unauthorized access, data breaches, and compliance issues.
As businesses continue to grow, so does the complexity of managing user access. It’s essential to adopt dynamic and scalable UAC solutions that can evolve with your organization. Automating access control processes, implementing robust authentication methods, and regularly reviewing access permissions are key to maintaining security and efficiency.
To stay ahead of the curve, businesses should continuously assess their UAC systems to ensure they are well-equipped to handle new security threats and regulatory changes. By proactively managing access, organizations can minimize risks, maintain compliance, and protect their most valuable data.


