Identity Governance and Service Accounts
Identity Governance and Service Accounts

Written By : Abhi Kumar
WHAT ARE SERVICE ACCOUNTS?
Service accounts are a special kind of non-human account that are often used with the intention of automating a wide variety of different system functions. They have their own unique set of permissions and privileges. Service accounts, which are unique to a certain service or application, are analogous to user accounts, which are held by actual persons. Service accounts can be privileged accounts that are utilized by mission-critical applications or services to interact with their respective operating systems, as well as to execute batch files, scheduled tasks, and applications that are hosted across a variety of databases, file systems, and devices.
CHALLENGES IN MANAGING SERVICE ACCOUNTS
In almost all cases, IT Operations and support staff do not have a complete list of all services running under the context of service accounts. Because of this, threat actors that want to migrate laterally across the network will often target service accounts as their primary point of entry. It is critical for the organization to have a solid understanding of how service accounts function as well as some best practices for ensuring that service accounts are managed proactively and are kept with the fewest possible rights. As a result of digital transformation and widespread usage of cloud computing, service account management is no longer a one-time effort but rather one that needs ongoing access reviews and remediation.
The key challenge in managing service accounts is lack of centralized repository. User accounts are managed in a HR application, and this provides enterprise teams with a single source of truth and an up-to-date, authoritative status that enables automated authorization changes in response to lifecycle events. These changes can include the termination of privileges when they are no longer required. However, service accounts do not have a single system of record as these are a function of the applications, many of which are under the preview of development teams. The absence of a single source of record for service accounts is a stumbling block for efficient identity governance of service accounts. In addition to this, as the identity of the service account owner is usually unknown it is impossible to enforce service account management and lifecycle changes upon account owner changes.
BEST WAYS TO HANDLE SERVICE ACCOUNTS
Adequate management of service accounts requires strong controls and continuous reviews that balance organizations’ need for speed and compliance. Numerous businesses utilize the SecurEnds CEM solution and based on our observations, we offer the following suggestions- while these are our top picks, this list isn’t exhaustive:
1) Discover all service accounts and categorize them in order of importance, as well as identify the relevant account owners and custodians. After identifying the accounts, re-certification of those accounts should be carried out to determine whether or not there is a real business requirement for each account. This should be done to determine whether or not each account has a valid business need that demands its use. The objective is to minimize the total number of service accounts to must haves in the environment.
2) Every company should make it a priority to implement all service accounts in a way that is in line with the principle of granting least privileges to each account. In addition to this, it is required to ensure stringent credential requirements for all the organization’s applications and systems, regardless of the account type, and it must make certain that this policy is strictly enforced. Examples of stringent credential requirements include not storing credentials in text files or scripts. In addition, organizations must change or expire passwords at regular intervals; enforce minimum complexity criteria, utilize and multifactor authentication.
3) Conduct continuous attestation or user access reviews of service accounts to know what permissions service accounts have, and if any permissions infringe the established policies or Principles of Least Privileges.
SecurEnds CEM product enables out-of-the-box compliance and is now being used by several different companies to manage, control, and audit service accounts. You’ll save time thanks to our many data ingestion methods and logic that guarantees that none of your service accounts will go unmanaged. After accounts are profiled, our system enables you to appoint an owner to the service account. The owners will next ensure that the service accounts have the fewest possible rights assigned to them, and they will continue to monitor the use of each service account.
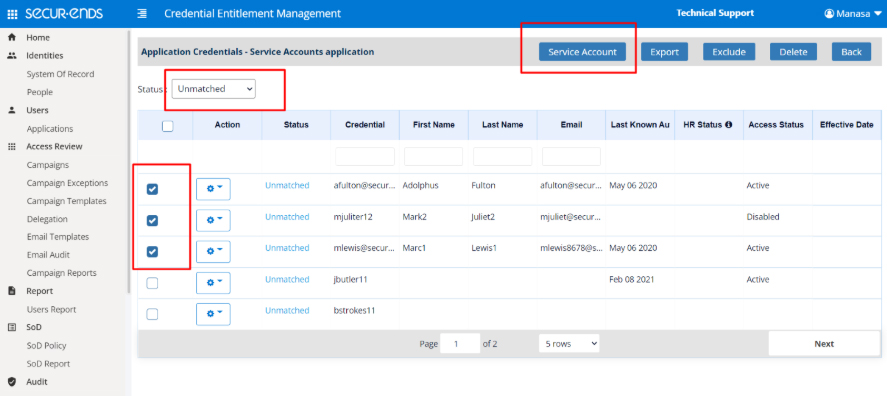
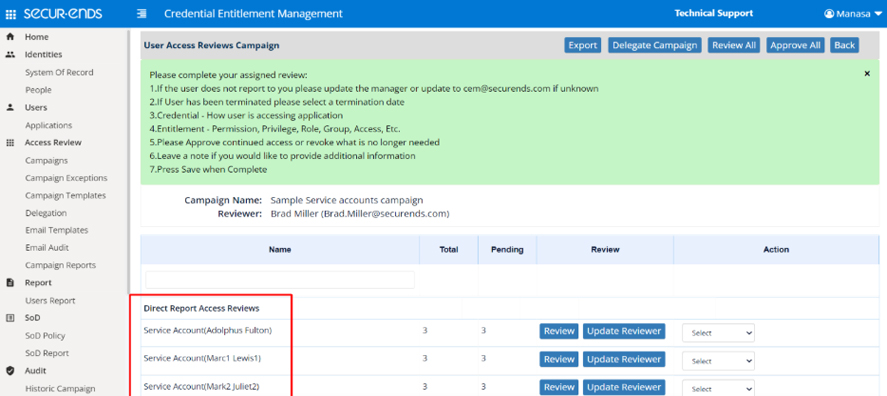
Companies seldom have the time or personnel to undertake a comprehensive assessment of service accounts across all IT assets because of the growing complexity of IT systems and infrastructure. Using SecurEnds CEM product, companies can considerably decrease the access footprint of service accounts, remove underutilized service accounts, remediate overprovisioned service accounts, and ensure companies are ready for security and compliance audits.
Schedule a demo to see how SecurEnds service account governance solution is CISO’s leading choice.