Employee Self Request: Simplifying Access Governance in 2025
Employee Self Request: Simplifying Access Governance in 2025
Introduction
Imagine joining a new company, eager to contribute, only to spend your first few days waiting on access—email, project tools, data folders—all behind layers of manual approvals. It’s a common scenario in enterprises still relying on outdated access request processes.
That’s changing fast.
As organizations embrace digital transformation and hybrid work at scale, the way employees request access to resources is undergoing a shift. Enter the Employee Self Request—a streamlined, policy-driven method that empowers individuals to initiate access requests on their own, within the guardrails of governance.
Part of the broader Identity Governance and Administration (IGA) ecosystem, Employee Self Request simplifies the intersection of security, compliance, and productivity. Instead of routing every access need through IT or team managers, employees can request what they need—when they need it—while organizations retain full control through approvals, tracking, and review mechanisms.
In this blog, we’ll explore what Employee Self Request means in the context of modern Identity Access Management (IAM), how it improves operational agility, and how SecurEnds enables secure, auditable self-service access in a way that’s scalable for enterprises.
What Is an Employee Self Request?
Building on the need for faster, secure access, Employee Self Request is the mechanism that enables users to initiate their own access requests within a governed framework. Unlike traditional models where access is provisioned top-down—through IT admins or reporting managers—this approach empowers employees to raise access needs directly, with pre-configured policies ensuring security and compliance.
Think of it as the modern self-checkout in enterprise systems—efficient, intuitive, and controlled.
An Employee Self Request can apply to a range of access scenarios:
- A new hire requesting access to team-specific applications during Employee Onboarding
- A marketing analyst seeking temporary access to a data platform for a campaign
- A developer moving into a new role and needing updated permissions
Unlike Contractor Self Requests, which usually require more restrictive, time-bound access, employee-driven requests are often recurring and tied to evolving internal responsibilities. The key difference lies in how governance frameworks handle each request type—especially in terms of risk and scope, which we’ll explore later.
By aligning these self-initiated access needs with Identity Access Management (IAM) and IGA policies, organizations not only reduce IT friction but also build a culture of accountability—where access is both empowered and traceable.
How Does an Employee Self Request System Work?
Once the concept of Employee Self Request is embedded into your Identity Governance and Administration (IGA) framework, the next step is ensuring it functions with precision and oversight. At its core, the process follows a structured path—defined by logic, enforced by policy, and streamlined through automation.
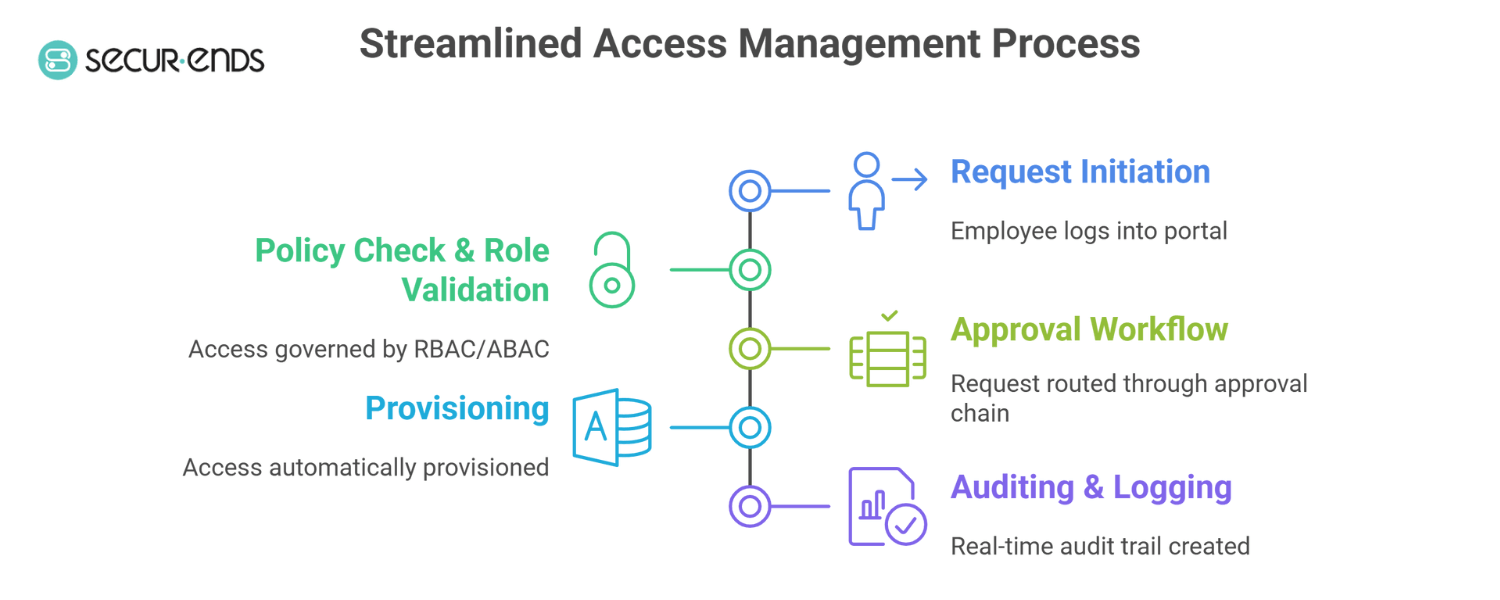
Here’s how a typical flow unfolds:
- Request Initiation – The employee logs into a centralized portal—often integrated with an Identity Access Management (IAM) tool like SecurEnds—and selects the resource, system, or application they need access to.
- Policy Check & Role Validation – Behind the scenes, access is governed by Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) models. These frameworks ensure that only users with the right context (department, role, location, etc.) can proceed.
- Approval Workflow – The request is routed through a predefined approval chain. This could be a line manager, application owner, or a designated reviewer. For high-sensitivity assets, multi-level or risk-based approvals may apply.
- Provisioning – Once approved, access is automatically provisioned across integrated systems—be it Active Directory, SaaS platforms, or internal applications.
- Auditing & Logging – Every step, from request to approval to provisioning, is logged in real time. This audit trail feeds directly into User Access Reviews, enabling post-access validation and governance.
What sets modern systems apart is their ability to integrate seamlessly with platforms like SecurEnds, which offer a no-code interface to configure workflows, trigger compliance alerts, and ensure that Self Requests—whether for full-time employees or short-term contractors—are never outside the visibility of your IGA strategy.
This operational clarity paves the way for tangible benefits, which we’ll cover next.
Benefits of Enabling Employee Self Request
Empowering employees to request access through a self-service model isn’t just a convenience—it’s a strategic move that directly impacts operational efficiency, compliance posture, and workforce experience. By placing access decisions closer to the user while maintaining governance oversight, organizations unlock several key advantages.
1. Accelerated Onboarding and Productivity
In traditional access models, delays caused by email trails, manual approvals, or IT bottlenecks can slow down employee onboarding. With Employee Self Request, new hires can quickly initiate access requests aligned with their roles, reducing time-to-productivity without compromising security. When backed by clear policies and automated provisioning, this process becomes both agile and accountable.
2. Reduced IT and Helpdesk Load
IT teams are often burdened with routine access requests that consume time but add little strategic value. Self-service request systems significantly cut down these dependencies, allowing IT staff to focus on more critical tasks. This also minimizes turnaround time, leading to improved user satisfaction.
3. Enhanced Compliance and Audit Readiness
Because every Self Request is tracked, approved, and provisioned through auditable workflows, organizations gain a transparent trail of access decisions. This traceability supports Identity Governance and Administration (IGA) requirements and streamlines internal audits or external assessments. When paired with timely User Access Reviews, the system reinforces access hygiene across the enterprise.
4. Support for Hybrid and Remote Workforces
As workforces become more distributed, centralized IT control becomes increasingly difficult. Employee Self Request ensures that remote and hybrid employees can still gain timely, policy-based access to the tools they need—without risking unauthorized exposure or inconsistent provisioning.
By rethinking access through the lens of usability and governance, organizations position themselves for greater agility—without losing sight of compliance and control.
Common Use Cases
While the advantages of Employee Self Request are clear, the real value emerges in how it adapts to diverse operational scenarios. From day-one access for new hires to short-term provisioning for project teams, self-service access requests can be tailored to fit a wide range of identity and access needs.
Application and Data Access
Employees often need access to applications or data repositories that aren’t part of their default provisioning. With a Self Request mechanism in place, they can submit requests for these resources directly—triggering workflows based on role, department, or project scope. This ensures that access is both appropriate and governed, without manual back-and-forth between departments.
New Hire Onboarding
During employee onboarding, timely access to collaboration tools, communication platforms, and job-specific applications is critical. Self-service models enable new employees to request access as soon as they’re provisioned into the HR system—accelerating ramp-up while maintaining alignment with IAM and IGA policies.
Access Updates for Internal Role Changes
As employees move between roles, departments, or projects, their access needs evolve. Rather than relying on IT or managers to initiate these changes, a Access Request process allows users to request updates based on their new responsibilities—triggering de-provisioning of outdated permissions and provisioning of relevant ones. This supports dynamic access governance and helps avoid permission sprawl.
Temporary Access for Project Teams
Cross-functional project teams often require short-term access to systems they don’t typically use. With self-service access capabilities, these users can request time-bound access—ensuring they’re enabled to contribute without opening up long-term exposure. This aligns with Just in Time Access Request principles and supports audit-ready provisioning practices.
From day-to-day operations to dynamic workforce changes, Employee Self Request simplifies how access is granted—making it faster, cleaner, and more accountable.
Risks & Challenges
While Employee Self Request offers significant benefits, it also introduces specific risks that organizations must address to maintain strong access governance.
Risk of Access Creep
One common challenge is access creep—the gradual accumulation of permissions beyond what a user needs. Without rigorous controls, Self Requests can unintentionally lead to overprovisioning, increasing the attack surface and compliance risks. This highlights the need for clearly defined roles and automated policy enforcement.
Inconsistent Approval Workflows
Without standardized workflows, approval processes may become inconsistent or bypassed altogether, weakening governance. Organizations must ensure that every access request follows a clearly defined approval path aligned with business policies, reducing the chance of unauthorized or inappropriate access.
Lack of Visibility and Audit Trails
A critical aspect of Identity Governance and Administration (IGA) is the ability to track who requested access, who approved it, and when it was granted or revoked. Without comprehensive logging and reporting, organizations face gaps in audit readiness and compliance, which can be costly during regulatory reviews.
How SecurEnds Addresses These Risks
SecurEnds mitigates these challenges through automation, built-in User Access Reviews (UARs), and certification workflows. By enforcing role-based policies and providing continuous monitoring, SecurEnds ensures that self-service requests remain compliant and that access privileges are regularly validated—strengthening both security and governance.
Best Practices for Implementing Self-Service Access Requests
Building a robust Employee Self Request system requires more than just enabling users to submit access requests—it demands a thoughtful approach that balances ease of use with strong governance.
Define Roles and Policies Clearly
Start by establishing clear role definitions and access policies. Whether using Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC), defining who can request what access—and under what conditions—is essential to prevent permission sprawl and ensure compliance.
Automate Workflows with Multi-Level Approvals
Automation is key to managing volume without sacrificing oversight. Implement multi-level approval workflows that involve managers, security teams, or compliance officers depending on the sensitivity of the request. This ensures that all access requests receive appropriate scrutiny before provisioning.
Implement Periodic Reviews and Certifications
Access rights should never be set and forgotten. Schedule regular User Access Reviews (UARs) to validate active permissions and certify that access remains necessary. This is crucial to maintaining the principle of least privilege and reducing risks from orphaned or excessive rights.
Monitor and Log All Self-Service Activity
Comprehensive logging and real-time monitoring provide visibility into who is requesting and approving access, helping detect anomalies or potential abuse early. These logs also serve as a vital part of audit evidence during compliance assessments.
By combining these best practices, organizations can empower employees with the flexibility of Self Request while maintaining a secure and compliant access governance framework.
How SecurEnds Supports Employee Self Request
Implementing an effective Employee Self Request system requires a platform that blends flexibility, automation, and compliance—all of which are central to SecurEnds’ Identity Governance and Administration capabilities.
No-Code Workflow Builder
SecurEnds simplifies complex access request processes with its no-code workflow builder, enabling organizations to design tailored approval flows without heavy IT involvement. This empowers faster deployment and easy adjustments as business needs evolve.
Seamless Integration
The platform integrates smoothly with existing HR Management Systems (HRMS), Active Directory (AD), and various SaaS or cloud applications. This ensures that employee lifecycle events—such as Employee Onboarding and Employee Off-Boarding—automatically trigger appropriate access changes, minimizing manual effort and errors.
Real-Time Monitoring and Reporting
SecurEnds provides continuous visibility into access requests and approvals through real-time dashboards and comprehensive audit logs. These features support compliance readiness by maintaining detailed records for all Self Requests and provisioning actions.
Built-In Access Reviews and Compliance-Ready Audit Logs
Beyond access provisioning, SecurEnds facilitates ongoing User Access Reviews and generates compliance-ready audit trails. These capabilities help organizations uphold stringent access governance standards and prepare confidently for audits.
Together, these features make SecurEnds a powerful partner in simplifying and securing the Employee Self Request process.
How Contractor Self Requests Differ from Employee Self Requests
While Employee Self Request streamlines access for internal staff, managing access for contractors introduces unique challenges that demand a different approach.
Short-Term, Limited-Scope Access
Contractors typically require access for defined periods and specific projects. Their permissions are often more restrictive, focusing on the minimum necessary resources to complete their work.
Elevated Risk from External Identities
Because contractors are external to the organization’s core workforce, they present a higher risk profile. Unmanaged or excessive contractor access can lead to security gaps, data exposure, and compliance violations.
Differentiated Policies and Reviews
SecurEnds addresses these challenges by enabling organizations to implement specialized policies for Contractor Self Requests. These policies enforce tighter controls, such as shorter access durations, enhanced approval requirements, and more frequent User Access Reviews tailored for third-party users.
By distinguishing contractor access management from employee access, organizations can reduce risk while maintaining operational efficiency.
When to Use Emergency Access Requests Instead
Despite the efficiencies offered by Employee Self Request and Contractor Self Request processes, there are times when urgent access is critical—situations where standard approval workflows may be too slow.
This is where Emergency Access Requests or Just-in-Time (JIT) Access Requests come into play. Designed for exceptional scenarios such as critical incident responses, system outages, or security breaches, these requests grant temporary, elevated permissions rapidly while maintaining strict oversight.
SecurEnds supports this need by enabling automated, auditable emergency access workflows. Each request is time-bound, logged comprehensively, and subject to post-event reviews, ensuring compliance without compromising response speed.
In essence, while Employee and Contractor Self Requests cover routine access needs, Emergency Access Requests ensure resilience and security during high-pressure, unplanned events.
Future of Employee Self Request in IAM
As organizations evolve, so do the demands on Identity Access Management (IAM) and Identity Governance and Administration (IGA) systems. The future of Employee Self Request is being shaped by emerging technologies and shifting security paradigms.
AI-Driven Access Recommendations
Artificial intelligence is increasingly being integrated into access governance, providing intelligent recommendations based on user behavior, role changes, and risk factors. This helps ensure that access requests are not only faster but also more accurate and aligned with security policies.
Adaptive Access Controls
Adaptive access adjusts permissions dynamically based on contextual factors such as location, device, and time of request. This level of granularity enhances security while preserving user productivity, especially in hybrid and remote work environments.
Integration with Zero Trust Models
The shift toward zero trust security frameworks emphasizes strict verification for every access request, regardless of origin. Future self-service access systems will seamlessly integrate with zero trust principles, enforcing continuous authentication and least privilege access.
By embracing these advancements, organizations can continue to simplify Employee Self Request processes while strengthening overall access governance.
Access management is evolving, and Employee Self Request is at the heart of that transformation. It’s more than just a process — it’s a critical enabler that empowers employees, reduces delays, and strengthens security all at once. In 2025, organizations can no longer afford cumbersome, manual access workflows that slow down productivity and increase risk.
With SecurEnds, you get a solution that not only simplifies access requests but also embeds compliance and governance at every step. From seamless automation to comprehensive User Access Reviews, SecurEnds helps you strike the perfect balance between user empowerment and security assurance.
If your goal is to streamline access governance while staying audit-ready and secure, it’s time to rethink your approach.
Experience how SecurEnds can revolutionize your employee access management — request a demo today and take the first step toward smarter, safer Identity Governance and Administration.


