Why Employee Onboarding Is Now a Security Issue
Why Employee Onboarding Is Now a Security Issue

Intro: Employee Onboarding is Now a Security Event
Employee onboarding was once a back-office function—create an email ID, hand out credentials, and move on. But in today’s digital-first enterprises, employee onboarding has become a security-critical event. Every new hire, whether on-site or remote, is a new access vector—one that must be tightly managed from day one to avoid data exposure, compliance violations, or productivity delays.
Modern onboarding is no longer just about provisioning access. It’s about provisioning the right access, at the right time, with built-in accountability. Delayed access slows down teams. Over-provisioning leads to privilege creep. And inconsistent controls open the door to audit gaps and insider threats.
That’s why secure employee onboarding is now a board-level concern—and why Identity Access Management (IAM) and Identity Governance and Administration (IGA) tools are at the heart of this transformation. From automating provisioning flows to enabling Just in Time Access Request capabilities, the IAM onboarding process is now essential to ensure compliance, reduce risks, and set employees up for secure productivity from day one.
The Modern Onboarding Problem
Even today, many companies handle onboarding with outdated, manual methods. It’s a process filled with delays, miscommunication, and unnecessary risks—especially when it comes to access provisioning.
The biggest challenge? Manual provisioning. IT teams often receive self request/access requests through spreadsheets or scattered emails. This creates room for human error, slows down response times, and makes it harder to ensure consistency.
Another major issue is over-provisioning. Without clear role definitions or guardrails, new employees often get more access than they need. Over time, this leads to privilege creep, where access accumulates beyond what’s required—posing serious compliance and security risks.
There’s also a lack of alignment. HR, IT, and department managers frequently operate in silos, making it difficult to coordinate onboarding effectively. As a result, key apps and tools may not be ready by day one.
The outcome? New hires face delays, lose productivity, and may feel disconnected from the start. According to Forrester, 58% of organizations still rely on spreadsheets for onboarding—highlighting how widespread these gaps remain.
Inconsistent access doesn’t just affect performance. It creates vulnerabilities, increases audit concerns, and leaves businesses exposed to growing onboarding IT risks. The contrast between manual vs automated onboarding has never been clearer—and automation is now the smarter, safer choice.
Why IAM & IGA Are Critical in Onboarding
To solve modern onboarding challenges, companies need more than checklists and manual handoffs—they need scalable, policy-driven systems. This is where Identity Access Management (IAM) and Identity Governance and Administration (IGA) come in.
IAM ensures the right people get the right access at the right time. Whether an employee is working remotely, changing roles, or accessing sensitive systems, role-based access and location-aware policies allow organizations to enforce precision and consistency from day one.
But access isn’t just about provisioning—it’s also about governance. That’s where IGA strengthens the process. It enables organizations to define access policies, implement review cycles, and maintain audit trails—ensuring that access aligns with compliance mandates like SOX, HIPAA, and GDPR.
With a modern solution like SecurEnds, onboarding begins the moment HR systems like Workday or BambooHR flag a new hire. This trigger initiates an automated flow that:
- Maps access based on predefined roles
- Assigns entitlements without guesswork
- Auto-provisions accounts, licenses, and group memberships across systems
This reduces the burden on IT, eliminates delays, and dramatically lowers the risk of overprovisioning or missed entitlements. It also allows flexibility for Self Request / Access Request workflows when special access is needed—making the process both secure and scalable.
By integrating User access reviews and enabling lifecycle automation, the IAM onboarding process ensures that no step is missed, and no system is left open to unnecessary risk. It transforms onboarding into a structured, compliant, and efficient process—without compromising speed or control.
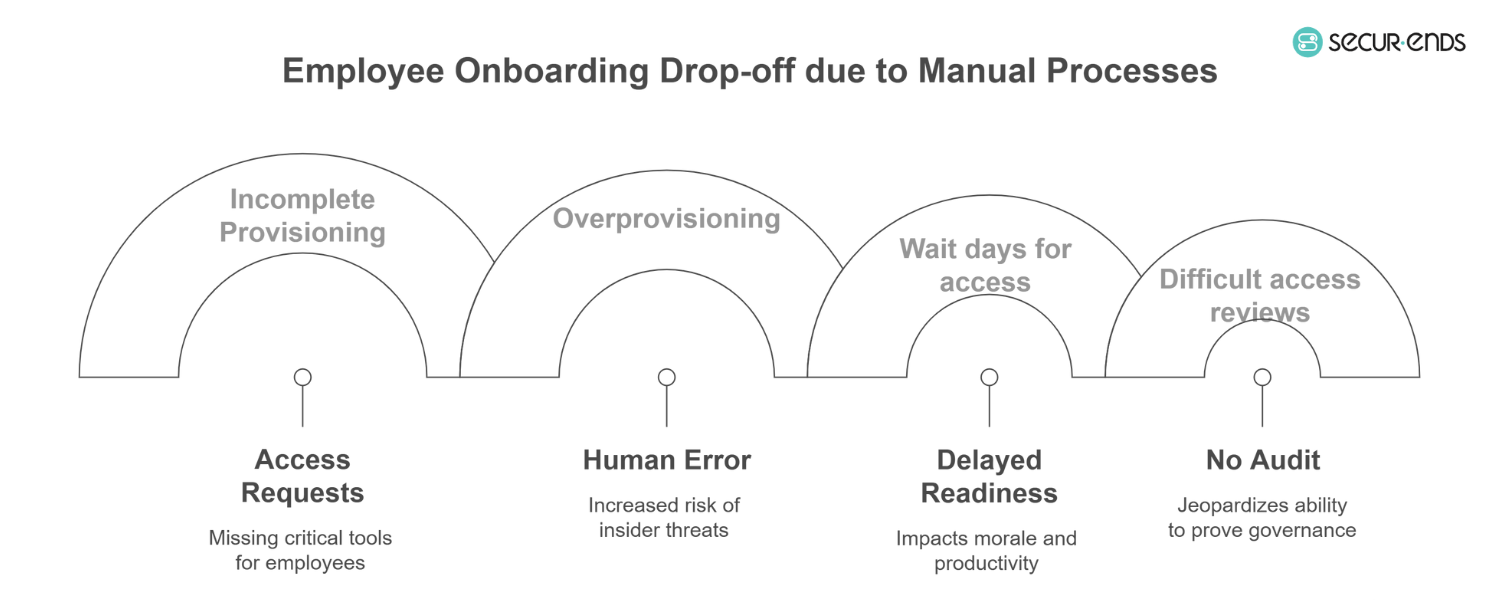
The Hidden Risks of Manual Onboarding (and Why Most Orgs Struggle)
Manual onboarding may appear manageable at first—but at scale, it quickly becomes a source of friction, inconsistency, and risk. Without automation and governance, organizations face gaps that impact everything from day-one readiness to long-term compliance.
Fragmented Access Requests
In many setups, access requests are passed through informal channels—emails, spreadsheets, or verbal instructions. This leads to incomplete provisioning, delays, or worse, missing critical tools that employees need to begin working. The absence of centralized visibility makes it difficult to track what’s been granted, when, and why.
Human Error and Overprovisioning
When roles and entitlements are assigned manually, mistakes are inevitable. Employees often receive more access than necessary, leading to privilege creep and increased risk of insider threats. Without the guardrails provided by Identity Governance and Administration (IGA), such errors accumulate silently over time.
Delayed Day-One Readiness
Lack of automation means IT must manually provision each app and system—often while juggling other priorities. New hires may wait days before gaining access to what they need, impacting both morale and productivity. It’s the opposite of what a secure employee onboarding experience should look like.
No Audit Trail
Without a unified system, there’s no consistent record of approvals or changes. This makes User access reviews difficult to manage and creates vulnerabilities during compliance audits. A missing audit trail doesn’t just affect security—it jeopardizes your ability to prove governance.
When organizations rely on manual onboarding, they’re left exposed. The absence of integrated Identity Access Management (IAM), Self Request / Access Request, and automated reviews creates risks that multiply with every hire.
How SecurEnds Automates the Onboarding Workflow
Fixing onboarding challenges isn’t just about speeding up provisioning—it’s about making it consistent, compliant, and secure at scale. That’s exactly where SecurEnds comes in.
The workflow begins the moment your HR system (like Workday or BambooHR) flags a new hire. SecurEnds picks up this event through a secure API integration, pulling in key employee details automatically. From there, everything moves through a streamlined, rules-based engine.
Here’s how the flow works:
- Assigns predefined roles based on department, function, and seniority
- Maps those roles to specific access entitlements
- Auto-provisions accounts, licenses, and permissions across multiple systems
Whether it’s Active Directory / Azure AD, SaaS platforms like Salesforce, Slack, or Asana, or DevOps tools like AWS, GitHub, or Jira, SecurEnds ensures that the right access is in place—on time and fully governed.
Need exceptions? SecurEnds supports Employee Self Request, Contractor Self Request, Just in Time Access Request, and even Emergency Access Request flows. These are routed through customizable approval workflows, giving IT full control without bottlenecks.
For IT teams, this means fewer tickets, less guesswork, and faster onboarding cycles. For security teams, it means confidence in least privilege enforcement and complete traceability.
Each onboarding event is automatically logged, creating a compliance-ready onboarding log with immutable records. This simplifies audits, supports policies, and enables real-time User access reviews.
The platform also integrates with systems like ServiceNow or Jira, so nothing falls outside your existing IT ecosystem. Every access request, approval, and provisioning step is fully trackable.
By automating the onboarding workflow, SecurEnds makes secure employee onboarding not just possible, but scalable, auditable, and future-proof.
From hiring to exit, access risks never stop. Visit our Employee Lifecycle Access Management hub to learn how SecurEnds streamlines and secures every stage of the employee journey.
Onboarding Access Checklist for IT Teams
Even with automation in place, having a clear access checklist ensures that every new hire starts strong—and stays secure. Whether you’re onboarding full-time employees or contractors, the following components should be standardized across your IT playbook.
Provision Access to:
- Active Directory / Azure
- Corporate email and calendar
- VPN and internal network resources
- Core SaaS tools (e.g., Slack, Salesforce, Zoom)
- Department or team-specific apps
- Shared folders, drives, and collaboration platforms
Enforce Security Readiness:
- Multi-Factor Authentication (MFA) setup
- Password manager enrollment
- Company device policy acknowledgment
- Endpoint protection configuration
Log and Track:
- Entitlement approval workflows
- Initial login activity and time stamps
- Scheduled User access reviews and future recertification dates
By embedding this checklist into your IT onboarding process, you reduce the chances of missed access or inconsistent provisioning. SecurEnds helps operationalize this by tying each step to automated workflows—making checklists not just best practices, but part of a fully auditable system.
For organizations scaling across regions or teams, this checklist becomes even more critical. It helps enforce uniform policies, simplify exception handling through Employee Self Request or Access Request, and maintain control over every access touchpoint.
A robust, automated checklist ensures that secure employee onboarding isn’t left to chance—it’s built into every workflow, every time.
Compliance & Audit Benefits
In heavily regulated industries, onboarding isn’t just an operational task—it’s a compliance obligation. Whether governed by SOX, HIPAA, or GDPR, organizations must prove that access is granted appropriately, reviewed regularly, and revoked when no longer needed.
With traditional processes, showing this level of control is difficult. But with Identity Governance and Administration (IGA), everything becomes traceable.
SecurEnds enables policy-based provisioning from the moment a new hire is onboarded. Access is granted based on role, location, and function—ensuring alignment with the data minimization principles outlined in GDPR.
In the case of SOX, access to financial systems is logged, monitored, and limited to only those with approved roles. For HIPAA, SecurEnds ensures that only PHI-relevant applications are provisioned to healthcare employees—helping meet strict data protection requirements.
Behind every action is a system of immutable audit logs, showing who approved access, when it was granted, and under what policy. These logs support regular User access reviews, ensuring entitlements remain appropriate as roles change.
Automation also strengthens governance around Employee Self Request, Emergency Access Request, and de-provisioning during Employee Off-Boarding—ensuring no step escapes review.
Ultimately, IGA for onboarding reduces the risk of human error while creating an audit-ready onboarding process that meets internal and regulatory standards with confidence.
Remote & Hybrid Employee Onboarding
As organizations extend their compliance frameworks across geographies and roles, a new layer of complexity emerges—remote and hybrid employee onboarding. The same policy-based controls and governance practices discussed earlier become even more critical when there’s no physical IT touchpoint.
Provisioning access remotely—without delays or missteps—requires more than just virtual handovers. It demands Zero-touch provisioning, device-agnostic policies, and a platform that scales with distributed endpoints. Here’s where SecurEnds ensures consistency: employee records flow from your HR system as usual, but the onboarding process adapts based on device type, user location, and access sensitivity.
Through remote IAM capabilities, conditional logic, and predefined Just in Time Access Requests, employees receive only what they need—and nothing more—from day one. Whether they’re accessing a VPN, core SaaS tools, or cloud infrastructure, access is provisioned securely and logged against policy.
This model doesn’t just apply to full-time employees. For contract workers or project-based roles, organizations can activate temporary access using Contractor Self Request and automatically enforce expiration or revocation as part of the Employee Off-Boarding workflow.
By embedding governance across every onboarding scenario—on-site or remote—SecurEnds protects access integrity without adding operational overhead.
Final Thoughts
Whether teams are fully remote, hybrid, or office-based, one truth remains: Employee Onboarding is no longer just a logistical step—it’s the first point of control in your access lifecycle. Without automation, it opens the door to delays, misaligned access, and costly compliance failures.
SecurEnds transforms onboarding into a strategic advantage—powered by Identity Access Management (IAM) and Identity Governance and Administration (IGA). It supports everything from Employee Self Requests to automated provisioning, embedded User access reviews, and secure off-boarding.
In a world where every new hire can be a new vulnerability—or a new risk vector—why take chances?
Let SecurEnds help you build a faster, smarter, audit-ready onboarding process that works on day one—and scales with your business every day after.
Get started with secure employee onboarding—automated, compliant, and built for the modern workforce.


