Emergency Access Request in IGA: Definition, Benefits & Best Practices
Emergency Access Request in IGA: Definition, Benefits & Best Practices

1. Introduction
What if your admin is locked out during a system outage? That’s not just a hypothetical—it’s a high-risk scenario that organizations must be prepared for. In critical moments like system failures, outages, or cybersecurity incidents, teams may need immediate elevated access to restore operations. This is where an Emergency Access Request (EER) becomes vital.
An Emergency Access Request—sometimes referred to as “break-glass access”—is a controlled, auditable mechanism to grant temporary, elevated privileges during a crisis. It acts as a safety net within your Identity Governance and Administration (IGA) program, ensuring that business continuity isn’t disrupted due to access restrictions.
In today’s dynamic IT environments, unmonitored emergency access can lead to compliance risks and data exposure. That’s why organizations integrating Identity Access Management (IAM) systems are increasingly relying on policy-driven EER workflows that align with governance, security, and audit-readiness goals.
At SecurEnds, we understand the delicate balance between speed and control during emergencies. Our IGA platform provides a secure, compliant, and fully traceable emergency access workflow—giving teams what they need, when they need it, without compromising oversight.
2. What Is an Emergency Access Request?
We’ve already touched on how an outage or system failure can halt operations if the right people can’t access critical systems. That’s where an Emergency Access Request (EER) steps in—not as a convenience, but as a safeguard.
At its core, an Emergency Access Request is a structured way to grant time-limited, elevated privileges during high-stakes situations. Also known as break-glass access, it’s designed for exceptional cases where standard approval workflows—like Self Request/Access Request or Contractor Self Request—aren’t fast enough to meet operational needs.
Imagine this as the digital equivalent of breaking the glass in case of emergency: it’s a contingency path that bypasses routine access protocols, but only under strict conditions, with logging, monitoring, and expiry mechanisms in place.
Organizations often invoke EERs during:
- System outages requiring admin-level intervention
- Incident response scenarios where time is critical
- Emergency maintenance or recovery during a cyber threat
- Gaps in access during Employee Onboarding or Employee Off-Boarding transitions
By embedding this capability within an Identity Governance and Administration (IGA) framework, enterprises ensure that even under pressure, access remains auditable, controlled, and aligned with compliance.
3. Why Emergency Access Needs to Be Controlled
While Emergency Access Requests are essential for operational continuity, they also introduce significant risk when not properly governed. Elevated access, even for a short period, opens the door to potential misuse—whether intentional or accidental.
During emergencies, teams may bypass standard Identity Access Management (IAM) workflows to act quickly. But without the right controls in place, this can lead to:
- Unauthorized privilege escalation
- Unmonitored changes to critical systems
- Inaccurate access logs or missing audit trails
In fact, several high-profile breaches have stemmed from uncontrolled emergency access. According to a SANS Institute report, unmanaged privileged access is one of the top contributors to internal security incidents—particularly in moments of urgency when oversight is weakest.
Beyond security concerns, there are serious compliance implications. Regulatory frameworks like SOX, HIPAA, GDPR, and ISO 27001 require organizations to demonstrate who accessed what, when, and why—even during a crisis. Lack of control over emergency access can result in:
- Non-compliance penalties
- Failed audits
- Erosion of trust with customers and stakeholders
Challenges often arise when emergency access is:
- Granted without formal approval
- Not time-bound
- Missing post-access review
- Not aligned with User Access Reviews or identity governance policies
That’s why leading enterprises don’t just enable EER—they govern it. Platforms like SecurEnds help organizations enforce structured Emergency Access Request workflows that are policy-driven, monitored, and fully auditable—minimizing risk while maximizing response efficiency.
4. Emergency Access Workflow (Step-by-Step)
To minimize risk and ensure compliance, an Emergency Access Request should follow a structured, policy-aligned workflow. Rather than being reactive or ad hoc, the process must be predefined within your organization’s Identity Governance and Administration (IGA) framework. Here’s how it typically unfolds in a secure environment:
Step 1: Incident Triggers Need for Elevated Access
A critical system goes down, or an application behaves unexpectedly. This operational disruption triggers the need for urgent intervention—often by someone who doesn’t have admin rights under normal conditions.
Step 2: Request Initiated via IAM Tool
The responder initiates a request through an IAM solution like SecurEnds—whether it’s an Employee Self Request, Contractor Self Request, or routed by a supervisor—depending on organizational policy. This step replaces informal communication (e.g., chat messages or emails) with a controlled Self Request/Access Request mechanism.
Step 3: Approval by Security Admin or Designated Authority
The request routes to an authorized reviewer—typically a security admin or team lead—who validates the urgency, scope, and necessity before granting access. This step ensures accountability even during time-sensitive situations.
Step 4: Time-Bound Access Granted, with Session Logging
Once approved, access is provisioned for a predefined duration, often minutes to a few hours. All actions performed during this window are logged, ensuring that post-event reviews can trace what happened and why.
Step 5: Auto-Expiry of Access
The access automatically expires once the time limit is reached—eliminating the risk of lingering elevated privileges. This aligns with Just in Time Access Request principles, where access is limited to only what’s needed, when it’s needed.
Step 6: Post-Access Review and Audit Logging
After the event, security teams perform a User Access Review to validate what was accessed, whether actions were appropriate, and whether any additional remediation is needed. Logs are stored for compliance and internal audit readiness.
5. Emergency Access in SecurEnds: How It Works
At SecurEnds, we understand that emergencies can’t wait—but that doesn’t mean security and compliance should take a back seat. That’s why our Emergency Access Request module is designed to be fast, controlled, and fully auditable—ensuring your organization responds quickly without compromising governance.
The module is built into our larger Identity Governance and Administration (IGA) platform, seamlessly working alongside features like Employee Onboarding, Employee Off-Boarding, User Access Reviews, and Just in Time Access Requests.
Here’s what makes it effective:
Access Expiration Timers
Every elevated session is automatically time-bound. Whether it’s a few minutes or a couple of hours, access expires precisely when it should, reducing the risk of forgotten or lingering privileges.
Comprehensive Audit Logs and Session Recording
All actions during an emergency session are captured in real time—who accessed what, when, and for how long. This allows for thorough post-event reviews and simplifies audit preparation.
Automated Policy Enforcement
SecurEnds enforces your organization’s pre-set policies, ensuring emergency access is aligned with security protocols. Whether it’s limiting which users can request access, or restricting what systems can be reached, controls are automated and customizable.
Alerts on Privilege Escalation
Security teams receive real-time notifications when elevated access is requested or granted. This visibility supports proactive oversight and enables fast intervention if needed.
Use Case Walkthrough: Responding to a Server Outage
Imagine a database server goes down outside business hours. An on-call engineer initiates a Contractor Self Request via SecurEnds. The system routes it for immediate approval. Once granted, the engineer receives time-limited access, performs the fix, and the access auto-expires. Logs are generated, and a User Access Review is scheduled post-resolution to ensure everything aligns with policy.
Client Perspective:
“What we love about SecurEnds is the auditability. Even during a midnight server failure, we know who did what and when—with zero manual tracking.”
— IT Security Manager, Financial Services Firm
Explore More: Learn how time-bound access policies work in detail on our Time-Based Access Control page.
6. Emergency Access vs Just-in-Time (JIT) Access
While Emergency Access Requests address unplanned incidents, they are often confused with Just-in-Time (JIT) Access Requests, which are premeditated and governed differently. Understanding the distinction is crucial to implementing the right controls in your Identity Governance and Administration (IGA) strategy.
Think of JIT access as a scheduled tool—ideal for limited, temporary access during routine work like patching, testing, or audits. On the other hand, emergency access is the proverbial “break-glass” option, used only when immediate, unscheduled access is necessary.
Here’s how they compare:
| Feature | Just-in-Time (JIT) Access | Emergency Access |
| Approval Needed | Yes | Often pre-approved or expedited |
| Use Case | Routine, scheduled tasks | Crises, outages, incidents |
| Duration | Few hours | Few minutes to a few hours |
| Monitoring | Proactive | Real-time and reactive |
| Audit Requirement | Standard | High—requires strict traceability |
Both access types can be initiated via Self Request/Access Request modules, whether by employees or contractors. SecurEnds offers governance for both scenarios—ensuring policy-driven controls, regardless of whether access is planned or emergent.
By differentiating these access paths, organizations can better tailor their workflows—balancing Identity Access Management (IAM) agility with security and auditability.
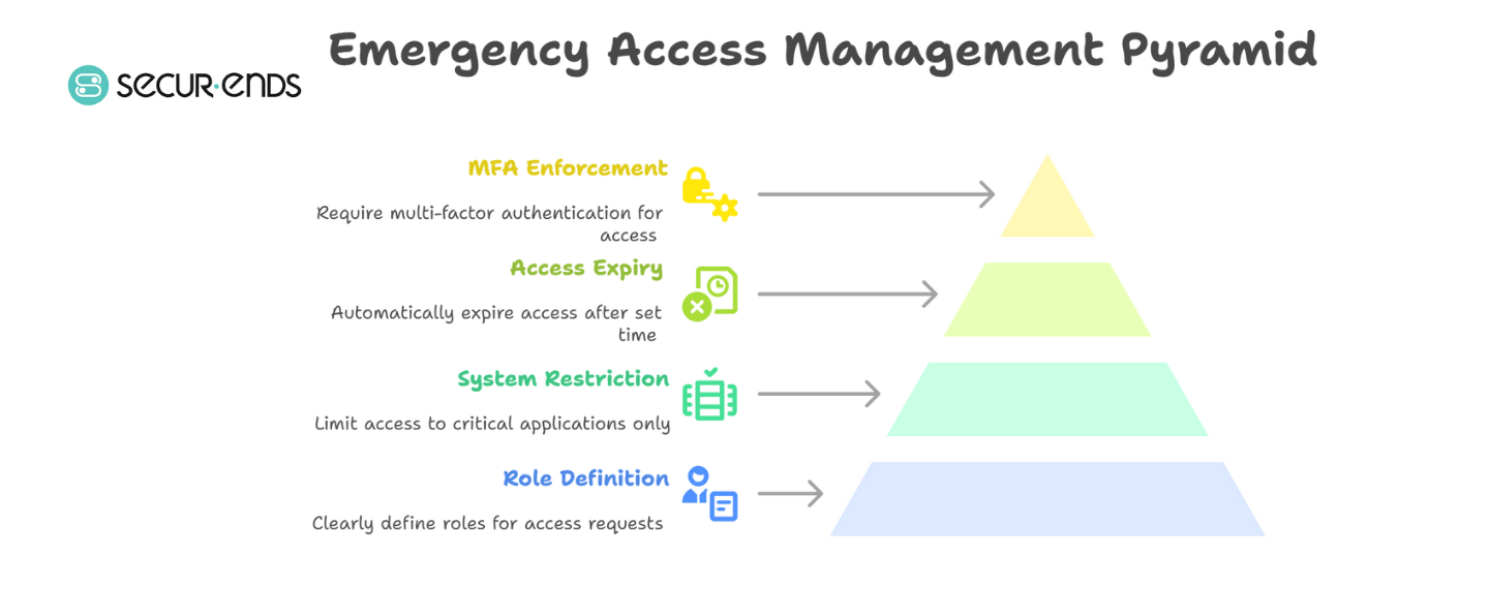
7. Best Practices for Emergency Access Management
Having an Emergency Access Request process is only the first step. To truly minimize risk and maintain compliance, organizations must adopt a structured approach to how emergency access is planned, granted, and reviewed. Below are best practices that ensure emergency access remains a security enabler—not a vulnerability.
1. Define Roles and Scope in Advance
Clearly define who can request and approve emergency access. For example, limit Employee Self Requests and Contractor Self Requests to critical roles, and assign dedicated security approvers. This pre-planning helps prevent misuse during chaotic moments.
2. Restrict to Critical Systems Only
Emergency access should be tightly scoped. Only the most essential applications—such as database servers, firewalls, or identity systems—should be eligible for elevated access. This aligns with Identity Governance and Administration (IGA) policies that prioritize risk-based control.
3. Enable Automatic Access Expiry
Set strict, non-negotiable expiration timers on emergency access. With SecurEnds, access durations are pre-configured and enforced automatically, ensuring no privileges persist longer than needed.
4. Enforce Multi-Factor Authentication (MFA)
Before granting access, require users to validate their identity with multi-factor authentication (MFA). Whether the request originates from an Employee Self Request or a contractor, this step is critical to maintaining control under pressure.
5. Monitor in Real Time and Review Post-Event
Use real-time monitoring during active emergency sessions, and schedule User Access Reviews afterward. This two-layered approach ensures that actions are both visible during the event and formally validated afterward.
6. Align with Compliance Frameworks
Design your emergency access workflow to align with industry regulations such as SOX, HIPAA, and ISO 27001. Each requires strong oversight of privileged activity—even in unplanned events. SecurEnds supports this with policy-driven workflows and audit-ready logs.
Pro Tip: Download our Emergency Access Governance Checklist to assess whether your current workflow is secure, compliant, and audit-ready.
8. Emergency Access and Compliance: What Auditors Look For
Compliance is non-negotiable—especially when it comes to Identity Access Management (IAM) and elevated access. During audits, emergency access can quickly become a red flag if it lacks structure, visibility, or documentation.
How Emergency Access Supports Compliance Frameworks
Emergency Access Requests (EERs) ensure that even in crisis scenarios, elevated access is:
- Requested with purpose
- Approved by the right authority
- Time-bound and monitored
- Revoked promptly after use
These principles directly support the requirements of major compliance standards:
- SOX (Sarbanes-Oxley Act): Demands strong internal controls and accountability for system access.
- HIPAA: Requires restricted, auditable access to PHI during emergencies.
- ISO 27001: Emphasizes documented access control procedures, including temporary access.
- NIST Cybersecurity Framework (CSF): Recommends identity-centric controls, even during security events.
In short, EERs help prove that elevated access was not only justified but also managed securely—an expectation for any modern IGA program.
Importance of Logging and Access Review Reports
Auditors look for traceable evidence such as:
- Who requested access (e.g., through Employee Self Request or Contractor Self Request)
- Who approved the request
- When access was granted and revoked
- What systems or data were accessed
Comprehensive User Access Reviews following each incident help validate that privileges were not only time-bound but also revoked post-crisis, maintaining the principle of least privilege.
How SecurEnds Automates Compliance Evidence
SecurEnds simplifies audit readiness by automatically capturing all required access data:
- Request initiator and approver
- Access timeframes and system targets
- Session logs and policy enforcement actions
These logs feed directly into structured reports that align with audit checklists across multiple compliance frameworks. The result: fewer manual interventions, reduced audit preparation time, and reliable, tamper-proof records.
User Access Review (UAR) for Post-Event Validation
After access is revoked, SecurEnds’ User Access Review module enables security and compliance teams to:
- Revalidate user roles and entitlements
- Detect privilege creep
- Confirm that all emergency rights were appropriately rescinded
By embedding this step into the Employee Off-Boarding, Onboarding, and Emergency Access Request lifecycle, SecurEnds helps enforce continuous compliance without overburdening internal teams.
9. Conclusion
Emergency access is indispensable in today’s fast-paced, high-risk digital environments—but without proper controls, it can quickly become a liability. From avoiding privilege misuse to staying compliant with global standards, organizations need a structured and secure way to handle elevated access in times of need.
That’s where Identity Governance and Administration (IGA) solutions like SecurEnds come in. By enabling Emergency Access Requests that are approved, time-bound, monitored, and auditable, SecurEnds transforms what used to be a high-risk exception into a well-governed process.
Through features like automated approval workflows, access expiration timers, User Access Reviews, and post-event validation, SecurEnds ensures that every emergency access instance supports the principles of Identity Access Management (IAM) and continuous compliance.
Want to secure your emergency access process?
Request a demo of SecurEnds today to see how our platform can help you implement controlled, auditable, and policy-driven emergency access workflows across all user types—from Employee Self Request to Contractor Self Request and beyond.
10. Frequently Asked Questions (FAQ)
Emergency access refers to temporary, elevated permissions granted to users—typically administrators or support staff—during critical incidents. Within an Identity Access Management (IAM) system, such access is tightly controlled, monitored, and revoked after the crisis ends.
A break-glass account, often used in Emergency Access Requests, is a predefined user account that allows elevated access during emergencies. Similar to breaking glass in case of fire, it bypasses standard workflows but must be auditable and time-bound to ensure compliance.
Emergency access should be used only during unexpected scenarios—like outages, security incidents, or when key personnel are unavailable—to restore operations. It complements Just in Time Access Requests, which are planned and pre-approved for specific tasks.
Emergency access is typically requested through a Self Request/Access Request or triggered automatically during incidents. It must be approved by an authorized stakeholder, granted for a short duration, logged, and revoked as soon as normal operations resume. Solutions like SecurEnds automate this process end-to-end.
Unmonitored emergency access can lead to privilege abuse, data breaches, and audit failures. Regulations like SOX, HIPAA, and ISO 27001 require that emergency access be documented, reviewed, and aligned with broader Identity Governance and Administration (IGA) policies.
SecurEnds enforces secure emergency access through:
- Time-bound access control
- Automated policy enforcement
- Real-time alerts and session logging
- Post-event User Access Reviews
- Audit-ready reports for frameworks like SOX, HIPAA, and NIST CSF
It also integrates with broader IAM workflows such as Employee Onboarding, Employee Off-Boarding, and Contractor Self Request, ensuring security throughout the user lifecycle.


