Understanding Access Control Policy: A Complete Guide for Modern Security
Understanding Access Control Policy: A Complete Guide for Modern Security

1. Introduction to Access Control Policies
In today’s complex digital landscape, safeguarding sensitive information is a top priority for organizations across all sectors. An access control policy is a fundamental component of any effective cybersecurity policy, serving as a framework that defines who can access specific data, systems, or resources within an organization—and under what conditions.
But what is access control exactly? At its core, access control is the practice of restricting and regulating user access to critical systems and information. This ensures that only authorized individuals can interact with data in ways that align with their roles and responsibilities. These rules and protocols form the basis of an organization’s user access management strategy.
By implementing a robust access control policy, businesses can prevent unauthorized access, reduce the risk of data breaches, and maintain regulatory compliance. Whether through role-based access, mandatory access controls, or discretionary models, these policies play a crucial role in shaping the security posture of modern enterprises.
2. Why Access Control Policies Matter in Cybersecurity
The importance of access control in today’s cybersecurity environment cannot be overstated. With cyber threats evolving rapidly, organizations must proactively safeguard their digital assets. This is where well-defined access control policies come into play—they act as a first line of defense against unauthorized access and potential breaches.
Effective policies directly contribute to data security by ensuring that only authorized personnel have access to sensitive information. This minimizes the risk of internal and external threats exploiting vulnerabilities or gaining access to critical systems.
Moreover, access control policies are vital for meeting compliance requirements set by regulatory frameworks such as GDPR, HIPAA, and ISO/IEC 27001. These regulations mandate strict access governance to protect consumer and enterprise data.
Another critical benefit is the enforcement of the least privilege principle. This concept ensures that users are granted the minimum level of access necessary to perform their job functions—nothing more, nothing less. By limiting access in this way, organizations can significantly reduce their attack surface and limit the potential damage of compromised accounts.
3. The Evolution of Access Control Models
Understanding the history of access control helps us appreciate how far cybersecurity strategies have advanced. Early systems primarily relied on Discretionary Access Control (DAC), where resource owners decided who had access to what. While simple, DAC was prone to inconsistencies and security gaps.
As organizations recognized the need for more structured security, Mandatory Access Control (MAC) and Role-Based Access Control (RBAC) emerged, marking a significant phase in access control evolution. These models introduced more rigid, rule-based systems that aligned access permissions with organizational roles and hierarchies.
In recent years, cybersecurity has shifted toward more adaptive and risk-aware approaches. This shift has given rise to the Zero Trust model—one of the most influential cybersecurity trends today. Zero Trust assumes that no user or system is inherently trusted, even within the network perimeter. It requires continuous authentication, authorization, and monitoring of all users and devices.
From basic file permissions to sophisticated identity-driven strategies, the evolution of access control reflects the growing complexity and urgency of modern cybersecurity needs.
4. How Access Control Policies Work
To understand how access control works, it’s important to break down the typical access management flow into its key stages: authentication, authorization, and auditing. These steps ensure that access to data and systems is both intentional and secure.
- Authentication
The process begins by verifying a user’s identity using credentials such as passwords, biometrics, or multi-factor authentication. - Authorization
Once authenticated, the system evaluates the user’s permissions and grants access based on predefined rules. This is the core of policy enforcement, ensuring users can only access what they’re allowed to. - Auditing
Every access attempt is logged and monitored. This supports incident detection, forensic analysis, and compliance audits.
By following this structured flow, organizations enforce secure access consistently and efficiently. Effective policy enforcement not only mitigates internal and external risks but also strengthens long-term governance and compliance.
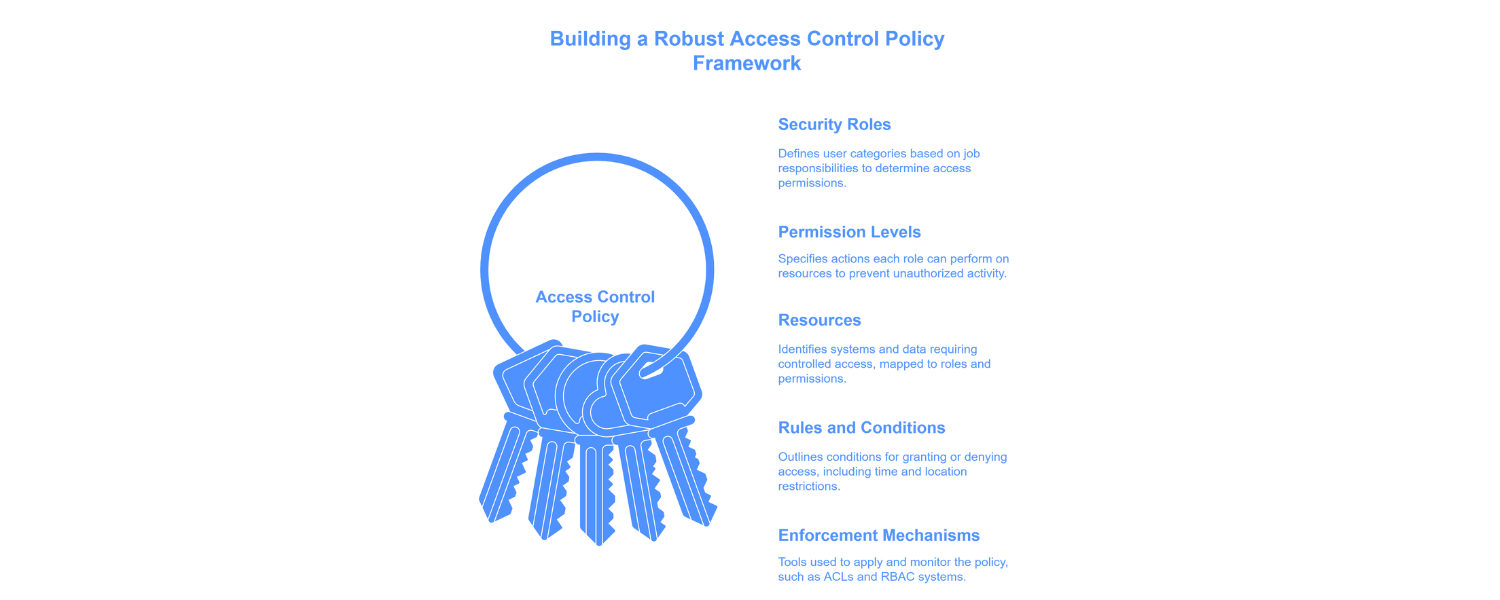
5. Key Components of an Access Control Policy
An effective access control policy is built on several critical elements that work together to regulate and secure access to digital resources. Understanding these access control components is essential for creating a robust and enforceable security framework.
- Security Roles
Define user categories based on job responsibilities or functions (e.g., administrator, HR manager, finance officer). These policy elements determine what each role is permitted to access.
- Permission Levels
Specify the actions each role can perform—such as read, write, modify, or delete—on specific resources. Assigning clear permission levels reduces ambiguity and prevents unauthorized activity.
- Resources
Identify the systems, files, applications, or data that require controlled access. Every resource within the infrastructure should be mapped to appropriate roles and permissions.
- Rules and Conditions
Outline the specific conditions under which access is granted or denied. This may include time-based restrictions, IP filters, device trust levels, or geolocation data.
- Enforcement Mechanisms
The technical and procedural tools used to apply and monitor the policy—such as access control lists (ACLs), role-based access control (RBAC) systems, or automated identity governance tools.
By clearly defining these access control components, organizations can ensure consistent application of access policies, improve system integrity, and support ongoing security compliance.
6. Types of Access Control Policies (RBAC, ABAC, MAC, DAC)
Access control is not a one-size-fits-all solution. Different organizations adopt different access control models based on their operational needs, infrastructure, and risk profile. Understanding the major policy frameworks—RBAC, ABAC, MAC, and DAC—helps in choosing the right model for your environment.
Here’s a comparison of key models:
- Role-Based Access Control (RBAC)
Access is granted based on predefined security roles within an organization.
- Use case: Ideal for enterprises with structured departments and consistent role hierarchies.
- Strength: Scalable and easy to manage in large organizations.
- Part of the ongoing discussion in RBAC vs ABAC when determining suitability for traditional vs dynamic environments.
- Use case: Ideal for enterprises with structured departments and consistent role hierarchies.
- Attribute-Based Access Control (ABAC)
Access decisions are made using attributes such as user role, device, location, and time.
- Use case: Best suited for dynamic, cloud-based environments where conditions frequently change.
- Strength: Offers granular and flexible control policies.
- Often preferred over RBAC in complex, context-driven systems.
- Use case: Best suited for dynamic, cloud-based environments where conditions frequently change.
- Mandatory Access Control (MAC)
Access is enforced by system-defined rules, often used in high-security environments.
- Use case: Government agencies or military institutions.
- Strength: Offers strict control with minimal user discretion.
- A common comparison in MAC vs DAC, highlighting centralized vs discretionary control.
- Use case: Government agencies or military institutions.
- Discretionary Access Control (DAC)
Resource owners determine access permissions.
- Use case: Suitable for small businesses or systems with limited sensitivity.
- Strength: Flexible, but more prone to misconfigurations and insider threats.
- Use case: Suitable for small businesses or systems with limited sensitivity.
Choosing between RBAC vs ABAC or MAC vs DAC depends on the organization’s security needs, regulatory obligations, and infrastructure complexity. Aligning the right model with the right use case is essential for building a resilient access control architecture.
7. Access Control Policies in Cloud Environments
Key Implementations:
- AWS Access Control (AWS IAM)
AWS Identity and Access Management (IAM) allows organizations to define users, groups, and roles with fine-grained permissions.
- Supports both resource-based and identity-based policies.
- Enables least-privilege access and multi-factor authentication (MFA) enforcement.
- Core to managing cloud security within Amazon Web Services environments.
- Supports both resource-based and identity-based policies.
- Azure Policy and Role-Based Access Control (RBAC)
Microsoft Azure provides a powerful Azure policy framework integrated with RBAC.
- Access is assigned at the subscription, resource group, or resource level.
- Supports compliance enforcement through policy definitions and initiatives.
- Ideal for enterprises needing governance across hybrid and multi-cloud setups.
- Access is assigned at the subscription, resource group, or resource level.
- SaaS Permissions
Modern SaaS platforms (e.g., Google Workspace, Salesforce, Dropbox) offer built-in access control tools to manage user roles and application-level permissions.
- Access is often role-based but may include conditional access depending on the platform.
- Ensuring secure SaaS permissions is vital for protecting data across third-party services.
- Access is often role-based but may include conditional access depending on the platform.
In all cases, consistent application of access control policies—whether in AWS, Azure, or SaaS platforms—is essential to mitigating risk and maintaining regulatory compliance in the cloud.
8. Roles and Permissions in Access Control
A well-structured access control system relies heavily on clearly defined access control roles and corresponding permission sets. These roles are assigned based on job responsibilities and dictate what resources users can access and what actions they can perform. Effective permission management is crucial for reducing security risks and ensuring operational efficiency.
Common Access Control Roles:
- Administrator
- Full system access, including user provisioning, configuration changes, and audit log management.
- Requires the highest level of user privileges and oversight.
- Full system access, including user provisioning, configuration changes, and audit log management.
- Standard User
- Limited access to perform routine tasks relevant to their role.
- Permissions are typically restricted to read or write access for specific data sets.
- Limited access to perform routine tasks relevant to their role.
- Auditor
- Read-only access to logs, reports, and system activities.
- Plays a key role in compliance and monitoring without influencing system behavior.
- Read-only access to logs, reports, and system activities.
Permission Assignments:
- Permission management involves mapping each role to a set of allowable actions—such as read, write, delete, or execute—on defined resources.
- Permissions should follow the principle of least privilege, granting users only the access required to perform their duties.
- Role-based models simplify the administration of user privileges, especially in large organizations where managing individual permissions can become complex.
Clearly defined access control roles and well-managed permissions help organizations maintain security, streamline access governance, and ensure compliance with regulatory requirements.
9. Benefits of a Strong Access Control Policy
Implementing a robust access control policy offers far-reaching benefits across cybersecurity, compliance, and organizational performance. When properly structured and enforced, these policies not only protect sensitive data but also streamline internal operations and support long-term risk management goals.
Key Policy Benefits Include:
- Enhanced Security Advantages
- Minimizes the risk of unauthorized access, insider threats, and data breaches.
- Supports the enforcement of the least privilege principle and role-based restrictions.
- Minimizes the risk of unauthorized access, insider threats, and data breaches.
- Regulatory Compliance
- Helps meet legal and industry-specific requirements such as GDPR, HIPAA, and ISO 27001.
- Enables comprehensive audit trials and evidence of due diligence for security reviews.
- Strengthens alignment with regulatory compliance frameworks through consistent access governance.
- Helps meet legal and industry-specific requirements such as GDPR, HIPAA, and ISO 27001.
- Operational Efficiency
- Simplifies user provisioning and de-provisioning processes.
- Reduces manual oversight through automation and predefined role structures.
- Enhances accountability by mapping actions to verified user roles.
- Simplifies user provisioning and de-provisioning processes.
By delivering measurable security advantages and reducing compliance-related risks, a strong access control policy becomes an integral part of any organization’s cybersecurity and governance strategy.
10. Challenges in Policy Implementation
While access control policies are essential for maintaining security and compliance, organizations often face significant hurdles during implementation. These access control challenges can lead to gaps in enforcement, inefficiencies, or user friction if not proactively addressed.
Common Policy Pitfalls and Implementation Issues:
- Role Explosion
- As organizations scale, the number of roles can multiply rapidly—especially in Role-Based Access Control (RBAC) models.
- This makes it difficult to manage and audit roles effectively, leading to excessive or outdated user privileges.
- As organizations scale, the number of roles can multiply rapidly—especially in Role-Based Access Control (RBAC) models.
- Legacy Systems Integration
- Older systems may lack modern access control features or APIs, making integration with current policy frameworks complex.
- These systems often require manual overrides or custom scripts, increasing the risk of misconfigurations.
- Older systems may lack modern access control features or APIs, making integration with current policy frameworks complex.
- User Resistance
- End users and even administrators may resist new policies that seem restrictive or impact productivity.
- Without proper change management and communication, security efforts can be undermined by workarounds or non-compliance.
- End users and even administrators may resist new policies that seem restrictive or impact productivity.
- Inconsistent Policy Enforcement
- When access rules vary across departments, platforms, or regions, it creates policy pitfalls that attackers can exploit.
- A centralized approach to governance is often needed to maintain consistency.
- When access rules vary across departments, platforms, or regions, it creates policy pitfalls that attackers can exploit.
- Lack of Visibility and Auditing Tools
- Without robust monitoring, it’s difficult to detect violations or optimize permissions over time.
- Auditing gaps contribute to long-term implementation issues and non-compliance risks.
- Without robust monitoring, it’s difficult to detect violations or optimize permissions over time.
Addressing these access control challenges requires a combination of the right technology, stakeholder alignment, and continuous policy refinement. Successful implementation balances security with usability while maintaining a clear path for policy evolution.
11. Best Practices for Effective Policies
To ensure that access control policies are both secure and sustainable, organizations must follow proven strategies that enhance visibility, reduce risk, and support ongoing compliance. These access control best practices are essential for maintaining control over user access across complex environments.
Recommended Approaches for Policy Optimization:
- Enforce Least Privilege Access
- Grant users only the permissions necessary to perform their job functions—nothing more.
- This reduces the attack surface and limits potential damage from compromised accounts.
- Grant users only the permissions necessary to perform their job functions—nothing more.
- Conduct Regular Access Audits
- Periodically review roles, permissions, and user access logs to identify anomalies, redundancies, or outdated privileges.
- Audits are critical for policy optimization and compliance with industry regulations.
- Periodically review roles, permissions, and user access logs to identify anomalies, redundancies, or outdated privileges.
- Implement Multi-Factor Authentication (MFA)
- Strengthens identity verification by requiring additional authentication factors beyond passwords.
- MFA is a foundational element in modern security frameworks like Zero Trust.
- Strengthens identity verification by requiring additional authentication factors beyond passwords.
- Use Automated Identity and Access Management (IAM) Tools
- Automate provisioning, de-provisioning, and role assignments to reduce human error.
- Integration with HR and IT systems ensures real-time updates and centralized control.
- Automate provisioning, de-provisioning, and role assignments to reduce human error.
- Align with Recognized Security Frameworks
- Follow guidance from frameworks such as NIST, ISO 27001, or CIS Controls to structure and enforce access policies.
- These standards provide a solid foundation for scalable and compliant access control.
- Follow guidance from frameworks such as NIST, ISO 27001, or CIS Controls to structure and enforce access policies.
Adhering to these access control best practices enhances policy effectiveness, reduces operational overhead, and supports long-term data security objectives.
12. Access Control Policies and Compliance
Robust access control policies are not only essential for securing digital assets—they are also a core requirement for meeting regulatory and industry-specific standards. Whether governed by privacy laws or cybersecurity frameworks, aligning with compliance requirements ensures that access is managed in a secure, auditable, and legally compliant manner.
How Policies Support Key Standards:
- GDPR Access Control
- The General Data Protection Regulation (GDPR) mandates that organizations implement measures to ensure personal data is accessed only by authorized individuals.
- Access control policies help enforce data minimization, role-based access, and auditability—key principles under GDPR access control mandates.
- The General Data Protection Regulation (GDPR) mandates that organizations implement measures to ensure personal data is accessed only by authorized individuals.
- HIPAA (Health Insurance Portability and Accountability Act)
- For healthcare organizations, HIPAA requires safeguards to protect patient health information (PHI).
- Policies must define user roles, access permissions, and audit logging to ensure only authorized staff can view or modify PHI.
- For healthcare organizations, HIPAA requires safeguards to protect patient health information (PHI).
- SOC 2 (System and Organization Controls 2)
- SOC 2 focuses on five trust principles: security, availability, processing integrity, confidentiality, and privacy.
- Strong access control frameworks are central to achieving SOC 2 compliance, as they demonstrate how sensitive data is protected against unauthorized access.
- SOC 2 focuses on five trust principles: security, availability, processing integrity, confidentiality, and privacy.
- NIST Guidelines
- The National Institute of Standards and Technology (NIST) offers widely recognized frameworks like NIST SP 800-53 and NIST Cybersecurity Framework.
- The National Institute of Standards and Technology (NIST) offers widely recognized frameworks like NIST SP 800-53 and NIST Cybersecurity Framework.
These NIST guidelines provide detailed controls for identity management, role-based access, auditing, and authentication protocols.
13. Future Trends in Access Control
As cybersecurity threats become more sophisticated, access control is evolving beyond traditional models. The future of access control lies in intelligent, adaptive systems that go beyond static rules to deliver real-time, context-aware protection. Emerging technologies are reshaping how organizations define, enforce, and optimize user access.
Key Innovations Shaping the Future:
- AI in Security
- Artificial Intelligence is being used to create dynamic, self-learning access control systems.
- AI can detect unusual user behavior, flag anomalies, and automatically adjust permissions based on risk scores.
- This reduces false positives and enhances threat detection, making AI in security a game-changer for identity and access management.
- Artificial Intelligence is being used to create dynamic, self-learning access control systems.
- Zero Trust Policies
- The Zero Trust approach assumes no implicit trust, even within the network perimeter.
- Access is continuously verified through contextual factors like device health, location, user behavior, and time of access.
- Zero Trust policies are increasingly being adopted across cloud, hybrid, and on-premise infrastructures.
- The Zero Trust approach assumes no implicit trust, even within the network perimeter.
- Behavioral Access Control
- This emerging model uses user behavior analytics (UBA) to determine access rights.
- Instead of relying solely on roles or static permissions, it evaluates how users typically interact with systems.
- Deviations from established patterns can trigger step-up authentication or temporary access restrictions.
- This emerging model uses user behavior analytics (UBA) to determine access rights.
- Policy Automation and Orchestration
- Future systems will focus on automating policy enforcement across multi-cloud environments.
- Unified dashboards and automated workflows will help security teams implement consistent controls at scale.
- Future systems will focus on automating policy enforcement across multi-cloud environments.
The future of access control is intelligent, context-aware, and adaptive—enabling organizations to stay ahead of threats while maintaining flexibility and compliance.
14. Conclusion: Is Your Policy Secure Enough?
Strong access control policies are critical for protecting data, meeting compliance standards, and reducing cyber risks. From setting roles and permissions to using AI and Zero Trust models, organizations must ensure their access strategy is built for today—and ready for tomorrow.
Key points to remember:
- A secure access control policy helps prevent unauthorized access and supports regulations like GDPR and HIPAA.
- Modern challenges like user resistance and outdated systems require better tools and clear policy design.
- Trends like AI, behavioral analytics, and Zero Trust are reshaping how access is managed.
Still unsure if your current strategy is enough?
SecurEnds offers advanced cybersecurity solutions that help you assess, automate, and improve your access policies. With tools for identity governance, access reviews, and compliance, our platform supports every step of your policy assessment journey.
Ready to strengthen your access control?
Get started with SecurEnds IAM solutions today.


