Access Analysis
Access Analysis
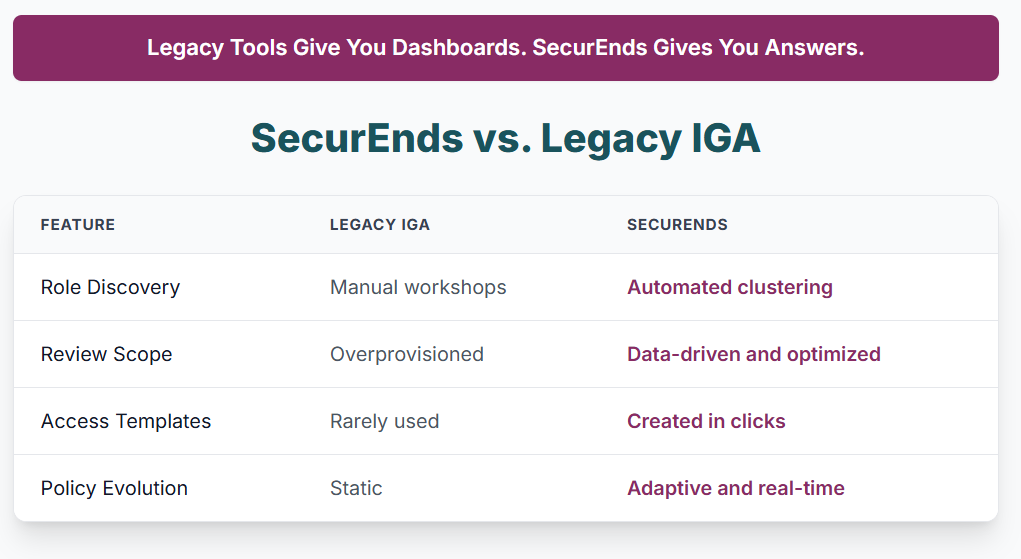
Turn Entitlement Chaos into Role Intelligence
Discover An Automated Alternative For Role Mining
Access governance fails when it’s built on assumptions. SecurEnds Access Analysis helps you discover what access should look like—based on real user behavior, not static role models or tribal knowledge.
SecurEnds Access Analysis: Unlocking Access Intelligence at Scale
SecurEnds Access Analysis is a purpose-built solution that enables organizations to shift from reactive identity governance to intelligent, proactive access management. Traditional identity governance often focuses on compliance after the fact—identifying issues only when audits uncover them or when breaches reveal weaknesses. SecurEnds turns that paradigm on its head by helping you understand how access is actually used across your enterprise—before it becomes a problem.
By automatically discovering patterns in access across users, departments, job functions, and applications, SecurEnds delivers the visibility and clarity needed to build governance frameworks that are sustainable, scalable, and tailored to your organization’s real-world structure. Whether you’re a fast-growing enterprise, a regulated institution, or a company maturing its security posture, Access Analysis helps you create smarter access controls rooted in data, not assumptions.
Why It Matters
Legacy IGA (Identity Governance and Administration) tools operate on a dated assumption: that IT or security teams can define roles and entitlements in a vacuum before any automation takes place. In reality, role-building in most organizations becomes a time-consuming, error-prone effort involving spreadsheets, workshops, and endless stakeholder interviews. Worse, by the time these roles are defined, the business has often changed—rendering those models outdated.
Roles don’t stay static. People change jobs. Contractors come and go. Mergers and reorganizations shift team boundaries. And yet, many organizations are left managing access with rigid models that no longer reflect business reality. This leads to overprovisioned users, stale entitlements, audit failures, and increased attack surfaces.
SecurEnds Access Analysis uses identity analytics to reveal how access is truly being assigned and used—across systems, regions, and teams. It doesn’t just show who has access. It shows why they have it, how they got it, and whether it still makes sense. With these insights, you can:
Eliminate overprovisioning by aligning access to actual usage
Accelerate RBAC deployment through automated, data-backed role generation
Simplify access reviews by grouping similar entitlements into templates
Strengthen compliance posture with evidence-based access models

Enable continuous improvement with an evolving view of entitlements over time
In short, Access Analysis cuts through the noise to deliver what every governance team needs: clarity, context, and control.
How It Works
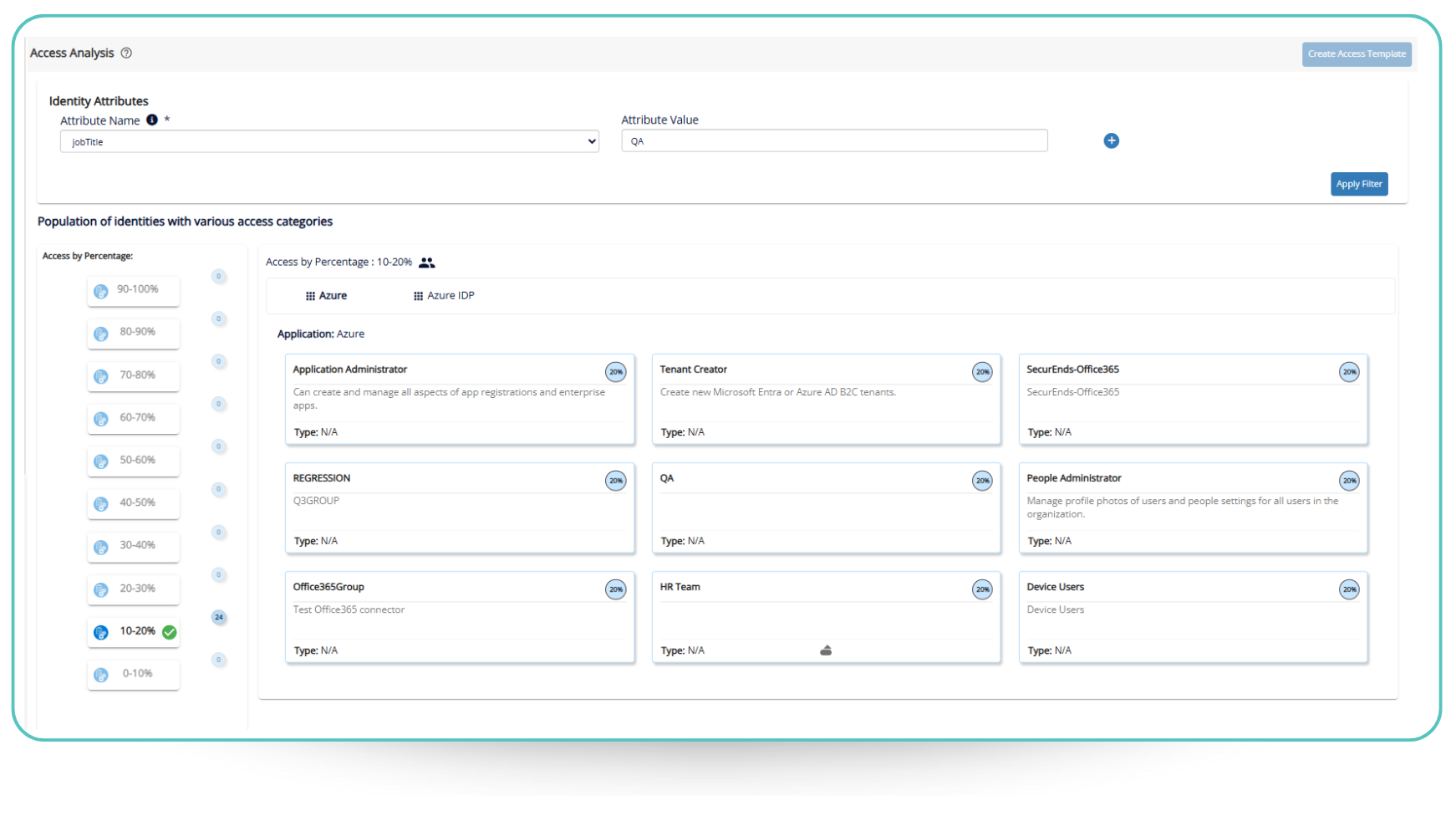
SecurEnds continuously mines entitlement data from your connected applications and cross-references it with user attributes like:
Job code
Department
Location
Business function
Employment type
Access data is only useful when it’s contextualized—and that’s where SecurEnds excels. The platform connects to your identity ecosystem, including both cloud-based and on-premises systems, to collect raw entitlement data. This data is brought in via flexible ingestion methods like T-Hub (SecurEnds’ own integration engine), secure file transfers, APIs, or native connectors.
Once ingested, the data is enriched using authoritative sources like your HR system, Active Directory, or LDAP. SecurEnds maps entitlements to user attributes such as job code, department, manager, employment type, geographic location, and more. This contextual enrichment is critical—it allows the system to understand not just who has access, but how that access aligns with their role in the organization.
The result is a rich, multidimensional view of access across your enterprise. SecurEnds presents this visually using access mind maps and entitlement clustering graphs. These interactive diagrams make it easy to spot trends, identify anomalies, and see which users fall outside the expected patterns for their role or department.
With this foundation in place, Access Analysis helps you automatically generate Access Templates—groupings of entitlements that can be reused across similar users or business units. These templates can be used in the Access Request module to streamline provisioning, or in Access Reviews to focus attention on deviations from the norm. Over time, as your workforce evolves, SecurEnds continually refines these templates by reanalyzing data, ensuring your governance model stays in sync with the organization.
The final outcome? Your team spends less time guessing and more time governing. You reduce identity risk, meet compliance demands with confidence, and build a more agile and resilient access model—ready to scale as your business grows.