What Is Automated Employee Onboarding and Why It Matters
What Is Automated Employee Onboarding and Why It Matters

I. Introduction: Why Onboarding Is More Than Just Paperwork
A new employee joins the company. HR completes the formalities, but IT’s still waiting on the ticket. Their system access? Delayed. Their credentials? Not ready. By the end of week one, they’re still chasing approvals and haven’t fully logged in.
Behind the scenes, a bigger problem is already unfolding: they’ve been granted broad access just to “get them started”—access they’ll never use, but will probably never lose either.
This isn’t a one-off mistake. It’s a pattern. One that plays out in thousands of organizations every week.
The traditional approach to employee onboarding is slow, fragmented, and dangerously inconsistent. And in environments where compliance, insider risk, and hybrid workforces are top concerns—that’s no longer acceptable.
That’s why security-first enterprises are moving toward a smarter model:
One where HR, IT, and Security speak the same language
One where access is granted based on roles, not guesswork
One where onboarding is automated, auditable, and built to scale
This shift—from spreadsheets to automated onboarding processes—isn’t just operational. It’s strategic.
Because in modern enterprises, onboarding doesn’t just welcome employees. It protects the organization.
II. What Is Automated Employee Onboarding?
Most people think of onboarding as HR’s job—paperwork, welcome emails, system logins. But in reality, onboarding is the first point where identity, access, and security intersect.
That’s where automated employee onboarding comes in.
At its core, it’s a framework where employee access provisioning, account creation, approvals, and compliance logging happen automatically—driven by rules, not reminders.
What It Includes:
- Account provisioning across enterprise apps, cloud tools, and internal systems
- Device setup, license assignments, and system entitlements
- Access provisioning tied to predefined roles or departments
- Approval routing and policy enforcement built into the workflow
- Audit-ready logging from day one
This isn’t just faster. It’s more secure and scalable—especially when integrated with tools like:
- HRIS (for real-time employee data)
- ITSM (to trigger service workflows)
- IAM (Identity Access Management) and
- IGA (Identity Governance and Administration) platforms (for controls, attestation, and lifecycle tracking)
With these systems connected, onboarding becomes intelligent. For instance, a software engineer in R&D might have auto-provisioned access to GitHub, Jira, and DevOps tools—no manual intervention required.
More importantly, it ensures role-based access control onboarding, so no one gets more access than needed.
And because it’s part of a broader employee lifecycle automation strategy, onboarding seamlessly transitions into ongoing access reviews, offboarding, and compliance checks—without friction.
III. Challenges in Manual Onboarding
For many organizations, onboarding still relies on a patchwork of emails, tickets, spreadsheets, and human follow-ups. The result? Delays, errors, and risk—none of which are scalable or compliant.
Here’s what typically goes wrong in manual onboarding environments:
Fragmented Requests Between HR and IT
HR teams often send access requests after the employee has already joined—or worse, forget to send them entirely. IT is left reacting instead of planning, creating last-minute scrambles and access gaps.
Overprovisioning Without Role Mapping
Without a standardized approach to role-based access control onboarding, new employees are often granted broad or default access “just to get started.”
This leads to privilege creep, where users retain unnecessary access even after role changes.
Delayed Day-One Productivity
New hires wait days—or weeks—for full access to the tools they need. This isn’t just frustrating; it’s expensive. Every delay affects onboarding experience, productivity, and team velocity.
Zero Auditability
With no centralized system to track what was provisioned, when, or why, organizations struggle during user access reviews and compliance audits.
There’s no approval trail, no policy enforcement, and no easy way to validate access decisions.
These issues aren’t just operational inefficiencies—they’re security liabilities.
That’s why the move to IT onboarding automation isn’t optional. It’s a necessity for modern enterprises that want to be fast, compliant, and secure from day one.
IV. Why Automate Employee Onboarding
The challenges of manual onboarding are clear. But automation isn’t just a fix—it’s a strategic upgrade.
With the right systems in place, onboarding becomes secure, compliant, and immediate.
Here’s what automating employee onboarding unlocks for modern enterprises:
Instant Day-One Access
Provisioning is no longer delayed by backlogged tickets or unclear emails.
With role-based provisioning, access is granted the moment HRIS data is updated—ensuring every employee can contribute from day one.
Least Privilege by Default
Using IAM onboarding best practices, access is assigned based on job roles—not personal requests.
This helps enforce least-privilege policies and reduces unnecessary exposure to sensitive systems.
Built-In Compliance from the Start
Automation ensures that every access request is logged, routed through approvals, and tied to a policy.
This eliminates guesswork and builds an audit trail ready for compliance checks.
Reduced IT Workload
By removing manual provisioning steps, IT no longer needs to manage Excel trackers, follow up on missing details, or clean up after incorrect access assignments.
Resources can focus on strategic work—not rework.
Automating onboarding is also the foundation for broader identity maturity. It supports employee lifecycle automation, enables user access reviews, and connects seamlessly with systems that manage contractor self requests, employee self requests, and even emergency access requests.
When every access decision is automated, transparent, and role-aligned, onboarding isn’t just efficient—it’s secure by design.
V. IAM/IGA: The Backbone of Onboarding Automation
Behind every successful automated onboarding process is a robust identity infrastructure—specifically, an integrated Identity Access Management (IAM) and Identity Governance and Administration (IGA) platform.
These platforms do more than connect systems.
They define how access is assigned, approved, monitored, and eventually revoked across the employee lifecycle.
Here’s how IAM and IGA power secure onboarding:
Role-Based Access Control (RBAC)
IAM systems apply role-based access control onboarding, ensuring that users only get access relevant to their job function—nothing more, nothing less.
Policy-Driven Provisioning
Access rules and provisioning workflows are governed by predefined policies. Whether it’s a just in time access request or a standard onboarding case, IAM ensures decisions are consistent and auditable.
Application Discovery and Mapping
IGA platforms continuously scan your environment to detect new systems and assign them to the right user groups—so that onboarding scales even as your tech stack evolves.
Audit and Attestation Workflows
Every access point is logged. IAM/IGA platforms support automated user access reviews, approval trails, and recertification processes—helping teams meet SOX, HIPAA, and GDPR requirements with ease.
Together, IAM and IGA serve as the enforcement layer that turns automation from a time-saver into a security-first onboarding strategy.
Without them, onboarding remains a disconnected process. With them, it becomes a scalable, policy-aligned part of your employee lifecycle automation program.
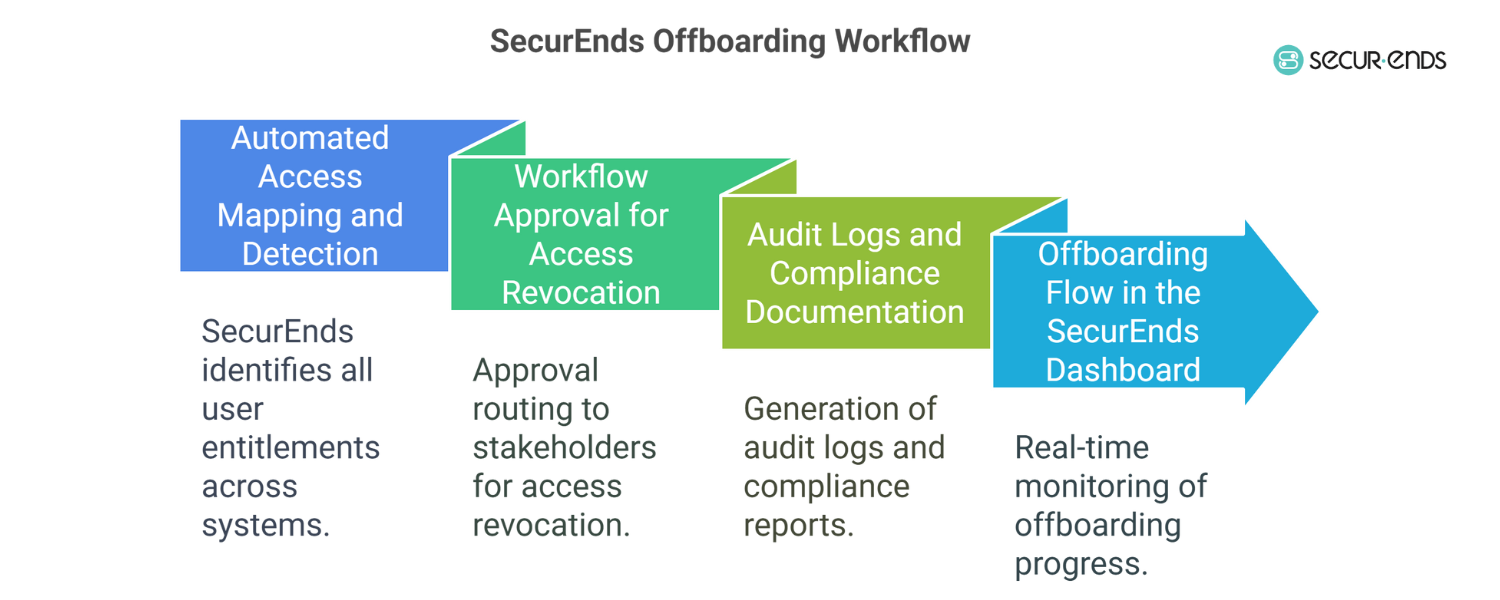
VI. Onboarding Workflow with SecurEnds (Step-by-Step)
Automation only works when it’s structured. That’s where SecurEnds comes in—offering a policy-driven, role-aligned onboarding workflow that seamlessly connects HR systems, IAM tools, and business applications.
Let’s break down how onboarding happens with SecurEnds in place:
Step 1: Employee Data from HRIS or ITSM
As soon as a new hire is added to the HR system, SecurEnds picks up the key details—department, location, title, and employment type.
This eliminates dependency on email-based requests or manual ticketing.
Step 2: Role Mapping to Access Profiles
Based on the employee’s attributes, SecurEnds assigns the appropriate access profile using role-based access control onboarding.
Developers get DevOps tools. Finance teams get ERP access. No overprovisioning. No guesswork.
Step 3: Auto-Provisioning Across All Systems
SaaS apps, cloud infrastructure, internal databases—access is automatically provisioned across environments.
Whether it’s a standard employee onboarding or a contractor self request, the flow is the same: fast, secure, and policy-aligned.
Step 4: Approval Routing + Audit Logging
For sensitive access, SecurEnds routes requests through predefined approval chains and logs every action—supporting IAM onboarding best practices and real-time compliance readiness.
Step 5: Full Visibility via Dashboards
Access status, pending approvals, and provisioning history are available in real time. IT, HR, and compliance teams get full visibility into the employee lifecycle automation process.
This isn’t automation for the sake of speed. It’s automation that improves control, reduces effort, and strengthens security—right from day one.
VII. Use Cases Across Industries
While every organization onboards employees, contractors, or vendors, the risks, regulatory requirements, and access complexity can vary dramatically by industry. That’s why a one-size-fits-all onboarding process doesn’t work.
Here’s how automated employee onboarding—powered by platforms like SecurEnds—adapts to meet industry-specific demands:
Healthcare
- Onboards doctors, nurses, and admin staff with department-specific access
- Supports employee self request and emergency access request workflows for high-pressure environments
- Maintains HIPAA compliance with full access visibility and approval logs
Financial Services
- Aligns with SOX and GLBA through centralized access controls
- Automates user access reviews and attestation cycles for auditors
- Prevents insider risk by enforcing least-privilege access during onboarding and offboarding
Retail & E-commerce
- Scales onboarding for seasonal and high-turnover roles
- Enables contractor self request capabilities for temporary staff and third-party vendors
- Ensures rapid provisioning without compromising security
Technology & SaaS
- Auto-provisions DevOps and cloud access based on roles
- Integrates with CI/CD tools and identity-aware infrastructure
- Supports just in time access request models to reduce standing privileges
No matter the industry, the value remains the same: Fast onboarding. Accurate access. Fewer tickets. Stronger compliance.
And when all of this is tied back into a unified Identity Governance and Administration (IGA) and Identity Access Management (IAM) strategy, organizations gain not just speed—but lasting control.
VIII. Manual vs. Automated Employee Onboarding: A Side-by-Side Comparison
By now, the benefits of automation are clear—but sometimes it takes a direct comparison to highlight just how much is at stake.
Here’s how manual onboarding stacks up against automated onboarding with SecurEnds:
| Feature / Process | Manual Onboarding | Automated Onboarding (with SecurEnds) |
| Provisioning Speed | Delays of 2–5 days; longer for remote or hybrid teams | Access granted within minutes of HR entry, based on roles and policy |
| Accuracy of Access | Inconsistent; prone to overprovisioning or missed apps | Role-based, policy-driven access provisioning with zero guesswork |
| Security Risks | Orphaned accounts, privilege creep, no consistent oversight | Least-privilege enforcement, automated deprovisioning, and full access traceability |
| Day-One Readiness | Employees often wait days for basic tools | All required accounts, devices, and systems ready on day one |
| Audit & Compliance | Scattered approvals, no unified trail, risky during audits | End-to-end audit logs, approvals, and access history for compliance mapping |
| IT/Helpdesk Workload | High — manual tickets, follow-ups, repeated provisioning | Low — automated flows reduce workload and human intervention |
| Scalability for Hybrid Teams | Breaks under pressure with distributed teams and third-party contractors | Built to scale securely across geographies and workforce types |
This side-by-side view helps IT leaders, CISOs, HR teams, and audit stakeholders align on why onboarding automation isn’t just about convenience—it’s about strengthening security, scalability, and compliance across the board.
It’s not just better. It’s necessary.
IX. Security & Compliance Advantages
When onboarding is manual, security is reactive. When onboarding is automated, security becomes proactive—and policy-driven from the start.
In regulated industries or high-stakes environments, this shift is critical. An intelligent onboarding framework doesn’t just speed up provisioning—it enforces compliance and reduces risk at every step of the employee lifecycle.
Here’s how automation directly strengthens your security posture:
Enforced Segregation of Duties (SoD)
Automation ensures conflicting access rights can’t be assigned—whether accidentally or through privilege creep. IAM onboarding best practices are built-in, not optional.
Full Access Traceability
With end-to-end logging and visibility into every employee onboarding event, organizations can confidently run user access reviews, meet attestation deadlines, and defend against audit inquiries.
Regulatory Readiness (SOX, HIPAA, GDPR)
Automated workflows maintain detailed records of who was granted access, when, why, and who approved it. This eliminates the risk of scattered approvals, helping you stay compliant at scale.
Reduced Insider Threat Exposure
By provisioning only what’s required—and automatically revoking access during employee off-boarding—organizations minimize standing privileges and close one of the most overlooked attack vectors.
Security isn’t a feature you add later. It starts with onboarding. And automation makes that security sustainable.
X. Final Thoughts: Building a Modern Onboarding Program
The first step in an employee’s journey is also the first opportunity to get security right. Or wrong.
In today’s dynamic, identity-driven enterprise, onboarding is no longer just an HR workflow—it’s a critical security function, deeply tied to your access model, compliance posture, and overall operational readiness.
And that’s exactly why manual processes no longer scale.
By adopting a centralized, automated approach, powered by platforms like SecurEnds, organizations can:
- Accelerate time-to-productivity with automated onboarding processes
- Implement role-based access control onboarding that eliminates guesswork
- Align with Identity Governance and Administration (IGA) and IAM onboarding best practices
- Strengthen compliance, reduce risk, and free up IT bandwidth
- Extend security across the entire employee lifecycle automation journey
Whether it’s employee self request, contractor onboarding, or emergency access, a well-structured onboarding system ensures every access point is intentional—and temporary, if needed.
It’s not just about who gets access. It’s about why, how, and for how long.
And that mindset begins on day one.