Offboard Remote Employees Securely with IAM Automation
Offboard Remote Employees Securely with IAM Automation
I. Introduction: Why Remote Offboarding Needs a Rethink
Offboarding used to be simple. An employee handed in their badge, returned the laptop, and IT disabled their account. Done.
But that model doesn’t hold up anymore. Today, teams are spread across cities, countries, and time zones. Employees work from home offices, co-working spaces, or airports—often on personal devices. Cloud tools are added weekly, and access is granted across dozens of platforms. In this environment, remote employee offboarding is no longer a one-step task—it’s a growing security blind spot.
And hybrid work? That adds another layer of complexity. In hybrid offboarding scenarios, employees often shift between roles and devices, leaving behind a fragmented trail of credentials and entitlements—some of which may never get revoked.
The problem isn’t just logistical—it’s strategic. Manual offboarding was never built for this kind of scale or fluidity. What’s needed is a system that knows who has access to what, automates removal in real time, and creates proof of every action. That’s where Identity Access Management (IAM) and Identity Governance and Administration (IGA) step in.
These frameworks bring structure to the chaos. They automate critical tasks, enforce policy-based access removal, and ensure employee off-boarding doesn’t slip through the cracks—no matter where the employee works from.
But to understand why this matters, it’s important to look at the hidden security risks that remote and hybrid setups expose—risks that can’t be seen until they cause real damage.
II. The Hidden Security Risks in Remote Offboarding
When teams are distributed, access is too. That’s what makes offboarding remote workers uniquely challenging—and uniquely risky.
In a remote or hybrid setup, employees use a mix of sanctioned and unsanctioned tools, operate across multiple devices, and often retain access to sensitive systems long after they’ve logged out for the last time. Here’s what that risk actually looks like in practice:
Orphaned Accounts: Still Active, Still Dangerous
It’s alarmingly common for ex-employees to retain access to SaaS applications—sometimes for weeks. Without automated triggers or centralized oversight, their accounts remain active in tools like Slack, GitHub, or Google Drive. These orphaned accounts create an invisible security gap—one that bad actors can exploit and auditors can flag.
A robust IGA solution can help detect and eliminate these accounts as part of a continuous user access review, ensuring no digital access lingers after offboarding.
Unmanaged Devices: BYOD at Its Weakest Point
When employees use personal laptops or smartphones under Bring Your Own Device (BYOD) policies, those devices often fall outside IT’s visibility. Unless Mobile Device Management (MDM) is tightly integrated with IAM processes, offboarding becomes guesswork—leaving data cached, emails synced, and access unrevoked.
The remote workforce risk here isn’t just access—it’s data sprawl on unmanaged hardware you no longer control.
Shadow IT Risks: What You Don’t See Can Hurt You
Employees often adopt unauthorized tools to get work done faster—especially in remote roles. From productivity apps to cloud storage, these shadow IT systems rarely get documented. So, when an employee leaves, no one knows what access to revoke—because no one knew it existed in the first place.
Without a consolidated access request framework and visibility through IGA, this data simply walks out the door.
Disgruntled Departures: Security is Emotional, Too
Offboarding isn’t always a clean exit. Layoffs, performance issues, or contract disputes can result in emotional departures. If access isn’t terminated immediately—especially from privileged accounts—there’s a serious risk of misuse.
This is where real-time deprovisioning through Identity Access Management (IAM), backed by policy enforcement and Emergency Access Request controls, becomes a critical line of defense.
III. Why Manual Remote Offboarding Fails Most Organizations
If the risks are so obvious, why are so many businesses still relying on spreadsheets, email threads, and manual handoffs to offboard employees?
The answer lies in habit—and in systems that haven’t evolved to match the way we work today.
The HR-to-IT Gap: Where Things Slip Through
Offboarding starts with HR—but finishing it usually falls to IT. In remote or hybrid setups, this handoff often breaks down. A resignation email might be sent, but no one checks if all access was removed. Someone assumes the laptop was returned, but no one confirms if the employee can still log in from their phone.
Now multiply this across dozens of employees, multiple time zones, and a growing tech stack—and it’s clear why manual remote offboarding creates blind spots. Add in contractor self requests or short-term hires, and you’re left with a messy, unreliable process that’s easy to overlook.
SaaS Sprawl: Too Many Tools, Too Little Visibility
Every team has its favorite tools—project management apps, file sharing platforms, communication tools. But with each new subscription comes another login, another access point, and often… another missed deactivation.
This is SaaS sprawl in action: a bloated ecosystem of cloud apps with no central visibility. Without a unified Identity Governance and Administration (IGA) system, IT teams often have no idea which tools an employee was using, let alone whether those accounts were properly deactivated.
Delays That Cost You More Than Time
With remote teams spread globally, offboarding doesn’t always happen in real time. If someone leaves a company on a Friday, but IT doesn’t remove access until Monday, that’s a two-day window for potential risk. Even if nothing malicious happens, that delay is still a liability.
Automation closes this gap. With IAM policies tied to employee off-boarding events or triggered by Self Request/Access Request actions, access can be revoked instantly—without waiting on human intervention.
No Audit Trail = No Proof
Here’s the part most teams realize too late: if something goes wrong, can you prove what actions were taken?
Manual offboarding usually lacks the one thing auditors care about most—proof. Without a digital audit trail, you can’t show when access was revoked, who approved it, or whether it was done at all.
That’s why organizations comparing manual vs automated remote offboarding are leaning into automation—not just for efficiency, but for assurance. You’re not just turning off access—you’re documenting trust.
IV. IAM + IGA for Secure Remote Offboarding: How It Works
So, what’s the real fix for broken offboarding workflows?
Automation alone isn’t enough—it has to be guided by identity. For a remote or hybrid environment, security starts with understanding who had access, why they had it, and when it should be revoked. This is exactly what Identity Access Management (IAM) and Identity Governance and Administration (IGA) are designed for.
Together, they form the foundation of a smarter, scalable way to automate remote offboarding—one that adapts to the complexity of distributed teams and ever-changing access needs.
IAM: The Enabler for a Remote Workforce
IAM for remote workforce scenarios is about more than just user provisioning—it’s about lifecycle control. From employee onboarding to employee off-boarding, IAM ensures access is tightly controlled across every system, cloud tool, and device.
When an offboarding event is triggered—say, through an HR system update or a Contractor Self Request—IAM immediately begins to revoke access based on defined rules. No delays, no missed steps.
IGA: Governance That Matches the Pace of Hybrid Work
IGA for hybrid teams adds oversight to automation. It helps organizations continuously review access rights, apply least-privilege principles, and manage entitlements—whether they were provisioned manually or via Employee Self Request, Just in Time Access Request, or even Emergency Access Request.
This ensures that by the time someone leaves, there’s already clarity on what access they had—and why.
Policy-Driven Offboarding with Access Reviews
With role- and policy-based deprovisioning in place, user access reviews become far more effective. Instead of chasing every app or platform, IT teams get clear snapshots of entitlements that can be instantly revoked.
The moment an offboarding is initiated, all systems—SSO platforms, cloud tools, even MDM solutions—can begin deactivation workflows in sync.
Built-In Audit Trails for Full Accountability
All of this happens with complete traceability. IAM and IGA platforms generate audit trails for every offboarding event: who approved it, what access was removed, and when it was logged. These logs become essential for compliance, investigations, and peace of mind.
So whether you’re offboarding a hybrid developer who used dozens of SaaS tools, or a contractor who had temporary access via a Access Request model—automation with identity context ensures nothing is missed, and everything is recorded.
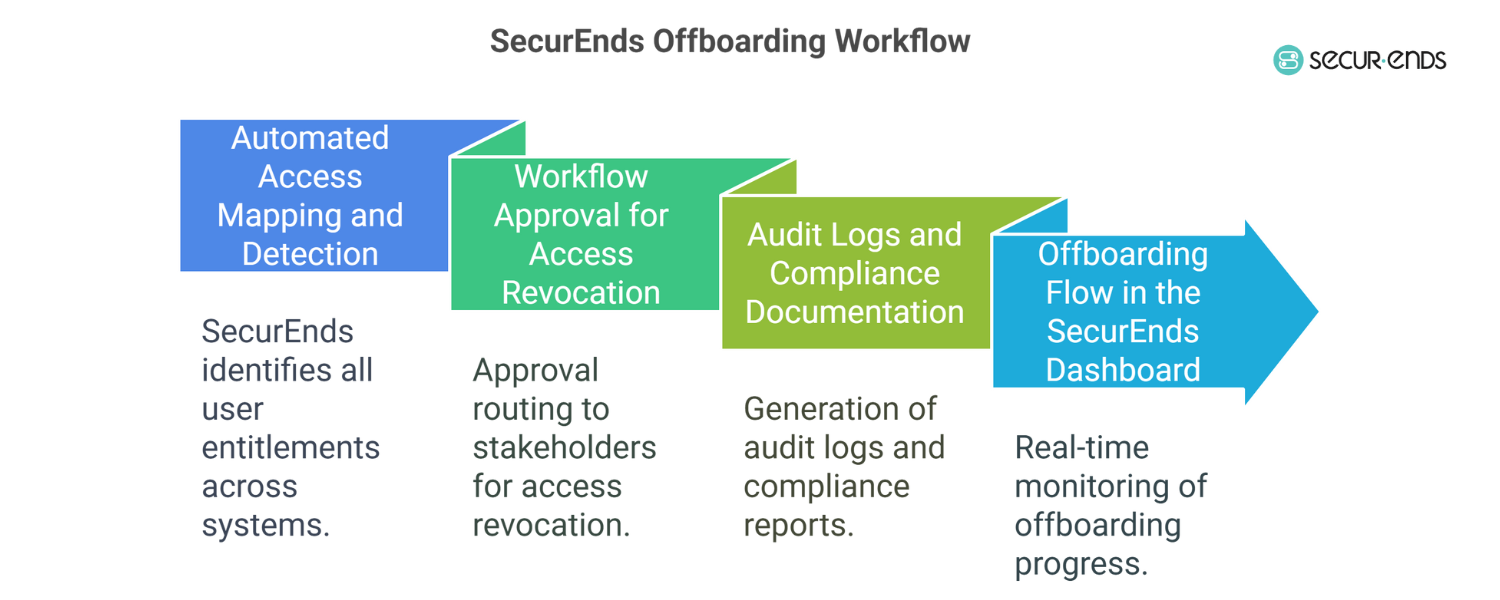
V. Step-by-Step Remote Offboarding Workflow Using SecurEnds
Knowing what needs to be done is one thing—being able to do it consistently, across every remote and hybrid user, is another. That’s where SecurEnds offboarding makes a measurable impact. Its unified approach brings automation, governance, and visibility together in one seamless process.
Here’s what a secure, automated offboarding workflow looks like using SecurEnds:
1. Trigger: Termination Notice from HRMS
The process begins automatically. A termination update in your HR system—whether it’s for an employee, contractor, or remote freelancer—immediately notifies SecurEnds to begin employee off-boarding.
Whether it’s a scheduled departure or a sudden exit requiring Emergency Access Request controls, SecurEnds handles it with the same precision.
2. Access Mapping: Identify All Entitlements
SecurEnds scans across identity providers like Okta or Azure AD, cloud platforms, and integrated SaaS tools to identify what access the departing user had—across accounts created directly, through Self Request/Access Request portals, or temporary Just in Time Access Requests.
This step also aligns with IGA principles, offering visibility into what needs to be revoked—and why.
3. Auto Deprovision: Revoke System Access
With mapped access in hand, SecurEnds initiates automated revocation across all connected systems. From email and VPN to project management tools, access is removed without delay. These employee access termination steps happen based on role, policy, or custom workflows.
Even admin or privileged access—like those gained via Contractor Self Request—can be revoked centrally without manual intervention.
4. Alert & Report: Keep Stakeholders Informed
As access is revoked, notifications are sent to managers and security teams. SecurEnds also generates detailed user access review reports and policy logs in real-time, supporting audits and internal oversight with minimal effort.
5. Data Retention: Secure What Matters
Before accounts are fully deactivated, SecurEnds enables backup of critical SaaS data—project files, shared documents, client communications—ensuring business continuity. Access can be archived without violating privacy or compliance standards.
6. Asset Recovery: Remote Instructions + Device Lockout
If the user has enrolled devices, Mobile Device Management (MDM) integrations can remotely wipe or lock them. SecurEnds supports sending secure offboarding instructions to guide hardware return or apply remote lockout—especially useful for fully remote teams.
This step-by-step flow isn’t just efficient—it’s secure, repeatable, and audit-ready. Whether offboarding a hybrid developer or a global sales contractor, SecurEnds offboarding ensures nothing gets missed.
VI. Offboarding Remote Employees Securely: IT Checklist
For remote teams, offboarding needs more than just a checklist—it needs precision. But having a well-structured, documented checklist ensures your process is consistent, complete, and compliant across all roles, tools, and locations.
Here’s a streamlined remote offboarding checklist tailored for today’s hybrid and remote workforces:
| Category | What to Check |
| SaaS Access | Revoke SSO access from tools like Google Workspace, Microsoft 365, etc. via IAM |
| Cloud Apps | Remove licenses from apps like Slack, Zoom, GitHub, Asana, and others |
| Admin Rights | Remove elevated or privileged access across systems and accounts |
| Endpoint Control | Disable VPN access, remove email forwarding, and perform MDM wipe if needed |
| Asset Collection | Coordinate courier pickup for devices or initiate remote lock via MDM |
| Logging & Proof | Archive user access review reports, approval trails, and offboarding logs for audits |
This checklist also supports access granted through temporary or ad hoc methods like Self Request/Access Request, Just in Time Access Requests, or Contractor Self Requests—areas often overlooked in manual employee off-boarding.
By combining identity controls from IAM with visibility from IGA, organizations can handle access revocation for remote teams with confidence—knowing no account, license, or device is left unmanaged.
VII. Compliance for Remote Offboarding: What Auditors Expect
When it comes to remote offboarding compliance, good intentions won’t help you pass an audit—evidence will.
Regulations like SOX, HIPAA, ISO 27001, and GDPR all require organizations to demonstrate timely removal of access for departing users. That’s where many manual offboarding processes fall short: they lack documentation, centralized control, and real-time visibility.
Here’s what regulators and auditors typically expect during employee off-boarding:
Orphaned Accounts = Immediate Red Flag
Leaving access open for former employees—especially in cloud apps or shared systems—violates nearly every major compliance framework. Whether it’s a user still in Salesforce two weeks after termination, or lingering admin rights in AWS, these gaps are treated as active risks.
Access Revocation Must Be Proactive and Documented
Auditors don’t just ask if access was revoked—they ask when, how, and who approved it. This is where Identity Access Management (IAM) and Identity Governance and Administration (IGA) step in. They enforce policy-driven offboarding and log every action taken.
With automated user access reviews, approvals, and time-stamped audit trails, your organization can provide proof—not just intent.
HIPAA IAM: Protecting Patient and System Data
In healthcare settings, HIPAA requires strict access control to protect patient data. That means revoking EHR system access immediately and ensuring no residual permissions remain. A misstep here could result in a compliance violation or worse—unauthorized access to sensitive records.
HIPAA IAM implementations through platforms like SecurEnds provide automated workflows and reporting that reduce human error and ensure no access goes unchecked.
Global Teams, Local Requirements
With remote teams working across borders, data sovereignty and local regulatory standards also come into play. Automating offboarding ensures consistent application of global policies—while providing localized logs and reports for region-specific audits.
Whether you’re preparing for a SOX offboarding audit or building GDPR readiness into your employee off-boarding lifecycle, automation makes compliance not only possible—but repeatable.
VIII. Case Example: How a Hybrid Tech Company Automated Offboarding with IAM
A fast-growing hybrid tech company with teams across North America and Southeast Asia was struggling to manage employee off-boarding at scale. With over 70 SaaS tools in use, manual tracking of user access had become unsustainable—and risky.
The Challenge
- Departing employees retained access to tools like Jira, GitHub, and customer databases for days after exit
- HR and IT operated in silos, causing delays in deprovisioning
- No centralized audit trail or proof of access removal during internal audits
- Contractor accounts created via Contractor Self Request portals were frequently overlooked
The Solution
The company implemented SecurEnds with integrated Identity Access Management (IAM) and Identity Governance and Administration (IGA) workflows. The offboarding process was automated from termination trigger to access revocation.
Key features enabled:
- Automated offboarding from HRMS alerts
- Mapping and removal of all user entitlements via access review workflows
- Immediate deprovisioning of cloud, VPN, and privileged accounts
- Logged approvals and notifications to satisfy SOX and internal compliance requirements
The Result
- 96% reduction in access termination time, from an average of 2.3 days to under 2 hours
- Passed a SOX audit with zero findings related to user access
- Reclaimed 15–20 unused SaaS licenses per offboarding, saving thousands in recurring costs
- Increased confidence in secure exits across hybrid, remote, and contractor roles
Whether your workforce is global, hybrid, or constantly shifting, the right automation strategy helps you take control of user access—without adding complexity to IT operations.
IX. Conclusion: Why IAM-Led Remote Offboarding Is the Future
Remote and hybrid work isn’t going anywhere—and neither are the risks that come with it. Every time an employee leaves without a defined, automated process in place, organizations face gaps in visibility, compliance, and security.
Manual methods simply can’t keep up with today’s distributed environments. They miss critical steps, create blind spots, and leave systems vulnerable. That’s why more businesses are turning to automated IAM solutions backed by strong IGA policies—to bring consistency and control to employee off-boarding.
From real-time user access reviews to audit-ready logs and seamless policy enforcement, modern offboarding needs to be secure, scalable, and built into your identity strategy. This isn’t just about cleaning up after an exit—it’s about building employee lifecycle security into your organization’s DNA.
If you’re ready to simplify offboarding, eliminate human error, and protect your digital environment—SecurEnds can help.
Explore a live demo or connect with our team to see how secure offboarding is done right with automation at the core.