How to Automate Employee Offboarding and Reduce Risk
How to Automate Employee Offboarding and Reduce Risk
Introduction
Employee exits are inevitable—but unmanaged exits are avoidable. In many organizations, offboarding still relies on manual coordination between HR, IT, and security—a slow, fragmented process with too much room for error.
This gap is no longer just operational. It’s a security concern.
From unauthorized data transfers to policy violations, the risks tied to poor employee off-boarding are mounting. Delays in revoking access—especially across identity providers, SaaS tools, and legacy systems—leave behind orphaned accounts that attackers or disgruntled ex-employees can exploit.
That’s why the shift toward automated offboarding is no longer optional. When tightly integrated into a company’s Identity Access Management (IAM) and Identity Governance and Administration (IGA) strategy, automation brings structure and control to a previously disjointed process.
An automated offboarding process ensures consistent user access reviews, faster revocation across systems, and cleaner separation of duties. It aligns with broader lifecycle practices—just as organizations streamline employee onboarding, they must also modernize how they handle exits.
So, why automate offboarding? Because manual processes don’t scale, and the risks of inaction now outweigh the cost of automation.
To ensure secure and efficient offboarding, it’s essential to manage access at every stage—learn how Employee Lifecycle Access Management plays a critical role in this process.
The Hidden Risks of Manual Offboarding
Manual offboarding isn’t just outdated—it’s dangerous. In decentralized IT environments, the lack of a structured exit process leads to critical oversights that can expose the business to avoidable security, compliance, and operational risks.
Fragmented Access Requests — Bottlenecks Between HR and IT
When HR and IT rely on emails, spreadsheets, or ad-hoc workflows to manage employee off-boarding, delays are inevitable. A departing employee’s last day may come and go, but their access remains intact simply because no one initiated the request—or didn’t know they had to. This kind of disconnect is common in organizations without centralized access request or self request systems, especially where contractors or temporary workers are concerned.
Overprovisioning & Human Error — Standing Privileges Remain Post-Exit
Without visibility into all the systems a user has access to, offboarding becomes guesswork. IT teams may deactivate a user’s email but forget the CRM or cloud file storage, especially in companies lacking robust user access reviews or automated role-mapping. These gaps lead to standing privileges that persist long after departure—prime examples of manual offboarding risks that go unnoticed until it’s too late.
Delayed Day-One Deactivation — SaaS Deprovisioning Lags Behind
In fast-growing businesses using dozens of SaaS tools, manually revoking access to each platform is time-consuming—and often skipped or delayed. Without automated triggers or policy-based controls tied to identity systems, employee access risks accumulate quickly. And for high-risk accounts (finance, customer data, DevOps), even a 24-hour delay can create major exposure.
No Central Audit Trail — Compliance & Security Blind Spots
Manual processes rarely generate the documentation required for audits or internal reviews. Who approved the termination? What apps were deprovisioned? When? Without centralized tracking—typically handled by IGA platforms—there’s no clear audit trail to demonstrate access was revoked properly. This creates both orphaned accounts and compliance red flags, particularly for industries bound by SOX, HIPAA, or GDPR.
Why Offboarding Is a Cybersecurity Risk
The moment an employee leaves, their access should end. But in many organizations, offboarding isn’t immediate—and that delay opens the door to security vulnerabilities that are often underestimated.
Insider Threats from Disgruntled Ex-Employees
When an exit isn’t managed securely, former staff can retain entry points into systems—intentionally or unintentionally. Whether it’s a contractor with leftover VPN access or a disgruntled ex-employee with admin rights, the potential for insider threats is significant. These scenarios are more common in companies where employee off-boarding is handled manually or inconsistently.
Standing Access Privileges in SaaS and On-Prem Systems
Most users collect access over time—gaining entry to apps, files, and systems beyond their original scope. Without a structured offboarding process, these standing access privileges linger. This is especially risky in hybrid environments where IAM doesn’t fully extend to legacy or on-prem applications. A lack of centralized oversight makes it hard to identify and revoke access completely.
That’s where Identity Access Management (IAM) and Identity Governance and Administration (IGA) become essential. By integrating automated policies, these systems ensure that all access—including elevated roles, Just in Time Access Requests, and Emergency Access Requests—is revoked promptly at offboarding.
Real-World Breaches from Poor Offboarding
The consequences of delayed access revocation are real. Several documented cases have shown how improper offboarding led directly to a data breach employee exit. In many of these breaches, orphaned accounts and outdated manual processes left backdoors open—giving former employees access to sensitive data, even months after termination. These events don’t just harm systems—they damage trust, trigger regulatory scrutiny, and create long-term financial impact.
Regular user access reviews and automated deprovisioning workflows are now critical safeguards. Without them, organizations leave too much to chance during employee off-boarding, especially when access requests are managed across multiple systems and teams.
The Role of IAM and IGA in Offboarding Automation
Modern offboarding is no longer about simply disabling an account or removing a user from Active Directory. It’s about managing risk through consistent, policy-driven, and automated processes—something only possible when IAM offboarding and IGA offboarding are fully embedded into your IT and security strategy.
Role-Based Access and Policy-Based Revocation
With a strong Identity Access Management (IAM) foundation, users are granted access based on roles—not individual permissions. That same logic should guide automated access revocation during offboarding. When an employee exits, their role-based entitlements can be revoked instantly, across all connected systems, using pre-configured policies—no manual intervention required.
This is especially valuable in organizations with distributed workforces or high turnover, where managing access manually becomes unscalable.
How IGA Enables Access Visibility and Governance
Identity Governance and Administration (IGA) adds another layer of control. It brings visibility into who has access to what, when, and why. During offboarding, this means IT teams can quickly identify entitlements, detect anomalies, and ensure user access reviews are enforced—automatically flagging any permissions that deviate from the norm.
It also streamlines removal of temporary access, such as contractor self requests, emergency access requests, or employee self requests, which can otherwise be missed in manual processes.
Continuous Access Certification Tied to User Lifecycle
True lifecycle security means building automation around every identity event—employee onboarding, transfers, promotions, and exits. With IAM and IGA working in sync, offboarding becomes a structured checkpoint, not an afterthought.
Automation ensures that deactivation happens in real-time, logs are generated for auditability, and access certifications are continuously updated—creating a secure and compliant offboarding flow that doesn’t rely on follow-up emails or delayed tickets.
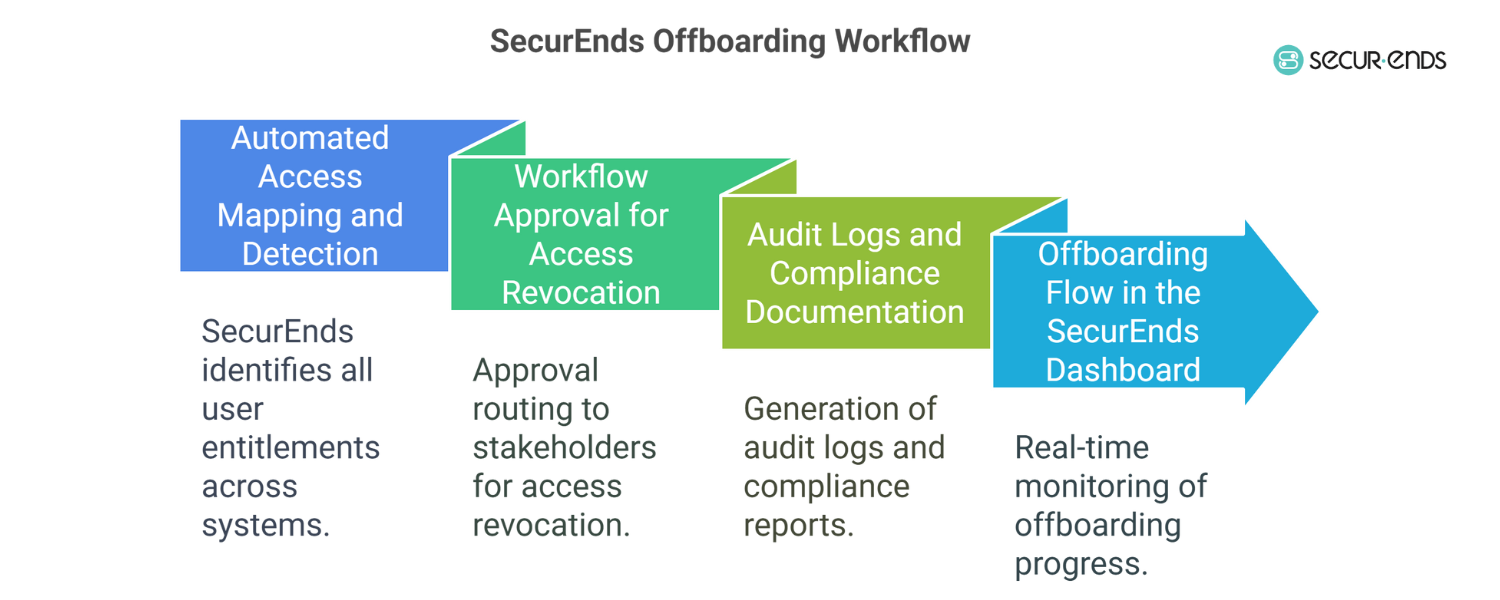
Offboarding Workflow with SecurEnds: A Step-by-Step Guide
A secure offboarding process should be consistent, repeatable, and verifiable. That’s exactly what the SecurEnds offboarding workflow delivers—bringing automation, oversight, and accountability into every stage of employee access termination.
Here’s how it works in a real-world setting:
1. Automated Access Mapping and Detection
The process begins with a complete inventory of user entitlements across cloud and on-prem systems. SecurEnds automatically detects accounts tied to the departing employee—including accounts created through employee self requests, contractor self requests, or Just in Time Access Requests. This eliminates guesswork and ensures that no access is missed, regardless of how it was originally provisioned.
2. Workflow Approval for Access Revocation
Once access points are identified, SecurEnds initiates an automated offboarding workflow with approval routing to the right stakeholders—whether it’s team leads, IT admins, or compliance managers. This ensures access revocation aligns with internal governance and satisfies regulatory review protocols. Revocation is executed based on IAM policies and IGA role mappings, including the removal of standing privileges and temporary entitlements.
3. Audit Logs and Compliance Documentation Generated Automatically
Every action in the offboarding workflow is captured and time-stamped. Audit logs, access removal confirmations, and certification reports are generated automatically, simplifying compliance with regulations like SOX, HIPAA, and GDPR. This level of documentation replaces manual tracking with verifiable proof—making it easier to demonstrate that your employee off-boarding process meets security and legal standards.
4. Example: Offboarding Flow in the SecurEnds Dashboard
In the SecurEnds dashboard, IT teams can monitor offboarding progress in real time. Dashboards display pending access requests, current revocation status, and user access review metrics—all tied back to identity records. This gives security teams the clarity and confidence needed to shut down access decisively and efficiently.
By integrating IAM and IGA principles into a single, actionable workflow, SecurEnds makes employee access termination steps both scalable and secure.
Access Revocation Checklist for IT Teams
Even with automation, IT teams need a clear process for ensuring that no digital doors are left open during offboarding. Whether you’re using a dedicated tool like SecurEnds or coordinating with multiple teams, this IT offboarding checklist outlines the critical steps to securely terminate employee access across your environment.
Remove Directory and Identity Provider Access (AD, Okta)
Begin by disabling the user’s account in your primary directory services like Active Directory (AD), Azure AD, or identity providers such as Okta. These serve as the foundation for access to multiple applications, and deactivating them should be the first priority in the employee access termination steps.
Revoke App Access (Email, CRM, Finance Tools)
Next, terminate access to essential business apps—email platforms, CRM systems, finance tools, and collaboration suites like Google Workspace or Microsoft 365. With a solution like SecurEnds offboarding, these steps can be built into an automated offboarding workflow, mapped to the user’s role or department through IGA.
Deactivate Shared Credentials
Any shared credentials or team-level logins the employee had access to must also be reset. Even if those accounts aren’t tied to individual identities, they’re a vulnerability—especially for temporary workers who gained access through contractor self requests or emergency access requests.
Archive Logs for Audits and Investigations
Maintain detailed audit logs of every access deactivation, policy trigger, and system update. This is crucial not only for internal governance and security reviews, but also to meet regulatory obligations under SOX, HIPAA, and GDPR. Solutions like SecurEnds ensure that logs are captured and stored automatically, reducing manual overhead for IT.
Run Final User Access Review
To ensure full closure, conduct a user access review post-termination. This helps confirm that no active or shadow accounts remain. It also ensures that future provisioning—via employee onboarding or self request/access request flows—can be properly managed without legacy access bleeding into new roles.
This checklist helps IT teams cover all bases while making automated access revocation systematic, auditable, and secure.
Compliance-Ready Offboarding: Meeting SOX, HIPAA, GDPR
Modern organizations operate in a landscape defined by strict regulatory obligations. Whether you’re managing financial data, health records, or personal information, the stakes are high—and that includes how you handle employee off-boarding. Incomplete or delayed access revocation isn’t just a security issue—it’s a compliance failure waiting to happen.
What Regulators Expect During Employee Exits
Frameworks like SOX, HIPAA, and GDPR demand strict controls over who has access to sensitive data—and just as importantly, when that access ends. Regulators expect a formal, documented offboarding compliance process that proves you’ve removed access in a timely, systematic manner.
For instance, SOX offboarding requirements focus on internal controls that protect financial reporting. Under HIPAA, failure to execute timely employee termination can lead to unauthorized access of protected health information. And with GDPR, lingering user access could constitute a violation of data minimization and confidentiality principles—especially when access requests are not fully decommissioned.
Proof of Access Revocation and Least Privilege
It’s not enough to say you removed access—you have to prove it. That means showing complete audit logs, access certifications, and evidence of least-privilege enforcement. Solutions like SecurEnds provide this transparency by integrating Identity Governance and Administration (IGA) into every step of the offboarding process, including automatic deprovisioning of access granted through Just in Time Access Requests, contractor self requests, and employee self requests.
How SecurEnds Automates Compliance Reporting
SecurEnds not only automates automated access revocation, but also generates the necessary documentation to demonstrate compliance. This includes timestamped logs, approval workflows, revocation status, and user access review results—all centrally stored and ready for audit.
With automated policy enforcement mapped to IAM offboarding and IGA offboarding workflows, your organization can confidently meet regulatory expectations, reduce human error, and avoid costly penalties.
ROI of Offboarding Automation: Cost, Time & Risk Reduction
Offboarding automation isn’t just about tightening security—it’s also about streamlining operations and cutting avoidable costs. Whether you’re a fast-growing company or a mature enterprise, the offboarding automation ROI is tangible, measurable, and increasingly essential.
Reduced IT Workload and Ticket Volume
Manual employee off-boarding consumes time and creates repetitive IT tickets: disable accounts, revoke app access, update audit logs, send reminders to multiple teams. With automated offboarding, all of this is centralized and workflow-driven. Tasks are triggered based on employee status changes, drastically reducing manual follow-ups and freeing up IT bandwidth for more strategic priorities.
Saved SaaS License Costs Post-Termination
Inactive accounts left unchecked can rack up unnecessary costs, especially in SaaS-heavy environments. Without prompt automated access revocation, you may end up paying for licenses tied to former employees—weeks or even months after they’ve left.
By integrating IAM and IGA with SaaS billing platforms, automated solutions like SecurEnds detect when access is no longer needed and initiate revocation, helping organizations recover wasted spend. This is a direct, ongoing return on investment that builds over time.
Faster Deactivation = Lower Risk of Data Leaks
The cost of manual offboarding isn’t just operational—it’s also a risk multiplier. Delays in access revocation increase the window for insider threats or accidental data leaks. With SecurEnds, the offboarding process includes built-in governance controls like user access reviews, role-based revocations, and visibility into all access points—reducing exposure from day one.
For companies managing emergency access requests, contractor self requests, or complex employee self request scenarios, automation ensures none of these fall through the cracks.
Conclusion: Don’t Let the Exit Become an Entry Point
An employee’s exit shouldn’t be the beginning of your next security incident. Yet, without structured automation, that’s exactly what it can become.
Manual processes miss steps. People forget. Access lingers. But with a modern, automated approach to employee off-boarding, you close those doors—instantly and confidently.
Tools like SecurEnds don’t just streamline automated offboarding workflows—they align with your broader IAM and IGA goals. From detecting shadow access and managing self request/access request flows to automating user access reviews and producing audit-ready logs, every part of the offboarding puzzle fits together.
The future of identity security isn’t just about who gets in. It’s about ensuring no one stays in once they’re out.
Ready to automate your offboarding and take control of access from start to finish? Let’s make exits secure—by design.