Time-Based Access Controls (TBAC) in 2025: A Complete Guide to Secure, Flexible Access Management
Time-Based Access Controls (TBAC) in 2025: A Complete Guide to Secure, Flexible Access Management

1. Introduction
Think of access like a hotel key card. It works only for the duration of your stay, in the specific room you’ve booked. After checkout, the card is useless. Now imagine if every organization managed digital access with the same level of precision.
Unfortunately, many still don’t. Access is often granted and forgotten—lingering well past relevance. Former employees retain login rights, third-party contractors access internal systems beyond project deadlines, and critical applications remain vulnerable to misuse. These aren’t hypothetical risks—they’re active vulnerabilities that continue to show up in audit failures and breach reports.
Traditional models like Role-Based Access Control (RBAC) or even Attribute-Based Access Control (ABAC) weren’t designed for this level of nuance. That’s why organizations in 2025 are turning to Time-Based Access Control (TBAC)—an evolved, time-sensitive approach that grants permissions only when needed, and automatically revokes them when no longer relevant.
With TBAC, modern Identity Governance and Administration (IGA) and Identity Access Management (IAM) systems finally close the loop—from employee onboarding to off-boarding, from Just-in-Time access requests to emergency access scenarios, and even contractor self-request flows. It’s precise. It’s auditable. And most importantly, it’s built for the pace and complexity of today’s enterprise environment.
Let’s explore how TBAC works, why it matters, and how it’s helping organizations enforce least privilege—on time, every time.
2. What is Time-Based Access Control (TBAC)?
As we’ve seen, the traditional ways of controlling access—assigning roles and permissions upfront—are no longer enough in today’s dynamic and risk-filled environment. Organizations now need a smarter, more flexible approach that adjusts access based on real-world factors like time, context, and urgency.
This is exactly where Time-Based Access Control (TBAC) comes in. Simply put, TBAC restricts system access to specific timeframes, adding a vital layer of security that goes beyond static permissions. Instead of granting someone indefinite access, TBAC ensures access is available only when it’s truly needed.
Think of it this way: When an external contractor submits a Contractor Self Request to access your network, TBAC might grant their access only during the approved project hours, automatically revoking it afterward. Similarly, an employee’s access could be limited to their work shifts or specific project durations—aligning perfectly with processes like Employee Onboarding and Off-Boarding.
In this way, TBAC complements established Identity Governance and Administration (IGA) and Identity Access Management (IAM) practices by introducing temporal control—allowing organizations to enforce the principle of least privilege with precision and confidence.
3. Why Organizations Need TBAC in 2025
This shift toward Time-Based Access Control isn’t just theoretical—it’s a necessary evolution driven by real operational gaps.
Traditional models like Role-Based Access Control (RBAC) assign access based on job roles, but they often lack the nuance to handle modern workforce dynamics. When access remains active beyond what’s operationally required—whether for an employee who switched roles or a vendor whose contract ended—it creates dormant permissions that can quietly become security liabilities.
In 2025, organizations face increasing regulatory and operational pressure. From GDPR and HIPAA to SOX, compliance bodies now demand evidence that access isn’t just role-appropriate, but time-appropriate. Persistent access is no longer just inefficient—it’s non-compliant.
Add to that the complexity of hybrid workforces, third-party contractors, and project-based roles. Without mechanisms like Just in Time Access Requests or Contractor Self Requests, organizations risk overprovisioning users. TBAC helps solve this with surgical precision—access is granted only when needed, and automatically removed when it’s no longer relevant.
And during User Access Reviews, having time-bound logs dramatically improves clarity. It’s no longer about asking “Should this person have access?” but instead, “Did they have it only when they needed it?”
4. Key Features of TBAC
Implementing Time-Based Access Control (TBAC) isn’t just about setting a clock on access. It’s about building smarter, more responsive access frameworks that reflect real-world business needs. Let’s explore its core features—each playing a crucial role in tightening security and aligning with modern Identity Governance and Administration (IGA) expectations.
Time-Restricted Permissions
At the heart of TBAC lies the ability to grant access that automatically activates and expires within a defined time window. Think of it like issuing a digital keycard that only works from 9 AM to 6 PM—or for the duration of a two-week project. This prevents “access sprawl” where users retain permissions long after they’re needed, which is a common finding during User Access Reviews.
Temporary/Ephemeral Access Grants
Instead of assigning permanent roles, organizations can now grant ephemeral access—rights that vanish once their utility ends. This is especially useful during Employee Onboarding, when new hires may need elevated access for setup and training, but shouldn’t retain it beyond their ramp-up period.
Automated Access Expiry & Revocation
Gone are the days of manual ticketing to revoke access. TBAC ensures that every access grant is paired with an expiry condition. Whether it’s a scheduled revocation post-shift or post-project, or a broader Employee Off-Boarding workflow, automation ensures no loose ends.
Just-in-Time (JIT) Access Requests
Rather than granting standing privileges, Just-in-Time Access Requests allow users to ask for access at the exact moment they need it. For instance, a developer needing production access for debugging can trigger a JIT request—approved, logged, and then automatically revoked after a set duration.
Emergency Access Requests
When urgent, high-risk access is required—say, for critical incident response—Emergency Access Requests can be triggered. These are tightly controlled, time-bound, and logged in detail, helping balance speed with security, especially in regulated industries.
Integration with IAM/IGA Systems
TBAC is most powerful when integrated into broader systems like Identity Access Management (IAM) and IGA platforms such as SecurEnds. These integrations ensure seamless policy enforcement, unified logging, and contextual controls across users, roles, and systems.
Audit Logging and Access Review Readiness
Every access event under TBAC—whether granted, requested, or expired—is logged with a timestamp and policy context. This simplifies audits and enhances User Access Reviews, giving auditors confidence that access wasn’t just appropriate, but temporally justified.
5. How Time-Based Access Control (TBAC) Works: Step-by-Step
Seamless security isn’t just about setting the right policies — it’s about executing them with precision. Time-Based Access Control (TBAC) achieves this by embedding time-awareness into every access decision. Here’s how it works in a real-world Identity Access Management (IAM) or Identity Governance and Administration (IGA) framework like SecurEnds.
Step 1: The Access Request is Initiated
A user or system raises a Access Request — this could be an Employee Self Request, a Contractor Self Request, or even an automated system task requiring temporary access.
Example: A developer needs access to a production server to deploy a patch, so they submit a Just-in-Time Access Request for a 2-hour window.
Step 2: TBAC Rules Check the Time Window
The TBAC engine checks the access request against predefined time constraints. If the request falls within the approved schedule — say, 9:00 AM to 6:00 PM — it proceeds to the next step.
Example: If the developer submits the request at 10 AM, the policy recognizes it as within business hours.
Step 3: Policy Logic is Evaluated
Beyond just the clock, TBAC evaluates role, context, urgency, and duration. Rules can be layered — for instance, “Access permitted only during work hours and if the employee is on shift.”
This dynamic logic ensures least privilege enforcement in both space and time.
Step 4: Access is Granted + Logged
If all conditions match, the system grants access. Simultaneously, it logs the action — capturing who accessed what, when, why, and for how long. These logs become critical for User Access Reviews and audit trails.
Step 5: Automatic Revocation at End Time
Once the time window expires — say after 2 hours or at 6 PM — the access is automatically revoked. This is especially powerful for Employee Off-Boarding, ensuring no lingering privileges remain after departure.
Example: If a contractor’s access was approved for a two-week project, TBAC ensures access is deactivated after the project closes, without manual intervention.
6. Real-World Use Cases of TBAC
Time-Based Access Controls (TBAC) are not theoretical anymore — they’re solving real security and compliance challenges across industries. The ability to assign temporary, time-restricted permissions has become essential in complex access environments driven by contractors, hybrid teams, and dynamic workloads.
Let’s look at how organizations are applying TBAC today:
- Financial Services
Banks and fintech companies are using TBAC to restrict access to core systems — like payment gateways or compliance dashboards — strictly during business hours. For instance, admin-level access is only active between 9 AM and 6 PM, reducing the risk of unauthorized activity after hours. These workflows are monitored through user access reviews as part of broader Identity Governance and Administration (IGA) efforts.
- Healthcare
Hospitals often link access to Electronic Health Records (EHRs) with staff shifts. So, an on-call physician has access only during their designated hours — improving patient privacy and satisfying HIPAA requirements. This also supports employee onboarding by automatically tying system access to scheduled shifts.
- IT Teams
Internal developers or DevOps engineers are granted Just in Time Access Requests to sensitive environments — like production servers — during a release cycle. Once their work is done, access expires automatically. This drastically reduces standing privileges and is reinforced by Identity Access Management (IAM) tools.
- Third-Party Vendors
Vendors onboarded for a short-term cloud migration project might receive two-week access to specific tools via a Contractor Self Request. The system revokes access after the period, eliminating cleanup hassles during employee off-boarding or project close-outs.
- Emergency Situations
In urgent scenarios — like security incident response — IT leads can file Emergency Access Requests to override standard controls temporarily. These are logged and tied into IGA workflows for post-event auditing and risk analysis.
These examples illustrate why TBAC is not a luxury anymore — it’s a necessity in today’s dynamic access landscape.
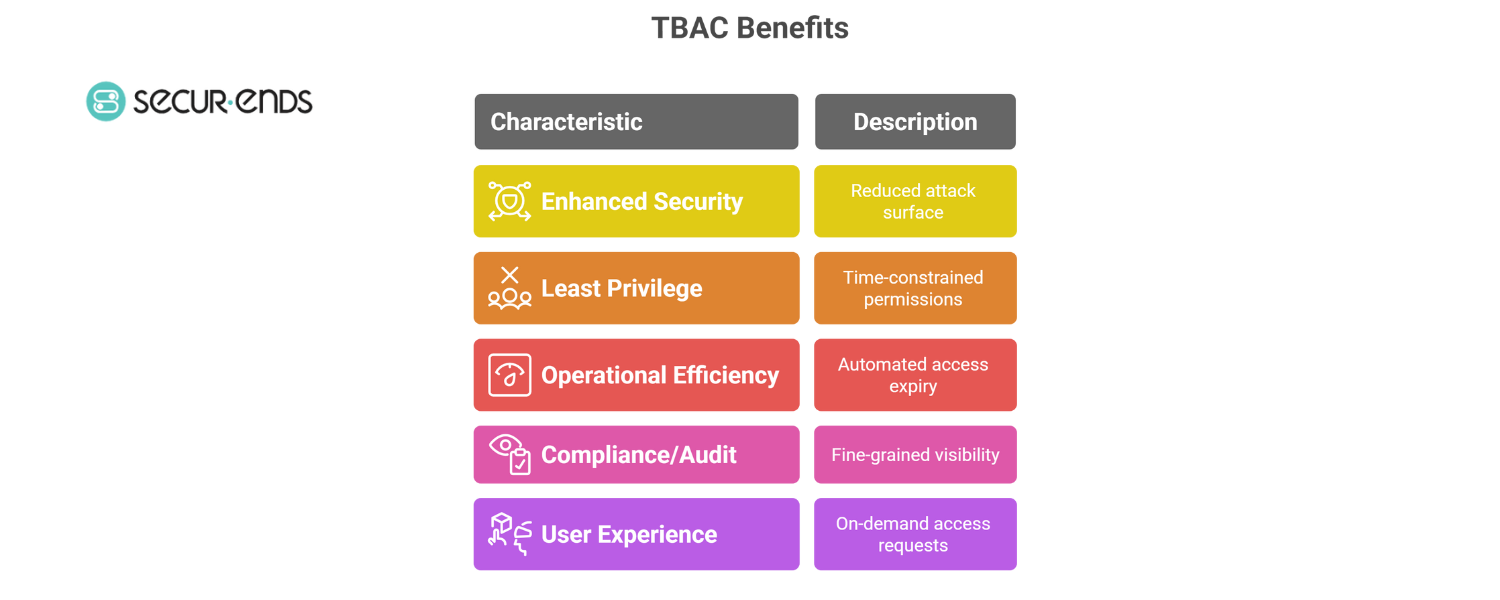
7. Benefits of Implementing TBAC
Integrating Time-Based Access Controls (TBAC) into your access strategy offers more than just an additional layer of control — it’s a practical move toward secure, scalable, and compliant access governance.
- Enhanced Security Posture
By granting access only for the exact time it’s needed, TBAC helps organizations reduce the attack surface. Dormant or unused accounts no longer become a backdoor risk. For example, a Just in Time Access Request allows a developer to troubleshoot production issues without retaining prolonged access — the system revokes it as soon as the task ends.
- Least Privilege Enforcement
TBAC naturally aligns with the principle of least privilege. Instead of assigning broad, always-on roles, you assign permissions with time constraints. Paired with Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC), it ensures users only access what’s required — and only when it’s required.
- Operational Efficiency
Automated access expiry means less manual intervention for IT and security teams. Whether it’s an Employee Self Request for weekend project access or a Contractor Self Request tied to a fixed contract window, time-bound workflows prevent overprovisioning and reduce the cleanup workload during employee off-boarding.
- Improved Compliance and Audit Readiness
Regulations like SOX, GDPR, and HIPAA demand strict control and tracking of access rights. TBAC enables fine-grained visibility and pairs seamlessly with user access reviews, making it easier to demonstrate access governance during audits. Integrations with Identity Governance and Administration (IGA) systems streamline this even further.
Better User Experience
TBAC might sound restrictive, but it actually empowers users. With well-configured Self Request/Access Request portals, users can request access on demand — for the exact time they need — without delays. It’s secure, flexible, and aligned with how modern teams work.
8. Challenges & Risks of TBAC
While Time-Based Access Control (TBAC) brings significant security and compliance advantages, implementing it isn’t without its complexities. To get the most out of TBAC, it’s essential to understand the potential hurdles and how to overcome them.
- Policy Complexity Across Teams
Different teams have different workflows — what works for a finance team’s access schedule may not fit IT or DevOps. Defining and managing policies that align with diverse roles, shifts, and exceptions requires thoughtful coordination and flexible policy design. This is where pairing TBAC with Identity Governance and Administration (IGA) platforms can simplify rule orchestration.
- Precise Time Synchronization
TBAC relies on accurate time settings across systems. Even slight discrepancies between the policy engine and access systems can lead to incorrect denials or unintended access. Using network time protocols (NTP) and centralizing policy enforcement via an Identity Access Management (IAM) layer helps mitigate this.
- Misconfigured Rules Can Disrupt Workflows
A poorly set time window could unintentionally block critical access, especially during urgent tasks. Fallback mechanisms — like Emergency Access Requests — are essential to avoid workflow bottlenecks or user frustration.
- Limited Support in Legacy Systems
Older infrastructure may not support dynamic or temporary access rules. In such cases, organizations need to either upgrade systems or use middleware solutions through modern IAM or IGA tools that bridge this functionality.
💡 Tip: Tools like SecurEnds help reduce these risks with pre-built templates, automation features, and access review modules that validate whether time-based permissions are functioning as intended.
9. How to Implement TBAC: Step-by-Step Framework
Implementing Time-Based Access Control (TBAC) isn’t just about adding time limits to access. It’s about building a structured framework that aligns with business goals, compliance needs, and user roles. Here’s how organizations can roll it out effectively:
1. Identify Critical Resources
Start by pinpointing which systems and applications house sensitive data or functionality. These could be financial platforms, admin consoles, or healthcare systems. Focus your User Access Reviews on these critical areas to prioritize access control.
2. Define Role-Based + Time-Based Policies
Combine Role-Based Access Control (RBAC) with temporal logic. Map each role to appropriate access windows — for instance, contractor access from 9 AM to 6 PM, or privileged database access only during maintenance windows. Incorporate Contractor Self Request workflows for short-term access.
3. Use IAM/IGA Platforms That Support TBAC
Ensure your Identity Governance and Administration (IGA) or Identity Access Management (IAM) system supports scheduling, temporary permissions, and rule-based expiry. Solutions like SecurEnds offer native support for Just in Time Access Requests, Emergency Access Requests, and automated revocation.
4. Test in a Sandbox Environment
Before rolling TBAC out enterprise-wide, simulate the policies in a test environment. This step helps uncover misconfigurations that might disrupt workflows — especially important for Employee Onboarding and Employee Off-Boarding transitions.
5. Monitor Access Logs and Auto-Reviews
Set up continuous monitoring and integrate TBAC events into your access review pipeline. Tools like SecurEnds help generate real-time audit trails that reflect time-based activities — critical for proving compliance and policy adherence.
6. Iterate Based on Usage and Audit Logs
Use audit insights to fine-tune TBAC rules. If a team consistently requests after-hours access via Self Request/Access Request modules, you may need to expand the window or automate approvals. Keep updating policies to match evolving workflows.
10. Best Practices for Time-Based Access Control (TBAC)
While Time-Based Access Control (TBAC) provides a powerful way to tighten access security, its success depends on thoughtful execution. To ensure it delivers both control and convenience, here are some best practices to follow:
1. Always Define Fallback or Escalation Rules
Not all access can be predicted. That’s why every TBAC policy should include backup procedures. For example, when access expires but critical work is ongoing, an Emergency Access Request pathway should allow for secure, auditable escalation — without compromising security or compliance.
2. Combine TBAC with RBAC or ABAC for Layered Control
TBAC shouldn’t operate in isolation. Blending it with Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) ensures more nuanced governance. Think of TBAC as the “when” layer complementing RBAC’s “who” and ABAC’s “why.” This layered approach is ideal for Employee Self Request workflows and Just in Time Access Requests.
3. Use Approval Workflows for Time-Sensitive Requests
Ensure every temporary access path — from Contractor Self Request to Employee Onboarding — is backed by approval workflows. This adds accountability and ensures that time-bound access is granted only when truly justified.
4. Maintain Clear Documentation and Policy Changelogs
Documenting every access policy — including time restrictions, exception workflows, and expiry rules — is essential. This supports easier audits and improves the transparency of your Identity Governance and Administration (IGA) strategy.
5. Periodically Validate Access Expiry and Time Rules
Don’t set and forget your TBAC rules. Regular User Access Reviews should include time-bound permissions to ensure they’re still relevant. Is that temporary access still needed? Are the configured time windows aligned with real work schedules? Refinement is ongoing.
11. How SecurEnds Supports Time-Based Access Controls
Modern enterprises need more than just policy—they need tools that execute those policies with precision. That’s where SecurEnds steps in. By integrating Time-Based Access Control (TBAC) directly into its Identity Governance and Administration (IGA) platform, SecurEnds transforms strategic intent into operational reality.
Centralized TBAC Policy Builder
SecurEnds allows IT admins to define, edit, and deploy time-restricted policies from a single interface. Whether it’s Just in Time Access Requests for DevOps teams or Employee Off-Boarding protocols that include automatic expiry of credentials, everything is managed in one place.
Workflow Integration with Access Request Modules
Access doesn’t exist in a vacuum. SecurEnds integrates TBAC into all its request pathways — including Self Request/Access Request, Contractor Self Request, and Emergency Access Request. These workflows are approval-based, auditable, and customizable to align with business processes.
Automated Revocation & Logging
The moment access time expires, SecurEnds automatically revokes permissions — eliminating risks from unattended standing access. These events are simultaneously logged, providing rich context for User Access Reviews and compliance audits.
Real-Time Access Reviews with TBAC Context
Access reviews aren’t complete without understanding when access was active. SecurEnds adds that temporal lens, allowing reviewers to validate whether time-based access is aligned with actual need. This is particularly helpful during Employee Onboarding, where temporary elevated access is often required.
12. Conclusion: Why TBAC is No Longer Optional
As organizations expand across cloud platforms, third-party ecosystems, and remote teams, access control is no longer just a security function—it’s a business enabler. But static access models, even when layered with IAM or IGA, often leave blind spots.
Time-Based Access Controls (TBAC) address this by introducing a temporal layer to identity governance—where access is granted not just to the right person, but at the right moment, for the right duration. Whether it’s handling Contractor Self Requests during onboarding windows or managing Emergency Access Requests during incidents, TBAC ensures every access decision aligns with the principle of least privilege.
More importantly, when integrated with User Access Reviews, Employee Self Requests, and auto-expiry workflows, TBAC becomes a cornerstone for proactive compliance, audit-readiness, and operational agility.
The organizations leading in 2025 won’t just be those that secure their data—but those that secure it intelligently, with time-aware access logic that adapts to modern risk.
TBAC isn’t a future solution—it’s today’s competitive advantage.
Frequently Asked Questions (FAQs)
1. What’s the difference between TBAC and RBAC?
While Role-Based Access Control (RBAC) assigns permissions based on a user’s role, Time-Based Access Control (TBAC) adds a critical dimension—time. TBAC limits access not only by role or attributes but also by specific time windows, ensuring access rights are active only when truly needed. This reduces risks from standing privileges and supports precise User Access Reviews.
2. Is TBAC suitable for cloud environments?
Absolutely. Modern cloud infrastructures demand dynamic, flexible access controls. TBAC integrates smoothly with Identity Governance and Administration (IGA) platforms to enforce time-sensitive policies across cloud applications, improving security for Contractor Self Requests and temporary access needs.
3. How does TBAC support compliance audits?
By automatically logging time-bound access events and enforcing access expiry, TBAC simplifies audit trails and demonstrates strong governance during regulatory reviews like SOX or GDPR. It aligns perfectly with periodic User Access Reviews to verify ongoing compliance.
4. Can TBAC be combined with MFA?
Yes, combining Multi-Factor Authentication (MFA) with TBAC creates layered security. MFA verifies identity, while TBAC ensures access is granted only during approved times, enhancing protection against unauthorized access.
5. What happens if time synchronization fails in a TBAC system?
Time accuracy is vital for TBAC. Most systems use Network Time Protocol (NTP) services to synchronize clocks. If synchronization issues occur, access may be temporarily restricted or flagged for review. This is why robust IGA tools often include alerts and fallback rules to prevent disruption.